Explore our posts
-

Identity Radicals: Groundhog day in identity security
Learn more -
Operationalizing Modern Identity Security: A CISO’s Perspective on Value Creation and Sustainable Growth
Learn more -

What is lifecycle management in identity security?
Learn more -

SOC 2 Compliance Requirements [2025]
Learn more -
Non-Human Identity Security: A Practical Guide to Mitigating Risk
Learn more -
Going Beyond Provisioning and Deprovisioning with Veza Lifecycle Management
Learn more
-

Identity Security Posture Management
Learn more -
The MIGHT of Veza
Learn more -

Veza welcomes Mike Towers as Chief Security & Trust Officer
Learn more -

Identity Security Spotlight: Cisco announces “Identity Intelligence”
Learn more -

Veza @ Blackstone: Modernizing IGA with Automation and Intelligence
Learn more -
The year of Intelligent Access
Learn more
-
Simplifying Security: The Power of Effective Access Control in Cybersecurity
Learn more -
Veza’s Automated Access Revocation and Access Remediation
Learn more -

Securing Snowflake: A CISO’s Guide to Effective Access Control
Learn more -

Introducing Access AI: The Future of Identity Security
Learn more -
What is SaaS Sprawl?
Learn more
-

Identity Radicals: Groundhog day in identity security
Learn more -
Charting a Path for the Future of Identity Security
Learn more -
Identity Radicals: Identity governance in the cloud era
Learn more -

Identity Security Posture Management
Learn more -

Decoding Data Sovereignty with Jenner Holden | Ep 3
Learn more -

Disrupting Breaches and Advancing InfoSec with David Tyburski | Ep 2
Learn more
-
IBM’s 2024 Cost of a Data Breach Report: AI-Powered Security Lowers Costs
Learn more -
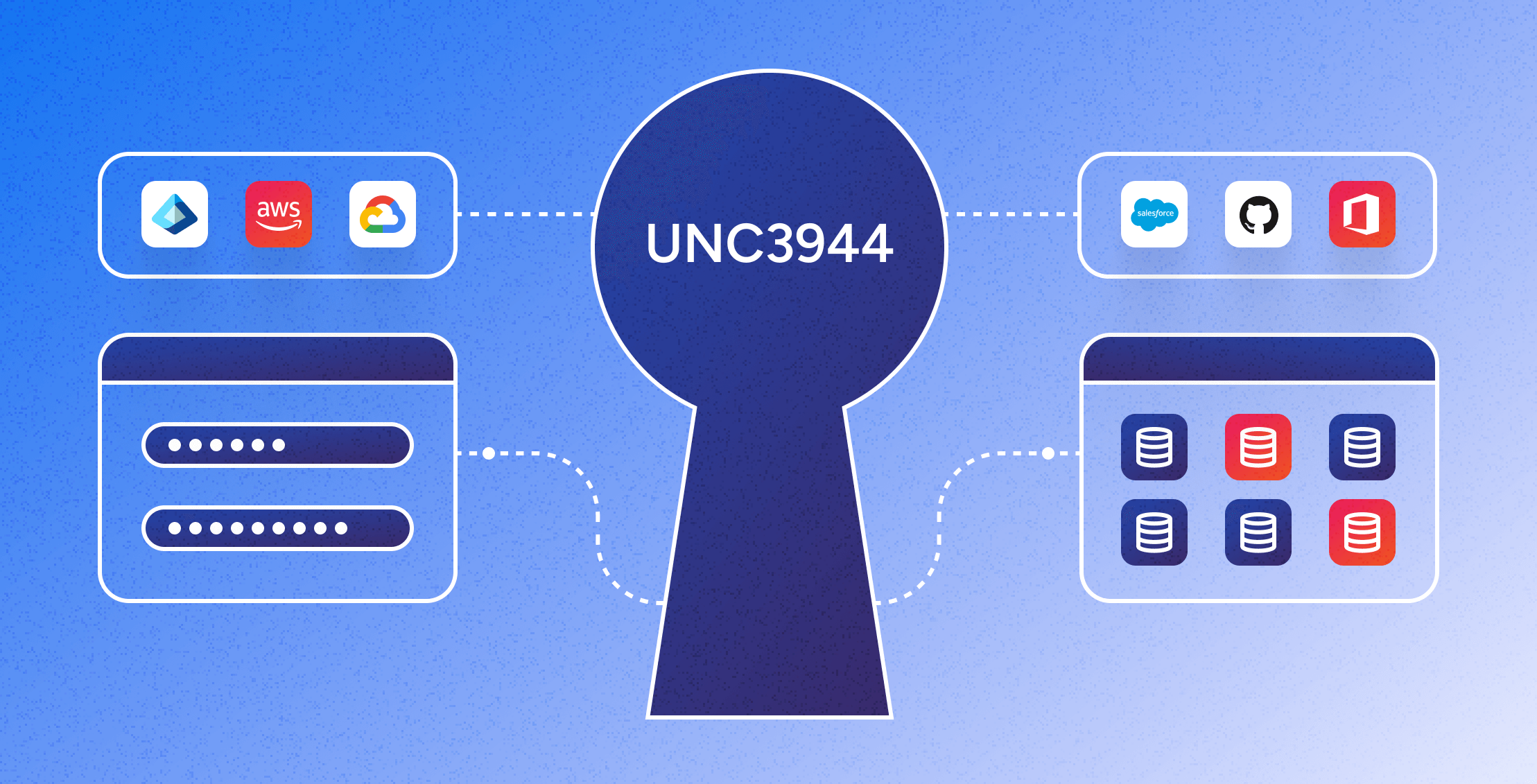
Mitigating the UNC3944 Threat: The Power of Modern Identity Security Platforms
Learn more -

Identity Security Spotlight: Ransomware attack on Ascension
Learn more -

Identity Security Spotlight: Microsoft CISA Investigation
Learn more -

Veza welcomes Mike Towers as Chief Security & Trust Officer
Learn more -

Identity Security Spotlight: Delinea acquires Fastpath
Learn more
No results found.
-
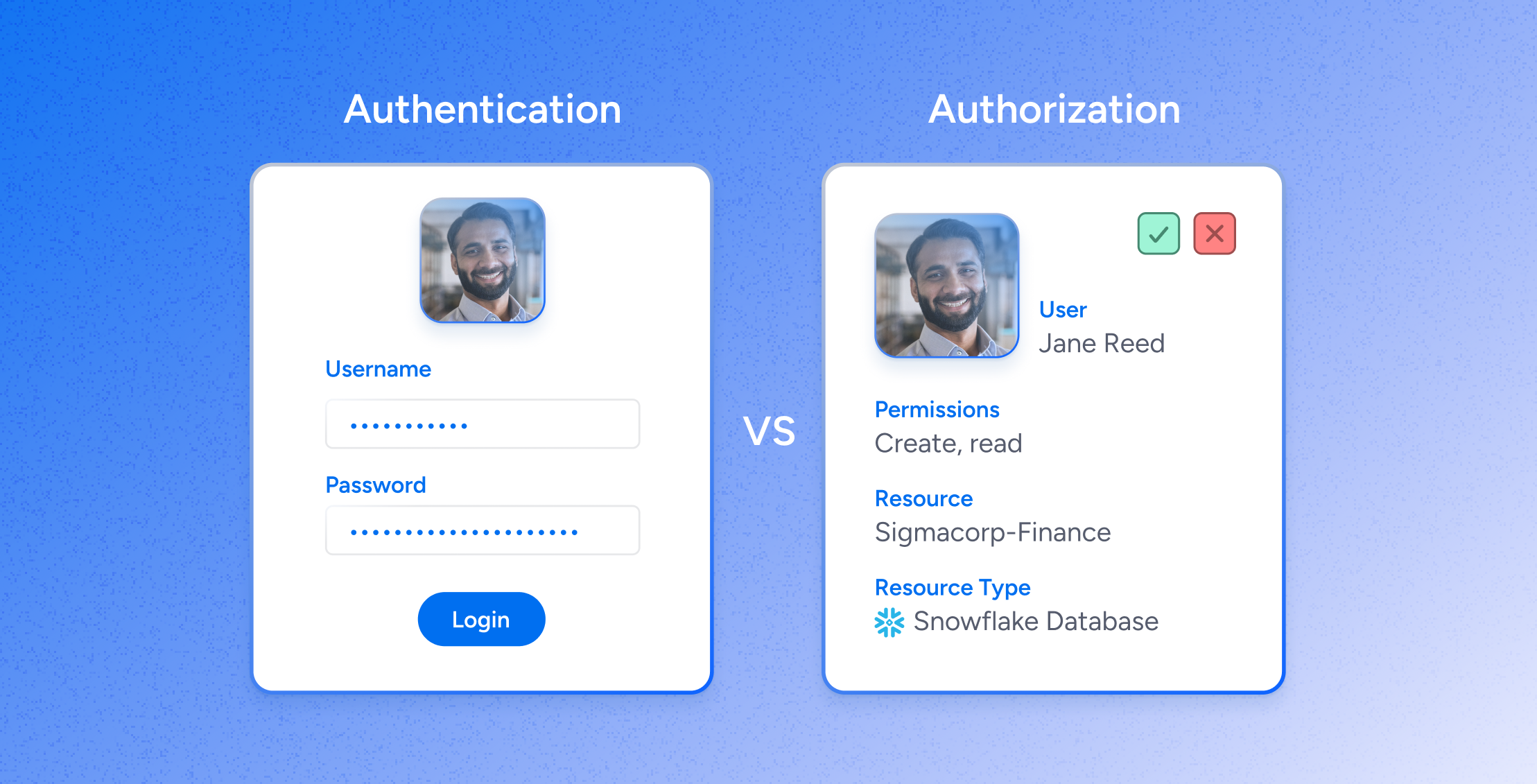
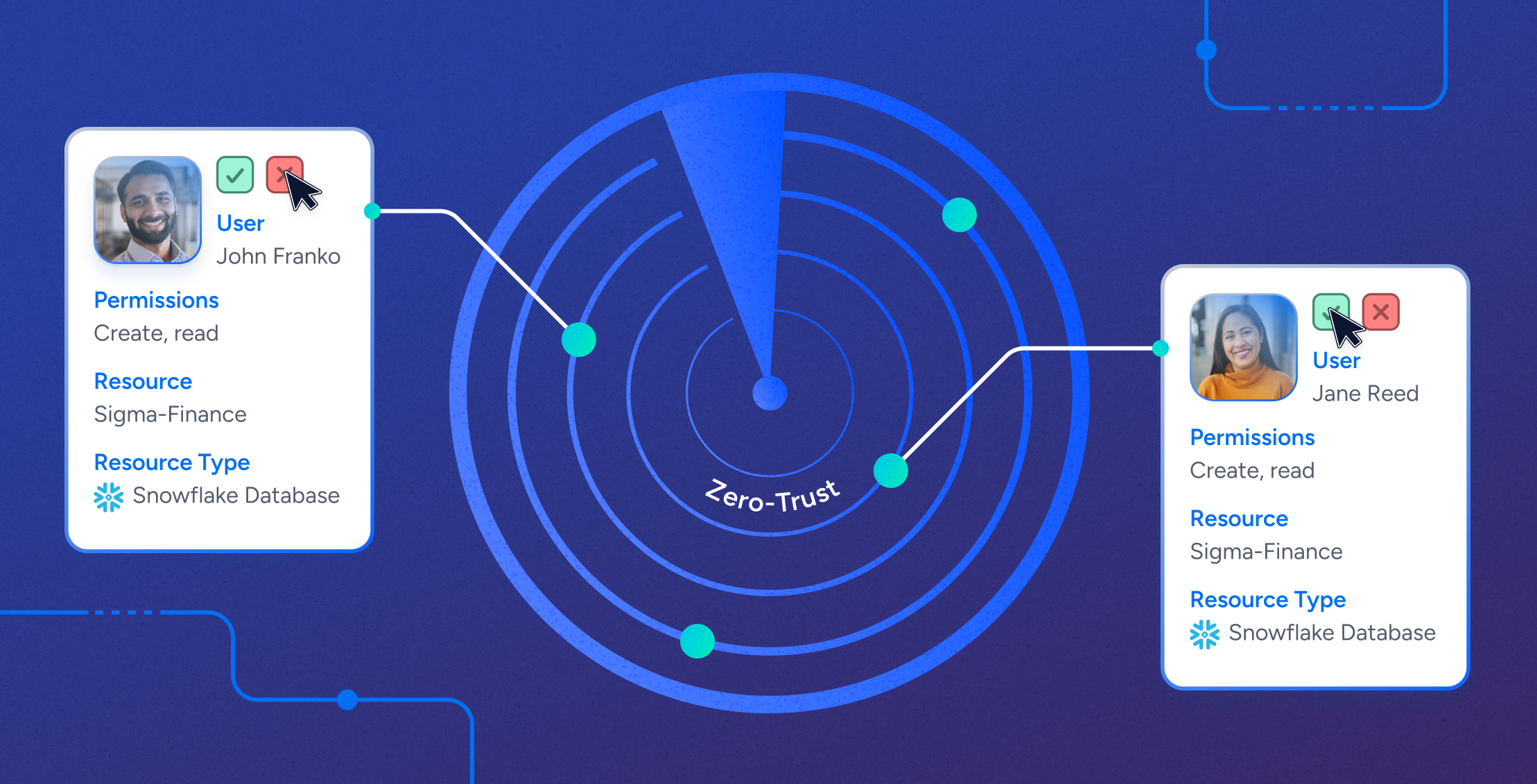
Authorization, NOT Authentication: the critical backbone for zero-trust security
Learn more -
Digital Transformation and the Data Authorization Imperative
Learn more -
Data Security: The Challenge of Securing Service Accounts
Learn more -
Why I’m excited about the future of Veza
Learn more -

Introducing Veza — Our Quest to Advance the Data Security Industry for Decades to Come
Learn more