Access Search
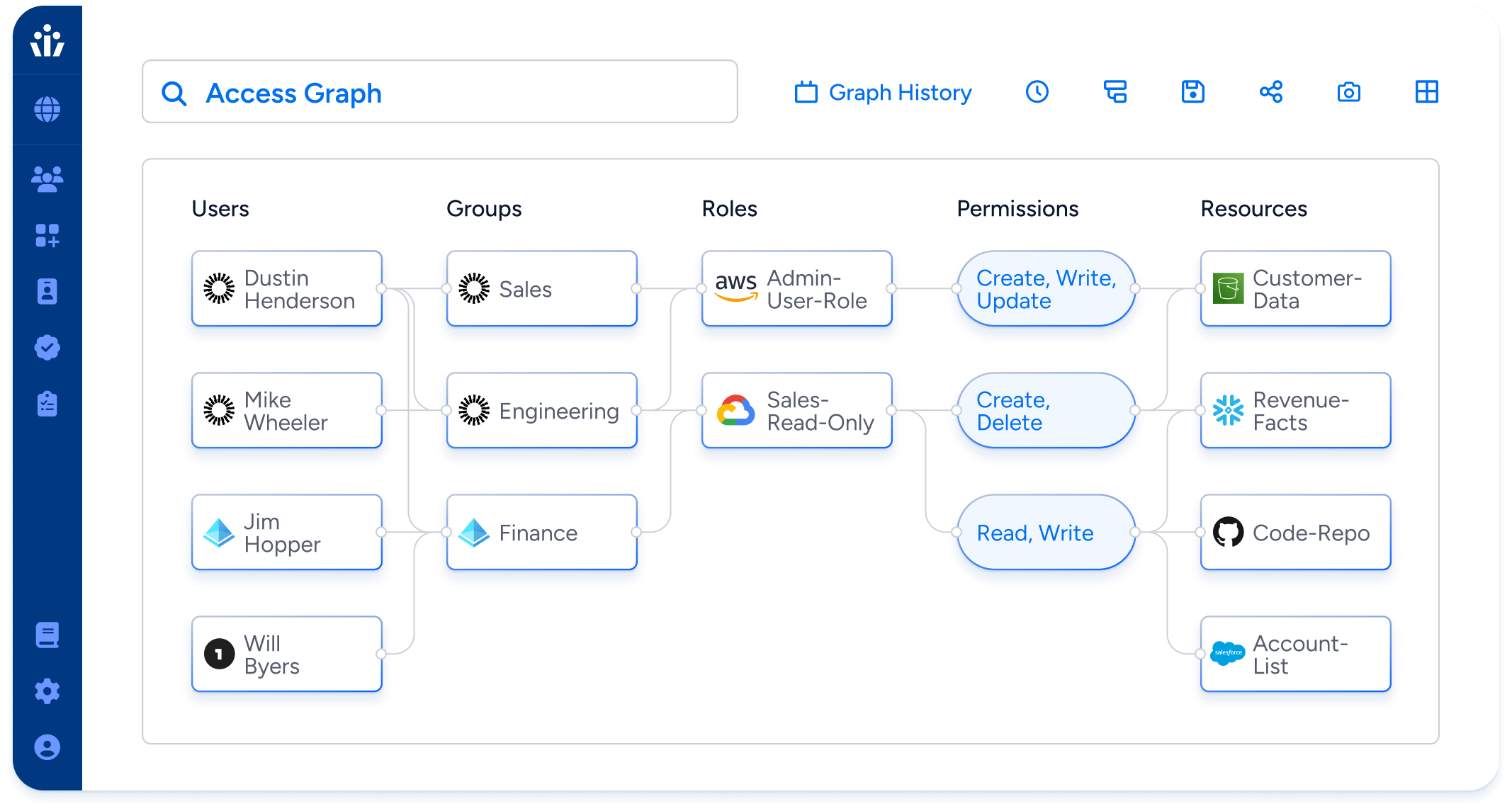
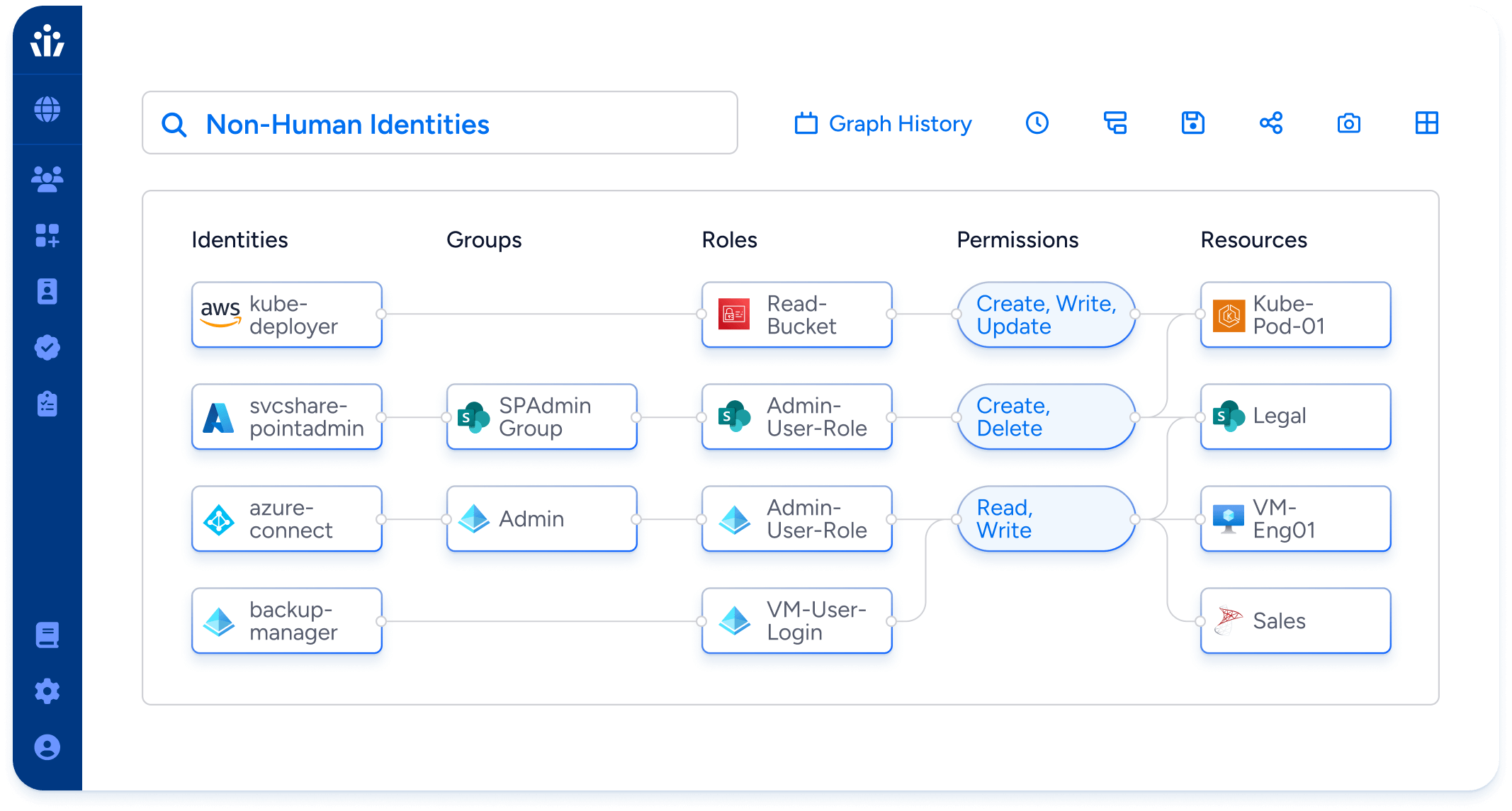
Visualize and control who has access to data across all enterprise systems. Only Veza reveals granular resource permissions for all identities, human & machine, helping security teams reduce risk before and after attacks.
Why use Veza
Key Benefits
- Least privilege: Visualize and control effective permissions for all identities in all systems, including apps, on-premise, cloud services, and data systems. Find and remove unneeded privileged accounts and unused access.
- Continuous compliance: Build queries and alerts to automatically scan for access that violates policies required for frameworks like SOX, SOC 2, NIST, and GDPR.
- Threat investigation: Quickly assess the detailed access of compromised identities to prioritize incident response.
Key Features
- Access Search: Visualize the current effective permissions for all identities in all systems, in near real-time. Covers apps, data warehouses, and all major cloud providers.
- Access AI: Search in natural language across identities, birthright groups, access roles, policies, permissions, and resources.
- Query Builder: Build rich queries with filtering, sorting, and complex operands spanning multiple systems. Leverage tags to search access to sensitive data types.
- Risk Heatmaps: Identify and prioritize risky permissions.
- Time Travel: Compare historical views of the Access Graph to surface changes in permissions over time.
- API Queries: Create and run queries via RESTful APIs to enrich data in your existing tools, workflows, and solutions.
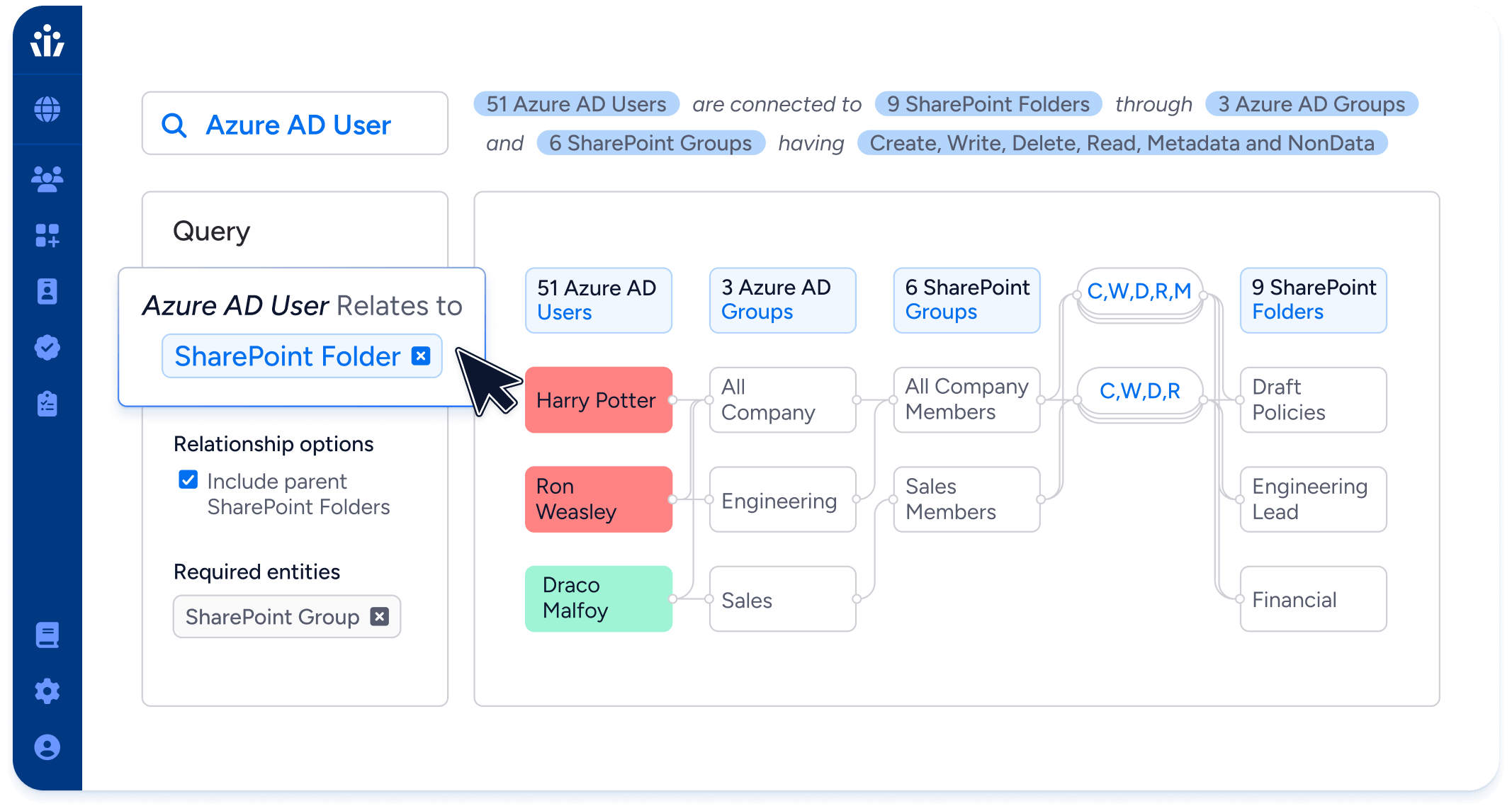
Veza Query
Language (VQL)
ADVANCED FEATURES
- Powerful queries: Track the relationships between any source and destination nodes in Veza’s Access Graph, and even specify relationship paths.
- Easy to learn: VQL utilizes familiar SQL conventions so you can pick it up fast. You’ll be forming complex queries and getting results in minutes.
- Focused results: Filter query results by entity properties to focus on what you’re looking for in a large data set. Supports a wide range of operators.
