Veza for Okta
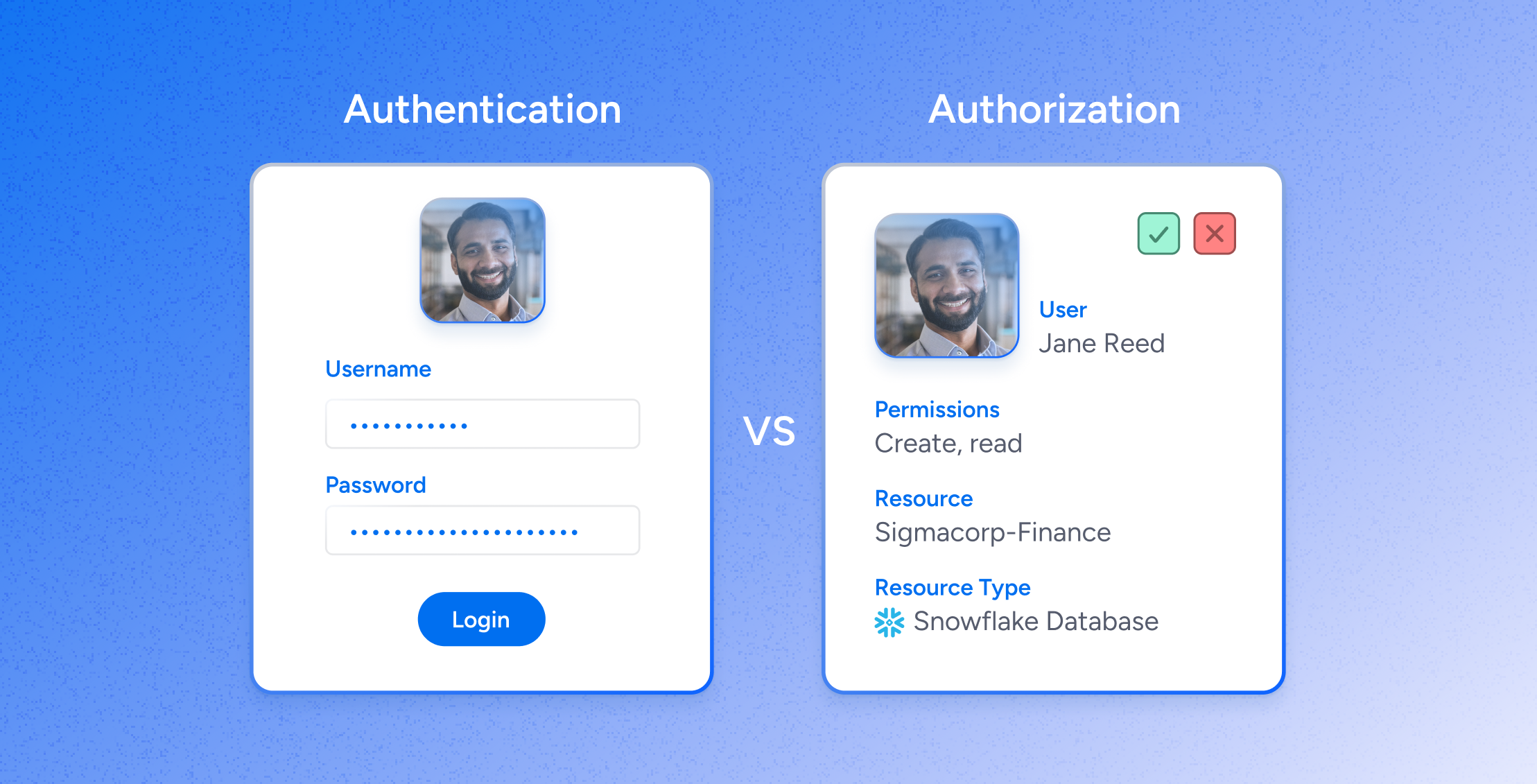
Veza bolsters Okta’s authentication capabilities with visibility into authorization—the granular permissions identities have to apps and data across your stack, allowing you to answer the question:
Who can take what action on what resources?
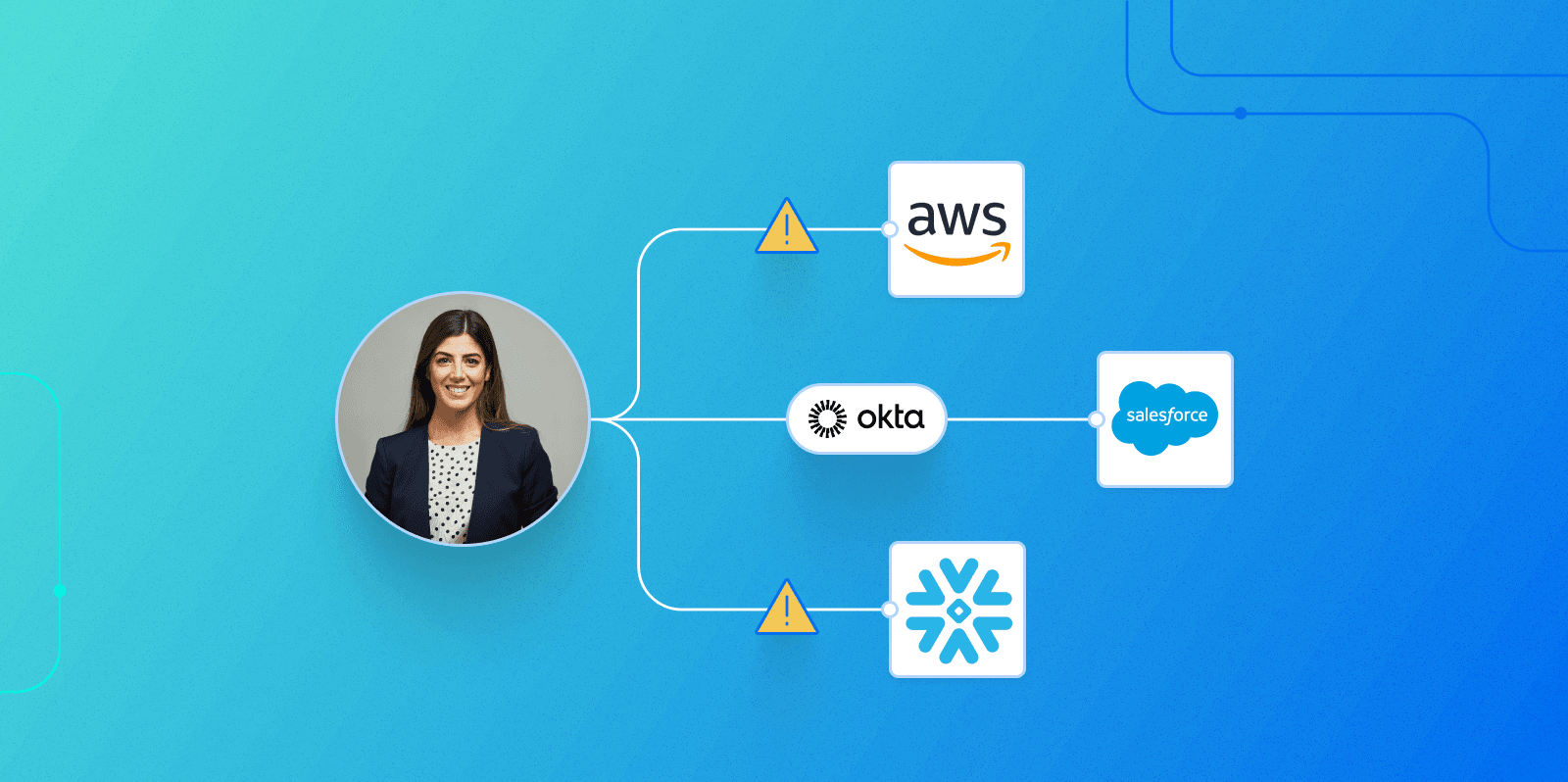
Identity security challenges in Okta
How Veza can help
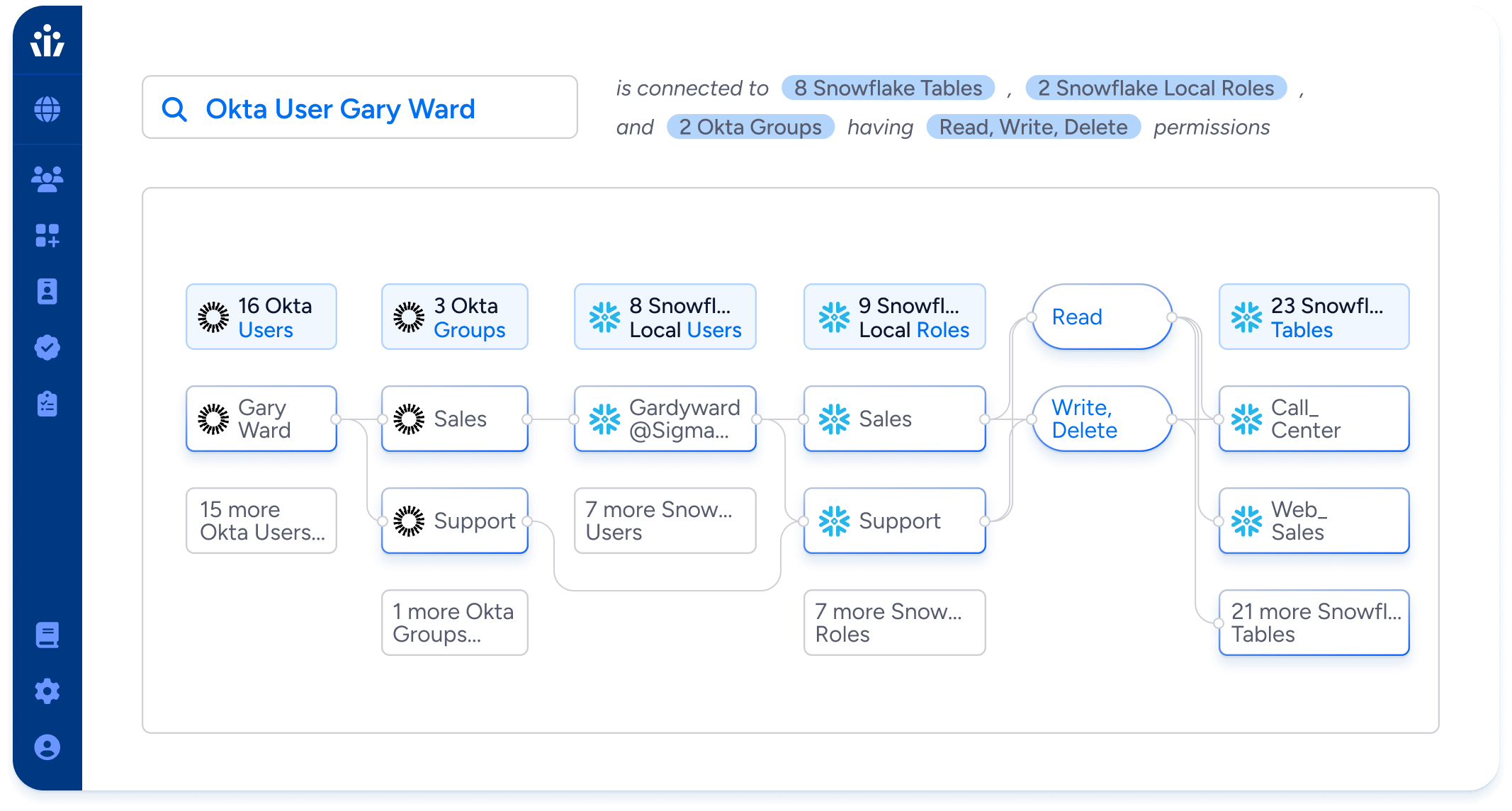
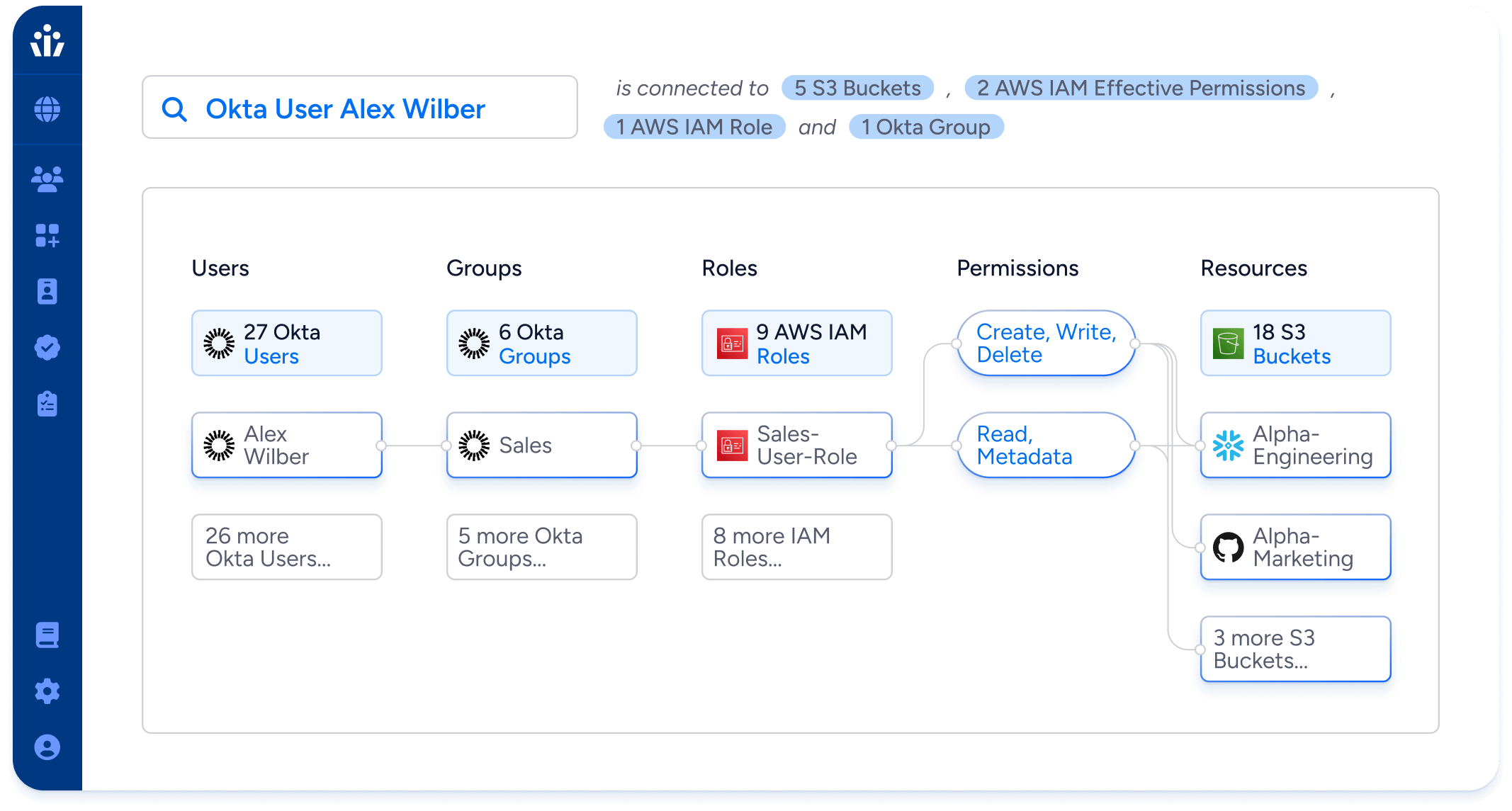
Veza is powered by its Authorization Graph, which gives organizations the ability to visualize authorization relationships between all identities and systems by connecting users, groups, roles, and permissions.
- Ensure effective & accurate provisioning: validate the outcomes of your group assignments in Okta to make sure that employees receive the permissions they need, and no more.
- Surface ungoverned identities: compare local accounts in your cloud providers, data systems, and SaaS apps against Okta data to find and remove ungoverned accounts circumventing your Okta provisioning processes.
- Identify misconfigurations & risks: deploy out-of-the-box reports and custom access queries to identify IAM misconfigurations, like admins without MFA, dormant users, and sovereignty violations, plus risk factors such as privilege drift.
- Reduced Risk: automate monitoring and remediation for misconfigurations, risks and best practice violations in Okta.
- Least Privilege: understanding the effective permissions each Okta group grants allows you to shrink your attack surface and make efficient provisioning decisions that avoid excessive or unnecessary permissions.
- Team Efficiency: bridge data silos and create a single control plane for identity governance, spanning not just Okta, but all identity providers, cloud infrastructure, data warehouses and on-premise systems.


Veza gives us both broader and deeper visibility into who has access to our data, and how they have access to that data, so we can trust and verify that personnel only have the access they need.
Puneet Bhatnagar | Senior Vice President, Cybersecurity


Veza gives us instant visibility into who has access to what data across all our cloud systems, providing a level of platform-agnostic, multi-cloud privilege visibility I hadn’t seen before. It’s truly playing a key role in our ongoing migration to the cloud.
John Forrester | VP, Information Security