Featured Resources
-
 Report
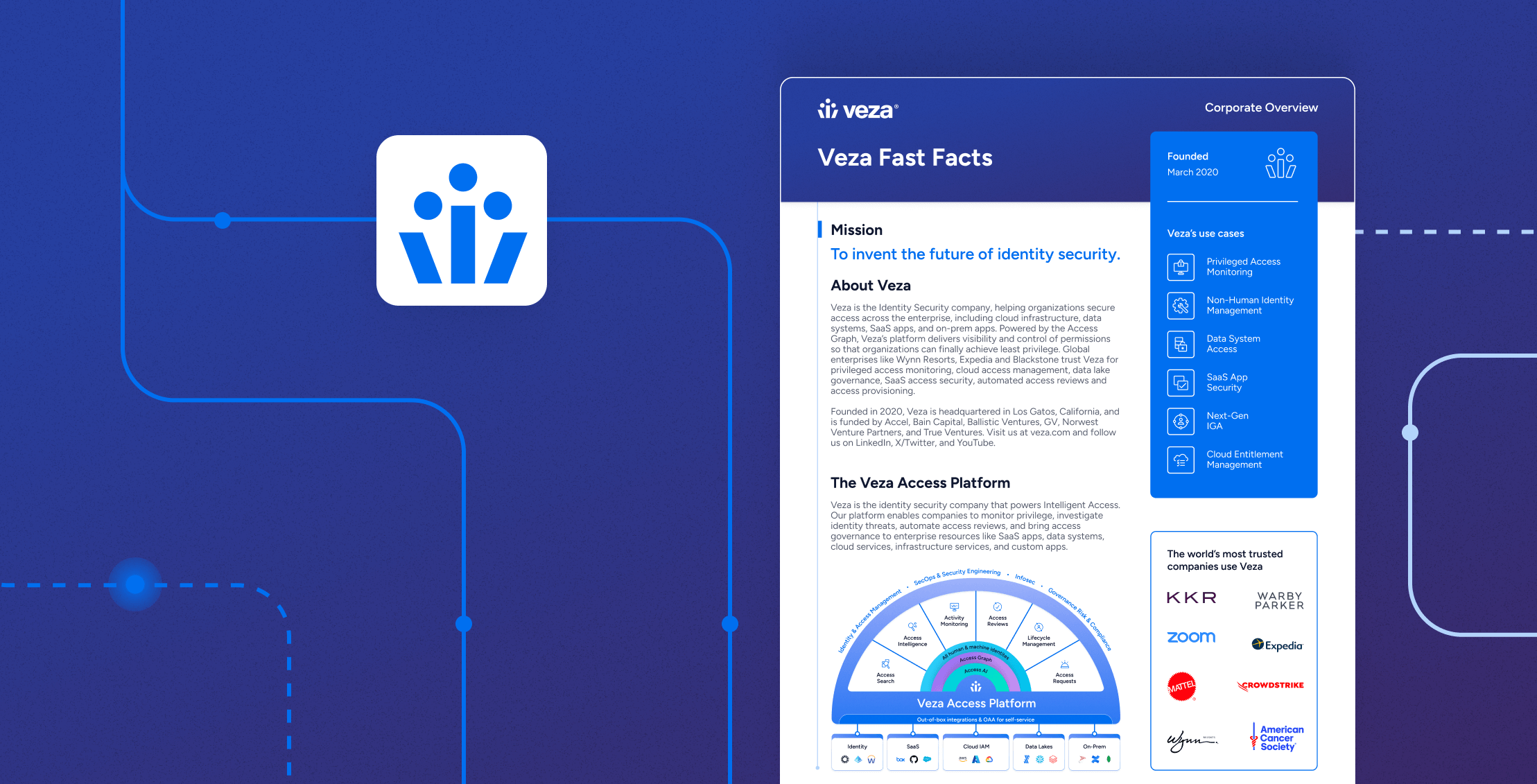
ReportThe State of Identity & Access Report 2026
Uncover how identities, permissions, and non-human accounts really behave with Veza’s State of Access report and benchmark your identity security posture. -
 Report
ReportVeza Named NHI Leader In The Frost Radar™ Report For 2025
Frost & Sullivan has recognized Veza as a leader in their latest report, Frost Radar™: Non-Human Identity Solutions, with standout scores in both Innovation and Growth. This independent validation highlights how Veza is redefining the way enterprises discover, govern, and secure machine and workload identities. As machine identities multiply far faster than human users, organizations […]
Explore our resources
-
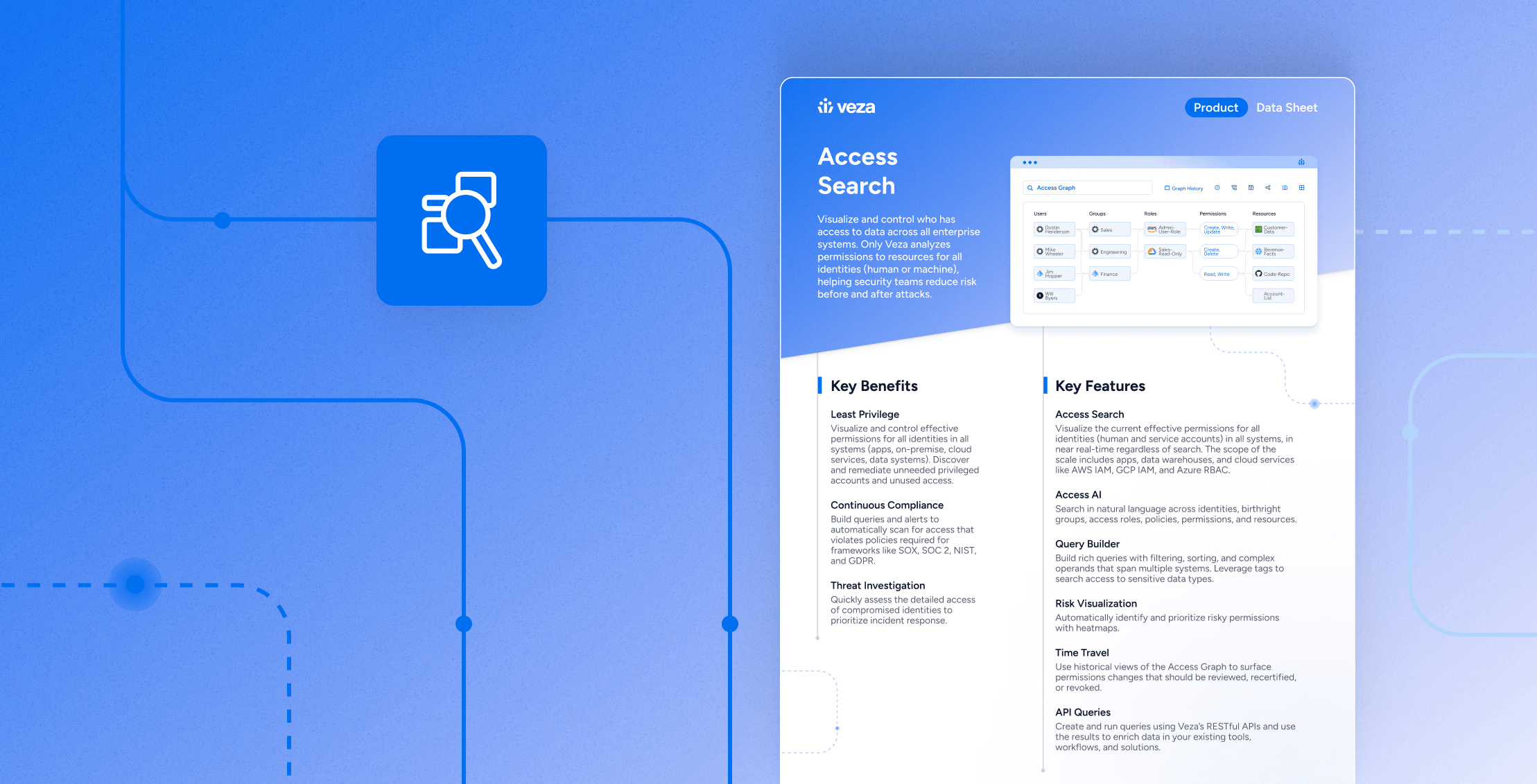
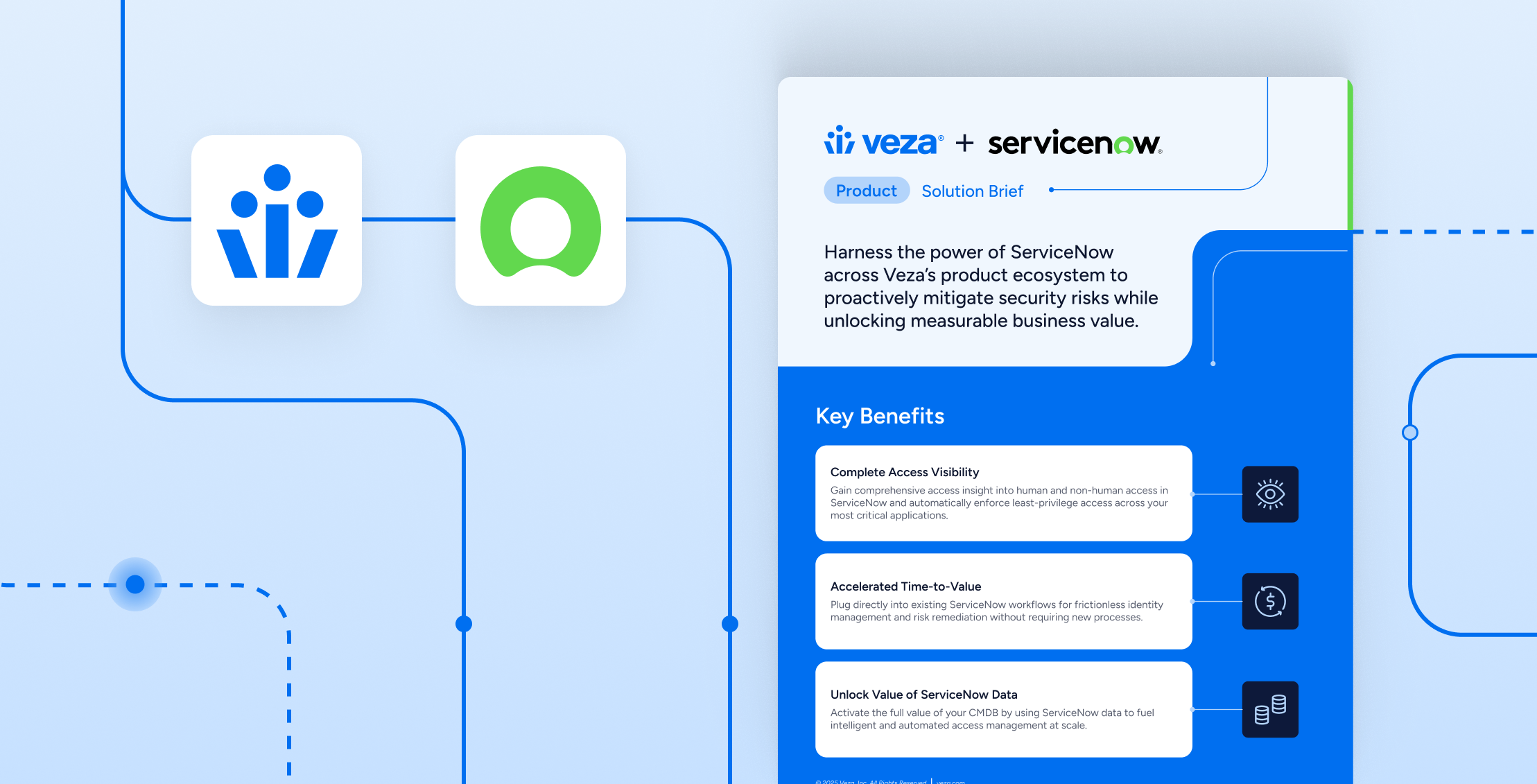 Solution Brief
Solution BriefVeza + ServiceNow
Learn more -
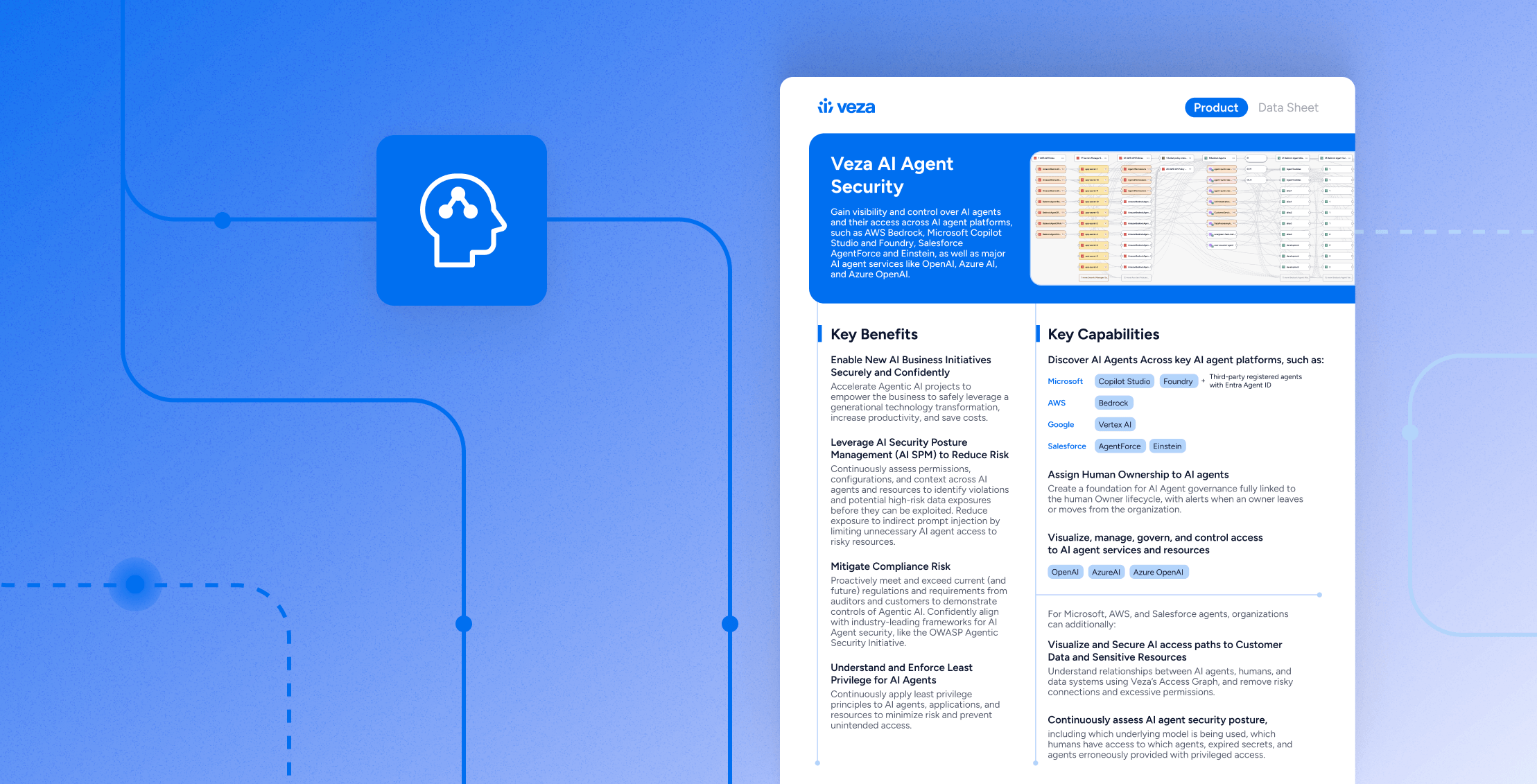 Data Sheet
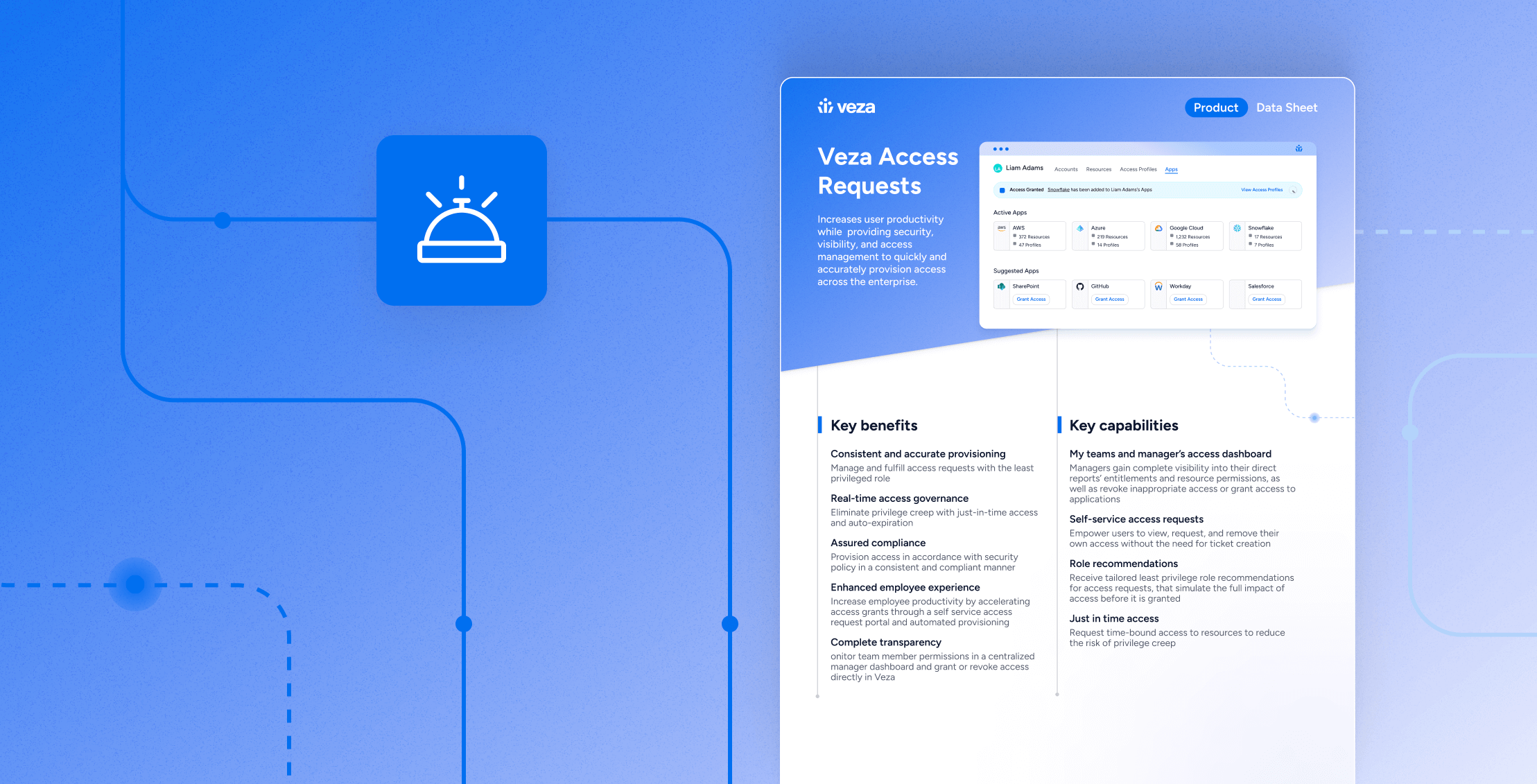
Data SheetAI Agent Security Data Sheet | Veza
Learn more -
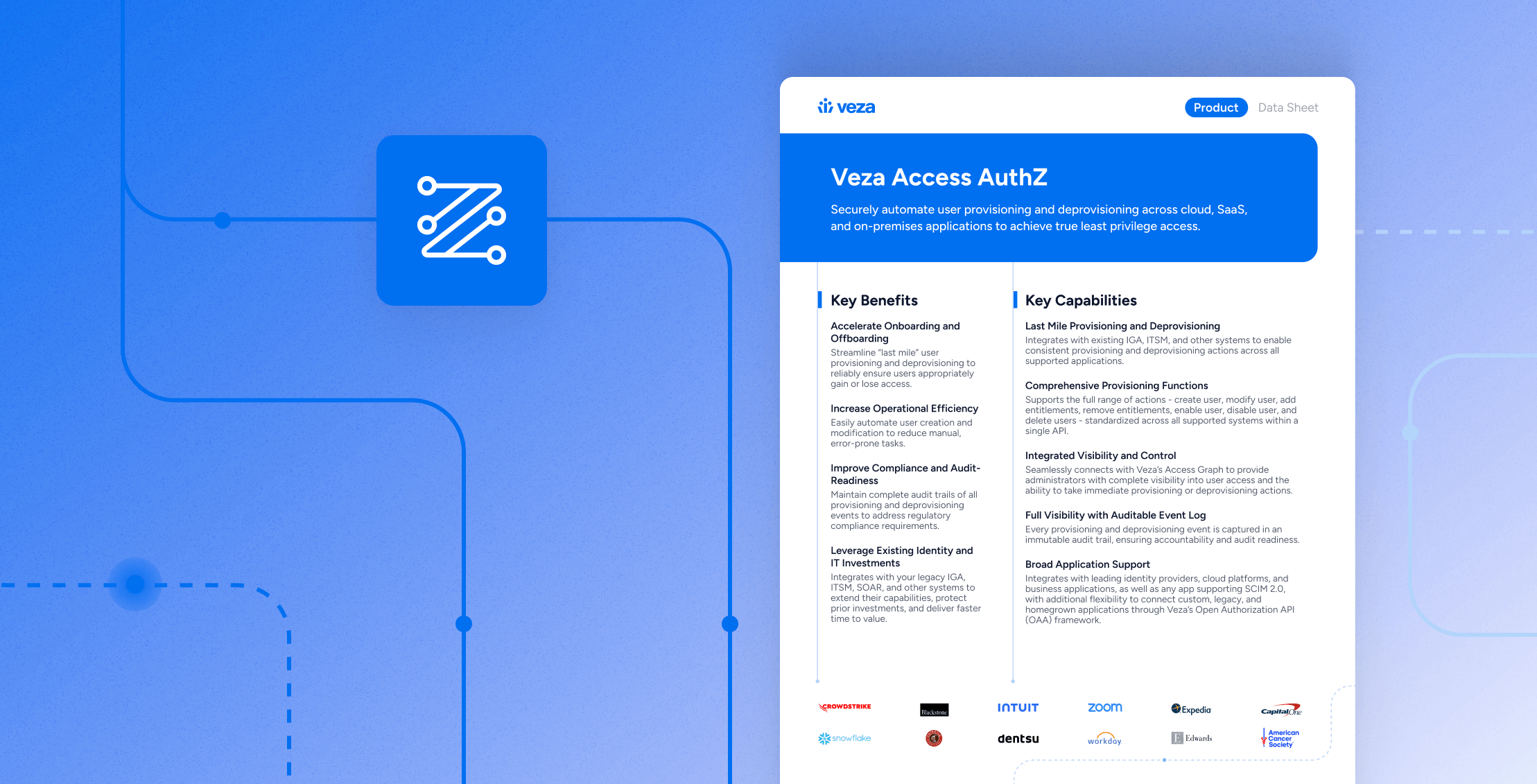 Data Sheet
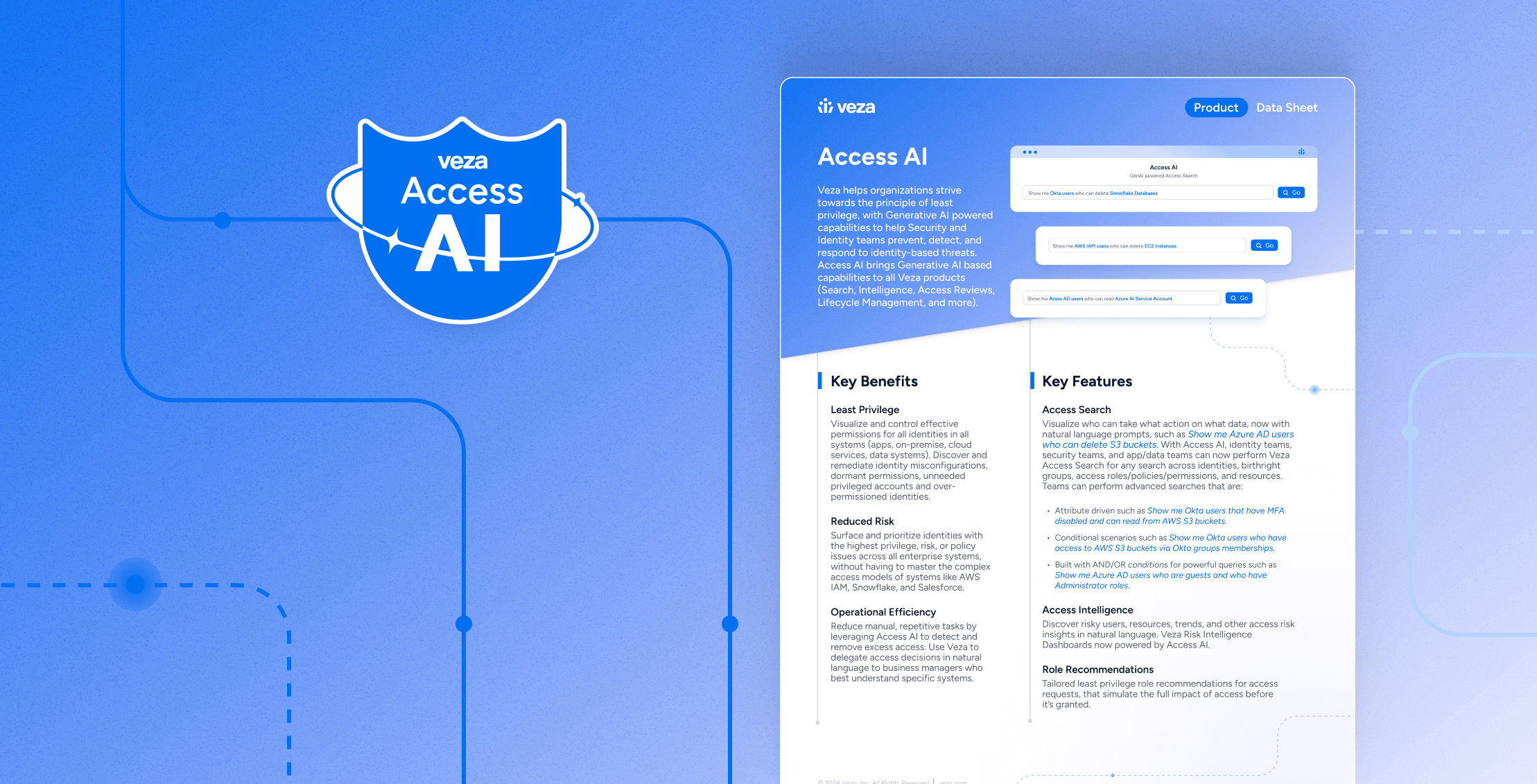
Data SheetAccess AuthZ – Data Sheet
Learn more -
 EBook
EBookRedefining Cybersecurity for the Agentic Era: Introducing AISPM
Learn more -
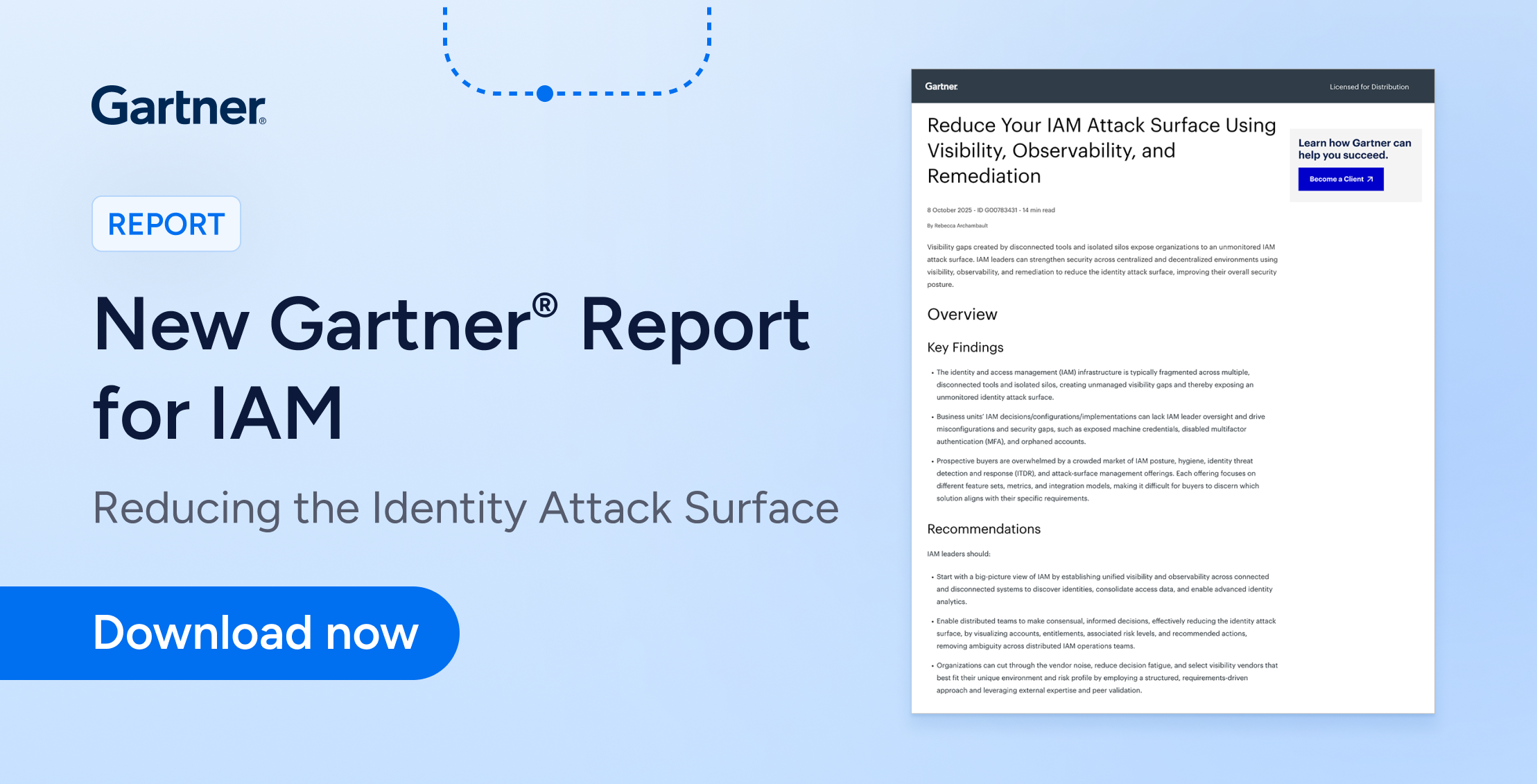 Report
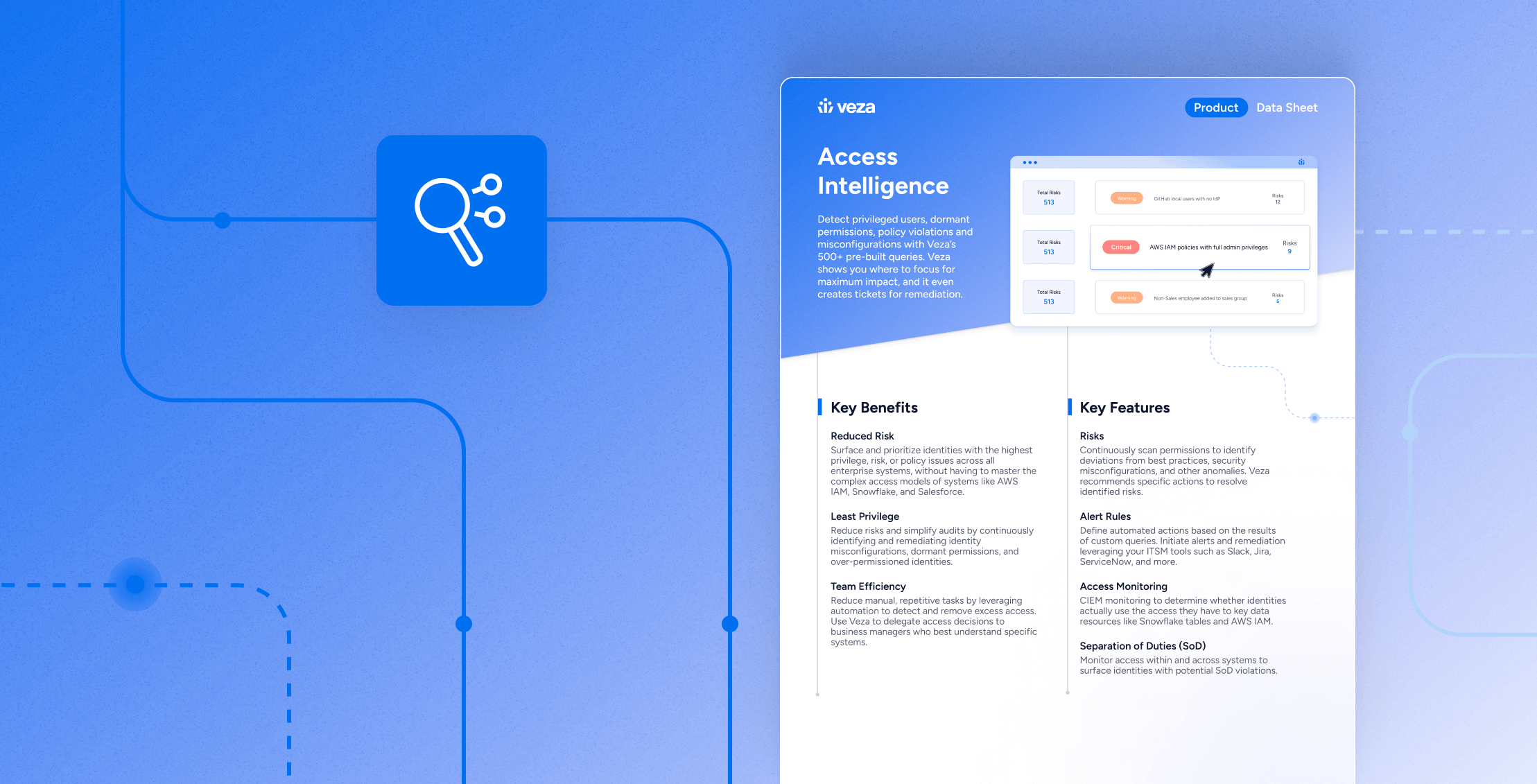
ReportNew Gartner Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation
Learn more -
 Guide
GuideVeza NHI Security: Protect Service Accounts, Tokens, and Workload Identities
Learn more
-
 Solution Brief
Solution BriefVeza + ServiceNow
Learn more -
 Solution Brief
Solution BriefOpenAI Identity Governance | Veza for OpenAI Solution Brief
Learn more -
 Solution Brief
Solution BriefVeza + Salesforce: Simplifying Access Control & Protecting Sensitive Data
Learn more -
 Solution Brief
Solution BriefVeza for Databricks | Access Governance for Unity Catalog & Workspaces
Learn more -
 Solution Brief
Solution BriefNon-Human Identity Management (NHI) | Veza
Learn more -
 Solution Brief
Solution BriefVeza for Oracle
Learn more
-
 Case Study
Case StudyStreamlined compliance and least privilege at Sallie Mae
Learn more -
 Case Study
Case StudyVeza for Identity Security at Snowflake
Learn more -
 Case Study
Case StudyUnlocking Automation & Compliance: CopperPoint’s Journey with Veza
Learn more -
 Case Study
Case StudyHow the City of Las Vegas safeguards the data of 42 million visitors a year with Veza
Learn more -
 Case Study
Case StudyHow Genesys runs access reviews 3x faster with Veza
Learn more -
 Case Study
Case StudyCybersecurity leader transforms access reviews with Veza, making an unmanageable process manageable
Learn more
-
 Case Study
Case StudyHow the City of Las Vegas safeguards the data of 42 million visitors a year with Veza
Learn more -
 Case Study
Case StudyBlackstone Case Study
Learn more -
 Video
VideoGoogle Ventures | Veza – why authorization matters, why now
Learn more -
 Video
VideoHow Veza Enables Identity Security (Explained in 7 Minutes)
Learn more -
 Video
VideoChoice Hotels’ identity-first approach to secure enterprise data
Learn more -
 Video
VideoSecuring access to data in SaaS apps
Learn more
-
 Whitepaper
WhitepaperVeza for PAM
Learn more -
 Whitepaper
WhitepaperReport: Trends for Securing Enterprise Data
Learn more -
 Whitepaper
WhitepaperManage and control privilege drift on AWS services with Veza
Learn more -
 Whitepaper
WhitepaperVeza provides comprehensive & actionable intelligence into data access trends on AWS
Learn more -
 Whitepaper
WhitepaperVeza Security Technical Whitepaper
Learn more
-
 EBook
EBookRedefining Cybersecurity for the Agentic Era: Introducing AISPM
Learn more -
 EBook
EBookISPM Buyer’s Guide | Identity Security & Zero Trust
Learn more -
 EBook
EBookIntelligent Access: Modernizing Identity with Just in Time Access
Learn more -
 EBook
EBookIntelligent Access: Strategies for Achieving Least Privilege in the Modern Enterprise
Learn more -
 EBook
EBookA Practitioner’s Guide to Intelligent Access
Learn more
-
 Report
ReportNew Gartner Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation
Learn more -
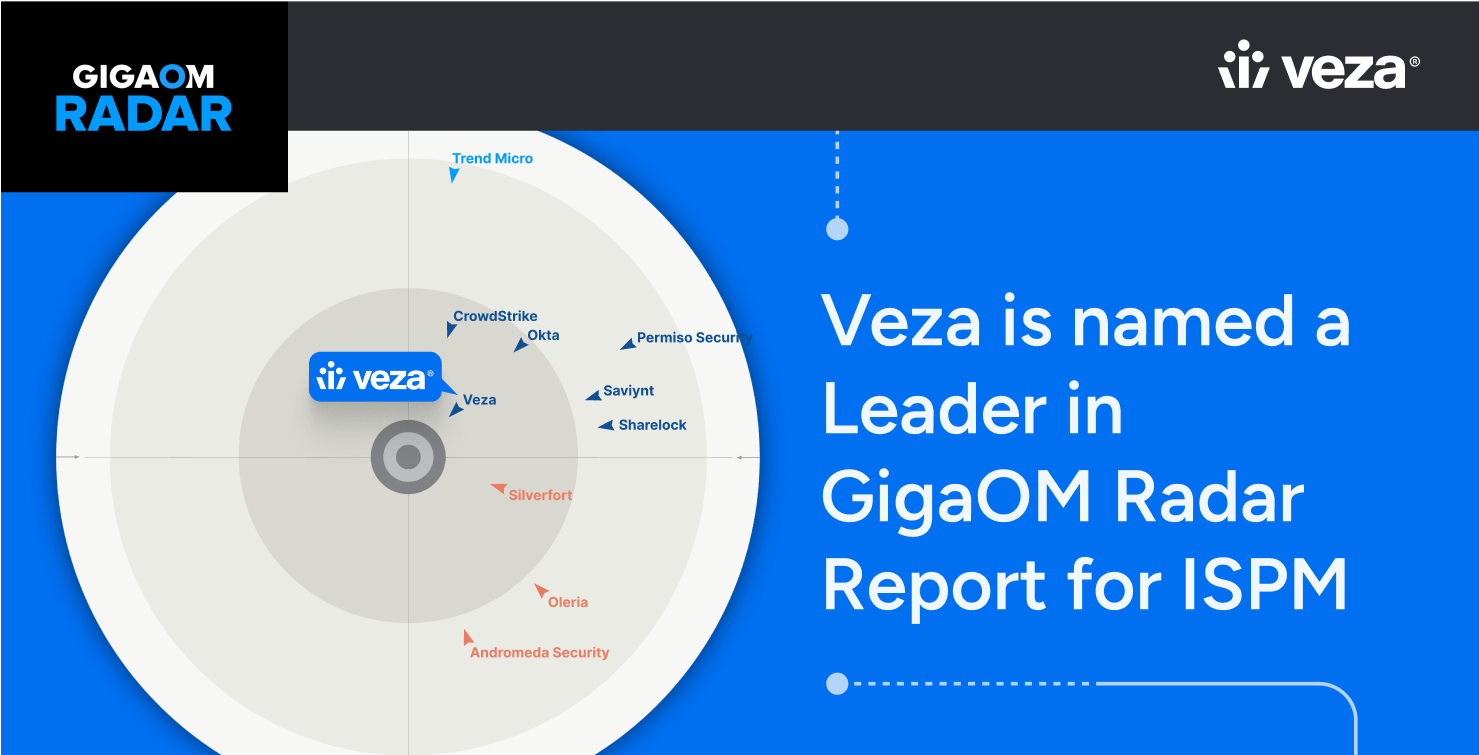 Report
ReportGigaOm Radar for ISPM
Learn more -
 Report
ReportPlanning the Migration of Enterprise Identity Governance to the Veza Platform
Learn more -
 Report
ReportThe State of Identity & Access
Learn more
-
 Guide
GuideVeza NHI Security: Protect Service Accounts, Tokens, and Workload Identities
Learn more -
 Guide
GuideGuide – The Veza Advantage
Learn more -
 Guide
GuideVeza for Insider Threat
Learn more -
 Guide
GuideIntelligent Access Guide for Microsoft Azure: Security, Access Control, Compliance, & Roles
Learn more -
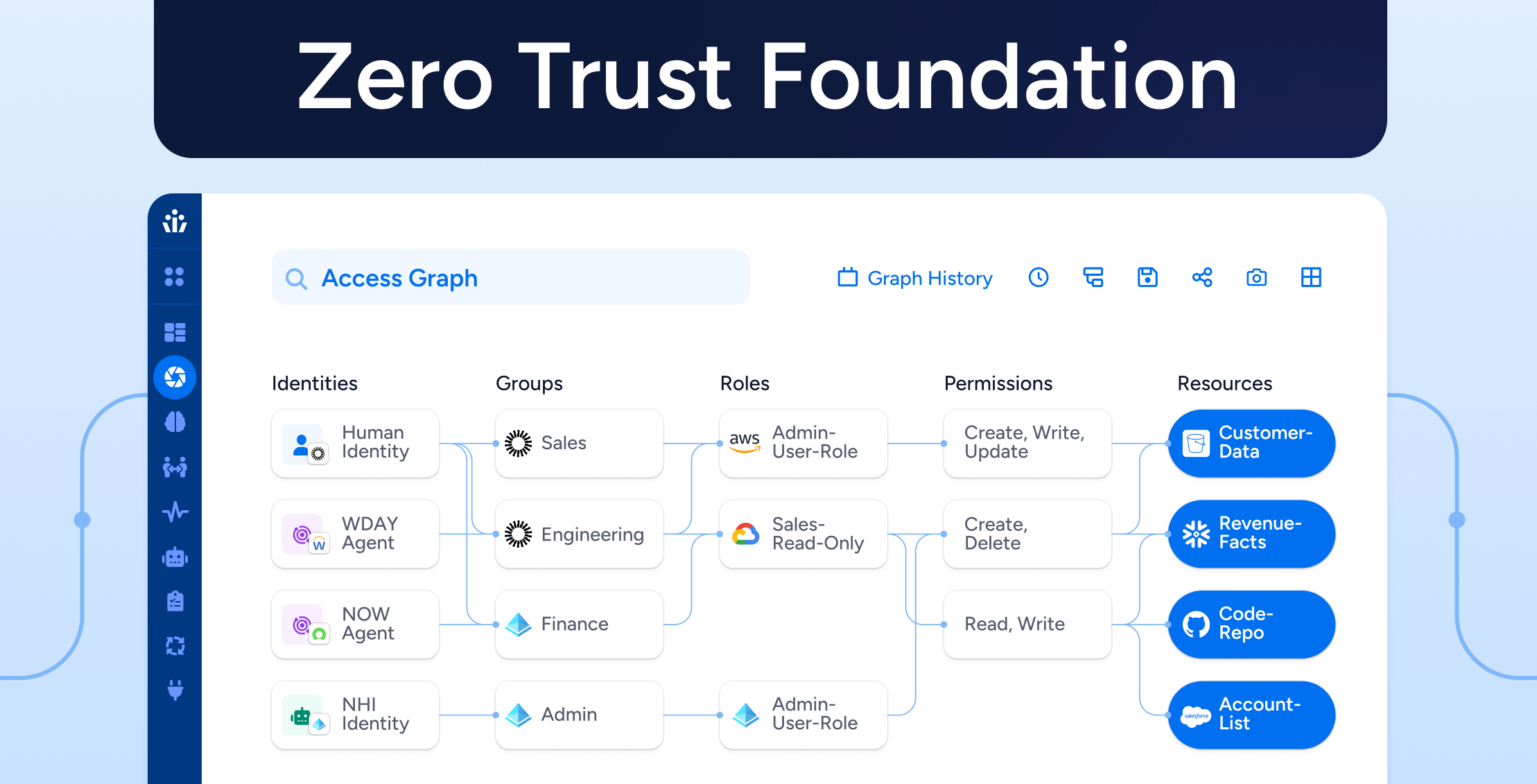 Guide
GuideIdentity Security IS the Foundation for Zero Trust
Learn more
-
 Case Study
Case StudyCybersecurity leader transforms access reviews with Veza, making an unmanageable process manageable
Learn more -
 Case Study
Case StudyDelivering data-driven guest experiences backed by strong corporate security practices
Learn more -
 Case Study
Case StudySecuring access to 14 hotel brands’ data in a multi-cloud environment
Learn more -
 Case Study
Case StudySafeguarding 100 years of entertainment content with Veza
Learn more -
 Case Study
Case StudyBlackstone Case Study
Learn more -
 Video
VideoGoogle Ventures | Veza – why authorization matters, why now
Learn more