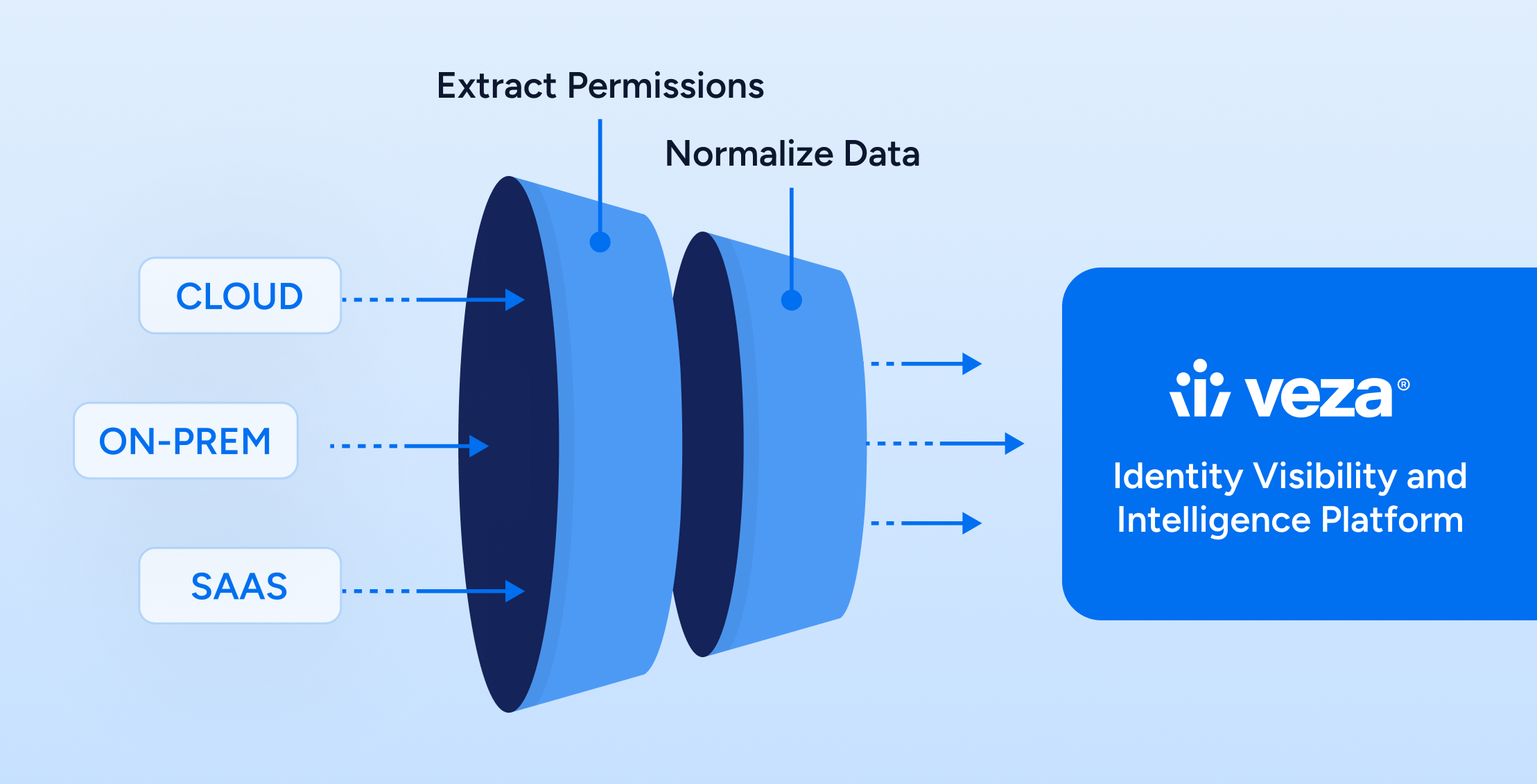
Non-human identity management (NHIM) addresses a real and growing challenge in security and governance. Behind every automated workflow, cloud deployment, API integration, or infrastructure process is a non-human identity (NHI)–a service account, token, credential, or script that grants software and machines access without human involvement.
But even though non-human identities are essential to modern operations, most organizations struggle to manage them effectively. Now outnumbering human users 17 to 1, NHIs usually fall outside traditional IAM controls, making them particularly vulnerable when left unmanaged.
This guide offers clarity on non-human identity management, what NHIs are and why managing them is important. It also briefly covers how to build an effective NHIM program across cloud, SaaS, and hybrid environments. So, whether just beginning to tackle this issue or already working at scale, this guide is the foundation for doing it right.
What are non-human identities?
Non-human identities (NHIs) are digital credentials used by machines and software to access systems, data, and services. They represent everything from API keys and service accounts to automation scripts, containers, and serverless workloads.
Unlike human identities, NHIs don’t log in with passwords or fingerprints. Instead, they operate in the background, connecting systems, triggering workflows, and authenticating machines and services across environments. Today, they’re essential to cloud operations, DevOps pipelines, third-party integrations, and infrastructure automation.
The most common types of non-human identities are:
- Service accounts used by applications to query databases or move data
- API tokens and OAuth credentials that connect SaaS tools and internal services
- Automation scripts that run scheduled jobs or CI/CD pipelines
- Machine identities for containers, virtual machines, and serverless functions
Why are non-human identities created?
Non-human identities are created to let systems operate without human intervention. They allow machines, services, and applications to authenticate and exchange data securely at speeds and scale beyond human capacity.
Most NHIs are created automatically by cloud platforms, orchestration tools, or software integrations. Others are configured manually during development or deployment. Either way, their purpose is to support communication between systems and services.
The common drivers for non-human identity creation are:
- Automation and workflows: CI/CD pipelines, RPA bots, and scheduled jobs rely on credentials to run tasks and interact with systems on their own.
- Cloud infrastructure: Virtual machines, containers, and serverless functions generate identities as they spin up to access compute, storage, or secrets.
- Application and API integrations: SaaS tools and custom applications use API tokens or service accounts to exchange data and trigger business logic.
- DevOps and infrastructure-as-code tools: Platforms like Terraform, Kubernetes, and Ansible create and manage identities to provision, configure, and deploy resources.
- Internal services and microservices: Large applications are often composed of dozens of interconnected services, each with its own identity to support secure internal communication.
Often short-lived, these identities are frequently created without oversight and rarely removed when their role ends. Unfortunately, that also makes them one of the most dynamic and difficult parts of the identity environment to manage.
Examples of non-human identities
Non-human identities weave throughout nearly every system and workflow in a modern enterprise. While some are created automatically by infrastructure and automation tools, others are introduced through SaaS integrations, internal services, or DevOps pipelines. All carry access–many with permissions misaligned to current usage or excluded from governance entirely.
The most common examples of non-human identities are:
- Service accounts are used by applications, automations, and infrastructure to connect with databases, systems, or APIs.
- API keys and tokens that grant programmatic access between services and systems are frequently embedded in scripts or stored in plaintext.
- Cloud and workload identities are created automatically by containers, serverless functions, and virtual machines to authenticate with other systems.
- System and operating system accounts are created by default to facilitate background services and administrative tasks at the OS level.
- Application and integration accounts that allow applications and services to interact internally or with external tools using OAuth tokens, custom connectors, or service-level messaging accounts.
Human vs. non-human identities
Human and non-human identities both grant access to systems and data, but they’re built for fundamentally different use cases and require different approaches to governance.
- Human identities belong to individual people, managed through centralized onboarding and offboarding, governed by role-based access, and authenticated via passwords or biometrics.
- Non-human identities belong to software or machines, are generated automatically, rarely have clear ownership, and rely on API keys or tokens, making them harder to track, control, and secure.
The key differences are:
- Creation: Humans onboard formally; NHIs are provisioned automatically and continuously.
- Ownership: Humans have defined owners; NHIs often don’t.
- Authentication: Humans use passwords/MFA; NHIs use API keys or tokens.
- Lifecycle: Human identities follow predictable patterns; NHIs are dynamic and ephemeral.
- Visibility: Human identities are centrally visible; NHIs are dispersed across environments.
Non-human vs. machine identities
Non-human identities and machine identities are closely related, but not the same. All machine identities are non-human, but not all non-human identities are machines.
- Machine identities specifically represent workloads and infrastructure components (containers, VMs, IoT devices) managed primarily by infrastructure teams and authenticated with certificates or secure keys.
- Non-human identities represent a broader category (including service accounts, API tokens, and automation scripts) often provisioned by developers or automation tools and authenticated via simpler methods like tokens or embedded secrets.
The key differences are:
- Scope: Machine identities represent infrastructure; NHIs also include services, scripts, and APIs.
- Function: Machine identities facilitate secure infrastructure communication; NHIs support broader automation and integration tasks.
- Credential type: Machine identities use cryptographic certificates; NHIs commonly use API keys or tokens.
- Management: Machine identities are infrastructure-driven; broader NHIs are managed across multiple teams, often informally.
- Governance: Machine identities typically follow structured lifecycle controls; broader NHIs often lack consistent oversight.
What is non-human identity management?
Non-human identity management (NHIM) is the process of governing access for digital identities that operate without a person behind them. Like human users, non-human identities require permissions. But they often fall outside the reach of traditional identity governance because they’re created by tools, not people.
NHIM provides a structured way to manage them by discovering where they exist, assigning ownership, limiting what they can do, and removing access when it’s no longer needed.
In practice, NHIM means:
- Making sure a deployment script can configure a server, but not access sensitive data
- Limiting a service account’s permissions to just the systems it needs to reach
- Detecting and removing an old integration token that hasn’t been used in months
- Preventing a short-lived container identity from persisting beyond its session
- Auditing a high-privilege API key used by a third-party platform
Access is controlled, visible, and aligned with purpose when non-human identity management is in place. But when it isn’t, credentials can accumulate, permissions can drift, and risk can become harder to quantify, let alone contain.
Why is non-human identity management important?
Non-human identities now outnumber human users dramatically. A 2025 global study found enterprises average 82 machine identities per employee–a ratio that climbs to 40,000 to 1 in cloud-native environments. Yet these identities rarely receive the same scrutiny or controls as human accounts.
The identity attack surface
According to Microsoft, fewer than 5% of permissions granted to non-human identities are used, yet over half are considered high-risk. In cloud environments, 99% of service accounts are over-permissioned, many at the administrative level.
This broad access makes non-human identities an attractive target for attackers. Verizon’s 2025 DBIR found that credential abuse remains the top initial attack vector, frequently involving compromised API keys, service accounts, or automation credentials. One recent breach forced the rotation of over 5,000 compromised cloud secrets after attackers extracted credentials from helpdesk logs.
The governance and compliance gap
Regulatory pressure is growing with security risks. PCI DSS 4.0 mandates least privilege controls and regular access reviews specifically for system and application accounts. HIPAA’s Security Rule and GDPR also require auditing of every identity (human or otherwise) that touches sensitive data. Yet traditional audits still emphasize human users, leaving many non-human identities unmonitored.
How non-human identity management helps
Effective NHIM addresses these security and compliance risks directly so organizations can:
- Clearly identify the purpose and necessity of each non-human identity
- Limit permissions to precisely match operational needs
- Assign clear accountability for each identity
- Continuously validate permissions to support Zero Trust
- Align security, engineering, and compliance teams through shared insights
How to manage non-human identities
Effective non-human identity management brings structure, accountability, and automation to access that has historically gone ungoverned. Each stage plays a role in reducing risk and aligning access with actual need.
The steps to manage non-human identities are:
- Discover and classify: Identify non-human identities across cloud, SaaS, on-prem, and development environments, and categorize them by type, function, and system.
- Provision with intent: Assign only the access required for each identity’s purpose, scoped to specific systems, actions, or environments.
- Assign ownership: Link every identity to a responsible person or team to regularly review credentials, maintain secure practices, and promptly remove unnecessary access.
- Monitor and analyze usage: Track activity across environments to detect anomalies, validate access patterns, and identify unused or misaligned permissions.
- Store and rotate credentials securely: Vault API keys, tokens, and certifications, rotate them on a defined schedule, and eliminate hardcoded or long-lived secrets.
- Maintain audit and review readiness: Record ownership, permissions, and activity to support access reviews and meet internal and regulatory requirements.
- Decommission when access is no longer needed: Detect inactive identities, revoke credentials, and remove system access to reduce sprawl and close lingering access paths.
Discovery, access control, ownership, and decommissioning all rely on consistent decisions across environments, and those decisions only work when backed by clear policies, real usage data, and tools built for scale. The next step is turning that process into practice, starting with the principles that keep access clean, controlled, and easy to govern.
Challenges of managing non-human identities
Even organizations committed to managing non-human identities struggle with practical execution. But operational complexity is usually the issue, not lack of intent. Because NHIs span diverse systems, rely on disconnected tools, and rarely align neatly with traditional identity workflows.
The most common challenges with non-human identity management are:
Fragmented inventory
Teams typically track non-human identities using scattered tools (like secrets managers, cloud IAM consoles, spreadsheets, or custom scripts) which rarely offer a single, real-time view. Identifying active identities, their access, or their usage becomes a tedious manual task rather than a structured process as a result.
Disconnected tooling
Secrets management, identity providers, infrastructure-as-code scripts, and spreadsheets all hold parts of the access puzzle, but seldom integrate. This fragmentation creates gaps in understanding and governance, forcing manual reconciliation and making it difficult to enforce consistent policies or spot risky configurations.
Unclear ownership
Without a direct tie to individuals, non-human identities frequently lack clear accountability. Credentials remain active long after they’re needed, simply because no team or individual owns the process of reviewing or removing them. This lack of clear ownership translates into persistent, unmanaged access.
Inconsistent review practices
Periodic access reviews typically focus on human identities, leaving machine identities overlooked or inadequately reviewed. Even when included, non-human identities lack enough context, causing reviewers to default to rubber-stamping permissions rather than making informed decisions.
Cross-team misalignment
Non-human identity management cuts across security, DevOps, cloud, and application teams, each with different priorities and tools. Security wants controls, engineering wants flexibility, and IAM wants standardized processes. Without coordinated processes, non-human access is often provisioned quickly, but rarely revisited, allowing permissions to accumulate and drift unchecked over time.
While these challenges are significant, proven best practices can help organizations simplify management and gain greater control. Here’s what leading organizations are doing to overcome these obstacles.
Non-human identity management best practices
Managing non-human identities effectively means bringing structure, accountability, and automation to a category of access that has historically gone ungoverned. The following best practices reflect what leading organizations are doing to regain control, without slowing teams down.
Apply Zero Trust to non-human access
Zero Trust applies to every identity, human and machine. Each request should be verified, scoped to the task, and continuously monitored, regardless of where it originates. As NIST’s Cybersecurity Framework 2.0 notes, non-person entities must be governed as “first-class identities.” Verification, policy enforcement, and visibility are non-negotiable. To support Zero Trust in NHIM:
- Use short-lived, limited-access credentials with clearly defined permissions
- Route access through API gateways or brokers for verification and logging
- Grant temporary access only when needed and remove it automatically afterward
- Monitor all access attempts, especially from service accounts or automation tools
- Treat privileged machine accounts with the same scrutiny as privileged user accounts
Enforce least privilege from the start
Many non-human identities are granted broad access at creation and never reviewed. Defining scope upfront prevents access drift and keeps permissions aligned with need–the earlier access is scoped, the easier it is to govern. Least privilege works best when it’s the default, not a correction. To enforce least privilege:
- Define roles based on system function, not team or department
- Remove default admin access from all machine identities
- Create reusable permission sets for common tasks
- Build access reviews into the provisioning process, not as a follow-up
- Schedule recurring reviews to catch unnecessary privilege accumulation
Prevent excessive access before it spreads
Over-permissioned accounts are one of the most common and preventable sources of identity risk. Left unchecked, they can introduce exposure that teams may not even know exists. Catching excessive access early helps reduce cleanup later, and keeps governance focused on the highest-risk identities. To limit overexposure:
- Require justification when broad or cross-system access is requested
- Enforce expiration for time-bound roles and temporary credentials
- Block inheritance of roles across unrelated environments or systems
- Review access after major changes in infrastructure or application scope
- Use automated controls to flag and review unexpected permissions
Monitor usage continuously
Non-human identities operate on schedules, APIs, and event triggers. They may not generate login events like human users, but they leave behind patterns. Usage data is one of the clearest indicators of whether an identity still serves a valid purpose. To monitor behaviour effectively:
- Define normal activity for each identity so oddities stand out
- Flag deviations in access frequency, scope, or timing
- Track credential reuse across environments or workloads
- Alert on unusual activity, like new system access or elevated commands
- Rotate or revoke credentials immediately if misuse is suspected
Audit inventories regularly
Identities pile up without regular audits, especially those tied to past integrations, deprecated services, or forgotten workflows. Auditing is how to stay ahead of unmanaged access. To keep identity inventories actionable:
- Maintain a centralized, cross-system list of all non-human identities
- Assign an owner to every identity, including those created automatically
- Review usage at set intervals to detect inactive or expired accounts
- Flag identities with no recent activity or undefined scope
- Automate cleanup workflows wherever possible
Use a platform designed for non-human identity management
Manual tools and spreadsheets can’t scale. Secrets managers aren’t enough. A purpose-built NHIM platform can help security, IAM, and engineering teams work from the same access picture and govern non-human identities with precision. The best NHIM platform can:
- Discover all non-human identities across cloud, SaaS, on-prem, and internal tools
- Correlate each identity with permissions, owners, and systems
- Analyze what each identity can actually do, not just what it was assigned
- Support rotation, expiration, and removal workflows based on policy and usage
- Enable access reviews, audit tracking, and provisioning without manual effort
Adopting these best practices can dramatically improve an organization’s identity security posture. But success requires the right approach and the right platform to turn theory into practice.
Manage non-human identities with clarity and control
Non-human identities have become one of the largest and least understood parts of the enterprise access surface today. Yet, even though they don’t follow the same rules as human users, they often operate with real, privileged, unmonitored access. That makes managing them less about patching a gap and more about rethinking how identity governance works at scale.
Non-human identity management tools like Veza can help bring structure to that process. By discovering accounts across environments, mapping what they can access, and showing who’s responsible for them, Veza supports access decisions that are grounded in context. It provides the visibility, structure, and consistency needed to manage non-human identities at scale, so teams can reduce risk, meet compliance requirements, and operate with confidence. Because when access is governed with clarity, security doesn’t have to come at the cost of speed.
Ready to Take Control of Your Non-Human Identities?
Whether you’re just starting to explore the NHI landscape or you’re actively looking to tighten the reins on machine identity sprawl, Veza has you covered.
- New to NHIs? Start with the fundamentals and get smart on what machine identities are, why they matter, and how they impact your security posture.
- Building your strategy? Explore our NHI Security capabilities to understand how Veza empowers you to discover, govern, and control NHIs with precision.
- Dig Deeper and review a Non-Human Identity Management Use Case. See how organizations are getting control over sprawling machine access with a purpose-built approach.
- See it in Action: Schedule a live demo and see firsthand how Veza helps you operationalize least privilege for every identity—human or not.
Addendum: Non-human identity management FAQs
What is an example of non-human identity management?
Non-human identity management means overseeing digital accounts used by machines or software. For example, managing a cloud service account that connects a storage bucket to a processing tool involves tracking its access, assigning ownership, and removing it when no longer needed.
Why are non-human identities created?
Non-human identities are created to help systems, services, and software interact without human input. They enable automation, connect cloud infrastructure, integrate APIs, and support DevOps pipelines that run continuously or at scale.
How do security teams prevent non-human identity breaches?
Security teams prevent non-human identity breaches by identifying every identity, restricting access to only what’s needed, rotating credentials regularly, monitoring usage patterns, and running automated access reviews to detect and remove outdated or risky accounts.
Non-human identity management terms to know
Non-human accounts
Non-human accounts are digital identities used by software, scripts, or devices to access systems or data without human involvement.
Non-person entities
Non-person entities are identities not tied to individuals, including those used by services, bots, APIs, workloads, and devices.
Non-human privileged accounts
Non-human privileged accounts are machine or software identities with elevated access to perform administrative or sensitive tasks.
Application accounts
Application accounts are identities created for software applications to securely access data, databases, APIs, or other systems.
Machine identities
Machine identities are credentials assigned to devices, containers, or workloads that authenticate them and allow secure communication.
About the Authors
This article was developed in collaboration between Mariah Brooks, an independent consultant and researcher focused on identity security, and Matthew Romero, Technical Product Marketing Manager at Veza.
Mariah brings deep experience translating complex technical challenges into practical, real-world insight. With a background spanning identity governance, cyber risk, and responsible AI, she’s spent 5 years working alongside CISOs and security architects to unpack emerging issues like Non-Human Identities (NHI). Her clarity, context, and credibility make her a trusted voice for security leaders navigating high-stakes access decisions.
Matthew brings a strategic marketing lens grounded in the realities of modern enterprise security. At Veza, he helps define go-to-market positioning for identity-first security solutions, bridging the gap between technical innovation and customer relevance. His work focuses on connecting product capabilities to the risks and operational demands that security teams face every day.
Learn more about their work:
Mariah Brooks – LinkedIn
Matthew Romero – LinkedIn