
Hello,
Welcome to The Veza Voice, our regular newsletter to arm Veza customers with everything you need to be successful with the Veza platform. As you read on, you will hear & see updates across our platform and products, new integrations, strategic partnerships, Veza events & more.
Before we get into anything Veza related, I wanted to highlight the single most important thing to Veza over the last 90 days: our customers. So many of the updates contained in Veza Voice have been driven by the incredible partnership from our customers and partners.
We are proud of the progress that we have made in our journey together, and none of it would be possible without you. So please allow me to speak on behalf of all of Veza when I say thank you.
Best,
Mike Torres
State of Access 2024
We’re proud to announce the release of our first annual Industry-First State of Access report! This first-of-its-kind analysis dives deep into the current state of access permissions across hundreds of leading organizations.
Our hope is that the report provides benchmarks for IT, security, and identity professionals to better understand their own identity security posture and areas of focus to reduce the risk of breaches and on the journey to “principle of least privilege”.
Tune in on May 16th for a virtual presentation of the findings and download the report here.
Here are just a few highlights for our Veza platform and products. As always, you can check our full release notes for February and March for a complete rundown on what’s new.
Product Updates
Query pipelines
Some access risk conditions are too complex to be expressed in a single query. For these, you can now create query pipelines in the query builder to chain together multiple queries. You can think of these like sub-queries in SQL. For example:
- Find all Box folders accessible to Okta users in China, which are also accessible to users outside China.
- Find highly-permissioned roles in Snowflake, which are accessible to local Snowflake users.
- Find Azure AD users with Admin permissions in AWS, who also do not have MFA enabled.
Snowflake Data Governance and Salesforce Access Risks Dashboards
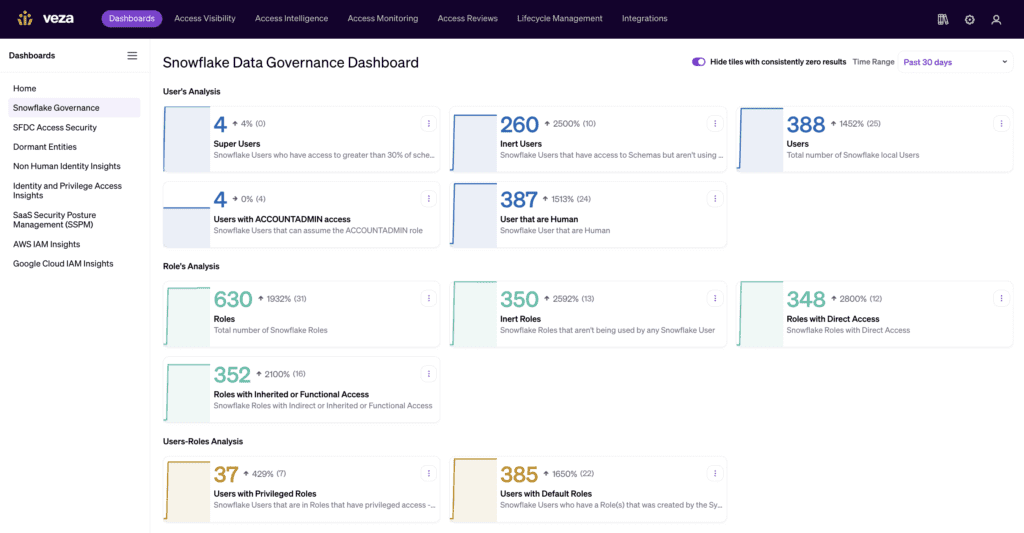
Get out-of-the-box insights on user access to Snowflake and Salesforce, including inactive users, privileged access, role analysis, and more.
Activity monitoring for AWS IAM and Okta
To implement least privilege, a crucial piece of the puzzle is not just what access an identity has, but what they’re doing with it. With Gartner estimating that up to 97% of cloud entitlements go unused, removing unneeded access is likely the single most important area for improvement in least privilege. Activity monitoring makes it simple to identify users and roles with unused permissions so that you can right-size access.
In addition to our existing support for Snowflake, this quarter we added the ability to monitor access to S3 buckets and KMS secrets in AWS. You can even track activity of individual Okta users assuming AWS roles via SAML. We’ve also added the ability to track Okta users use of Okta apps. Apart from applying least privilege this feature is great for identifying opportunities for cost savings by removing unnecessary licenses.
Expanded Lifecycle Management support for Modern IGA
We launched our Lifecycle Management offering last year with the goal of bringing Veza’s granular insight into user access to the process of provisioning and deprovisioning access, allowing organizations to onboard and offboard employees with confidence, knowing exactly what the outcomes of provisioning actions would be.
Furthering that goal, we’ve added new targets to our Lifecycle Management program, expanding to include Azure AD, Snowflake, and Workday as provisioning targets, and SAP Human Capital Management on the HR side. We’ve also added support for “mover” scenarios to automatically update access as employees move within the organization.
Streamlined Access Reviews

We’ve added some key improvements to further streamline access reviews and reduce the burden of manual processes. Firstly, we’ve added support for automatically deprovisioning certain types of rejected access to make sure that your decisions are consistently applied. For example, you can automatically revoke membership in an Okta group that granted inappropriate app access to a user.
Further, we now automatically enrich local accounts (for example a Snowflake local user) with metadata from HR and IdP records with a matching email address. In practice this means not only better context for the reviewer, but also the ability to auto-assign access reviews to the managers of the individuals with whom the local accounts belong, just like you can for IdP users.
We’ve also added more flexibility for automatically scheduling regular access reviews, adding quarterly, biweekly and monthly options, to make sure your access reviews always kick off on time, whatever your cadence.
On 5/17, we enabled a new user experience for reviewers in the Access Reviews product. This new experience saves reviewers time and simplifies decision-making when performing access reviews. More details can be found here.
Strategic partnerships
With over 200 integrations and counting, we’re closer than ever to our vision of a single pane of glass for access intelligence across your whole stack. This quarter we launched two new strategic partnerships, In addition to our existing offerings with Crowdstrike and Snowflake:
Veza for Hashicorp
In any enterprise, managing secret entitlements is fundamental to security. Veza for Hashicorp gives you detailed insight into which identities—both human and machine—can create, read, update, and delete secrets in Hashicorp Vault. This insight can power non-human identity discovery, comprehensive access reviews for Hashicorp secrets, alerts for crucial changes to access, and more.
Veza for ZScaler
80% of cyberattacks rely on identity-based techniques. Veza for ZScaler gives you comprehensive visibility into the access rights of users and service accounts in Zscaler. Identify and manage privileged accounts, power automated access reviews and compliance audits, align permissions in Zscaler with geographical and departmental policies, and more.
Other New Integrations
With over 200 integrations and counting, we’re closer than ever to our vision of a single pane of glass for access intelligence across your whole stack. Here’s a few of the new additions from this quarter.
Veza for Google Drive and Dropbox
While fileshare platforms like Google Drive and Dropbox enable frictionless collaboration with stakeholders both inside and outside your organization, the flipside is that it’s easy to lose track of who has access to sensitive data, potentially risking customer information, financial data, and IP. Veza for Dropbox and Google Drive lets you understand who has access to all drives and folders, including guest users, surface misconfigured drives and folders that allow for external or unauthorized access, and automated access reviews for unstructured data in your fileshare systems
Events
Here’s where to catch Veza at industry events over the next few months:
May 28-31 Identiverse
- Visit us at booth #2206
- Schedule a meeting with us
- Attend our breakout session: The Trend Toward Intelligent Universal Access Policy presented by Rich Dandliker, Chief Strategy Officer, Veza and Davis Tyburski, CISO, Wynn Resorts on Thursday, May 30th 4:35-5pm Room: Joshua
June 3-6 Gartner Security & Risk Management (SRM)
- Schedule a meeting with us
- Tee up with Veza at TopGolf June 4th to network with industry peers and master Modern IGA.
- Attend our session June 5th: Assessing and Addressing Your Identity Security in the Wake of the Recent <<Cloud Platform Provider>> Breaches.
Tips & Tricks: Using Veza to monitor application access in Okta
Veza monitors not only who is assigned what application in Okta but also the last time they have accessed that application to identify applications that have not been logged into. This can help you reclaim licenses for your expensive unused applications as well as help manage your SSO application lifecycle.
A common challenge with single sign-on, is the ability to know the last time a user logged into a specific application. Since your last login date for the user is going to be the last time the user logged into your identity provider rather than the last time the user logged into X application. Veza’s activity monitoring for Okta addresses this in an easy to use way which allows you to quickly identify applications that haven’t been logged into by any user or identify users who haven’t logged into those costly license applications.
Scenario 1: Monitor Otka for all Unused SSO Applications
- Query a List of Okta Applications related to Okta Users
- In the “Over Provisioned Score Threshold” section update your operation to “==” and ensure the “Threshold” value is 100.
- Click “+ Add Filter Group” to set a filter on your Okta App where it was Created At before X days ago (X days should match your Activity Monitoring Timeframe value)
- Listed are all the applications that have not been logged into for the last X days and were created more than X days ago.
- Save your query and set up a Rule to alert you when a new application falls into this scenario.
Congratulations, you have now successfully set up automated monitoring of unused applications in your Okta environment.
Scenario 2: Monitor Okta for unused Costly Application Licenses
- Query a list of Okta Users related to Okta Applications
- In the “Over Provisioned Score Threshold” section update your operation to “==” and ensure the “Threshold” value is 100.
- Click “+ Add Filter Group” to set a filter on your Okta User where it was Created At before X days ago (X days should match your Activity Monitoring Timeframe value)
- Click “+ Add Filter Group” to set a filter on your Okta Application where the ID equals the ID value of your Application ID for the costly license application. This is to ensure that you are looking at the right application since Okta will allow you to have applications with the same name.
- Save your query and set up a Rule to alert you when a new user falls into this scenario.
- Repeat for each application with a costly license.
Congratulations, you have now successfully set up automation monitoring of used costly application licenses in your Okta environment.
Veza welcomes Mike Towers as Chief Security and Trust Officer
This quarter marked the arrival of a key new member of our leadership team. Mike Towers brings twenty-five years of experience driving security and technology initiatives across the industry and we’re stoked to welcome him to Veza as our Chief Security and Trust officer. Read more about Mike’s appointment in our press room, or head to our blog to read Mike’s thoughts on the new challengers of Non-Human Identity Management, and the imperative for Identity Security as a discipline. You can also catch Mike’s take on the recent string of ransomware attacks in the healthcare industry.
Identity Security Spotlight: Midnight Blizzard’s Breach of Microsoft
Russian Intelligence-backed group Midnight Blizzard’s attack on Microsoft joins a long list of major breaches teaching us that identity is the weakest link in security. For Veza’s perspective on the incident, join our Co-Founder and CEO Tarun Thakur, and Chief Strategist Rich Dandliker to run down the key lessons from the Microsoft breach. For more, Rich talks with Veza Field CTO Tarek Khaled for a detailed demo of how Veza could potentially help to prevent similar attacks.
New customer case studies
Our customers are why we come to work every day, and nothing is more exciting than sharing their success. Head over to our website to learn more about how the City of Las Vegas protects the data of 42 million visitors a year, and how CopperPoint streamlined their operations and compliance processes with automation powered by Veza.
Gartner Peer Insights
See the latest Veza reviews on Gartner Peer Insights
Webinar: Security tips from the FBI
In April, we hosted a session with FBI Special Agent and Special Assistant U.S. Attorney Donovan McKendrick. Donovan shared tips based on his years of experience combating cyber crime with the Bureau. While the session was live-only, you can still head over to our website for a review of some of the key takeaways from that session.





