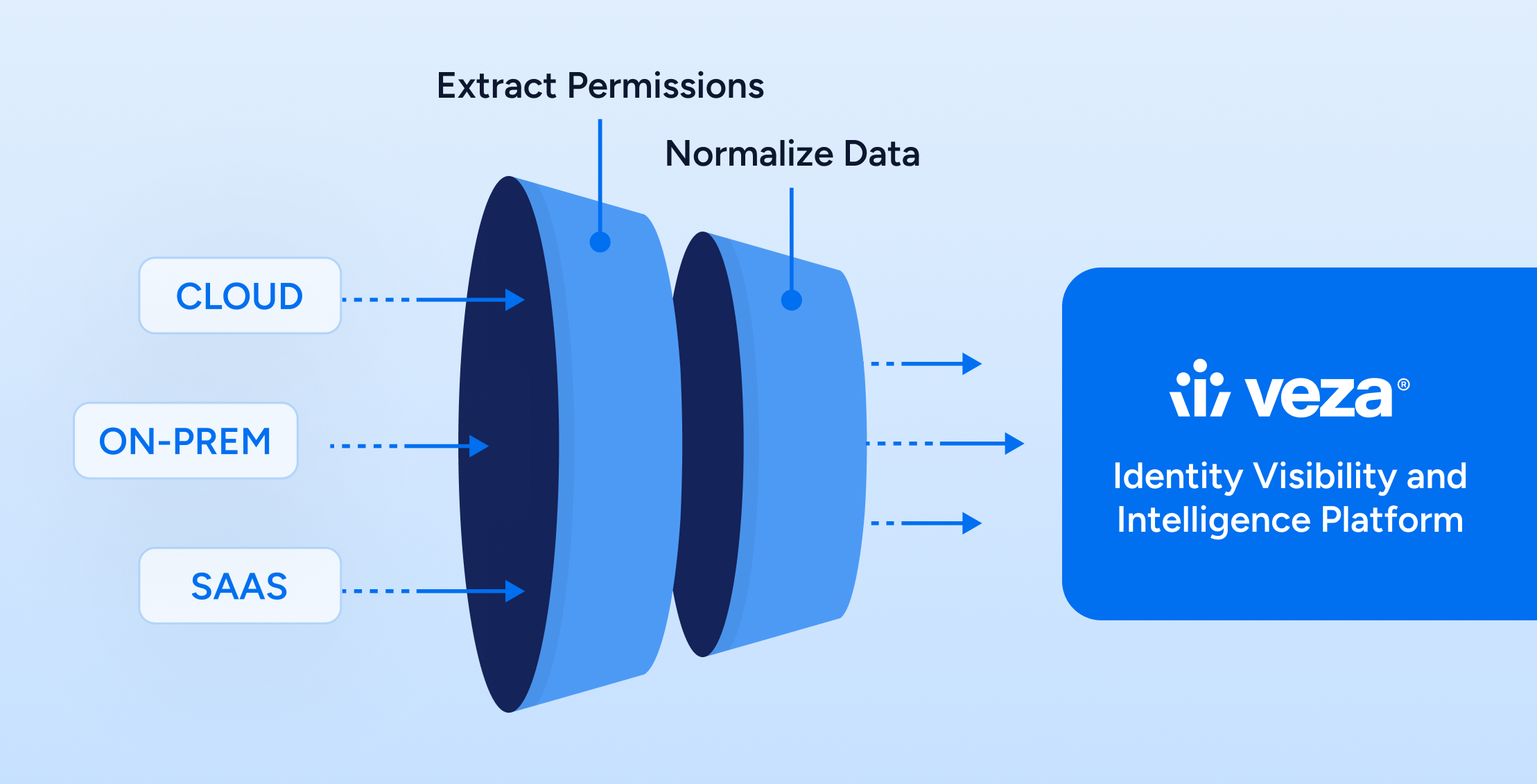
We founded Veza based on the insight that identity itself is fundamentally flawed. The entire identity industry has been focused on moving identity to the cloud and building on authentication frameworks such as SAML – a framework that was never designed for the reality of modern identity governance – instead of leveraging the power of identity data (IAM, RBAC, ACL, etc.) to build least privilege access to data.
Here at Veza, we are strongly committed to helping organizations secure access to data – and, doing so starts with making the principle of least privilege attainable at scale. There’s already been enough said and written about the importance of “data” as organizations accelerate innovations and build products to grow their businesses. However, these initiatives must be rooted in serving customers’ needs and companies must do everything it takes to operate while keeping their customers’ trust front and center. To do so, organizations must operate with the least privilege mindset as it relates to access to data.
We believe that access to data is rooted in understanding “who can take what action on what data” – and, the purest form of truth to answer this question lies within the identities and associated permissions to data everywhere (SaaS apps, databases, cloud services, etc.). Identity, IAM, and permissions are business enablers: any new product or project starts with identity. We all have seen the number of cyberattacks continue to grow and, unfortunately, we predict that 2024 will come with further acceleration. As generative AI increases the speed and volume of cyber attacks while the world continues to adopt SaaS cloud native services, breaches will be inevitable. Threat actors are increasingly targeting identities, credentials, and bad permissions as the core vector to attack and to get access to data.
These insights play a key role in shaping the world of identity-first security in 2024 → beyond, as well as our roadmap. Here at Veza, we’re continually building our Access Control Platform in a bold way that enables identity-first security innovations around the world (in 2023, alone, we released new features, new enhancements, and usability improvements every week of the year!), leverages automation to master access governance and acts as a catalyst toward least privilege at the enterprise level. With identity on the defense more than ever, here’s what we anticipate to see industry-wide in 2024:
Forecast 1: Generative AI will increase the speed and volume of cyber attacks.
AI is going to drastically change cybersecurity forever (it already has). In fact, the FBI has already issued AI cyber warnings. According to Gartner, AI trust, risk and security management (AI TRiSM) “supports AI model governance, trustworthiness, fairness, reliability, robustness, transparency and data protection.” Organizations who use AI models managed with TRiSM may experience game changing results: better strategic decision making aided by more accurate information, the ability to quickly pivot to remain competitive amongst a growing market, boons to data security, risk management and access governance at scale, and much more.
However, when enterprises use AI models that are not managed with AI TRiSM, the negative results can quickly create disaster: misleading information leading to short-sighted – or, entirely incorrect business decisions – as well as increased attack surface. For example, a recent attack confirms that the training data memorized by ChatGPT can be extracted and leveraged, suggesting that some of OpenAI’s tools may not be subject to TRiSM. Without proper controls and safeguards in place, enterprises may find their sensitive data compromised. Generative AI needs to be managed by Access Intelligence – modern access governance strategies and solutions that are designed to visualize and manage identity governance automatically, enabling continuous least privilege without the risk of human error.
Forecast 2: Ransomware will continue to accelerate and attacks on identity and IAM infrastructure will increase.
Similarly to how AI can power the enterprise, it unfortunately gives threat actors a leg up, as well. With the ability for generative AI tools to produce inaccurate media, create deep fakes and ultimately produce a much higher quantity of seemingly high-quality content, we expect to see identity-related attacks – primarily phishing attempts – rise significantly. Traditionally, the biggest hindrance of phishing attempts was resources. Phishing is a numbers game, meaning that if enough emails, voicemails, false websites and download links hit the population, a certain amount will fall for the bait. With AI now giving cyber attackers the ability to create an unlimited amount of these phishing baits in record time, the number of identity-related attacks is sure to rise.
To combat this, we expect enterprises to make bold moves to overhaul identity in 2024, including tying identity products and processes directly to business initiatives to garner more buy-in across the organization, increasing training, going passwordless and employing modern identity-first security solutions (i.e. adding “automation” and “intelligence” to IGA, adding “monitoring” to privilege access management, from identity governance to identity threat, etc.) to identify and block bad actor attacks.
Forecast 3: Companies will accumulate “access debt,” and CISOs will tackle security in the data lake.
Now that companies recognize the value of data lakes and data warehouse architectures, they are leveraging them all. However, the data lake remains the preferred storage option. With various analysts and data scientists accessing the data lake for so many purposes, it is harder than ever to configure permissions. Who can take what action on data in the lake? IT teams receive requests for access and feel pressured to respond. After being inundated with hundreds of requests, they may start clicking “allow” so as not to impede the speed of business, even if the access granted is over permissive. The inevitable result? Companies will collect “access debt.” In 2024, CISOs will start looking for ways to monitor and trim that debt.
Forecast 4: Identity-first security will take off in the enterprise as CISOs double-down on identity access debt.
Data democratization is here, distributed across a hybrid cloud that includes transactional data systems like Active Directory, Oracle, and SAP. As companies try to map which identities (people) can access which data, they’ll see that the old way of rules and policy-based engines can no longer handle the volume. Enterprises will find it difficult to make real progress on their “least privilege” intentions and objectives. In response, security companies will launch new capabilities using AI and ML to prune access on a continuous basis.
CIOs and CISOs will rush to mature and expand IAM while adapting to new identity use cases: identity threat, identity posture, and identity SecOps (beyond the usual use cases of governance, privileged access and storage).
Forecast 5: A lingua franca for identity data, permissions, and authorization data sets will emerge.
RBAC (role-based access control), a method of restricting network access based on the roles of individual employees within an organization, has always brought challenges. It’s complex, technical, manual, and unique to every system. Other types of access control, like ABAC (attribute based access control) add to the complexity. In 2024, identity professionals will turn to authorization technology as a better way to control who can read or delete data. This is especially important for larger organizations with hundreds or thousands of users. Common standards will begin to emerge around a universal model for access controls (RBAC, ABAC, ACL, IAM, etc.).
Although authentication tools like SSO and MFA will still be critical, the “Beyond-SSO and MFA” era will accelerate. IAM modernization and identity will take the center stage of every vendor’s security strategy in 2024. Every security vendor will rush to accelerate product innovations and partnerships in order to meet the IAM needs of their end customers. Hyper-scalers will accelerate initiatives that launch IAM authorization as standalone service offerings.
Embracing 2024 with Intelligent Access
We are extremely optimistic and bullish that 2024 will be a year where CIOs, CISO, CFOs, and CEOs will all come together to take a hard look at their identity initiatives: modernizing the use of existing identity tools and products, consolidating multiple tools into a unified-platform approach, optimizing for “validate the value” with adoption geared to time-to-value, and leveraging the power of identity “data” to go beyond traditional IAM – so they can finally, truly operationalize least privilege.
About Veza
Veza is the Access Control Platform that enables identity governance. The platform helps companies to monitor privilege, investigate identity threats, automate access reviews, and bring access governance to enterprise resources like SaaS apps, data systems, cloud services, infrastructure services, and custom apps.