Identity
Reimagined
Reveal, Visualize, and Secure Your Identity Entitlements Everywhere
























Identity Reimagined
2026 State of Identity & Access Report
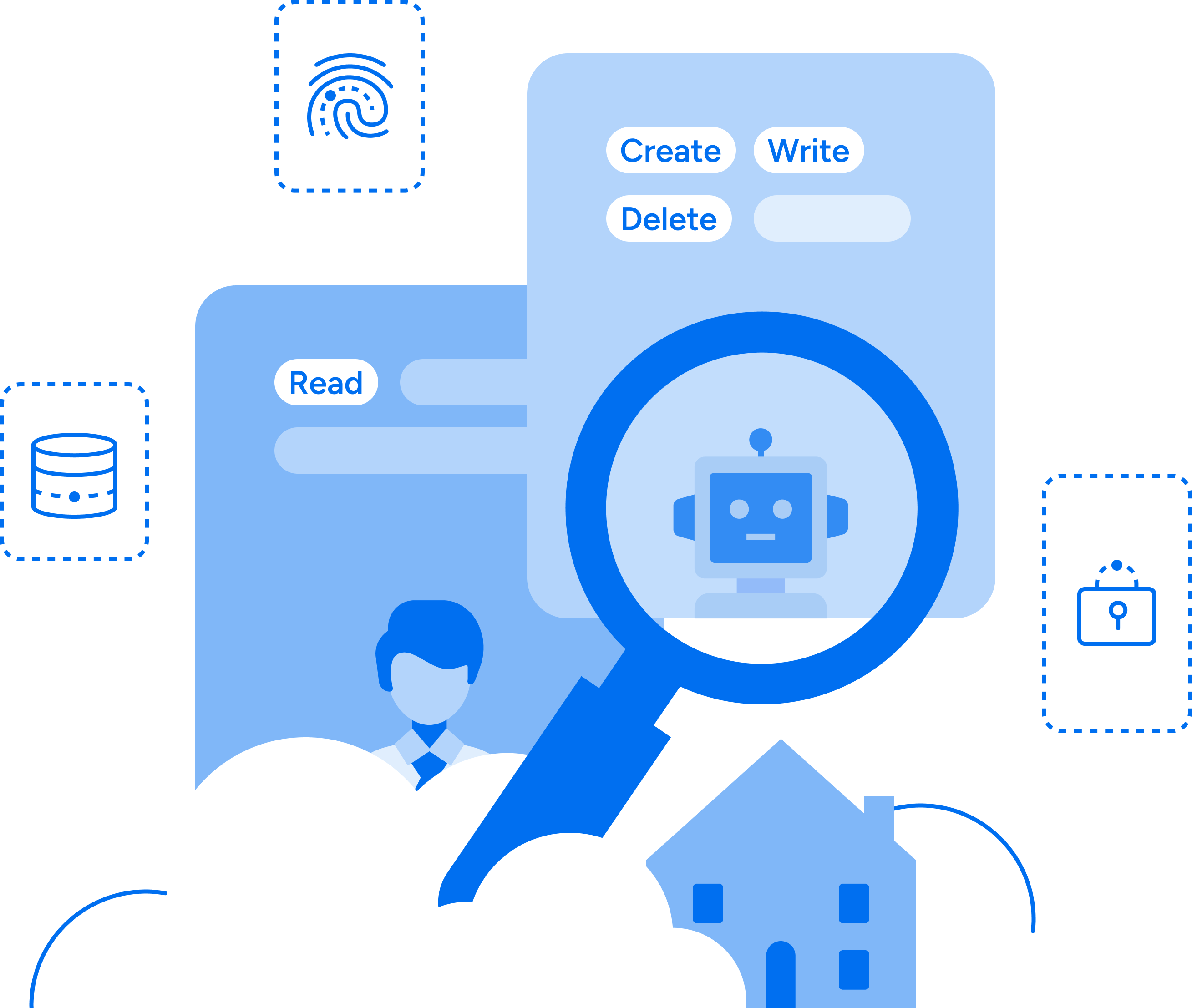
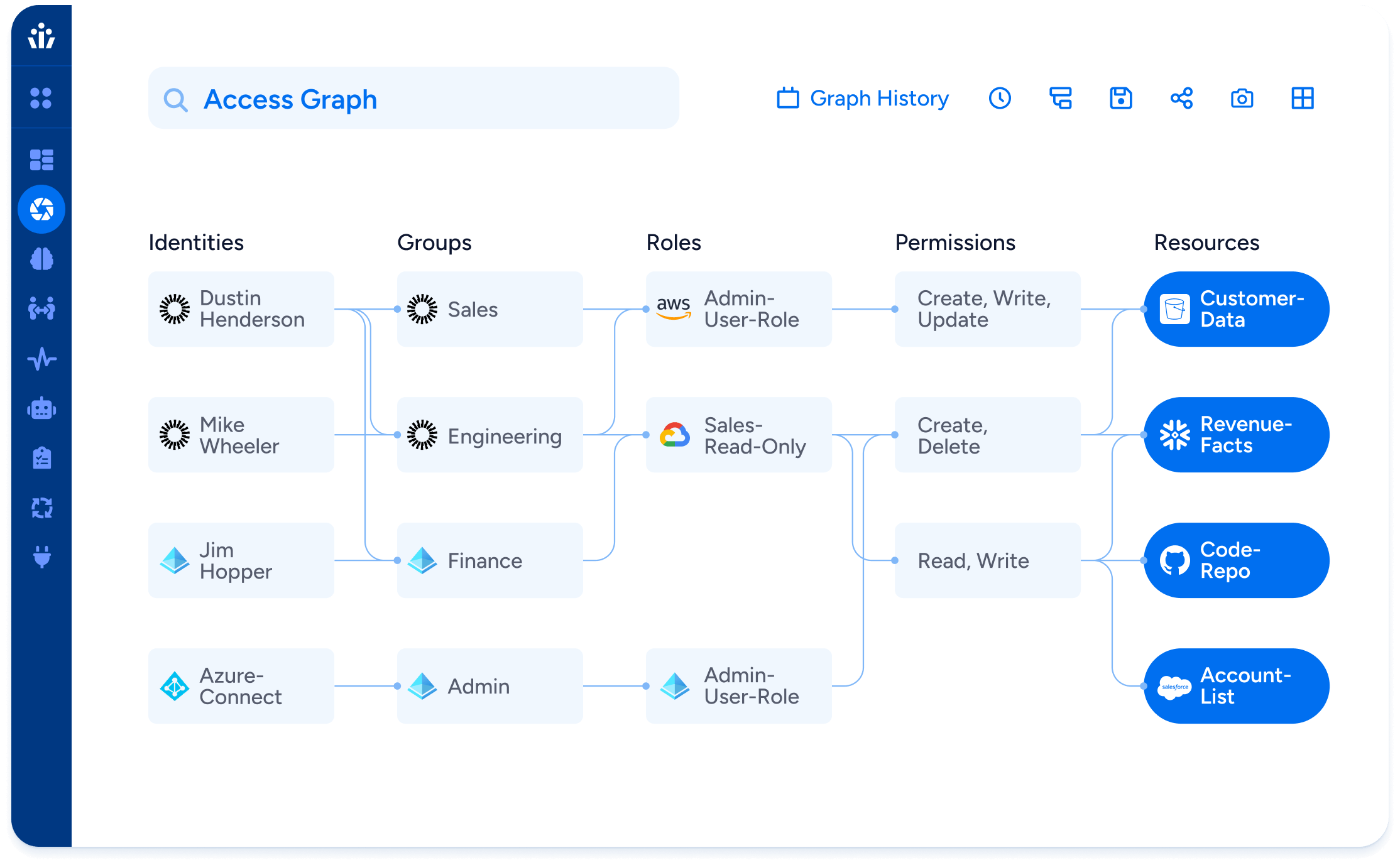
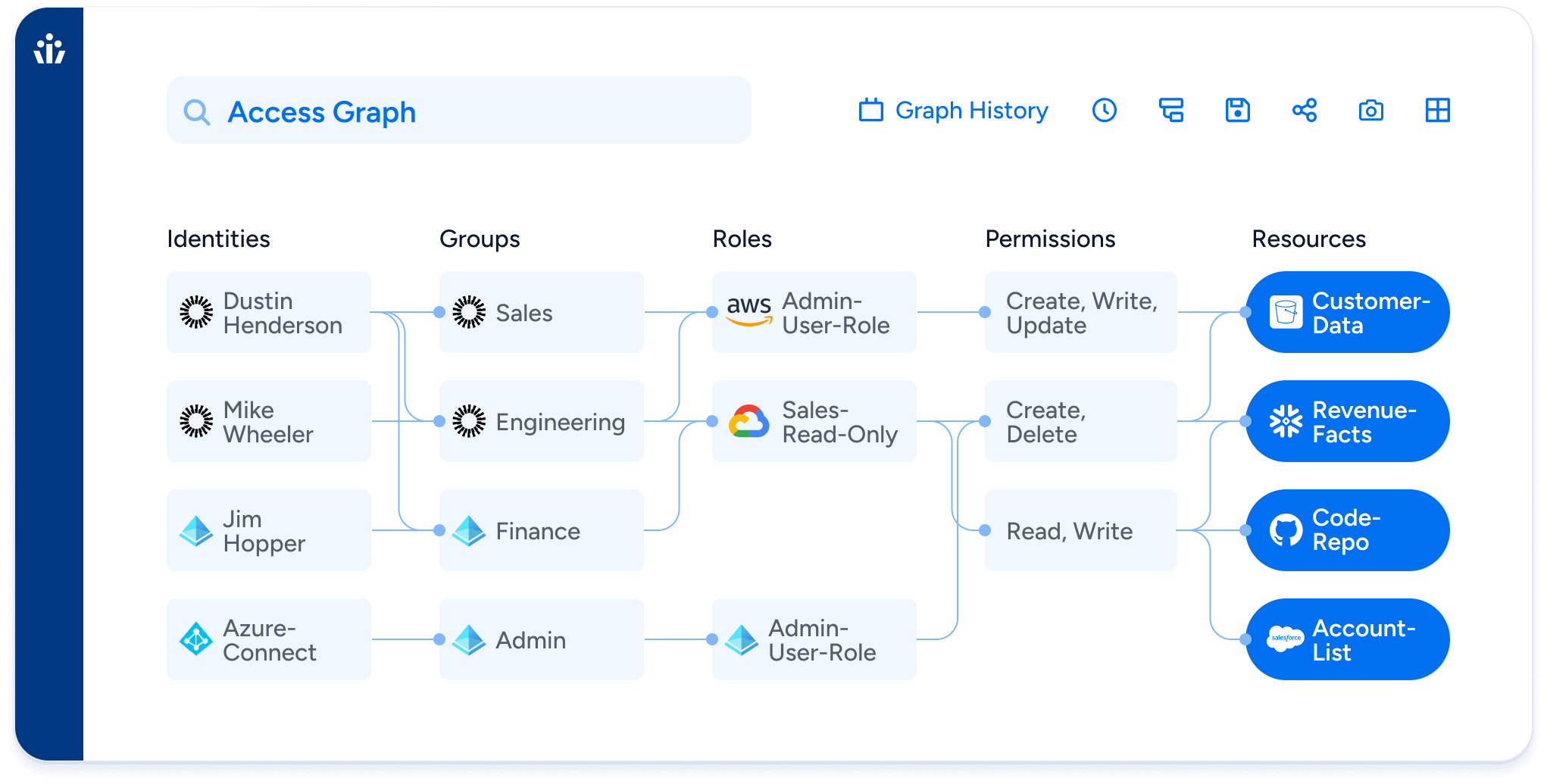
With billions of permissions to manage, security and identity teams are struggling to maintain and enforce the principle of least privilege across their organizations. Excessive privileges, dormant accounts and over permissions are running rampant all across. The latest State of Identity and Access Report by Veza illustrates these threats and underscores a key tenet: identity risk is everywhere, and it’s growing faster than most teams realize. Every security leader should study this report and use it to inform their roadmap of understanding and countering these threats before they become impossible to address effectively.
Enterprise wide Access Governance with Phil Venables
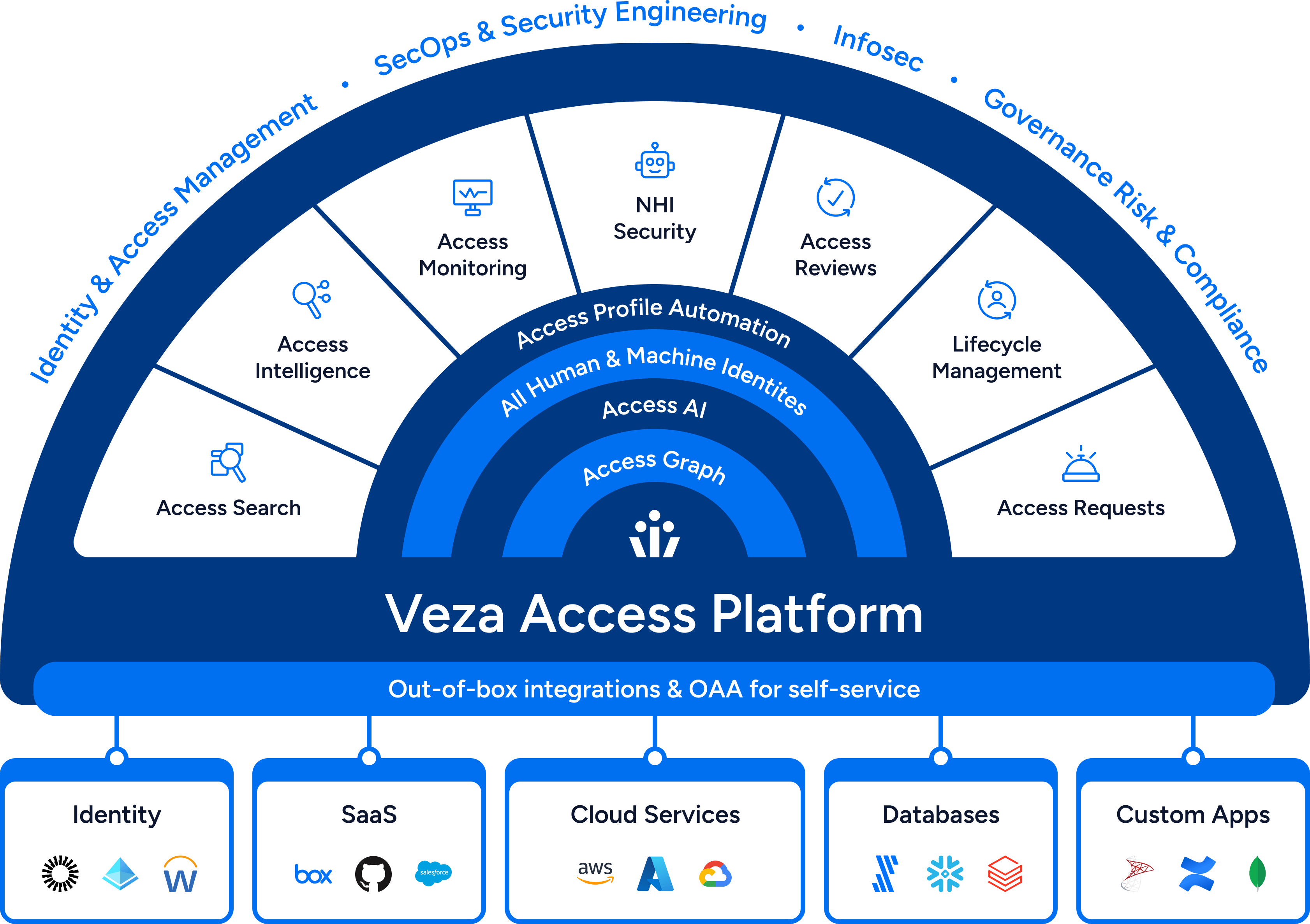
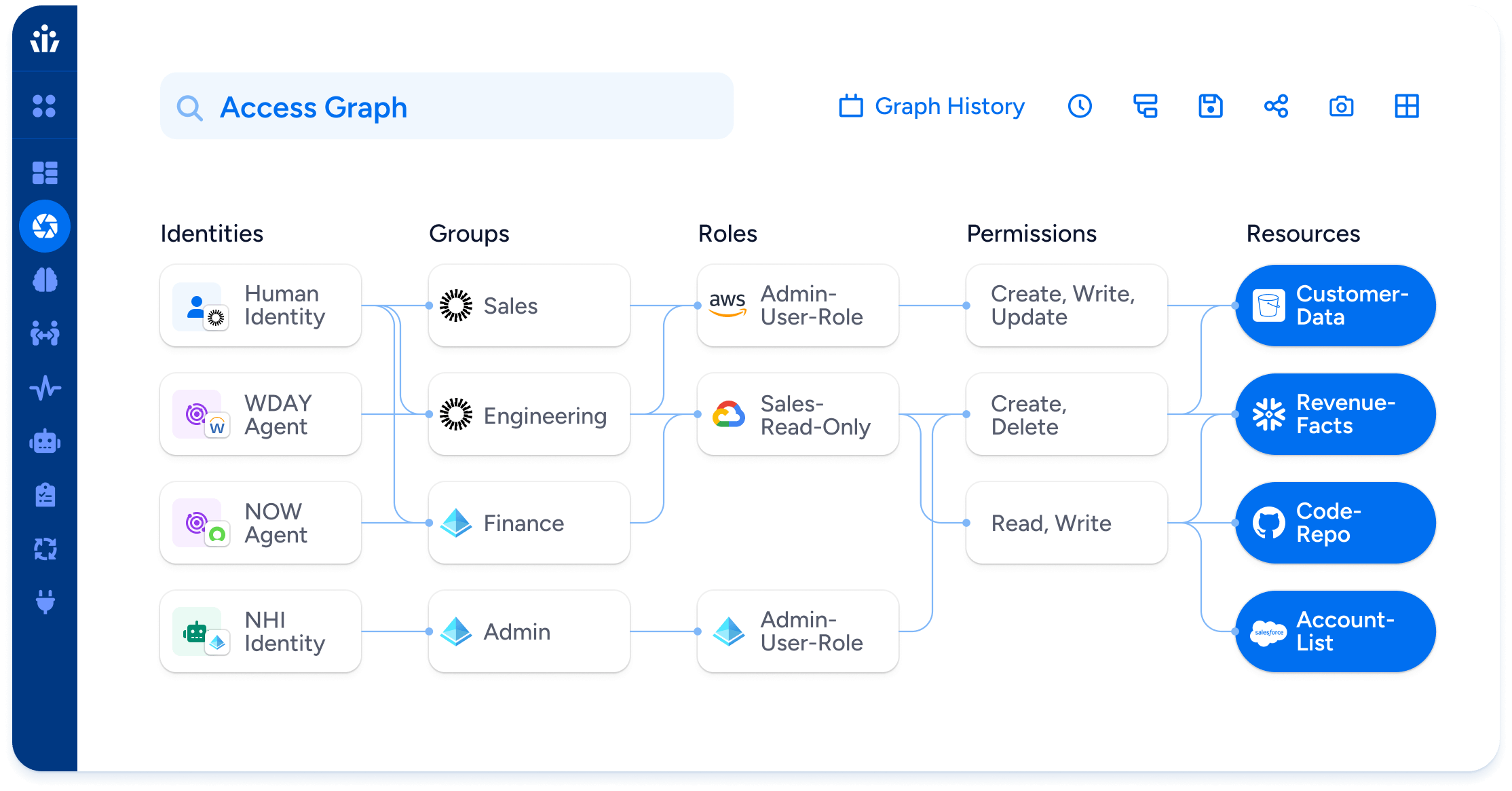
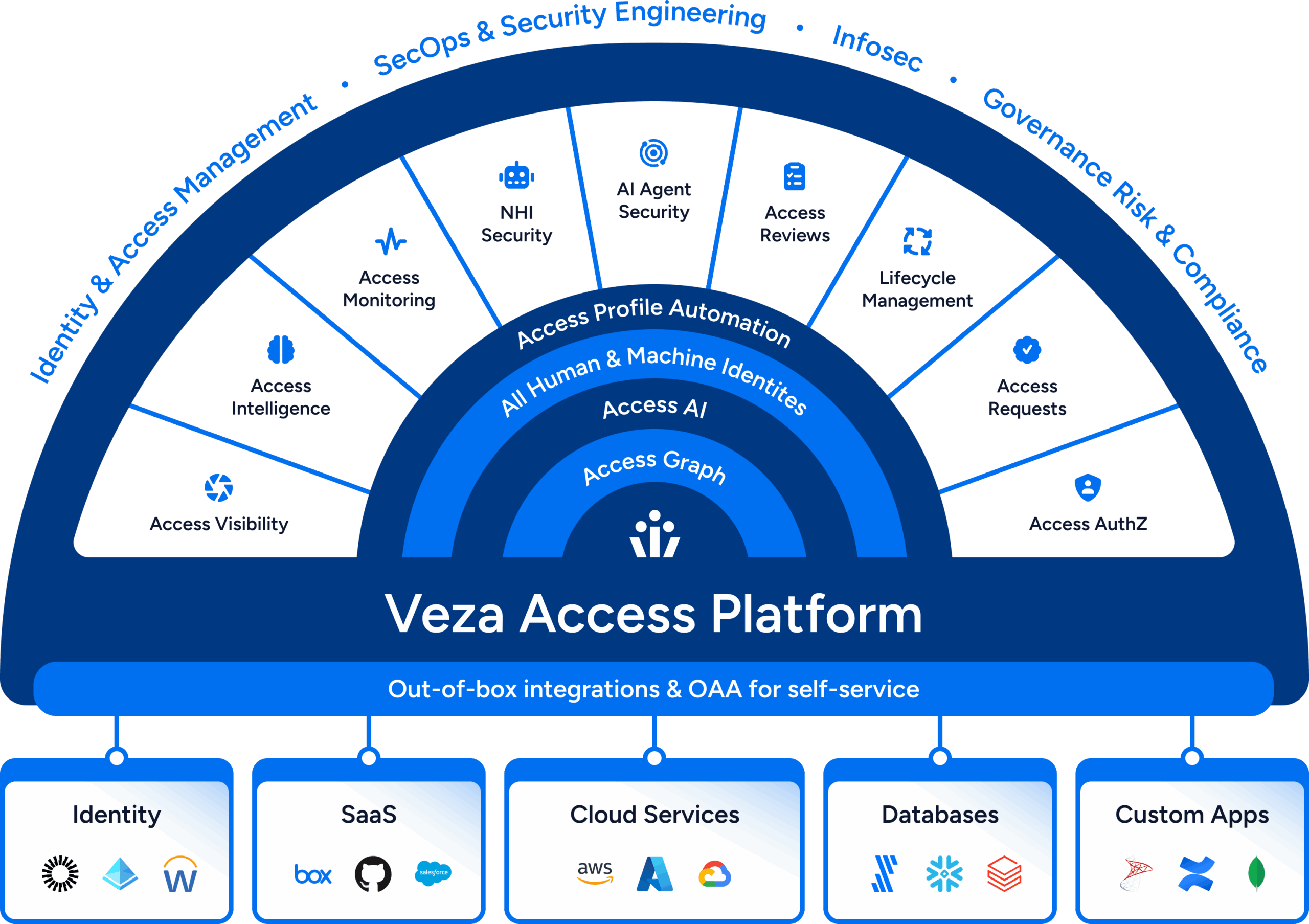
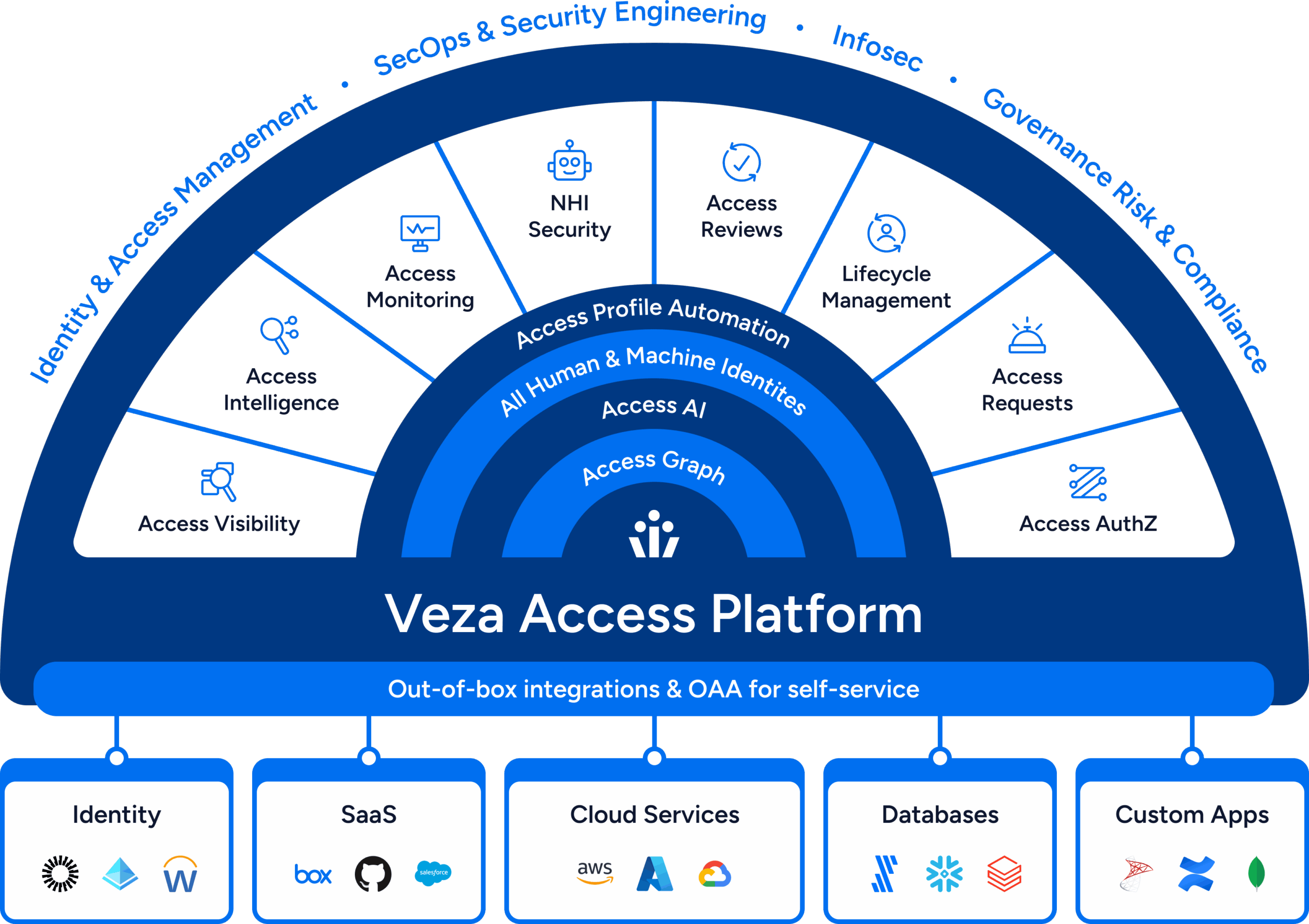
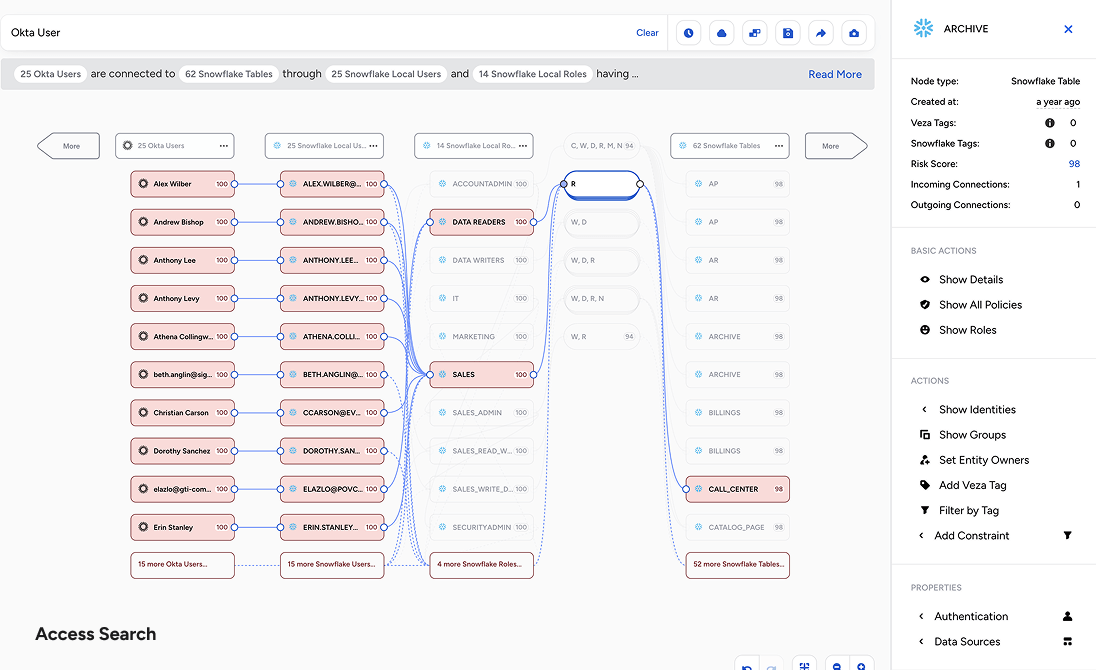
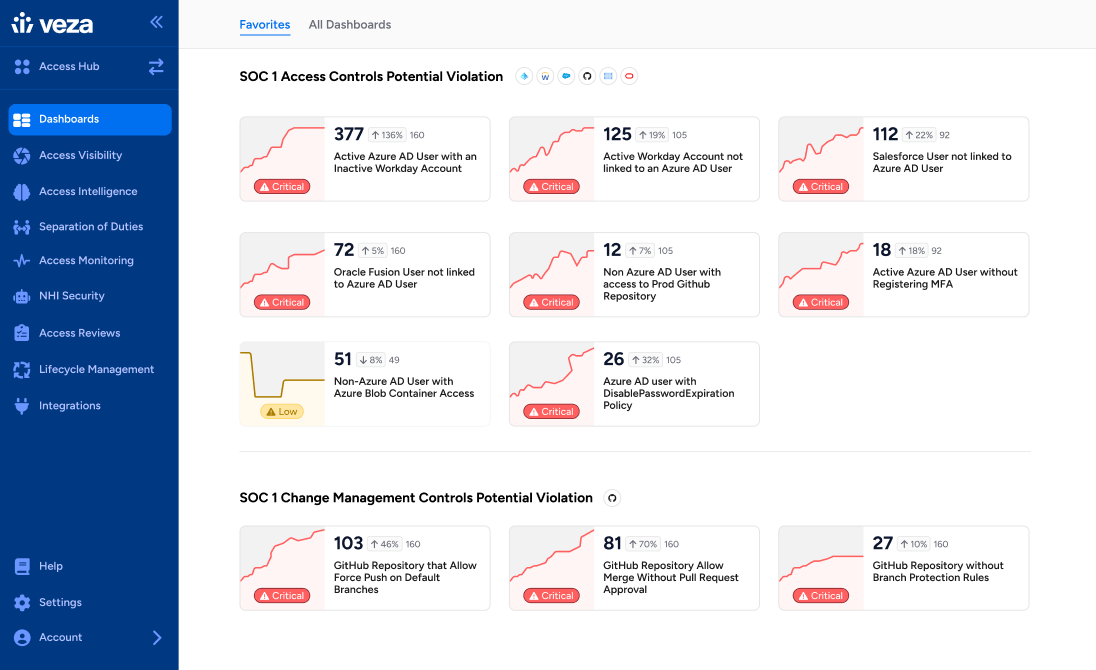
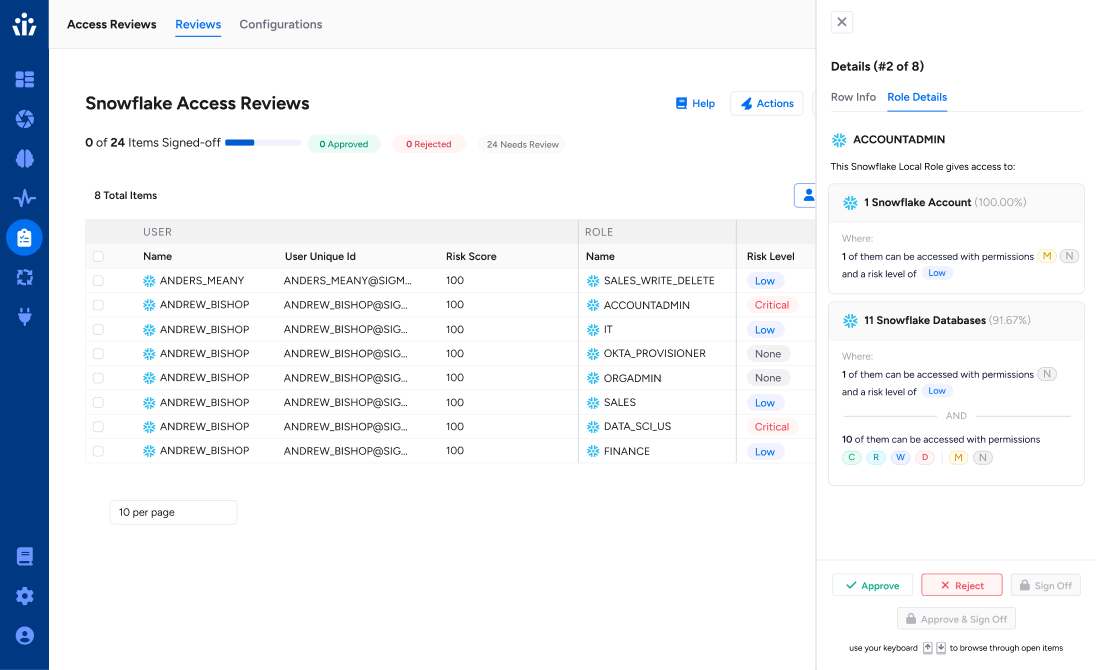
Top use cases
Leverage Veza’s Intelligent Access to power
key business initiatives in your organization
Privileged Access Monitoring
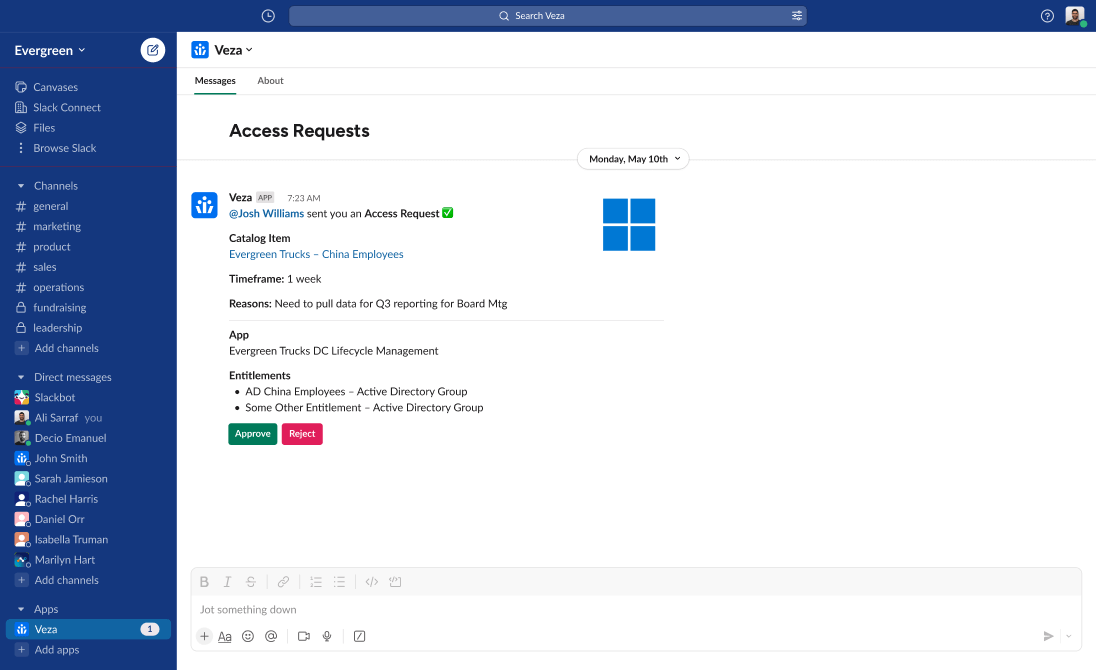
Non-Human Identity Management
Data System Access
SaaS Access Security
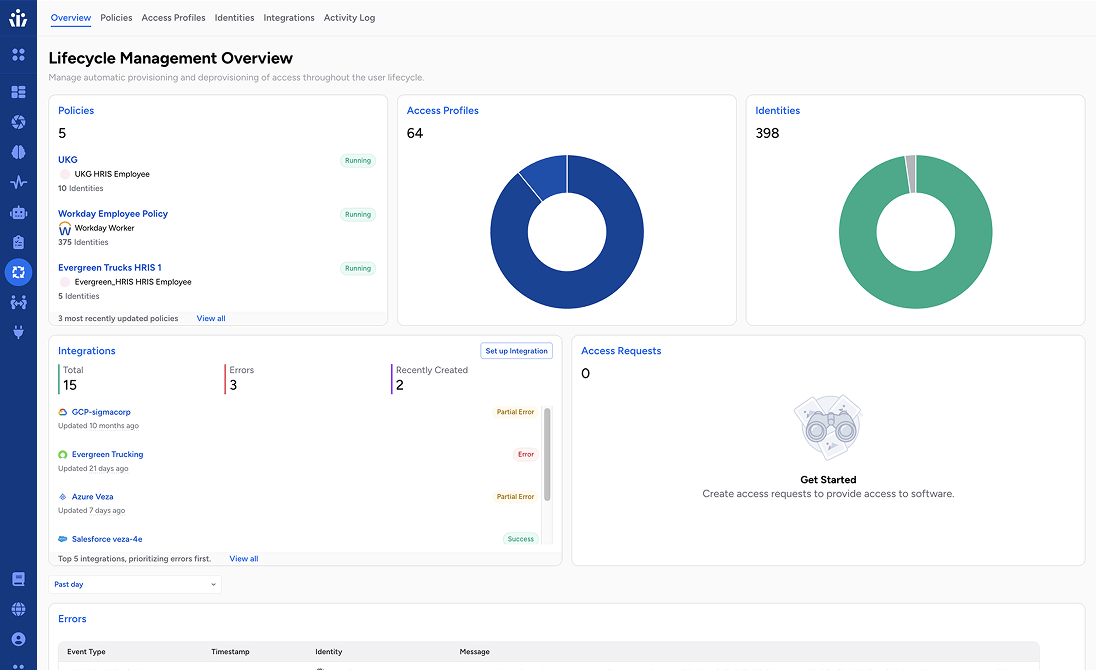
Next-Gen IGA
Cloud Access Management
Agentic AI Security

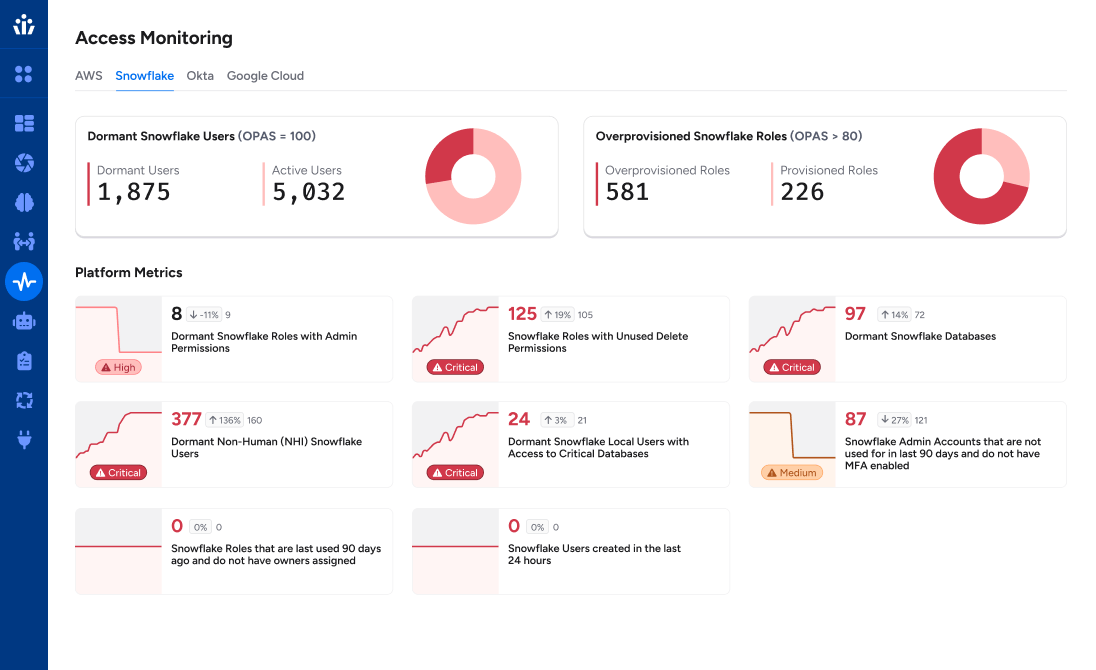
Veza for identity security at Snowflake