In my journey across the cybersecurity and digital trust landscape, I’ve always been fascinated by the actors that don’t take a physical seat at the table, yet hold keys to the kingdom: non-human identities (NHIs). From my experience, these faceless entities—API keys, service accounts, service principals, AI models, chatbots, vaults, KMS keys, and more—are the silent cogs in our digital machinery. Their management is not a mere technical routine; it’s a strategic imperative that defends the front lines of our cyber defenses.
What is Non-Human Identity Management?
Non-human identity management is the discipline of assigning, securing, and overseeing the digital credentials and permissions of automated actors—software, applications, or devices—within IT environments (cloud, multi-cloud, hybrid cloud, etc.). These identities are integral to cloud services, automated processes, and service-oriented architectures. In aggregate they can collectively have deep and broad access to many systems and resources, further widening an already challenging identity attack surface. Veza stands at the forefront of this domain, offering innovative access intelligence, access governance and access lifecycle solutions tailored for the nuanced needs of NHI management.
Why Non-Human Identity Management matters
The significance of NHIs has only magnified with each technological leap—cloud computing, DevOps, robotic process automation (RPA), Internet of Things (IoT), and new Gen AI advancements. They are the unsung heroes that ensure seamless operations. Yet when compromised, as I have seen in too many cases, they can silently springboard an adversary into the heart of our most sensitive operations. Beyond security, I also contend that NHI management is about preserving operational integrity, compliance, and the efficiency of our data and digital endeavors.
Two examples come to mind of breaches where NHIs were a significant contributor to the initial incident, entry or spread:
- SolarWinds – In this sophisticated supply chain attack, attackers compromised the infrastructure of SolarWinds, then used the access afforded by NHIs (in this case, software updates) to infiltrate customer systems.
- Twitter Bitcoin Scam – Although primarily involving the compromise of high-profile accounts, automated bot accounts were used to amplify the scam, demonstrating how NHIs can be involved in the spread of cybersecurity incidents.
Key use case scenarios for Non-Human Identity Management
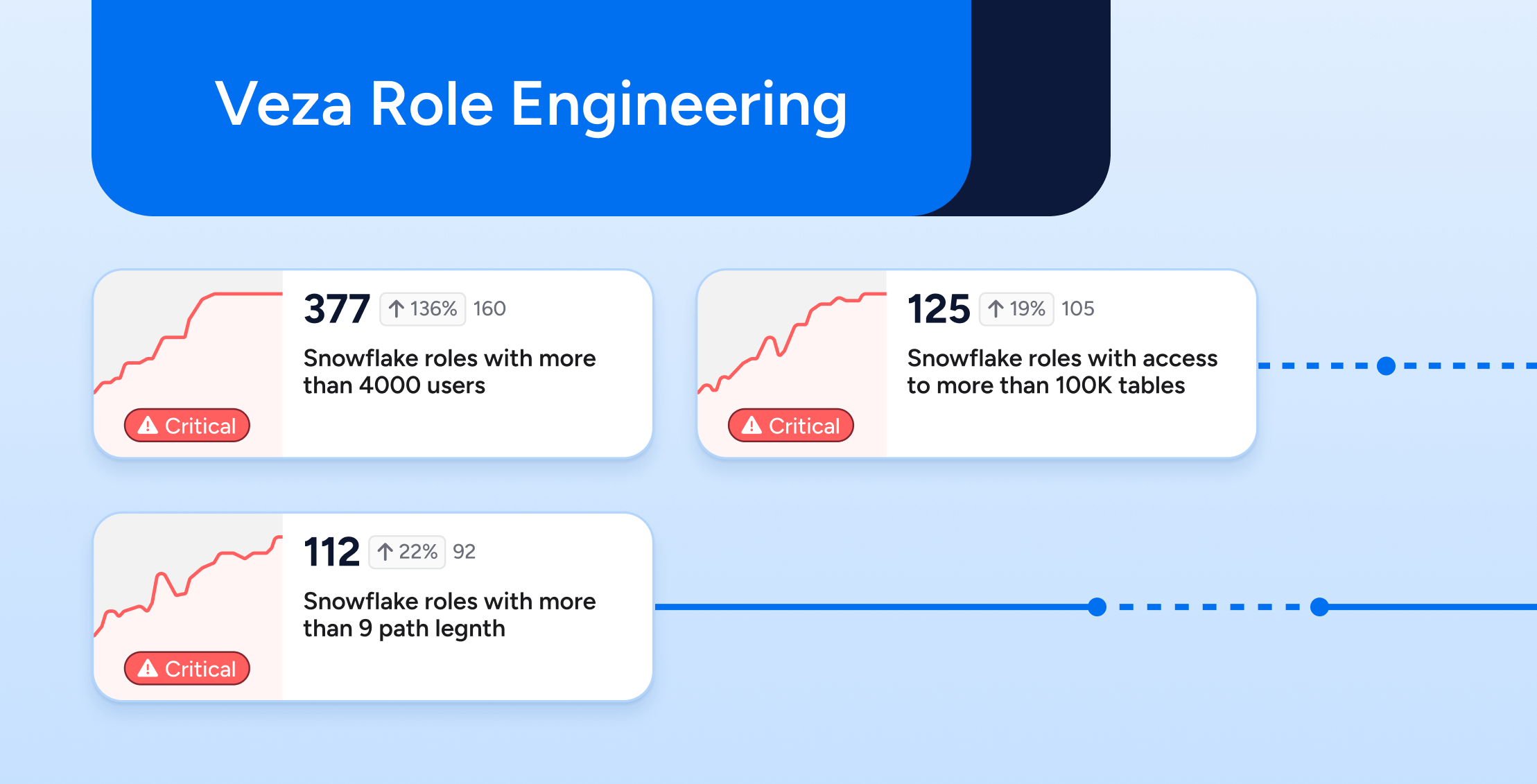
Access Visibility
From what I’ve experienced, organizations often lack a comprehensive inventory of NHIs, which can be dangerous. This includes understanding which resources they can access and the actions (permissions, entitlements, etc.) they’re authorized to perform. Veza’s access control platform echoes my conviction, providing unparalleled visibility and ensuring no NHI falls through the cracks.
Access Intelligence
Having long advocated for the intelligent analytics of digital entities, I’m impressed by Veza’s Authorization Graph. It’s the disruptive innovation that I see as crucial for mapping the complex web of NHI permissions and enabling informed, proactive or even real-time decisions.
Access Monitoring
Continuous monitoring of NHIs is crucial for detecting anomalous behavior (access creep, privilege drift, privilege elevation, lateral movement, etc.) that may indicate a security breach or misconfiguration. Veza’s platform offers continuous monitoring capabilities, providing automated rules, alerts and insights into NHIs’ activities. This enables organizations to quickly identify and mitigate issues before they escalate into full-blown security breaches.
Access Governance
Governance must transcend the checkbox compliance culture—where we craft tailored policies that adapt to the unique rhythms of NHIs across the enterprise ecosystem. Veza’s governance and access lifecycle model resonates with my philosophy of “adaptive” security, where NHIs are governed by dynamic policies that reflect their evolving roles and the shifting cyber landscape. This nuanced approach to governance is essential for fostering a resilient digital environment where security and compliance are seamlessly integrated into the operational fabric of an organization. Through Veza’s platform, governance becomes a living process that not only mitigates risks but can empower NHIs to contribute to the organization’s overall security posture.
Conclusion
In modern data, digital and technology environments, non-human identities (NHIs) are as critical to operational integrity and security as their human counterparts. Technology leaders recognize the necessity of a disciplined approach to managing these digital entities, which requires robust visibility, intelligent decision-making, and rigorous governance to ensure transparency and control.
Veza’s solutions embody the digital trust principles I support—comprehensive management tools that align with the strategic goals of securing and streamlining modern technology infrastructure. With a focus on practicality and quick time-to-value, Veza’s platform streamlines the access visibility, access intelligence, access monitoring and access governance of NHIs, helping to mitigate risks and uphold operational continuity in the ever-evolving digital landscape.
To discover how Veza’s platform can enable, enhance or fortify your NHI management, from the ground up, visit veza.com or schedule a demo today.
Further reading and references:
- Cloud Security Alliance: Machine Identity in Cybersecurity and IAM
- Cybersecurity Tribe: An Introduction to Non-Human Identity Management (NHIM)
- Security Magazine: Non-human identities: Secure them now, not later
- LinkedIn Advice: How do you manage the identity lifecycle of non-human entities, such as bots, IoT devices, and APIs?
- TechTarget: SolarWinds hack explained: Everything you need to know
- Mitnick Security: The 2020 Twitter Bitcoin Scam: How it Happened and Key Lessons