GitHub Privileged Access Management
GitHub is the de facto collaboration platform for millions of developers worldwide, facilitating collaboration and innovation at an unprecedented scale. But with great power comes great responsibility–specifically, the responsibility to secure and manage access to the vast repositories of intellectual property it houses.
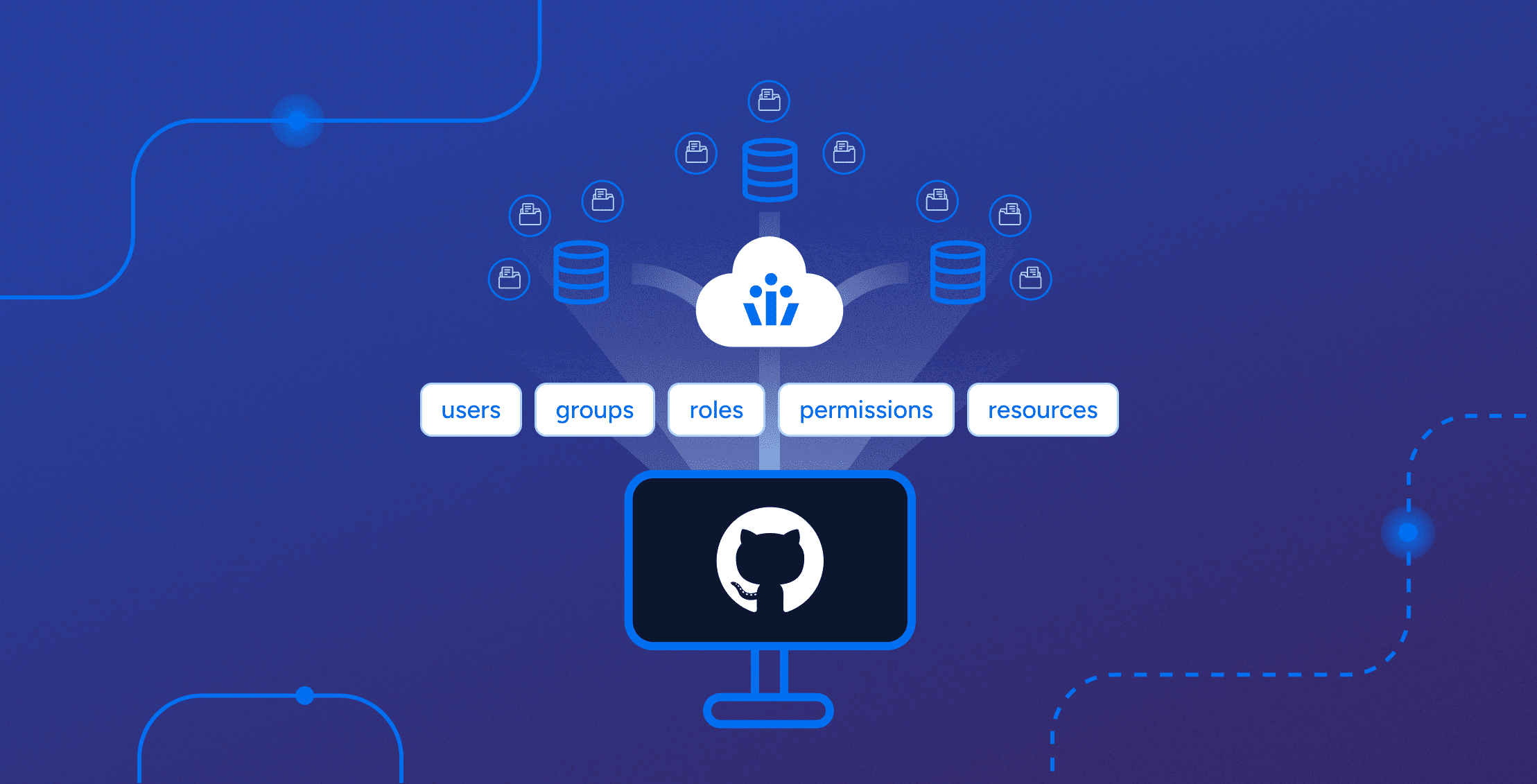
Veza makes it easy for companies to prevent unwanted access to their GitHub projects. By helping teams see who has access to what, your organization can quickly find and fix any GitHub access issues before they become problems.
- Keep Your Source Code Safe: Make sure only the right people can access your GitHub projects.
- Save Time on Reviews: Spend 90% less time checking and approving who has access to what.
- Stay Compliant: Meet rules and regulations without the headache.
GitHub Access Control & Security Challenges
From managing access to repositories to ensuring compliance with regulatory standards, the path to GitHub security is fraught with obstacles. Ensuring the security of GitHub repositories isn’t just about protecting code: it’s about safeguarding the innovation and integrity of your entire organization. Veza is here to help you navigate these challenges effectively.
Access to GitHub Repositories
One of the biggest challenges in GitHub’s dynamic environment–characterized by the frequent creation and updating of repositories–is controlling who is granted access to which resources. This is particularly complex for organizations that utilize both private and public repositories to accommodate different operational needs.
For instance, public repositories may host user-accessible documentation, company-sponsored open-source projects, sample applications, or connectors, serving as a window to the organization’s contributions to the open-source community. On the other hand, private repositories are often reserved for more sensitive content, such as proprietary source code or Infrastructure as Code (IaC) repositories, which require stringent access controls to prevent intellectual property theft or data breaches.
The coexistence of private and public repositories within the same organization introduces a nuanced layer of access management. Given the vast number of repositories a company might manage–potentially numbering in the hundreds–it becomes a formidable task to keep track of where external collaborators are permitted and where their access should be restricted. This necessitates heightened vigilance and a sophisticated access control system to ensure that sensitive information remains secure while still fostering the collaborative spirit GitHub embodies.
Regulatory Compliance & Certifications
Meeting regulatory compliance and obtaining certifications is another significant hurdle. Manual efforts or reliance on third-party services to audit and certify GitHub access can be time-consuming and costly. Automating this process saves time and ensures a consistent and reliable compliance posture.
Complex Github RBAC Model
GitHub’s Role-Based Access Control (RBAC) model adds another layer of complexity. With various roles like owners, members, and billing managers, and different permissions across organizational and repository levels, understanding and managing GitHub’s RBAC model is no small feat. This complexity often leads to misconfigured permissions, exposing organizations to unnecessary risk.
Mingling of Company and Personal Identities
In the GitHub ecosystem, the lines between company and personal identities often blur, much like the overlap between private and public repositories. It’s common to encounter personal and company identities among internal collaborators. Developers frequently prefer to use their personal GitHub handles to document their contributions throughout their careers.
This practice persists even when companies mandate the creation of separate accounts for work purposes. The universal nature of GitHub usernames introduces a unique challenge: desired usernames may already be taken or easily be mimicked. For instance, one doesn’t need to be an employee of Cyberdyne Systems to create a username like “miles-dyson-cyberdyne,” leading to potential confusion.
This scenario complicates the already challenging task of distinguishing between internal and external contributors. Questions like “Who is CodeNinja666?” become commonplace. Determining whether such a user is an internal team member with legitimate access rights or an external part can be daunting. Should this individual have the authority to make changes to the source code?
The intermingling of personal and company identities on GitHub not only raises questions about security and access control but also underscores the importance of establishing clear guidelines and verification processes to identify and manage contributors accurately.
How to Manage GitHub Access, Roles, & Authorization
Let’s take a closer look at how Veza supports GitHub roles, access control, GitHub authorization, and more.
GitHub Roles
GitHub roles determine the level of access and control a user has over repositories and organizational settings, which range from read-only access for some users to full administrative powers for others. Managing and understanding the implications of each role can be complex, especially as the number of users grows. Misassignments can lead to security vulnerabilities or operational inefficiencies.
Veza clarifies GitHub roles by mapping them within its intuitive interface, making it easy to assign the right level of access to the right person. It also enables audit trails for role assignments ensuring that changes are tracked and can be reviewed for compliance and security.
GitHub Access Control
Access control in GitHub involves managing who can see, contribute to, or administer projects and data. It’s about ensuring the right people have the right access at the right time. However, keeping access controls up-to-date becomes a daunting task as projects scale and teams evolve. Outdated or excessive permissions can expose sensitive data.
Veza automates enforcing access policies, ensuring only authorized users can access sensitive information. It simplifies the review and adjustment of permissions, making access control management more efficient and less prone to error.
Proper Removal of Terminated Employees
A critical aspect of access control involves the diligent removal of access rights for employees or engineers who are no longer part of the company. This step is especially important in an environment like GitHub, where personal accounts are often linked with company projects. Unlike company-owned resources, personal GitHub accounts are not directly under the company’s control, which means they might not be automatically disconnected by the organization’s standard provisioning and de-provisioning tools upon an employee’s departure.
Ensuring the proper removal of access for terminated employees requires a proactive and often manual review process. Since these GitHub accounts are often personal to the individuals and merely associated with the company for collaborative purposes, they can easily slip through the cracks of automated systems designed to revoke access to internal systems and tools.
Veza can assist with these challenges by offering an automated mechanism for auditing and managing access permissions, even for personal accounts linked to company resources. With Veza, you can ensure access rights are properly updated or even revoked when employees leave, helping to maintain secure and compliant access controls.
GitHub Authorization
Authorization is the process of determining what actions a user can perform within GitHub. It’s a critical component of security, ensuring users can only perform actions that they’re explicitly permitted to perform. Managing authorization rules can also be complex, especially in large organizations with many users and GitHub repositories. Incorrect settings can lead to unauthorized access or restricted workflows.
Veza simplifies authorization management by providing a clear view of who has access to what and why. It enables easy updates to authorization policies and automates the enforcement of these policies, ensuring secure and efficient operations.
How Veza Secures GitHub Repositories
Veza secures your GitHub deployment by empowering your risk/governance, trust, and security teams to understand and control authorization across all GitHub repositories–minimizing the risk of exposure to your code.
More About Privileged Access in GitHub
Find access to common questions about GitHub privileged access, security, and best practices.
What is GitHub repository access?
GitHub repository access refers to the permissions granted to users to view, edit, or manage the repositories. Access levels include read, write, and admin, determining user actions within a repository.
Veza provides clear visibility into repository access levels across your organization, making it easy to see who has what access to each repository. This aids in ensuring that the right people have the right access.
How to check Github permissions
To check GitHub permissions, go to the repository’s settings and click “Manage Access.” There, you’ll see a list of users and their access levels. For organizations, check under the “People” section in organization settings.
With Veza, checking GitHub permissions is simplified through a centralized dashboard that displays all user permissions across repositories. This allows for quick audits and adjustments without navigating through each repository’s settings.
What is GitHub read-only access?
GitHub read-only access allows users to view and clone the repository without making any changes. Users can submit issues and pull requests without merging them or altering the repository’s code or settings.
Veza can help manage read-only access by applying it correctly and only to the intended users. It monitors access levels to prevent unauthorized changes, ensuring compliance with access policies.
How secure is GitHub?
GitHub employs robust security measures, including encryption in transit and at rest, two-factor authentication, and regular audits. However, security also depends on users’ practices, such as using strong passwords, limiting access, and regularly reviewing permissions (and removing them if needed).
Veza enhances security by monitoring for misconfigurations or unauthorized access attempts, offering an additional layer of security on top of GitHub’s built-in mechanisms.
What is GitHub advanced security?
GitHub advanced security provides additional protection with features like code scanning for vulnerabilities, secret scanning for exposed credentials, and dependency review to identify security risks in project dependencies.
Veza complements GitHub’s advanced security by providing insights into how security features are utilized and identifying gaps in security coverage.
How do I manage access to GitHub? Does GitHub have access control?
Manage access to GitHub by regularly reviewing and updating repository and organization access settings, using teams for group access management, applying branch protection rules, and leveraging GitHub’s built-in roles for precise permission control.
Veza automates and streamlines access management in GitHub by providing tools for easy permission monitoring, access reviews, and the enforcement of access policies, making management more efficient and less prone to error.
The platform enhances GitHub’s access control by offering a more granular view and management of permissions. It ensures access controls are correctly implemented and adhered to across all GitHub repositories and teams.
What are some best practices for GitHub access management?
Best practices for GitHub access management include:
- Implementing the principle of least privilege.
- Using teams to manage group permissions efficiently.
- Regularly reviewing access permissions and audit logs.
- Enabling two-factor authentication for all users.
- Applying branch protection rules to critical branches.
- Conducting periodic access reviews and security audits.
Understanding and implementing these practices will enhance the security of your GitHub repositories, ensuring that your code and data remain protected.
Veza supports best practices for GitHub access management by automating least privilege access, facilitating efficient team-based permissions management, and providing regular access reviews and security audits. It ensures that best practices are not just recommended but actively enforced. It also provides the tools and insights necessary to address these common concerns, ensuring GitHub repository access is secure, compliant, and efficiently managed.