Veza for AWS
If AWS is a cornerstone of your cloud infrastructure, excessive or misconfigured access permissions in AWS IAM can be your single biggest vulnerability. Veza is the identity security platform enabling you to answer the question: Who can take what action on what services and data in AWS?

Identity security challenges in AWS
How Veza can help
Veza is powered by its Authorization Graph, which gives organizations the ability to visualize authorization relationships between all identities and systems by connecting users, groups, roles, and permissions.
- Reduced Risk: Surface and prioritize identities with the highest privilege, risk, or policy issues across all enterprise systems, without having to master the complex access model of AWS IAM.
- Least Privilege: Reduce risks and simplify audits by continuously identifying and remediating identity misconfigurations, dormant permissions, and over-permissioned identities.
- Team Efficiency: Reduce manual, repetitive tasks by leveraging automation to detect and remove dormant access. Use Veza to delegate access decisions to business managers who best understand specific systems.
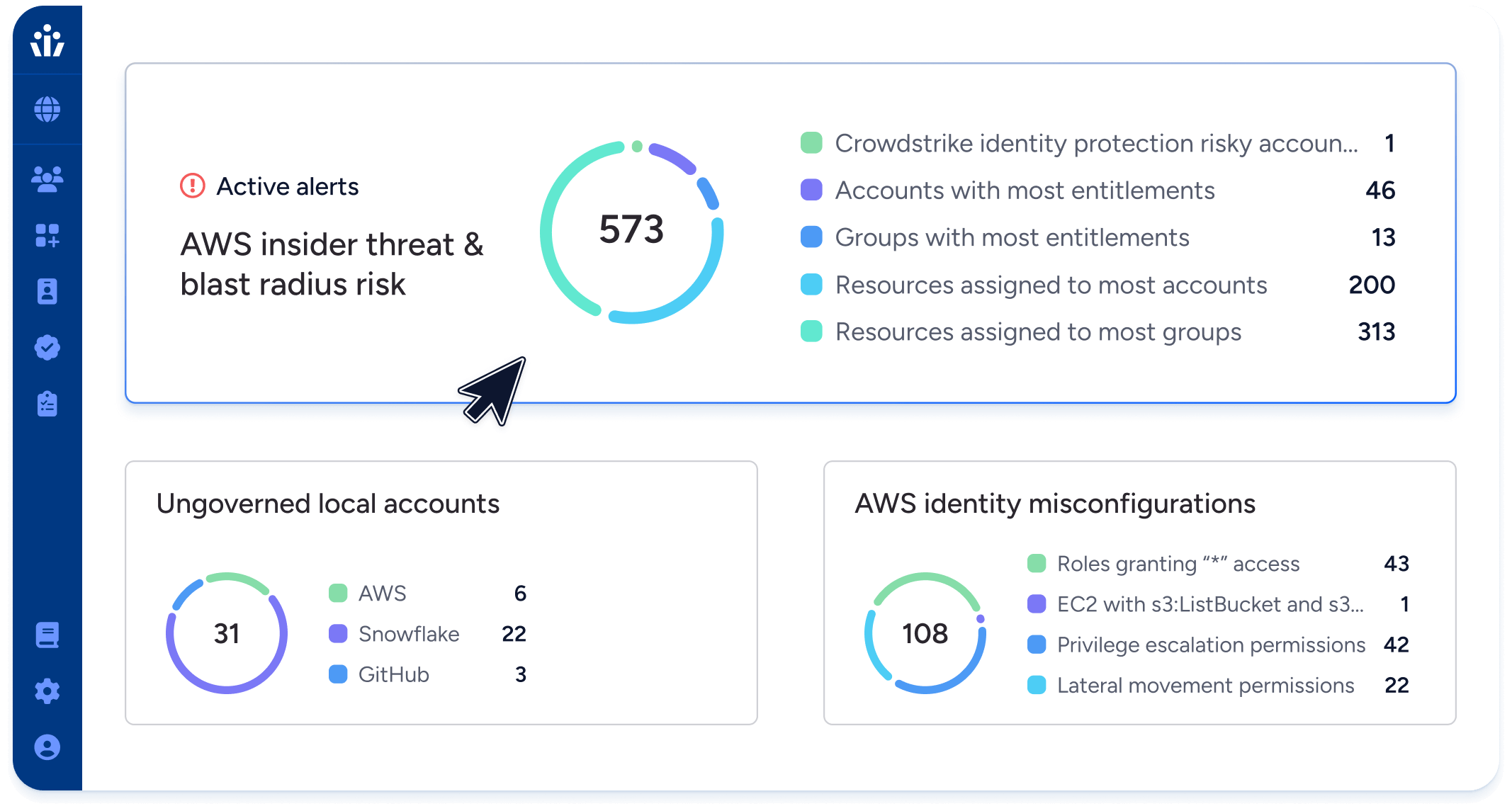
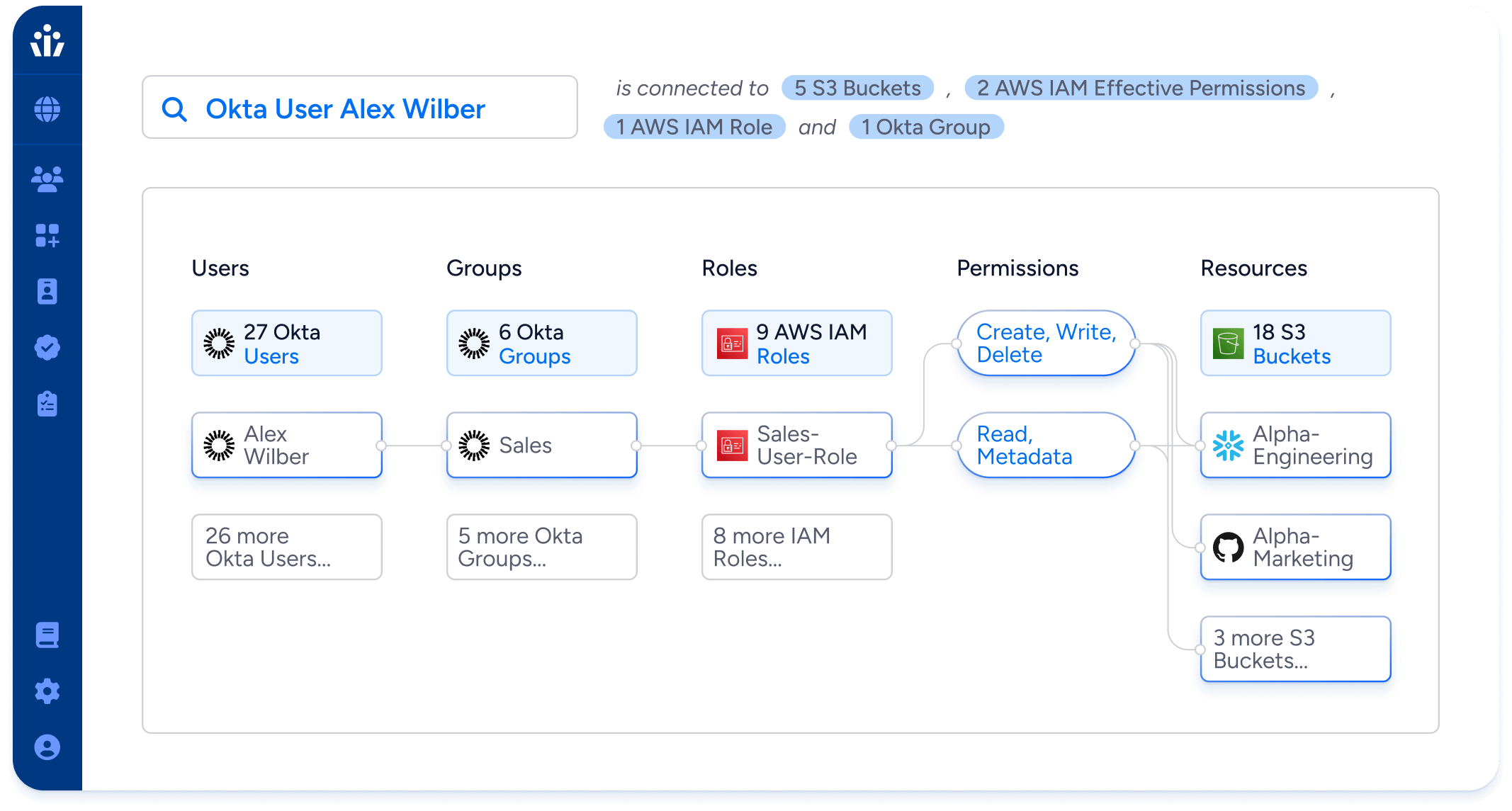
- Effective permissions: translate AWS IAM permissions into simple, human-readable language—”create, read, update, delete”—and resolve complex policy interactions to give actionable intelligence on who can do what in AWS.
- Automated monitoring: watch continuously for policy violations and new privileged accounts, so you can comply with internal controls and external regulations without burdening security and governance teams.
- Agentless read-only connections to both AWS and your identity providers, give a complete picture of the access granted to federated identities, revealing governance blindspots, like local users.
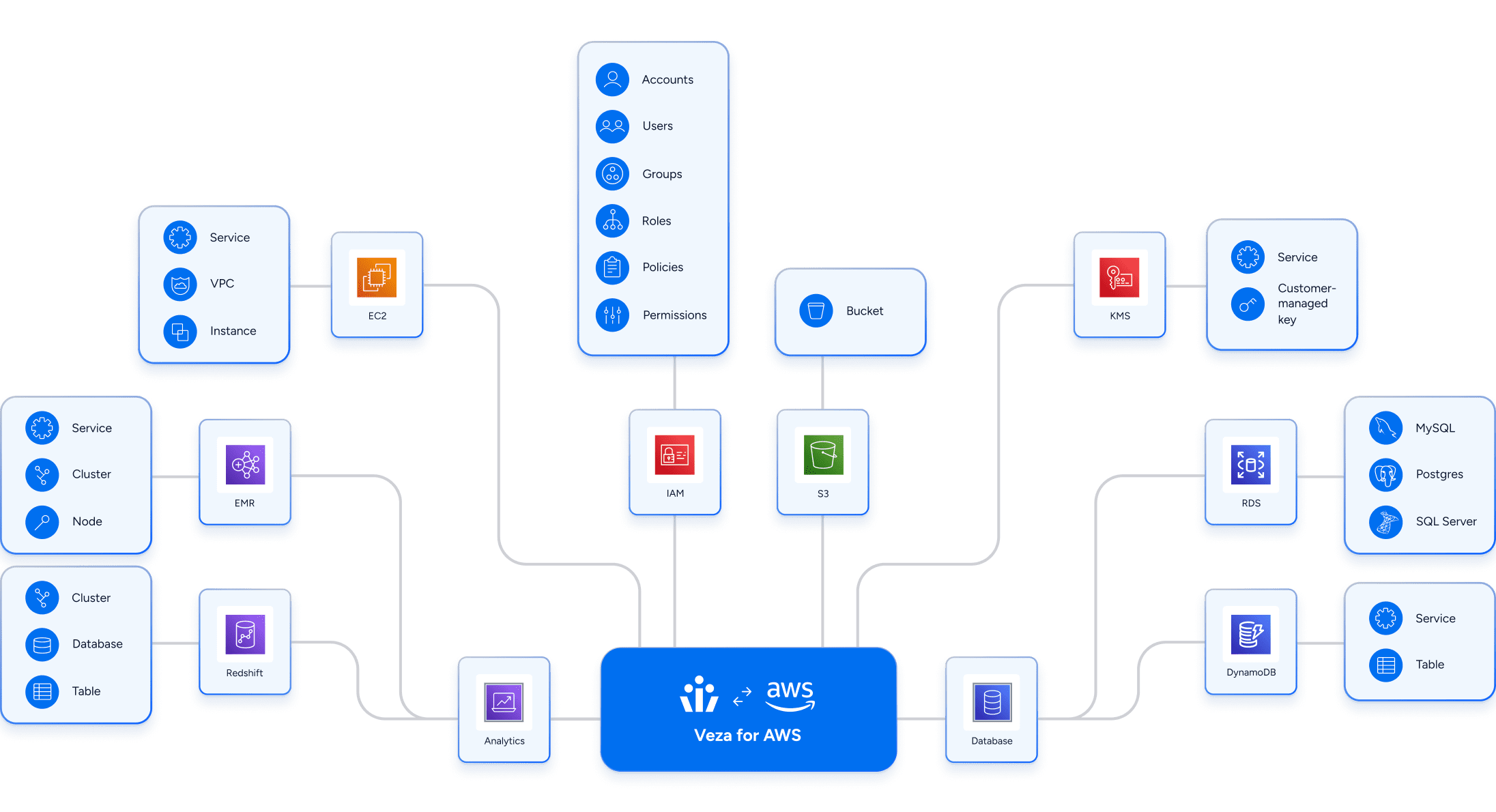
Full coverage of AWS services
Veza connects to the full range of AWS services for intelligent access across your cloud infrastructure, including AWS IAM itself, data systems like S3 and Redshift, Compute resources like EC2 and Lambda, and more.
14 hotel brands in a multi-cloud environment
Choice hotels uses Veza to secure access to data across 14 separate hotel brands using multiple cloud providers including AWS. Check out the case study to learn how Choice developed fine-grained access controls in AWS, and the ability to monitor for policy-violating permissions.


Veza brought something unique to the table that we had never seen before: the permission graph that lets us deeply understand the link between Okta and all of our different AWS accounts, to our databases, and Active Directory. We hadn’t seen anything like that and to be able to visualize that in basically 30 seconds is truly amazing.
Jason Simpson | Vice President of Engineering



