Identity Security Posture Management (ISPM) is a top priority in cybersecurity this year and it’s easy to see why. With 80% of data breaches linked to identity-related issues, organizations are stepping up their identity security game by adopting modern solutions to answer cybersecurity’s hardest question: “Who can take what action on what data?”
As cloud services and SaaS applications multiply, traditional security methods simply can’t keep pace with this expanding attack surface. The challenges associated with managing access across multiple environments have proven that traditional identity tools (SSO, IAM, IGA) can’t solve the identity security puzzle. That’s why many organizations are turning to ISPM: a holistic approach to reducing and fortifying the attack surface associated with all identity access in the enterprise.
In today’s complex digital world, understanding and implementing ISPM is no longer optional—it’s essential for resiliency against identity threats.
What is Identity Security Posture Management (ISPM)?
Identity Security Posture Management is the practice of securing an organization’s access to data for all digital identities. It includes processes, technologies, and policies used to manage identities and access entitlements across an organization’s IT systems and applications. The goal of ISPM is to minimize the risk associated with identity access across the enterprise, while still meeting the needs of the business.
This includes adherence to the principle of least privilege and disciplined pruning of role structures. This includes identifying vulnerabilities and gaps, preventing accidental and overprivileged access, and ensuring access rights and permissions are properly managed and aligned with security policies (e.g. MFA use and separation-of-duties).
Since businesses change all the time, ISPM is necessarily an ongoing pursuit. ISPM helps organizations continuously monitor and secure their identities, reducing the risk of data breaches, ransomware and insider abuse.
What security challenges does ISPM address?
Today, the identity landscape spans IT infrastructures and multi-cloud architectures and includes multiple identity stores. “Identity” also means more than just users—it includes machines, service accounts, workloads, and more. Without end-to-end visibility across the identity landscape, it’s difficult to get a true understanding of an organization’s security posture.
Mismanaging identity access can lead to issues like dormant accounts, weak passwords, excessive permissions, and orphaned accounts—all of which can become attack vectors for bad actors. According to Gartner, preventative security controls can help organizations avoid the following issues:
- Misconfigurations: Over-privileging accounts, improper identity lifecycle management, and incorrectly implementing multi-factor authentication (MFA) can leave organizations susceptible to threat actors. Failure to continuously monitor configurations for suspicious changes can also increase the risk of a breach.
- Vulnerabilities: Poor identity hygiene, including weak passwords and inadequate conditional access controls, further exposes organizations to threats.
- Risk Exposure: An accumulation of unnecessary or excessive access rights, dormant accounts with stale passwords, and misconfigured identity and access management (IAM) policies can result in excessive privileges and potential breaches. Dormant accounts from former employees or contractors that weren’t disabled or deleted, as well as third-party and orphaned accounts that lack ownership and proper monitoring, all increase the risk of unauthorized access.
To mitigate these risks, enforce strong, unique passwords and ensure you’re implementing MFA properly–for all identities. Across the millions of human identities tracked by Veza, 13% of users still haven’t enabled MFA. Make sure to provide user training and regularly review and update your MFA policies when needed.
Regular password audits, rotation policies, and proper identity synchronization between on-premise directories and cloud platforms can also help reduce security threats. And, with ISPM, organizations can get even more visibility into their identity security weak spots, automate controls, and reduce potential risks to their digital assets and infrastructure.
How frequently should a company assess its Identity Security Posture?
Given the dynamic nature of cyber threats and constant changes to IT infrastructures, organizations should monitor and assess their identity security posture on a continuous basis. Traditionally, companies would assess their posture quarterly or monthly. However, with the complexity of today’s digital landscape and increasing sophistication in cyber threats, that’s no longer enough.
Now, organizations are turning to continuous monitoring to reduce their risk of an attack. Instead of discovering an issue potentially months after it occurred, modern identity security solutions send an alert immediately if something significant has changed in your security posture.
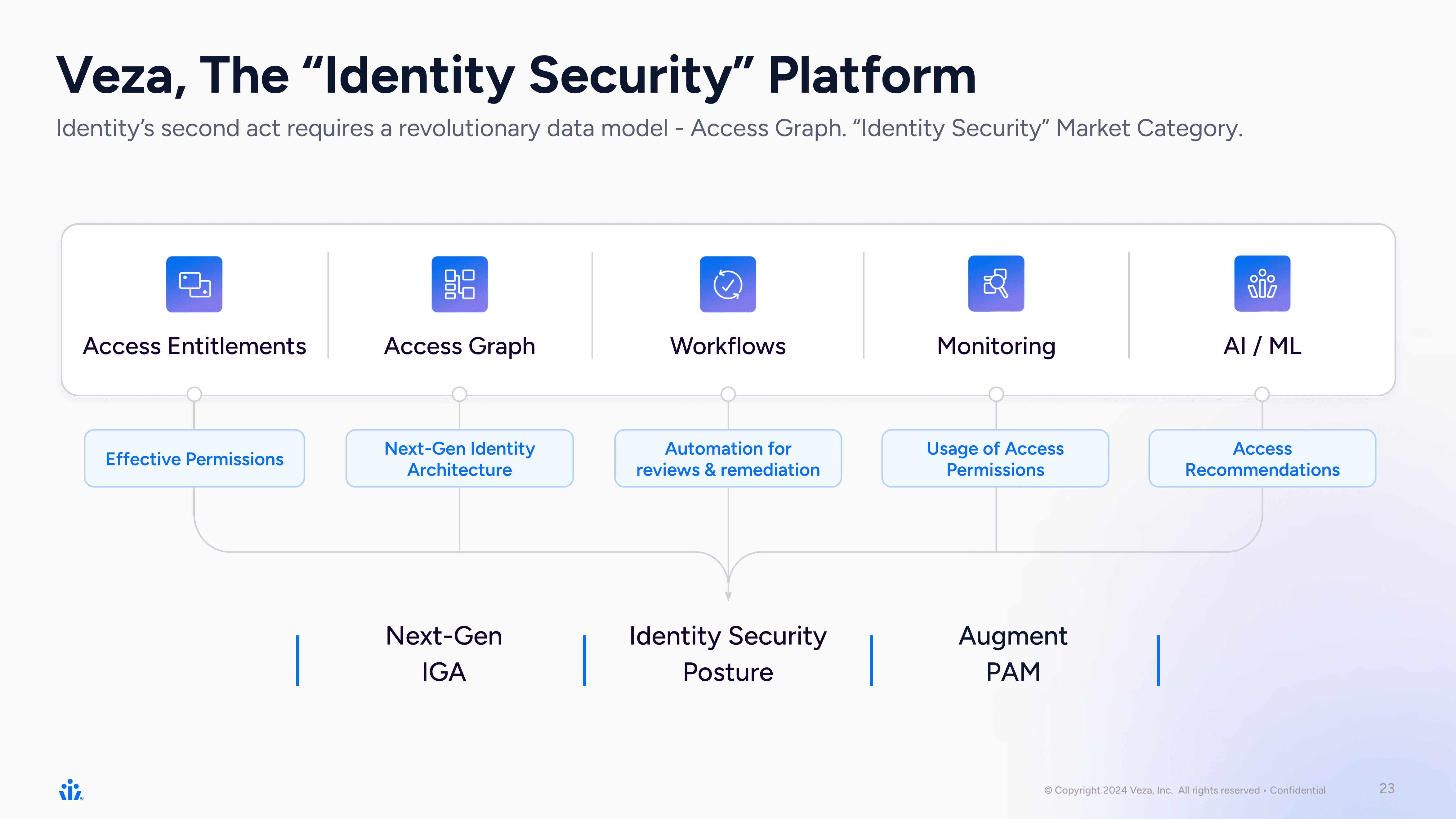
Identity Security Posture Management components
ISPM requires a portfolio of identity solutions operating as a cohesive system. This helps organizations address all aspects of identity and access management for a more holistic view of their security posture.
Generally speaking, ISPM is gradually subsuming the following components:
Identity and Access Management (IAM)
Identity and Access Management (IAM) typically involves implementing specific technologies like MFA, Single Sign-On (SSO), and password management tools to secure user access to systems and applications.
IAM ensures that the right individuals have access to the right resources at the right times. By verifying users’ identities before granting access to systems and data, IAM ultimately forms the first layer of defense in security posture.
Identity Governance and Administration (IGA)
Identity Governance and Administration (IGA) is important for managing user identities, access rights, and permissions across multiple systems and applications within an organization.
An IGA solution should help you automate user provisioning and de-provisioning, streamline user access reviews and certifications, detect and remediate excessive user access and entitlements, and ensure compliance with security policies and regulatory requirements with continuous monitoring and auditing capabilities.
This can help organizations control who has access to what–a critical aspect of ISPM.
Privileged Access Management (PAM)
Privileged Access Management (PAM) is about managing and monitoring privileged accounts and access to sensitive systems and data. PAM tools are typically designed to prevent unauthorized access and ensure compliance with regulations and policies by vaulting and rotating privileged account passwords, closely auditing the activities of privileged users, and enforcing MFA for privileged accounts.
In the context of ISPM, PAM can reduce the risk of breaches and protect critical resources because privileged accounts are often coveted by attackers. However, for PAM to be useful, privileged accounts must first be known.
Risk intelligence
Risk intelligence means using data analytics tools to monitor user behavior and identify potential security threats. Risk intelligence tools assess and mitigate risks associated with user access and permissions by baselining normal user behavior. This allows them to detect anomalies that could indicate compromised accounts or insider threats and analyze access and entitlement risks.
Risk intelligence is essential for visibility into their identity security posture because it can discover and prioritize privileged access that was previously hidden.
Access reviews and control
Regular access reviews and control mechanisms are essential for maintaining a strong security posture. They involve periodically reviewing and certifying user access to ensure that permissions and remediation processes can help organizations reduce the risk of over-privileged accounts and support the principle of least privilege. This helps ensure that access rights remain aligned with security policies and business needs.
Non-human identity management
Non-human identity management means managing identities not associated with individual users—like machines, service accounts, and workloads. Ensuring these identities are properly managed and secured is critical for a strong identity security posture.
This includes monitoring for excessive permissions, automating the provisioning and deprovisioning of non-human identities, and enforcing strict access controls to prevent unauthorized access.
Why is Identity Security Posture Management important?
A strong identity security posture is critical for protecting an organization’s sensitive data and assets. Without a proper ISPM strategy in place, organizations are vulnerable to cyberattacks, which can lead to data breaches, ransomware extortion, business disruption, and reputational damage.
Reduced risk of breaches
By implementing ISPM practices and technologies, organizations can significantly reduce the risk of unauthorized access to sensitive information and systems–which is often the cause of data breaches and cyberattacks.
ISPM helps organizations continuously monitor and assess the effectiveness of access controls, identify vulnerabilities, and prevent unauthorized and over-privileged access. This not only helps prevent breaches but also minimizes the impact if a breach does occur by limiting what data is accessible to the compromised identities.
Streamlined access management
By implementing ISPM practices, organizations can automate the provisioning and deprovisioning of user accounts, streamline access reviews, and detect and remediate excessive user access and entitlements. This can reduce the risk of over-privileged accounts and helps enforce the principle of least privilege, which is critical for minimizing security risks.
Regulatory compliance
ISPM helps governance and risk teams spot any areas where they might not be in compliance with regulations like GDPR, HIPAA, and PCI-DSS.It helps those same teams watch over employee and contractor access on a continuous basis, stepping in whenever policies are violated. Additionally, many industry-specific regulations require organizations to implement ISPM strategies to protect sensitive data and maintain privacy.
By adhering to these regulations, organizations can avoid hefty fines while doing the right thing for security and privacy.
How to improve your Identity Security Posture
Today’s identity security posture comprises access across resources and apps, people and machines, cloud and on-premise environments, and more. However, this complexity makes identity a valuable target for adversaries.
To protect themselves against identity-based attacks, organizations should consider a holistic approach. Here are some steps your organization can take to improve its security posture.
- Adopt an “assumed breach” mentality
Adopting an assumed breach mentality means operating under the assumption that a breach will occur and proactively implementing measures to limit the damage. Fortunately, the right identity security platform helps organizations embrace this state of mind with continuous monitoring, real-time threat detection, and automated response.
By leveraging advanced analytics and machine learning, identity security tools can identify unusual patterns of behavior that may indicate a breach so organizations can act quickly to contain and mitigate potential threats.
And, when a breach does occur, detailed audit logs and forensic capabilities can help security teams trace the origin, understand the scope, and respond quickly.
- Implement continuous monitoring
Effective control and monitoring of authorization are fundamental for a strong ISPM strategy. With an identity security platform, organizations can get real-time visibility into user activities and access patterns.
By continuously monitoring who has access to what resources and making sure that these access rights are appropriate, organizations can maintain strict control over authorization. This is especially important in dynamic environments where roles and responsibilities frequently change and updates to access permissions are constant.
- Offer user training
Providing regular user training is an important part of improving ISPM. Again, this is where an identity security platform can be helpful. By delivering insights into user behavior and highlighting areas where training is needed most, the right tool can help organizations tailor their training programs to address specific vulnerabilities and reinforce best practices for identity and access management.
Plus, detailed audit logs and reports allow security teams to track the effectiveness of training programs and monitor improvements in user behavior and compliance rates.
- Don’t depend on MFA alone
While MFA is an important layer of security, it’s not enough. For example, individuals could still fall victim to phishing attacks, where threat actors trick them into providing their login credentials and MFA codes. They could also be vulnerable to a man-in-the-middle attack, when an attacker intercepts the MFA code sent to their device.
An advanced identity security platform can help organizations implement a multi-layered approach that integrates authentication and authorization processes with real-time analytics and automated response.
- Try Veza: The Identity Security platform
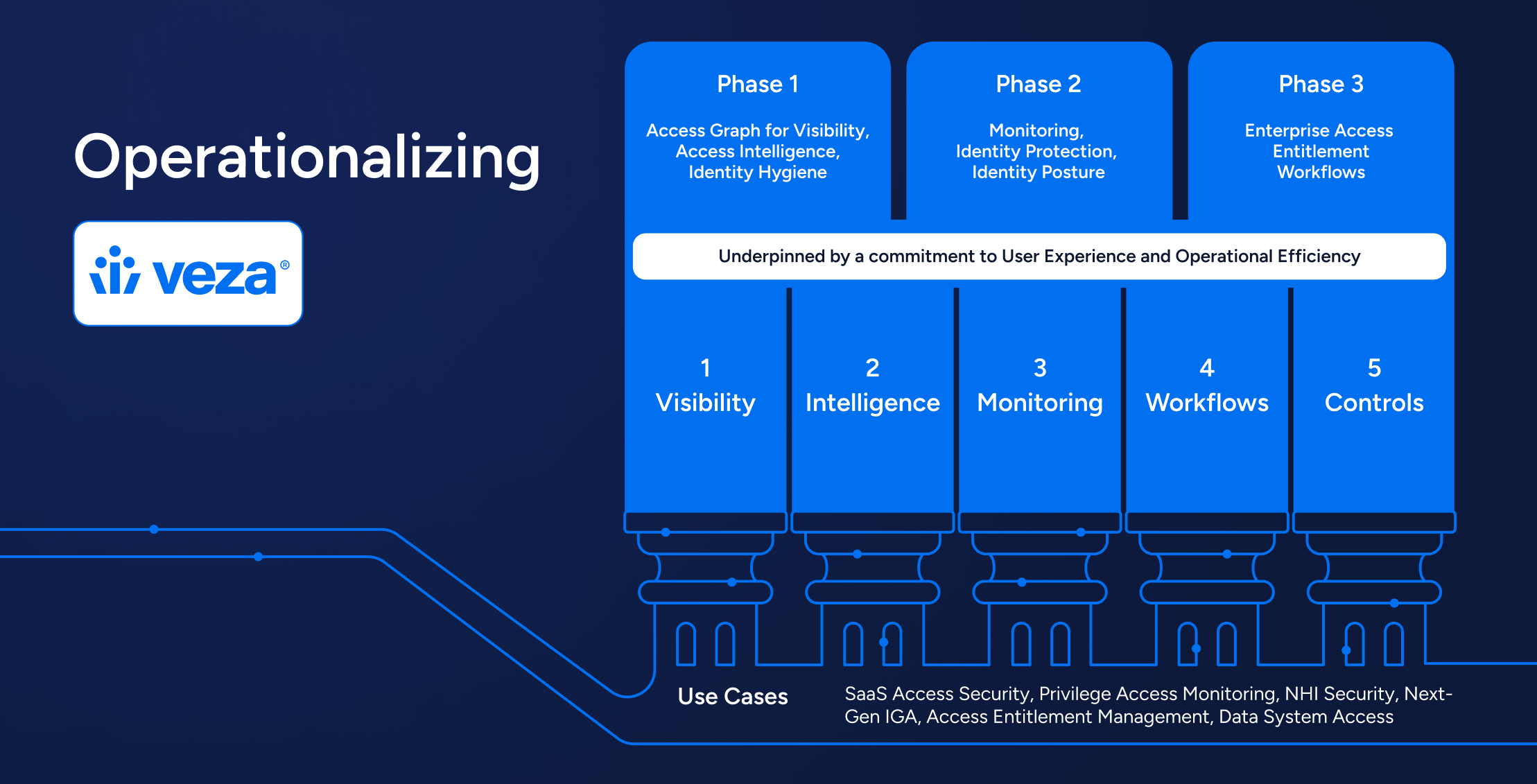
Here at Veza, we are building the modern Identity Security Platform. We believe that identity is the perimeter and our core intuition is that access permissions are the purest form of identity; permissions and entitlements represent the true “treasure map” to understanding and securing access.
Bringing Identity Security Full Circle
Veza’s approach to ISPM isn’t just a new chapter—it’s a new playbook for how security and identity teams safeguard the business. Understanding the risks tied to over-privileged access and inactive accounts is just the beginning. Reducing identity risk demands an operational shift: from point-in-time snapshots to continuous, cross-system visibility and control.
If you’re just starting to explore the identity security landscape, this primer on identity security provides the strategic backdrop for why traditional models are falling short—and where a modern approach can take you.
For security leaders evaluating how to unify identity data across silos and drive measurable access outcomes, the Veza Product Overview outlines how Veza connects identities, permissions, and usage to deliver actionable intelligence and accelerate identity lifecycle workflows.
And for organizations ready to take the next step—whether it’s operationalizing least privilege, automating access reviews, or building identity into your zero trust foundation—the Platform Overview Data Sheet offers a deeper technical dive into how Veza delivers.
Solving identity security isn’t about more dashboards—it’s about better answers. With Veza, identity risk becomes visible, measurable, and most importantly—manageable.