80% of cyberattacks rely on identity based techniques – stolen credentials, MFA workarounds, privilege abuse, and access creep. Traditional identity tools across PAM, IGA, and IAM were not architected to help organizations answer the question: who can take what action on what data?
Beyond IAM era is here. 2024, The Year of Identity. Security leaders everywhere are looking evolve their IAM toward an identity-first approach that puts identity-based controls at the heart of enhancing their cybersecurity posture: reducing risk, delivering digital transformation and business value.
In today’s fast-evolving digital landscape, ensuring seamless security and least privilege across your organization is more crucial than ever. That’s why we’ve taken a significant leap forward to empower your teams with end-to-end visibility and control over user access and security policies – from HR systems like Workday to Identity Providers (IdPs) such as Azure AD, AD and Okta, and now, extending into Zscaler cloud security platform.
🛡 Full integration with Zscaler Internet Access is now live! 🛡
What’s New?
- Comprehensive Visibility: See user and service accounts detailed roles and access rights in Zscaler and correlate them against your HR systems and IdPs to keep access up to date.
- Permissions Alignment: Ensure every user is assigned to the correct geographical or departmental policies in Zscaler, aligning with their roles and responsibilities as defined in Azure AD or Okta and remediate incorrect access .
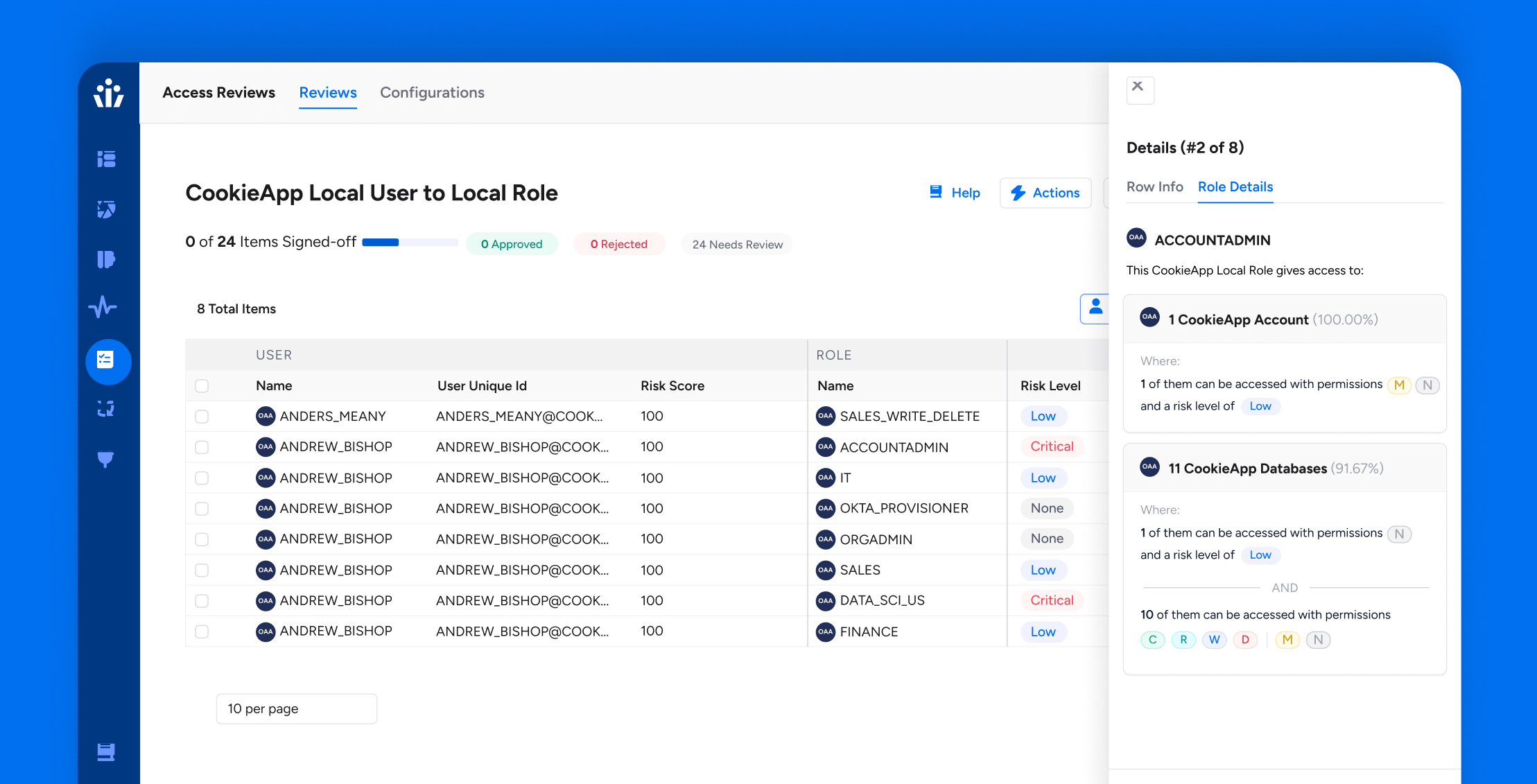
- Access Reviews Powered by Automation and Intelligence: Simplify access reviews and compliance audits with our enhanced auditing capabilities. Stay ahead of the compliance curve with detailed, easy-to-understand audit trails.
- Privileged Access Monitoring: Identify and manage privileged accounts and right-size their permissions.
Why This Matters?
- Enhanced Security Posture: Tighten your security by ensuring the right people have the right access, reducing the risk of internal and external threats.
- Streamlined Compliance: Meet regulatory and compliance requirements with ease, thanks to comprehensive and integrated audit trails.
- Increased Efficiency: Save time and resources by automating role assignments and policy enforcement, ensuring users are always correctly provisioned across your entire tech stack.