Access Intelligence
Detect privileged users, dormant permissions, policy violations and misconfigurations with Veza’s 500+ pre-built queries. Veza shows you where to focus for maximum impact, and even creates tickets for remediation.
Why use Veza
Key Benefits
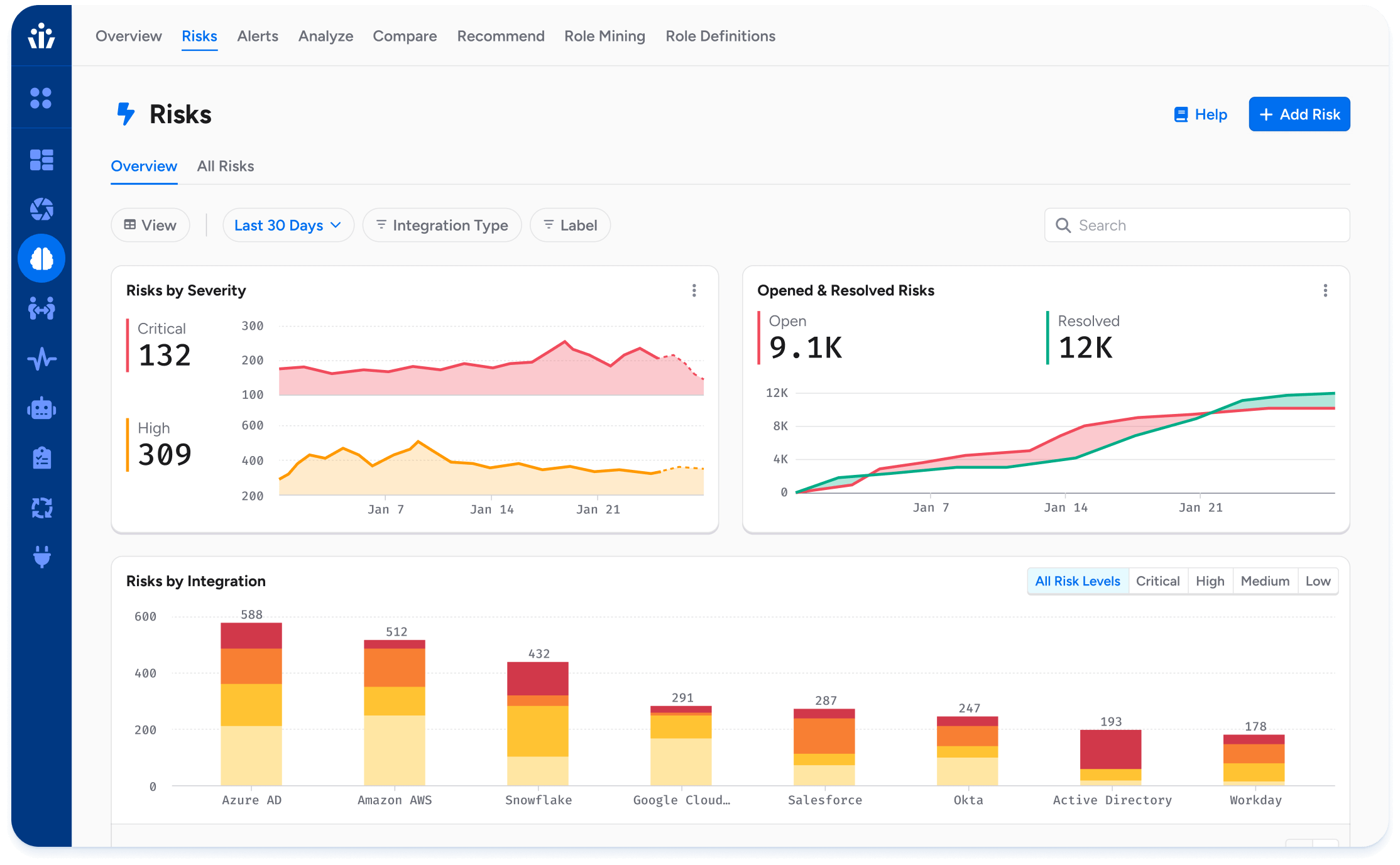
- Reduced risk: Surface and prioritize identities with the highest privilege, risk, or policy issues across all enterprise systems, without having to master the complex access models of systems like AWS IAM, Snowflake, and Salesforce.
- Least privilege: Reduce risks and simplify audits by continuously identifying and remediating identity misconfigurations, dormant permissions, and excess privilege.
- Team efficiency: Reduce manual, repetitive tasks by leveraging automation to detect and remove excess access. Delegate access decisions to line-of-business experts.
Key Features
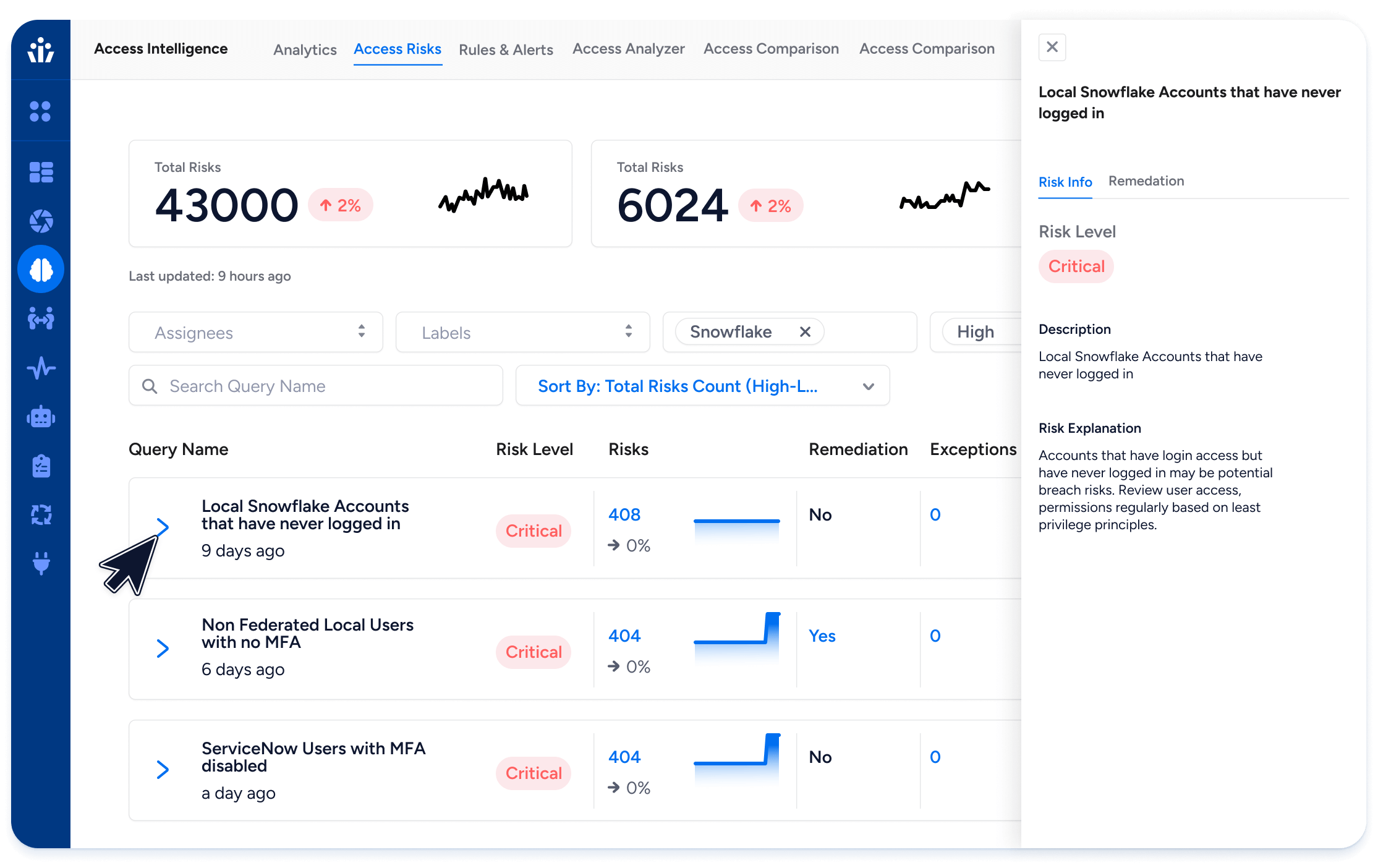
- Risks: Continuously scan permissions to identify deviations from best practices, security misconfigurations, and other anomalies. Veza recommends specific actions to resolve identified risks.
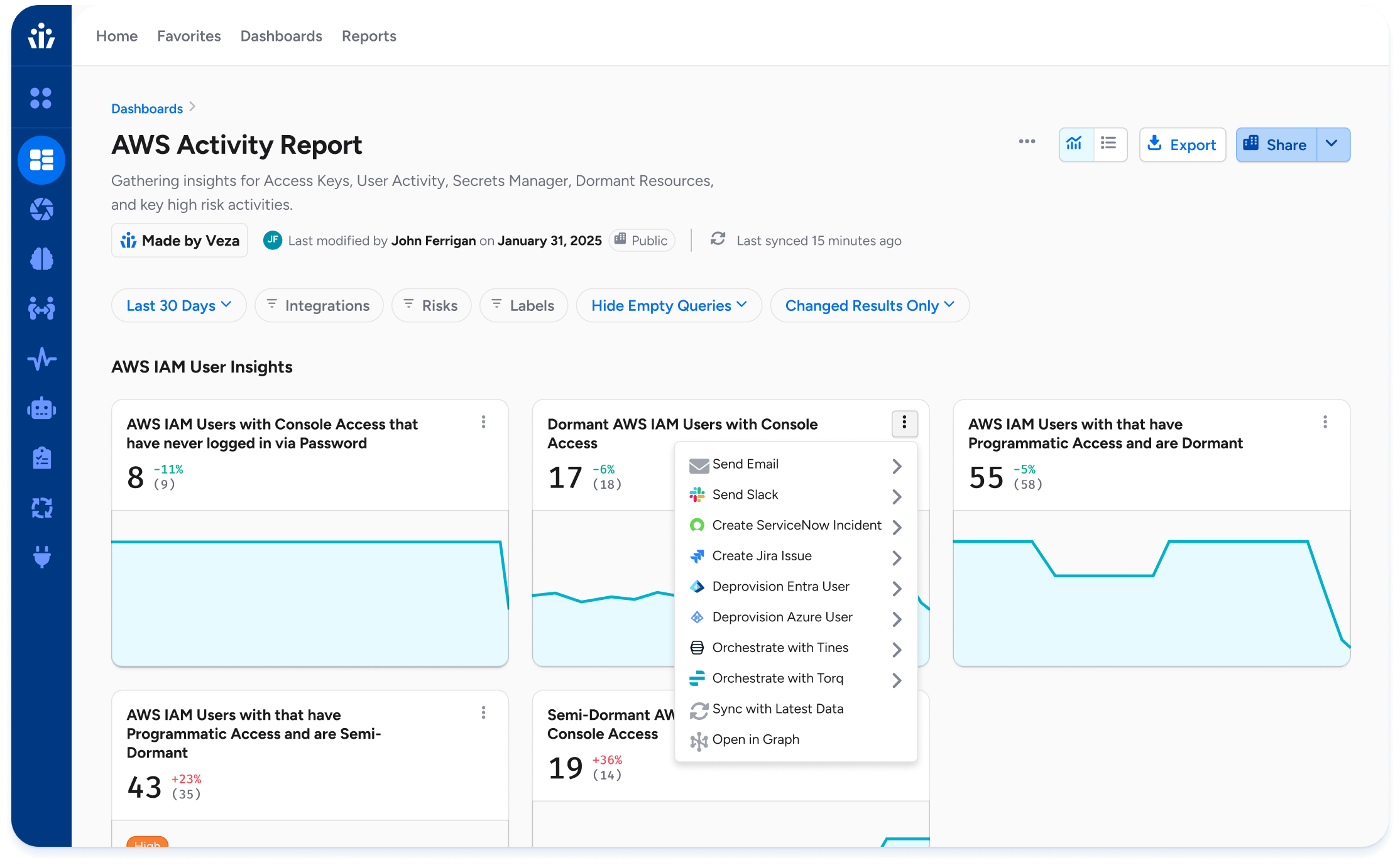
- Alert rules: Define automated actions based on the results of custom queries. Initiate alerts and remediation leveraging your ITSM tools such as Slack, Jira, ServiceNow, and more.
- Access Monitoring: CIEM monitoring to determine whether identities actually use the access they have to key data resources like Snowflake tables and AWS IAM.
- SaaS Misconfiguration Detection: SSPM monitoring to identify risky misconfigurations in SaaS applications.
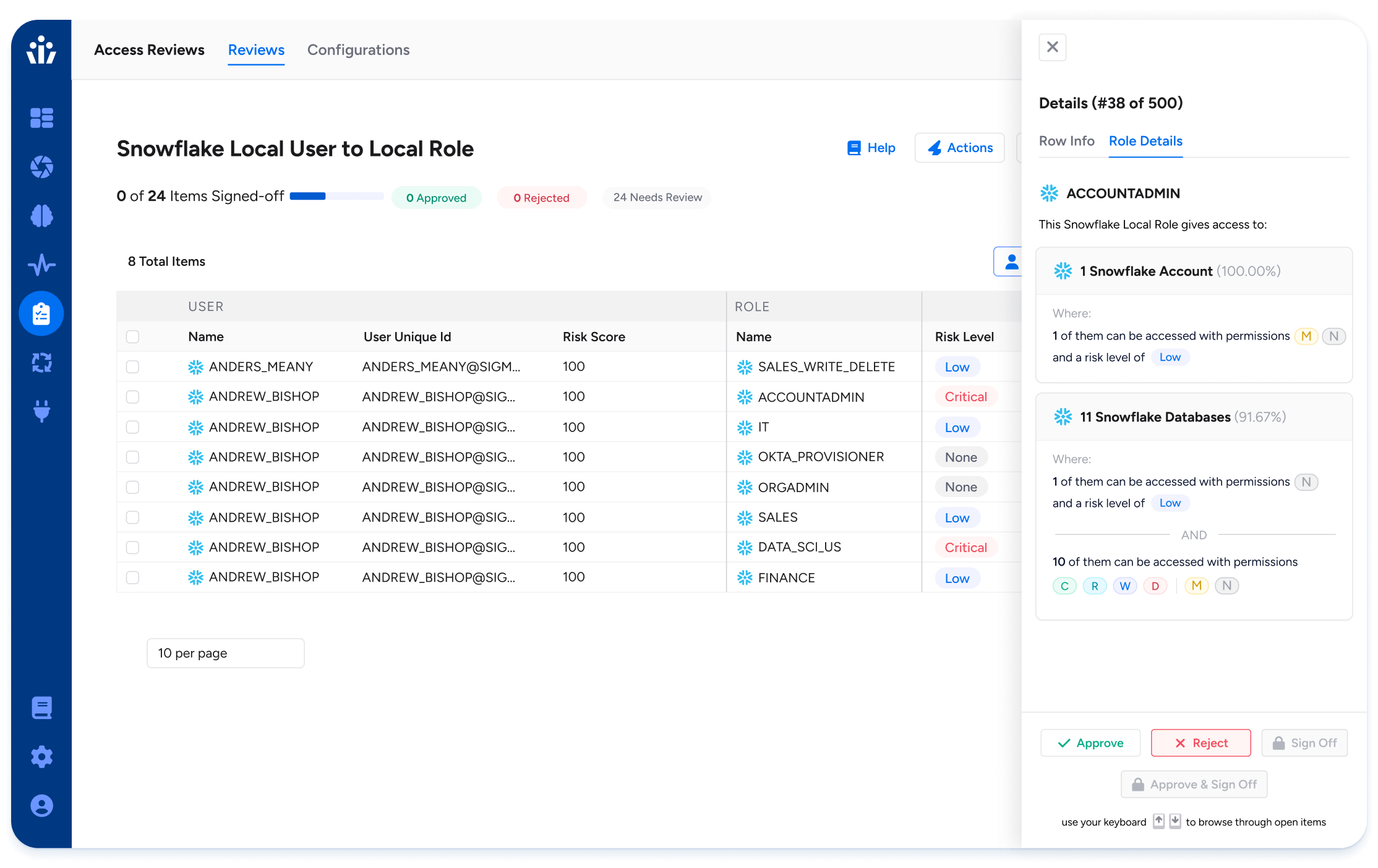
- Separation of Duties (SoD): Monitor access within and across systems to surface identities with potential SoD violations.
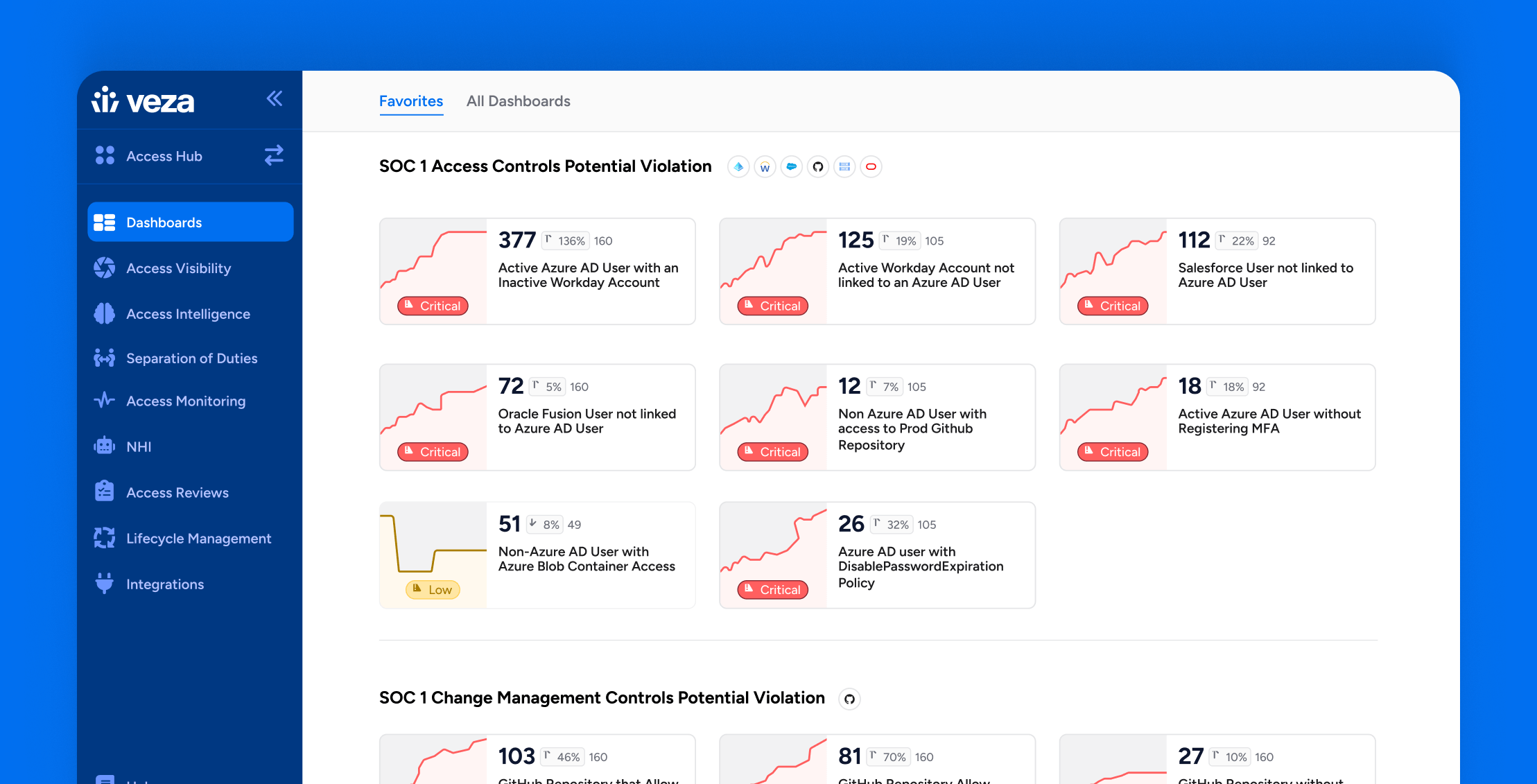
- Custom reports: Create custom reports and dashboards organized by data source, service, risk, or other.
- Dashboards: Out-of-the-box insights, including security-focused dashboards for vital systems (Salesforce, Snowflake, and GitHub) and summary dashboards tailored for CISOs and audit teams.