Why Veza?
The scope, scale, and complexity of access control has skyrocketed, creating new surface area for identity-based cyber threats. And with the frequency and cost of data breaches also accelerating, the stakes have never been higher.
Old tools, built on old technology are no longer enough. Join Veza’s Co-Founder and CEO Tarun Thakur to explore Veza’s vision for Intelligent Access.
Veza Dramatically Improves Risk Management while Cutting Costs

Slash Integration Costs and Complexity
Break free from expensive, slow integration services. Veza’s modern framework, out-of-the-box integrations, and self-service connectors slash onboarding costs and eliminate the need for costly consulting firms.
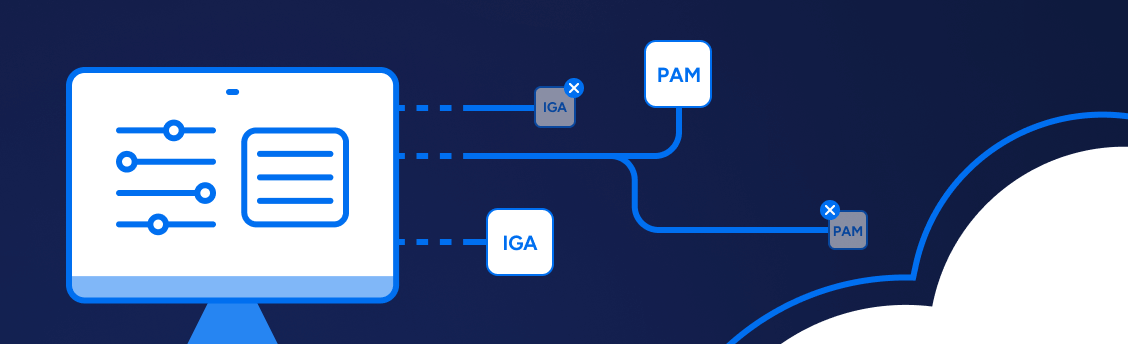
Cut Expensive IGA Software Spend
Consolidate identity management, replace outdated IGA systems, and cut software fees with a unified platform that simplifies and modernizes access governance.

Eliminate License Waste and Save Millions
Identify and eliminate unused licenses to slash waste and optimize spend—often recovering millions in savings that offset the cost of Veza.
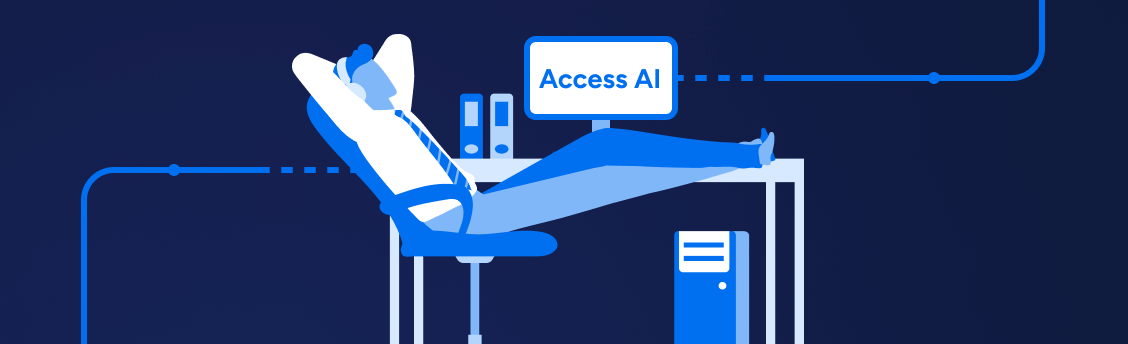
Accelerate Certification Campaigns with Access AI
Shrink setup and reporting times for access certifications from weeks to days with built-in automation, dramatically reducing manual effort and audit preparation work.

Instantly Answer Audit and Compliance Requests
Get answers to least privilege and access entitlement questions in seconds, without custom scripting or delays—ensuring you’re always audit-ready.









































Secure Access to Data Everywhere
and Anywhere
Time to value
Veza connects to your systems in minutes, not months, and delivers immediate value in visibility and remediation, with out-of-the box intelligence on key risks and misconfigurations. Unlike traditional IGA solutions, Veza does not need long deployments with professional services building integrations to your systems.

Enterprise Integrations Coverage
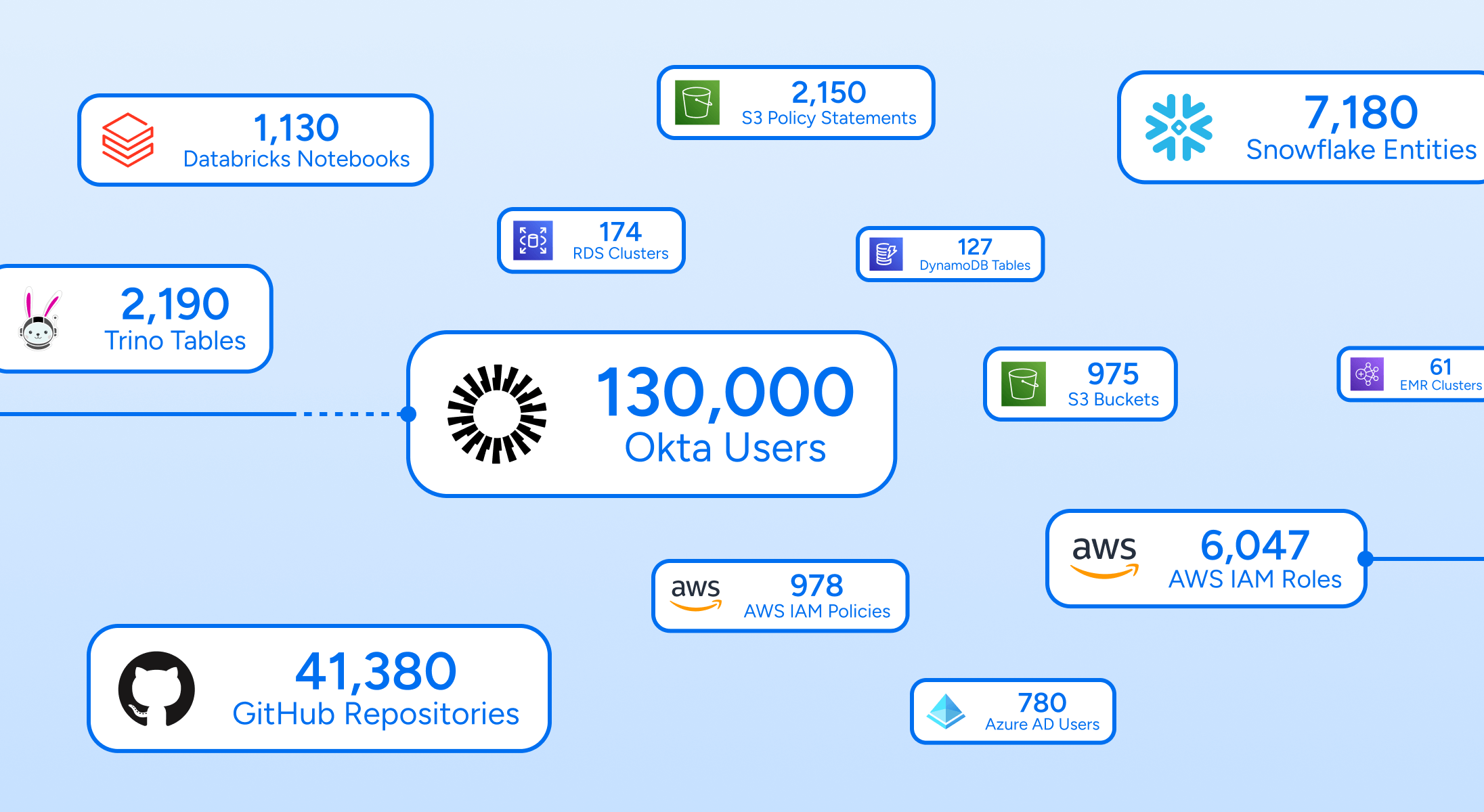
Only Veza can cover all your systems. Veza has hundreds of native integrations covering on-prem apps, cloud services, SaaS apps, and data lakes. To fill any gaps, Veza’s Open Authorization API (OAA) allows for building quick custom integrations to your own apps.
Proven Scale
Veza’s purpose-built graph infrastructure—already protecting over 30 million identities and 500 million permissions—is engineered to handle the scale and complexity required by large enterprise customers. We built the Veza platform to seamlessly support massive AI/ML-based capabilities, from access recommendations to universal search and more
Born in the cloud
Veza is a modern, cloud-native SaaS platform that introduces no admin overhead when deploying new updates. It also takes an API-first approach, which means that customers can build the power of Veza’s Access Graph into their own security apps.
Secure by Design
No agents, installers, ports, or firewalls. This out-of-band approach means no risk of downtime. Veza embraces industry best practices including independent penetration testing, data encryption at rest and inflight, strict role-based access controls, complete tenant isolation and zero external access by design. Veza is SOC 2 Type II, and ISO 27001 certified, demonstrating our dedication to security and compliance.
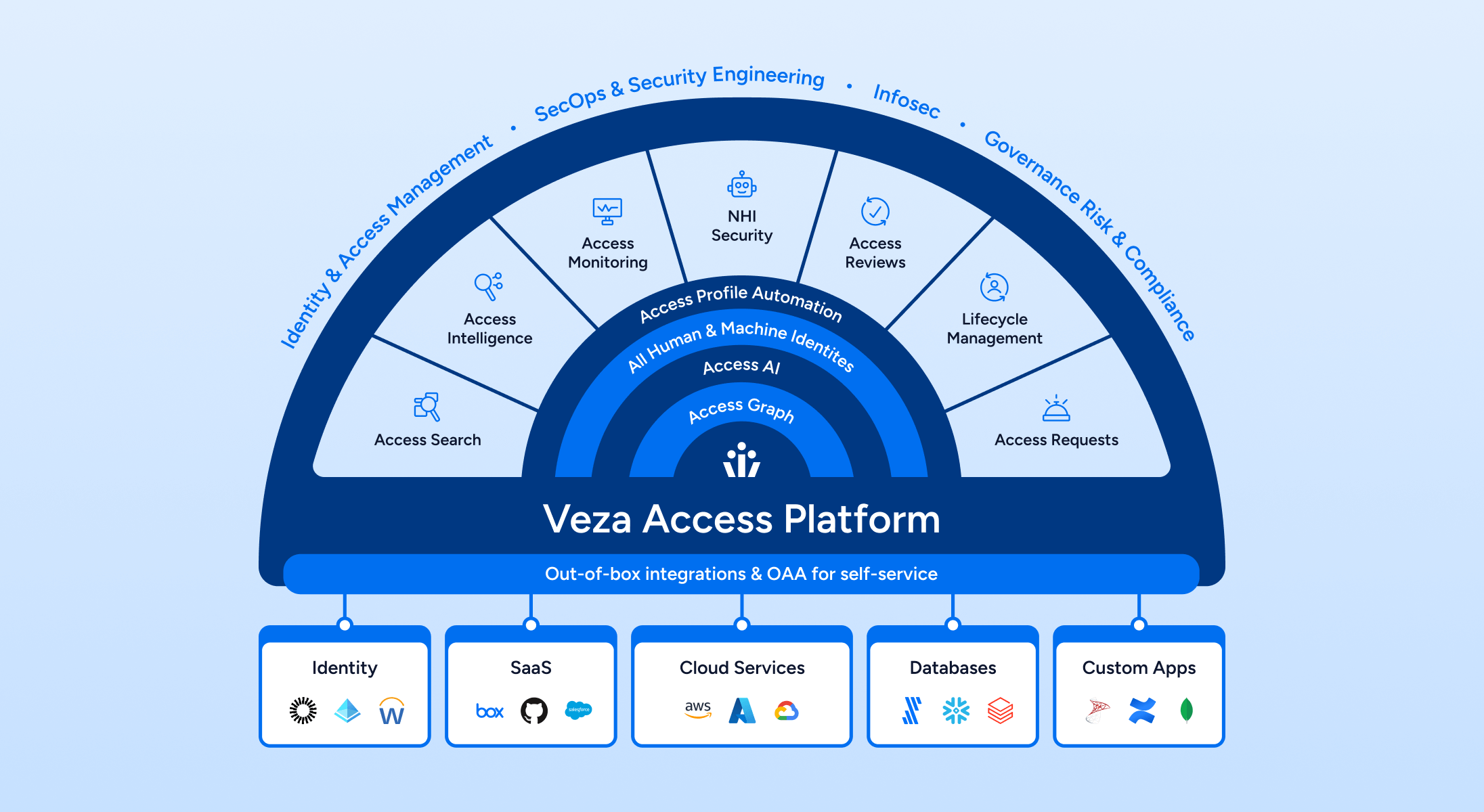
Access Platform
Veza provides a unified Access Platform, with native products offering access search, access intelligence, access monitoring, access workflows, lifecycle management, and access requests. API-first design enables a unified ecosystem experience with tooling like ServiceNow, Snowflake, AWS, and more. A unified experience helps organizations realize fast time to value, hard savings, and operational savings.