Introduction
Today, 64% of organizations manage at least one petabyte of data – roughly 500 billion pages of printed text – and 41% manage at least 500 petabytes.
With so much information, choosing the right data governance tools in 2025 has become a critical business challenge. Governance is no longer just about storage. It is about setting policies, maintaining accuracy, monitoring usage, and enforcing access in ways that protect sensitive data and create value. Without it, organizations face inefficiency, compliance gaps, and security risks.
To address these challenges, enterprises are adopting data governance tools and identity security solutions to classify, monitor, and protect data throughout its lifecycle. This article explains how to choose the right data governance tools: the features to prioritize, the challenges to anticipate, and how governance tools support compliance across North America and the EU, including GDPR, NIS2, DORA, CCPA, and SOX.
Looking ahead, data governance is increasingly linked to access governance and Gartner’s emerging Identity Visibility and Intelligence Platform (IVIP) model. Together, these approaches bridge the gap between policies and real-world entitlements, ensuring governance programs remain sustainable in 2025 and beyond.
What is Data Governance?
Data governance is the discipline of managing information throughout its lifecycle – from creation to retirement – to keep it secure, accurate, and accessible. It requires clear internal policies for collecting, storing, classifying, using, and disposing of data while demonstrating compliance with regulations. Effective governance creates consistency, strengthens trust in data, and reduces the cost of audits.
Governance is now inseparable from access. Programs that focus only on quality or classification miss the core risk: who has access to sensitive data, and why. This is why governance increasingly overlaps with Identity Security Posture Management (ISPM) and Gartner’s emerging Identity Visibility and Intelligence Platform (IVIP) framework. Both emphasize monitoring and controlling entitlements across human and non-human identities to ensure permissions match business policy.
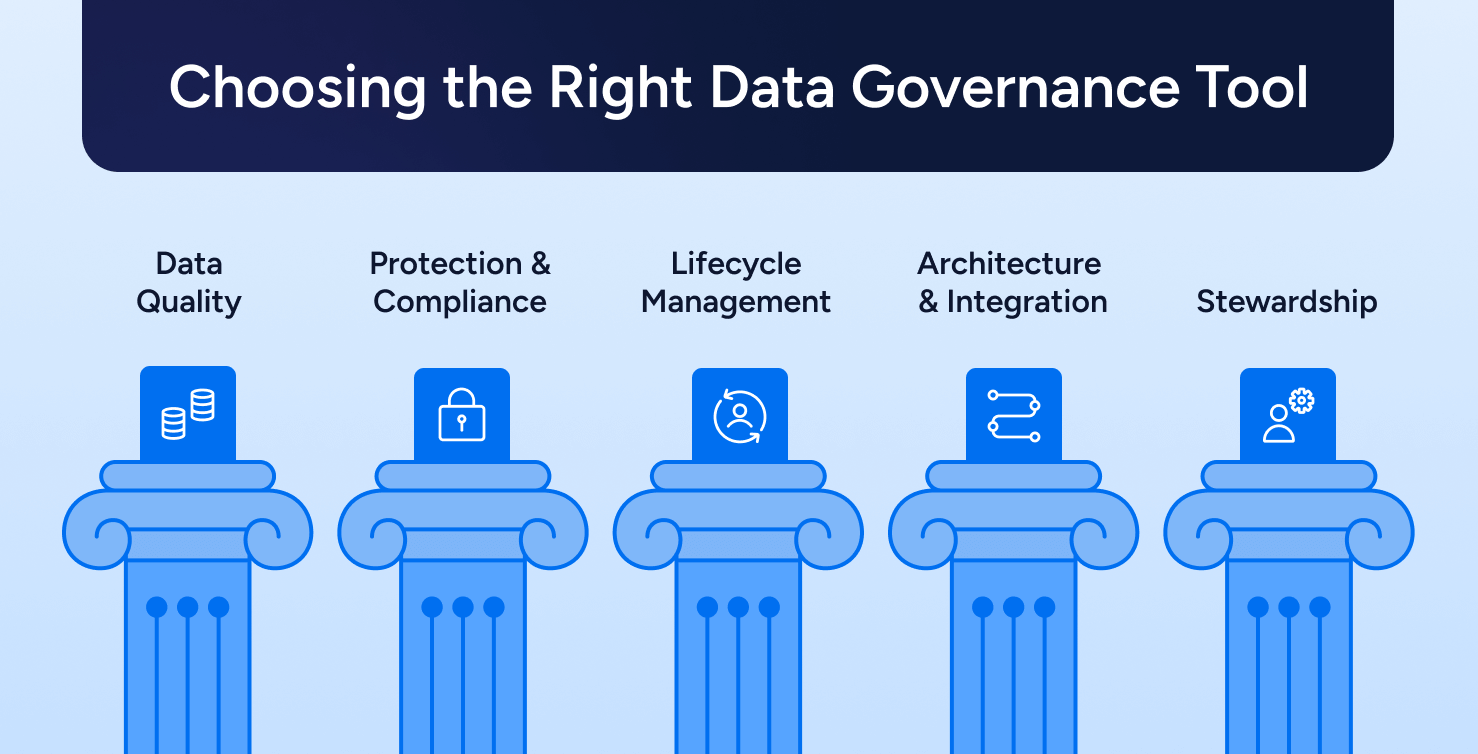
What Are The Pillars Of Data Governance?
Data quality
Quality data must be accurate, complete, and consistent to be trusted for decision-making. Define measurable standards for each domain and validate against them continuously. Modern platforms increasingly use Artificial Intelligence (AI) driven monitoring to detect anomalies, duplicates, or stale records in near real time.
Data stewardship
Strong stewardship means assigning data owners and stewards with clear accountability. They enforce policies, resolve issues, and align stakeholders across business and IT. In 2025, stewardship is also key to managing SaaS sprawl by centralizing oversight to reduce redundant applications and prevent new silos.
Data protection and compliance
Protecting sensitive data requires aligning governance with compliance mandates. Regulations such as GDPR and DORA in the EU, alongside HIPAA, SOX, and CCPA in North America, set the bar. Effective Data protection requires encryption, applying the principle of least privilege, monitoring access, and preserving audit evidence.
Data architecture and integration
Sound Data architecture provides scalable integration between warehouses, SaaS, and cloud systems. It ensures that data is consistent across platforms and avoids duplication of identity or entitlement information. Integration with identity providers is increasingly critical for aligning governance policies.
Data management
Data management spans the entire lifecycle, from capture and classification to retention, archival, and secure disposal. Automation through catalogs and workflow engines improves consistency, reduces manual effort, and ensures that governance policies are actually enforced.
What Is a Data Governance Tool?
Modern data governance tools in 2025 not only handle policy and metadata, but also help organizations define and enforce how data is managed, from creation through retirement. These platforms centralize policy, metadata, classification, lineage, and quality rules. They also support access governance and security by monitoring permissions for both human and non-human identities. By tracking who has access to what and monitoring changes, governance tools help prevent unauthorized access and detect potential risks.
They also automate essential tasks such as user access reviews, monitoring data usage, and generating compliance reports.
For smaller teams, free tools provide basic capabilities like classification and compliance reporting. But as organizations scale, they often require more advanced features such as non-human identity management, granular access visibility, and audit-grade reporting.
Benefits of Using Data Governance Tools
Support regulatory compliance
One of the biggest reasons organizations adopt data governance tools in 2025 is to help enforce data protection laws such as GDPR and CCPA. They simplify policy enforcement, cataloging, and reporting, making compliance more manageable.
Improve operational efficiency
Accurate and well-organized data improves collaboration, reduces redundancy, and saves time by automating routine tasks. Cataloging and user access reviews are common early benefits.
Mitigate risk
Governance tools reduce the risk of misuse or unauthorized access by monitoring permissions and usage. Visibility makes it easier to spot issues early.
Improve decision-making
Consistent, reliable data leads to better insights and reduces the risk of conflicting metrics across business units.
How to Compare the Best Data Governance Tools
When evaluating data governance tools in 2025, consider core capabilities, key features, usability, and pricing. Increasingly, buyers should also look for capabilities that go beyond cataloging and lineage. Support for non-human identity (NHI) management is critical as organizations rely more heavily on service accounts, tokens, and automation. For a deeper look at how leading vendors approach identity security – including NHI – see Veza’s 2025 overview of identity security software.
Core capabilities
Look for platforms that automatically handle metadata, enforce policy, classify sensitive data, and provide lineage. Prioritize tools with strong access governance and authentication support.
Key features
- Automated quality checks for accuracy, consistency, and completeness
- Dashboards for real-time insights
- Sensitive data classification for PII and financial records
- Role-based access control (RBAC)
- Automated alerts for policy violations
- Lineage tracking for transparency and compliance
- Audit trails to record changes and access events
- Access governance features to align permissions with policy
Usability features
Choose tools with intuitive dashboards, clear relationship visualizations, and collaboration features for stewards and security teams.
Features like intuitive dashboards, clear visual displays of data relationships, and easy navigation help users quickly find the information they need. Ideally, the tool should also allow you to track workflows, manage tasks, and collaborate across teams within the platform for smoother communication and more efficient data management processes.
Pricing models
Vendors may charge by users, features, or data volume. Model total cost, including connectors, lineage compute, and review frequency.
Challenges When Comparing Data Governance Tools
Common challenges include:
- Scalability: Some tools struggle at enterprise scale. Test with production-size datasets.
- Integration: Gaps in native connectors lead to silos and extra manual work.
- Customization: Unique workflows often require policy-as-code or API support.
- Balancing control and access: Overly strict access slows business. Weak access creates risk. Pilot reviews and looks for plain-language explanations of why access exists. See industry challenges for additional context.
Choose the Right Data Governance Tool For Your Organization
Managing governance requires more than policies. It requires control over who can access data across SaaS, cloud, and on-prem environments.
Veza provides the access governance layer that makes data governance actionable. With the Access Graph, organizations gain visibility into permissions for both human and non-human identities. Security and data teams can review access by data domain, enforce least privilege, and produce audit-ready evidence to meet EU and North American compliance frameworks.
Veza also simplifies complex permissions into plain language, integrates with existing governance stacks, and reduces the manual work required to align policy with real-world access.
- Learn: Why traditional governance approaches are no longer enough in Is Your IGA Solution Stuck in the Past?.
- Explore: Join our executive-level webinar Identity Is the New Battleground: How to Forge a Path to Identity Security to learn how leaders are redefining identity security – from visibility to value – within changing hybrid environments.
- Engage: See how Veza’s Access Graph delivers entitlement visibility, least-privilege enforcement, and audit-ready reporting. Request a demo today.
By connecting governance to access, Veza helps enterprises meet global regulations like GDPR, NIS2, DORA, SOX, and CCPA while strengthening security posture and improving operational efficiency.
About the Authors
Matthew Romero – Technical Product Marketing Manager at Veza
Matthew connects identity security depth with clear, practitioner-ready guidance. His 25+ years across infrastructure and cybersecurity shaped this article’s 2025 relevance-grounding the recommendations in real-world access risks, non-human identities, and compliance outcomes.
Mariah Brooks – Editorial Lead & Cybersecurity Writer
Mariah brought the research backbone and narrative clarity, translating complex governance and access concepts into approachable, accurate explanations that work for both technical and business readers.
Madeline Hogan – SEO & Editorial Strategy
Madeline tuned structure, headings, and phrasing to improve scanability and search performance. Her edits tightened definitions, clarified feature lists, and aligned the flow with how buyers actually compare governance tools – so the content ranks, gets read, and drives action.





