The landscape of user access reviews is much different than it was even a year ago. Think of the house-buying process. You’ve put in your offer and just found out the inspection passed. You buy the home…and then find out the inspection company only evaluated the home’s plumbing. You’re still vulnerable to issues with the foundation, the roof, the electric–and much more.
This is the reality of managing user access in today’s IT environments. With the average enterprise juggling 364 SaaS applications and 1,295 cloud services, the task of overseeing who can access what has reached incredible levels of complexity. It’s easier than ever to create identities outside of the identity provider or provision access outside of the standard access request policy.
Introducing service accounts and machine identities has added additional layers of complexity to access management. These non-human entities often possess poorly understood permissions and are even more poorly monitored, creating invisible pathways through which security breaches can–and do–occur.
Furthermore, the creation of local accounts and accounts for contractors and other third-parties has made visibility into access rights more elusive than ever.
Thanks to the Cloud and SaaS apps, the “holes” of access points are bigger and more unknown. Simply evaluating role names is no longer sufficient–you have to look at complete permission metadata to get the entire picture. This, combined with the increasing sophistication of cyber attacks means there’s a greater chance for threat actors to exploit vulnerabilities or find gaps in security coverage.
This article will demystify the process of user access reviews in today’s complex digital era, offering insights into best practices that can protect your organization from the inside out. We’ll explore how user access reviews work, why they’re more important than ever, and how adopting Intelligent Access can not only streamline the process–but transform it into a strategic advantage.
What is a User Access Review?
At its core, a user access review (UAR) is the process of examining and verifying users’ rights and permissions within an organization’s systems and applications. It’s about ensuring that each person is authorized to access only the resources they need for their job–and nothing more.
User Access Review Example
Let’s break down the UAR process with some real-world examples:
- Joiners: These are new employees or users added to your system. A common mistake here is granting them broader access than necessary because it’s quicker or easier.
- Movers: These are existing employees whose roles within the organization have changed. Often, their access rights accumulate, leading to privilege creep.
- Leavers: These are employees who have left the organization but whose access has not been fully revoked.
A user access review entails auditing these scenarios to ensure that joiners have the correct access from day one, movers’ access rights are adjusted to fit their new roles, and leavers’ access is revoked when they exit the organization.
Performing user access reviews are crucial for maintaining the integrity of your organization’s security posture, ensuring sensitive information remains protected, and upholding compliance with various regulatory standards. They can be used as part of a defense in depth strategy that provides an extra layer of security to catch any provisioning (or deprovisioning) mistakes along the way and stick to the principle of least privilege.
Importance of User Access Reviews
The significance of user access reviews cannot be overstated in our rapidly evolving digital landscape. These reviews are not merely a procedural checkbox, but a cornerstone of an effective cybersecurity strategy.
Protects Sensitive Data
Sensitive data is the lifeblood of any organization. Whether it’s financial records, personal employee information, or proprietary intellectual property, ensuring data security is paramount. UARs are a critical checkpoint to verify that only authorized individuals can access this data.
Regardless of whether a data breach has occurred–though one will–it significantly reduces the organization’s vulnerability to cyber threats.
Comply with Standards, Laws, & Regulations
Compliance is not optional in today’s regulatory environment. From HIPAA, GDPR, SOX, PCI DSS to SOC 2, each set of regulations demands rigorous control over who can access what within an organization.
- HIPAA: In the healthcare sector, the Health Insurance Portability and Accountability Act mandates biannual or annual reviews, depending on the specific stipulations of an organization. The focus is ensuring that only necessary personnel have access to patient health information and safeguarding patient privacy and security. Violations can attract fines ranging from $10,000 to $50,000 per incident, with the potential for criminal charges in severe cases.
- GDPR: Affecting any organization that processes the data of EU citizens, the General Data Protection Regulation requires biannual or annual reviews to ensure employees have access only to the EU personal identifiable information (PII) necessary for their job functions. The penalties for non-compliance are severe, with fines up to €20 million or 4% of annual global turnover, whichever is greater, making GDPR compliance a critical priority.
- SOX: The Sarbanes-Oxley Act applies to all publicly traded companies and requires quarterly access reviews. These reviews are crucial for ensuring financial information is accurate and secure, preventing fraud and errors in financial reporting. Non-compliance can lead to fines of up to $5 million, prison terms, and a loss of investor trust, which can significantly impact a company’s stock price.
- PCI DSS: Aimed at all entities that handle cardholder data, the Payment Card Industry Data Security Standard mandates annual access reviews to protect against unauthorized access (moving to biannual in March 2025 due to the shift to v4.0). The goal is to verify that measures are in place to safeguard cardholder data from unauthorized access, modification, or destruction. Non-compliance could lead to suspending credit card processing capabilities, a dire consequence for any business.
- SOC 2: Specifically for Software as a Service (SaaS) providers, SOC 2 requires quarterly access reviews. These reviews ensure that customer data is shielded from unauthorized access and alteration. The stakes of non-compliance are high, potentially resulting in the loss of business from large enterprises that demand SOC 2 compliance as a prerequisite for engagement.
- ISO 27001: This international standard outlines best practices for an information security management system (ISMS), requiring regular reviews to ensure the secure management of financial information, intellectual property, employee details, and information entrusted by third parties. While not mandated by law, ISO 27001 certification is often required by business partners and customers to establish trust in your information security practices
User access reviews are crucial for demonstrating compliance with these standards and helping to avoid severe penalties, reputational damage, and potential financial losses: non-compliance can lead to millions of dollars in fines and potentially years of prison time.
Prevents Privilege Creep
Privilege creep, or the gradual accumulation of access rights beyond what is necessary for an individual’s role, poses a significant security risk. It creates unnecessary vulnerabilities within an organization’s IT environment.
Regular UARs ensure access rights are continually adjusted and realigned with current job functions, effectively mitigating this risk. They also decrease the blast radius of a compromised account. If an attacker gains control of a user’s account, their access to sensitive systems and data is confined to the scope of that user’s legitimate needs, making it more challenging to move laterally across the network or escalate privileges to cause widespread damage.
Decreasing Access Debt
Access debt accumulates when outdated or unnecessary access rights linger within the system, creating a breeding ground for security vulnerabilities and inefficiencies. User access reviews help identify and clean up disabled, inactive, and terminated accounts to streamline user access and reduce overall access debt.
This proactive approach enhances security and improves system performance.
Reduces Insider Threats
Insider threats, whether malicious or accidental, are a significant concern for organizations. Employees with unnecessary or excessive access can inadvertently or intentionally misuse their privileges, leading to data breaches or other security incidents.
By regularly reviewing and adjusting user access rights, UARs can help minimize this risk, ensuring that users have only the access they need to perform their duties.
User Access Review Checklist
Navigating user access reviews can seem like a daunting task. However, armed with a clear and concise checklist, organizations can streamline this essential process, ensuring it is effective and efficient.
Here’s a step-by-step guide tailored for today’s digital landscape:
- Determine what systems should be reviewed
Begin by inventorying your organization’s systems, applications, and data stores. This includes everything from cloud-based services and SaaS applications to on-premise servers and databases. The goal is to create a comprehensive list of assets that require regular access reviews, ensuring that sensitive data across all platforms is adequately protected.
- Determine how often user access should be reviewed
The frequency of your user access reviews should align with the sensitivity of the data involved and regulatory requirements. While some systems may require quarterly reviews, others might only need annual attention.
Remember, the more critical the system, the more frequently its access controls should be evaluated. This step also involves reviewing local accounts and contractor and third-party user access, as well as non-human identities, such as service accounts and machine identities, to ensure a holistic review of all access points.
- Identify who should review access for each role
Assigning the right reviewers is crucial. Typically, this involves managers who understand their departments’ specific roles and responsibilities. Additionally, IT security teams should be involved to provide technical oversight and ensure that access rights adhere to the principle of least privilege.
This collaborative approach ensures access rights are granted based on need and role specificity, minimizing the risk of over-privileged accounts.
- Generate user access reports
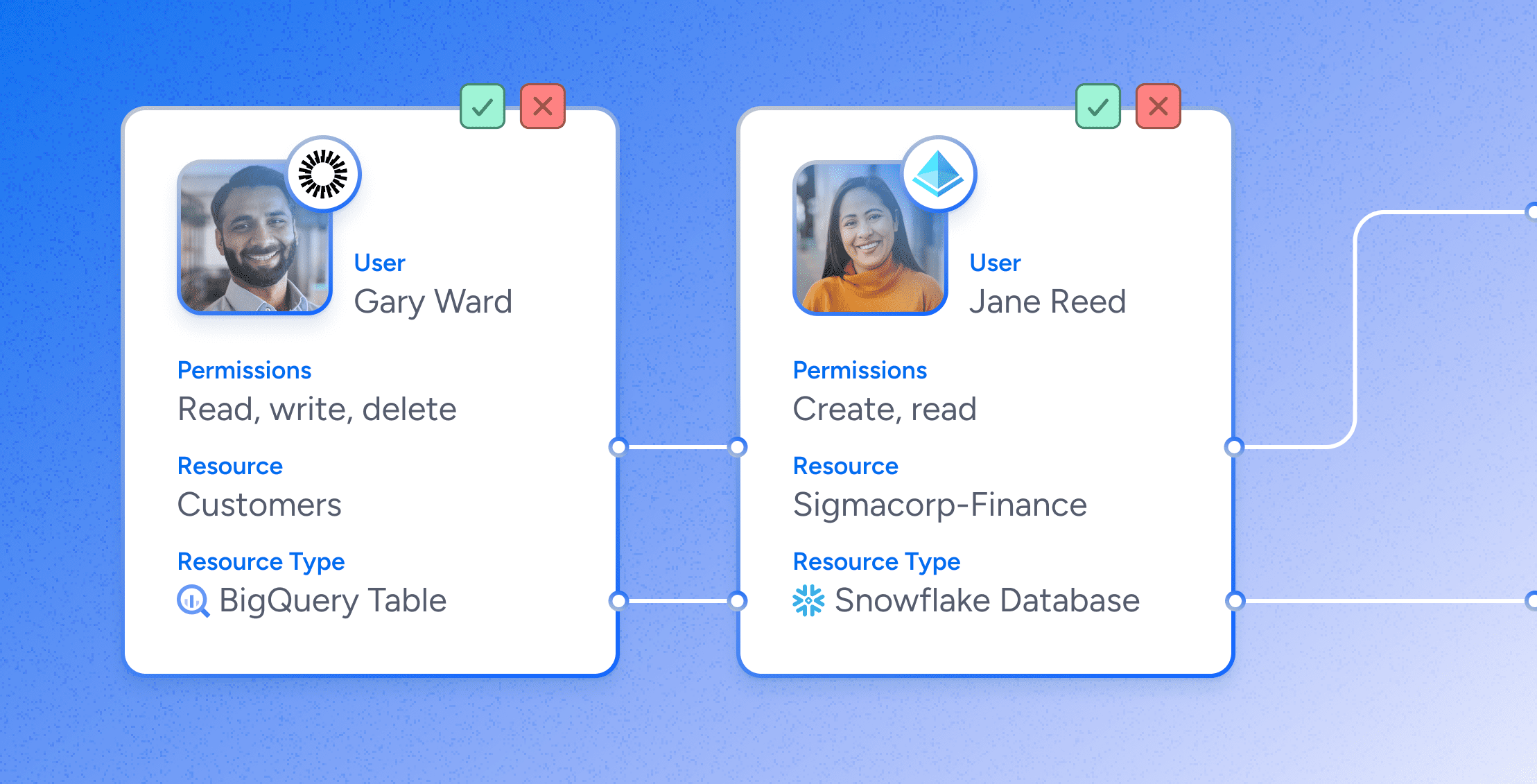
For each system under review, you’ll have detailed reports that list every user and their respective permissions, especially those that are relevant to the audit. These reports should highlight the access levels of each user, making it easier to identify any discrepancies or excessive privileges.
This step is critical for documenting the current state of access rights across the organization, providing a baseline for the review process.
- Perform the access assessment
With the reports in hand, reviewers should assess whether the permissions granted to each user align with their daily job responsibilities. This involves scrutinizing each account to determine if the access level is appropriate based on the user’s current role and tasks.
The aim is to identify any instances where access can be reduced or revoked, adhering to the principle of least privilege.
- Remove access for those who don’t need it
Upon identifying users with unnecessary or excessive access, take immediate steps to adjust their permissions accordingly. This may involve revoking access entirely for users who no longer require it or adjusting permissions to better align with current job functions.
- Re-run the access list to ensure access was appropriately removed
Finally, generate a new set of user access reports to verify that the changes have been implemented correctly. This step confirms that access rights have been accurately adjusted according to the review findings, ensuring your organization’s data remains secure.
Best Practices for Conducting User Access Reviews
User access reviews are pivotal for safeguarding your organization’s digital assets. However, the effectiveness of these reviews hinges on how they are conducted. Below, we outline best practices that ensure your UAR process is compliant, strategic, and efficient.
Document your access control & management policy
Begin by clearly documenting your access control and management policies. This documentation should outline how access is granted, reviewed, modified, and revoked. It serves as a reference point for all stakeholders, ensuring that everyone understands the criteria and procedures for access management.
Having a well-documented policy also ensures consistency and accountability across the organization.
Implement the principle of least privilege
At the heart of effective access control is the principle of least privilege, which means granting users only the access necessary to perform their job functions—nothing more, nothing less. Regularly applying this principle through UARs helps minimize potential attack surfaces and reduces the risk of data breaches.
Automate the user access review process
Manual reviews are time-consuming and prone to human error. You must complete them completely and accurately within a specific time period to avoid receiving control deficiencies during audits. However, rushing these processes and rubber stamping can lead to significant security vulnerabilities–and the control deficiencies you’re trying to avoid.
Provide education and training on user access best practices
Educating and training your staff on the importance of cybersecurity and the role of user access reviews is crucial. Awareness programs should cover the principle of least privilege, the risks associated with excessive access, and the procedures for requesting and revoking access.
Training empowers employees to recognize and report potential security concerns, making them active participants in the organization’s security posture.
Challenges Associated with User Access Reviews
User access reviews are essential for maintaining a secure and compliant IT environment. However, organizations often encounter several challenges that can complicate the review process. Addressing these challenges head-on is critical to ensuring that UARs are effective and efficient.
Understanding User Access Reviews vs Access Reviews
The evolving IT landscape demands a broader approach to access reviews, extending beyond traditional user accounts to service accounts, machine identities, and third-party access. Traditional tools often fall short, leaving significant gaps in an organization’s security posture.
Manual or Outdated Review Processes
One of the most significant challenges is the reliance on manual or outdated review processes. Gathering data across diverse systems and verifying access rights by hand is time-consuming and prone to errors.
From pulling access reports from in-scope applications to determining what individuals should be reviewing access for each team or data set, these processes can take several weeks every single quarter.
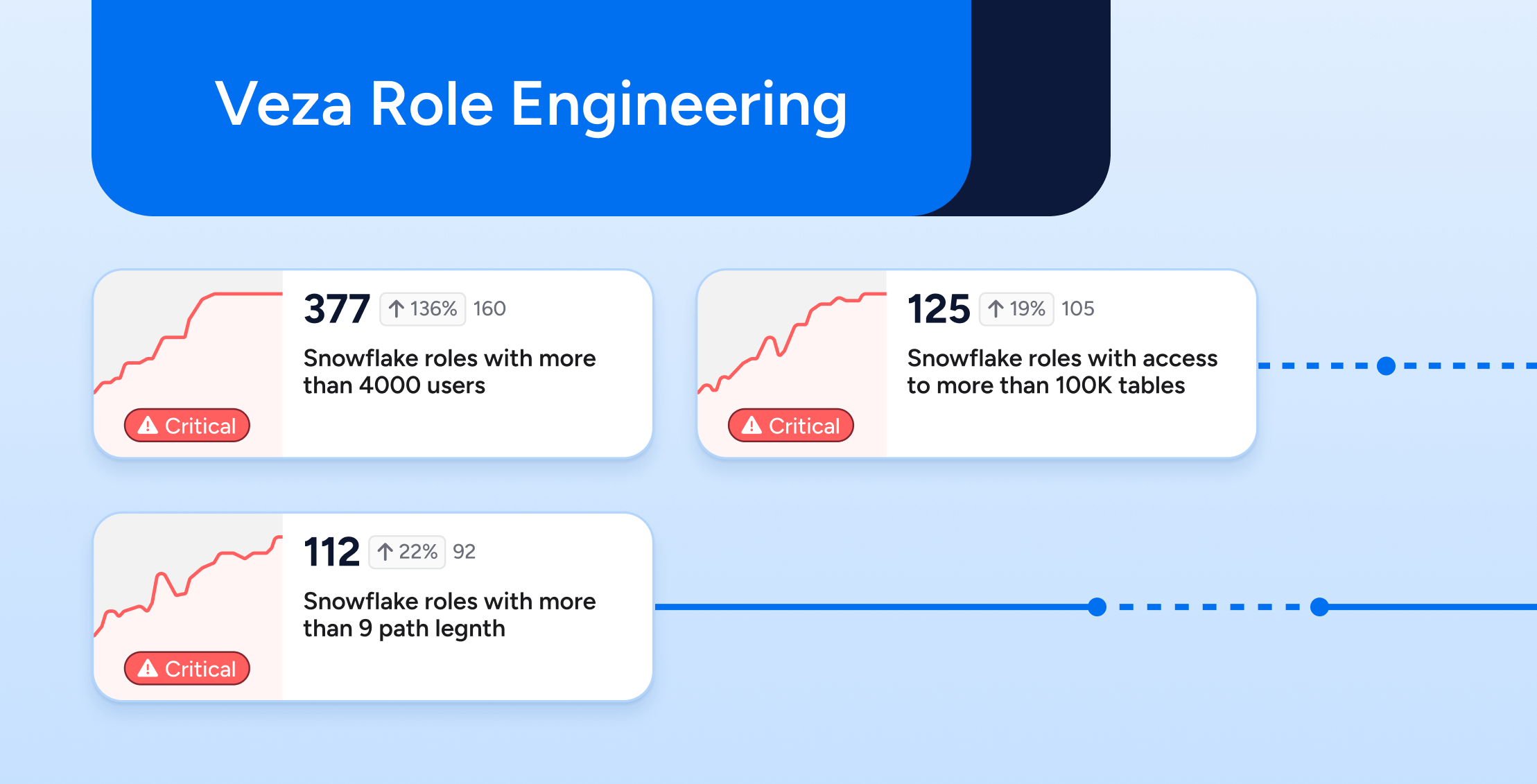
Complex Permissions
The diversity of permission models and the granularity of access rights across different systems can make UARs exceptionally complex. Inaccurate group labeling and the constant evolution of cloud and SaaS permissions exacerbate this complexity, leading to incomplete reviews and overlooked access discrepancies.
Of course, evaluating role names is no longer sufficient: you must look at permissions metadata to get a complete picture.
Lack of Context
Another challenge is the lack of context during the review process. Reviewers may struggle to make informed decisions about access rights without a clear understanding of each user’s role and responsibilities. This can result in overly permissive access or unnecessary restrictions impeding productivity.
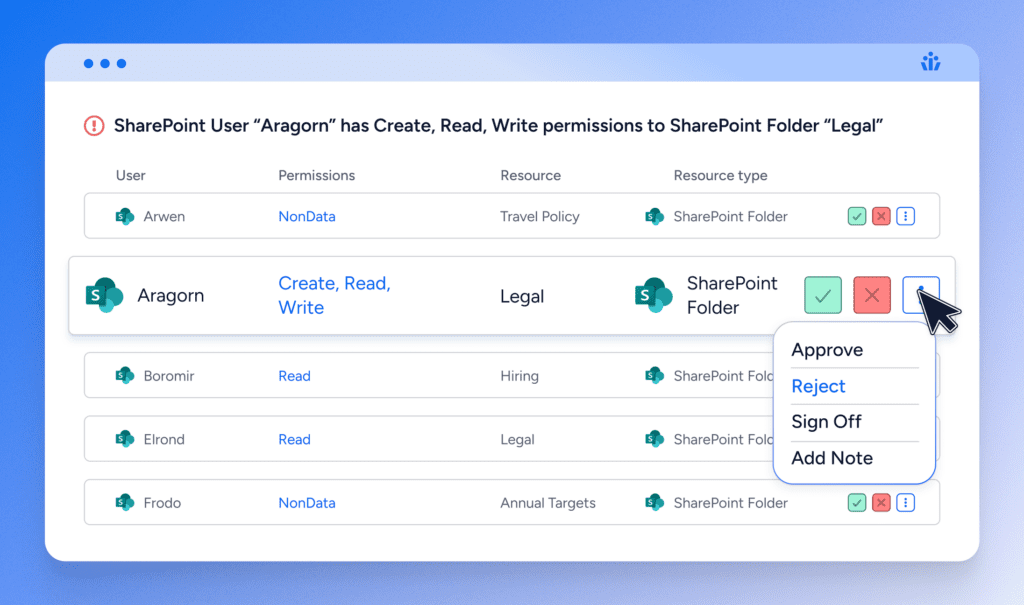
Modernize User Access Review with Intelligent Access
Traditional methods of conducting UARs are no longer sufficient to address the complexity and scale of today’s enterprise IT environments. This is where Veza’s Access Intelligence comes into play, offering a revolutionary approach to streamline and fortify the UAR process.
With Veza, companies gain a unified view of user and non-human identity access, automate manual reviews, and drive compliance with confidence—all while reducing the risk of excessive privileges and data exposure.
Whether you need to auto-approve access, flag violations of segregation of duties, or generate intelligent reviewer suggestions, Veza’s review intelligence delivers precision, scalability, and control.
- Ready to understand what modern UAR should look like? Explore Access Intelligence.
- Want to benchmark your current process? Use The Definitive Checklist for User Access Reviews to identify gaps and next steps.
- Prefer to see it in action? Schedule a personalized demo and experience how Veza can help you take the guesswork out of access reviews.
Let Veza empower you to modernize your approach—combining automation, intelligence, and visibility to safeguard your enterprise at scale