User access reviews are commonly considered painful. With the rise of cloud and SaaS applications, identities and permissions have exploded in complexity, leaving teams scrambling to accurately depict the state of access and successfully pass their audits.
Download our comprehensive checklist for successful access reviews. By following these step-by-step guidelines, you can deliver a UAR program that saves time and money, all while patching the blind spots that plague traditional UARs.
Now that we don’t have to invest so much time and effort into setting up and running access reviews each quarter, our team is able to spend more of our time on our mission to design security processes and configurations that strengthen our overall security posture.
David Morton || Team Lead, Senior Security Engineer, Genesys
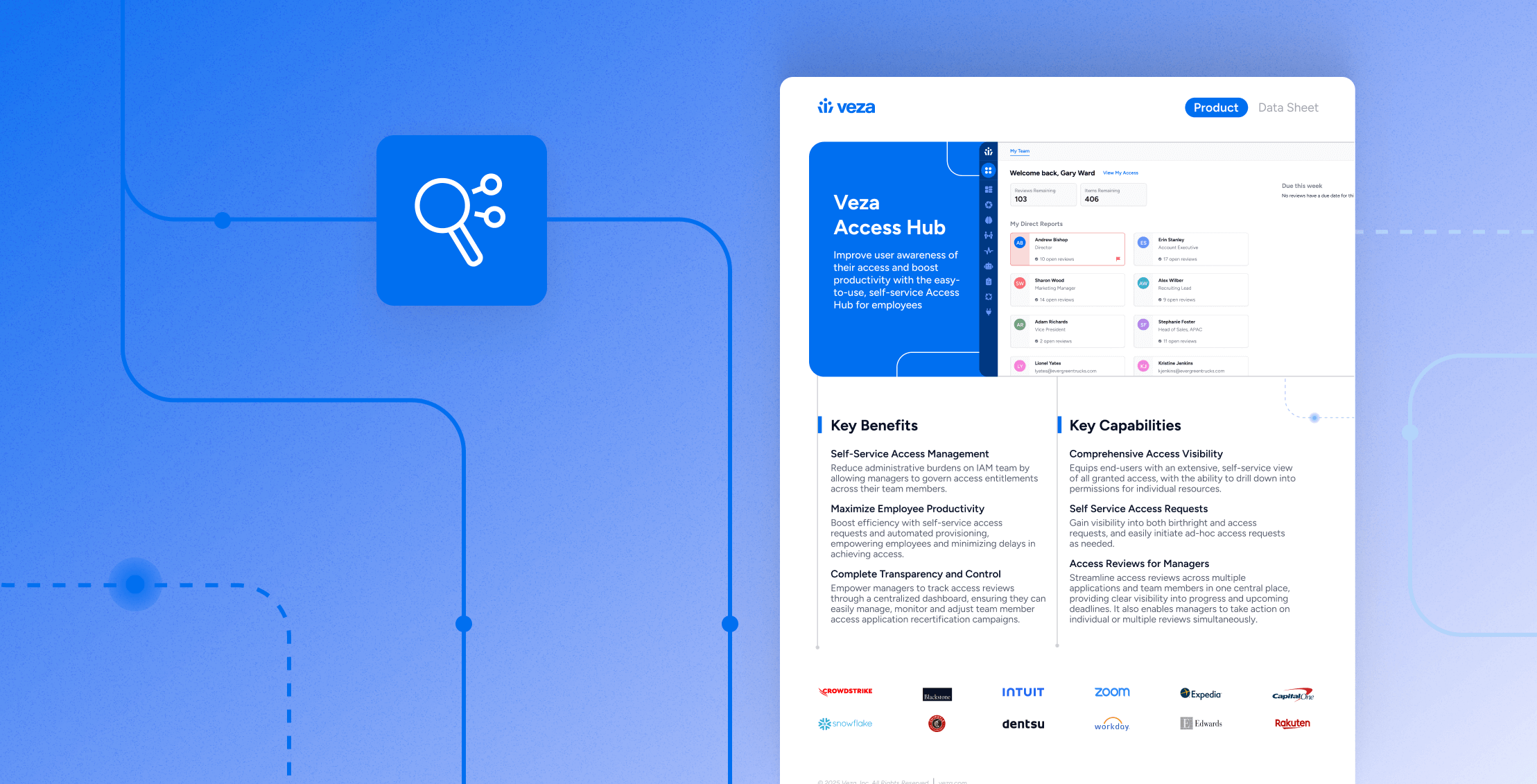
Here at Veza, we’re pushing access reviews even further by enabling organizations to complete successful access reviews in minutes. By leveraging automation, Veza customers can partake in one-click access reviews to view and approve user permissions on mobile or desktop, improving the speed and accuracy of access decisions. These Next-Gen UARs help organizations answer the simple question, “who can take what action on what data?” without the complicated runaround. Learn more
Veza gives us both broader and deeper visibility into who has access to our data, and how they have access to that data, so we can trust and verify that all personnel only have the access they need.
Puneet Bhatnagar || Senior Vice President, Head of IAM – Cybersecurity, Blackstone Technology & Innovations