In 2025, the identity security conversation wasn’t just about adopting artificial intelligence (AI); it was about operationalizing it fast enough to stay secure in a landscape of evolving risk.
Identity-based attacks are now the leading cause of enterprise breaches, and AI is both a disruptor and a defense. Whether you’re dealing with insider threats, agentic AI misuse, or unmanaged machine identities, organizations need intelligent, real-time visibility into who (or what) can access sensitive data, and how that access is used
By combining machine learning with behavioral analytics and context-aware automation, AI-powered identity platforms are helping security teams strengthen their identity security posture, proactively reducing risk, enforcing least privilege, and streamlining compliance across complex multi-cloud and hybrid environments.
But AI adoption isn’t without challenges. From data dependency to explainability and regional regulatory requirements, effective implementation requires clarity, oversight, and adaptability.
In this post, we’ll explore how AI is transforming identity and privileged access management (PAM) in 2025. You’ll learn how security-forward organizations across North America, EMEA, APAC, and the Middle East are leveraging AI to harden defenses, govern non-human identities, and maintain a resilient identity security posture in an increasingly volatile threat landscape.
Importance of AI in identity security and privileged access management
Identity-based attacks are some of the most dangerous and costly challenges organizations face today. According to the Identity Defined Security Alliance (IDSA), 90% of organizations have experienced an identity-related incident in the past year, and 84% reported direct business impact. These attacks often leverage valid credentials—whether from human users or AI agents—and bypass traditional controls by appearing legitimate.
The rise of AI agents and non-human identities has added complexity. CyberArk’s 2025 Identity Security Threat Landscape notes that while 96% of enterprises recognize AI agents as a risk, fewer than half have appropriate governance controls in place.
Compared to other types of threats, identity-based attacks are especially problematic. Once attackers gain access to valid credentials, they can operate undetected, mimicking legitimate users and causing damage before anyone notices.
Integrating AI into identity security and privileged access management is key to stopping these attacks before they escalate. AI-driven tools can quickly spot suspicious activity–whether it’s an unusual login attempt or strange usage patterns–by constantly monitoring user behavior and processing large amounts of data.
How AI Enhances Identity and PAM Operations
Managing identities and privileged access is much more complex once organizations move to digital and cloud-based systems. Manual oversight simply can’t keep pace with the growing number of users, non-human identities, and diverse platforms most businesses need to operate.
Instead, AI automates security tasks and helps teams get the real-time visibility needed to respond immediately to threats.
Threat detection
Implementing AI in threat detection means using automated tools to continuously monitor user behavior and spot unusual activities, like unauthorized login attempts or unexpected access to sensitive data. AI learns what’s normal by analyzing everyday user actions and immediately flagging any deviations that could signal potential threats. By catching these issues earlier, AI helps organizations respond before a small problem turns into a major breach.
Veza, the identity security company, helps you reveal, visualize, and secure your identity entitlements everywhere. The platform helps organizations put AI-driven threat detection into practice. Its platform automatically analyzes permissions and activities across all enterprise systems, pinpointing risky access or unusual behaviors in real-time.
With clear dashboards and automated alerts, security teams can easily see and act on threats without sifting through mountains of data.
Attack correlation and prediction
Attack correlation and prediction is a core use case for AI in modern identity security. AI models trained on identity activity, system logs, and access relationships can detect patterns that suggest policy drift, privilege escalation, or lateral movement—often before any damage is done. By establishing behavioral baselines and continuously analyzing access events across cloud, on-prem, and SaaS environments, AI helps security teams spot vulnerabilities that might otherwise go unnoticed.
Platforms aligned with the emerging Identity Visibility and Intelligence Platform (IVIP) framework bring this to life by contextualizing who has access, what they’re doing with it, and where overprovisioning could introduce risk. Tools like Veza correlate identity signals across disparate systems, surfacing hidden toxic combinations, access anomalies, and early signs of insider or automated threats.
This proactive, real-time visibility empowers teams to prioritize remediation, reduce alert fatigue, and strengthen overall identity security posture.
Automatic remediation
AI helps organizations respond to threats immediately by revoking access or triggering extra verification steps as soon as it detects suspicious activity. Instead of waiting for human intervention, AI handles some threats instantly to minimize the potential harm.
Veza speeds up remediation by automatically pinpointing risky permissions and swiftly kicking off actions like revoking access or generating security tickets in tools like Jira, ServiceNow, or Slack, streamlining modern access governance.
With Veza, security teams get clear visibility and can act decisively to limit attacker access before damage occurs.
Continuous monitoring
AI monitors user activities 24/7, identifying unusual behavior the moment it occurs. Unlike human teams that need rest, AI tools continuously analyze events to detect potential insider threats or unauthorized access attempts in real time.
Veza collects and analyzes access data from all connected systems, clearly showing security teams exactly who accessed what resources and when. By highlighting dormant accounts and unnecessary privileges, Veza helps organizations eliminate risky access with real-time insights that keep systems secure day and night.
Access reporting
AI automates access reporting by analyzing user activities against established security rules. Instead of manually auditing permissions, which can be slow and error-prone, AI instantly flags any access that deviates from policy. Security teams can spot risks early to keep systems safe and aligned with compliance standards.
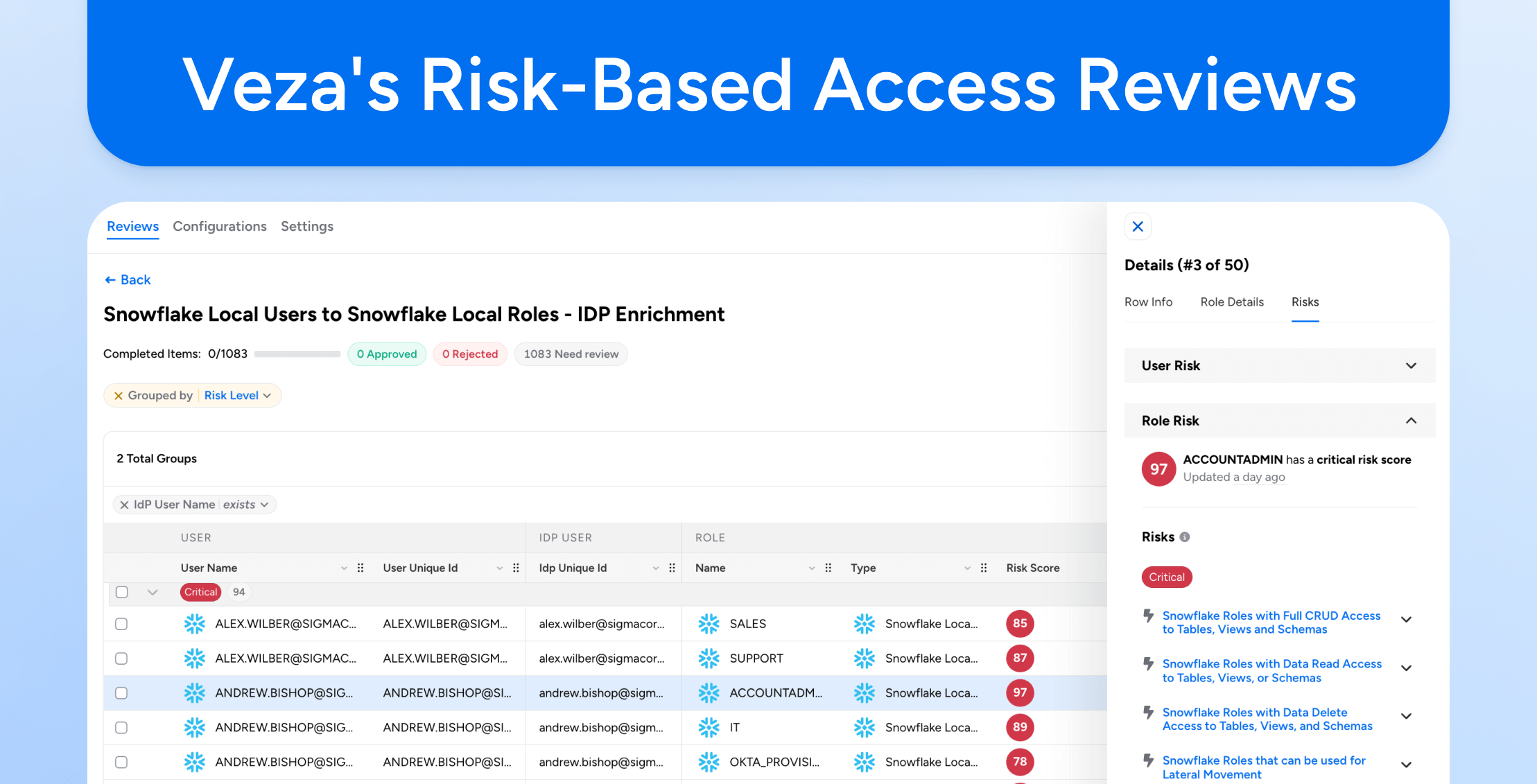
Veza simplifies access reporting even further. It scans permissions across all applications, cloud services, and data systems to quickly identify risks like excessive permissions or policy violations. With Veza’s easy-to-use reports and dashboards, security teams get clear, actionable insights into who has access to sensitive resources, audits are more straightforward, and user access reviews are easier to maintain.
Automating least privilege role enforcement
Implementing AI for least privilege role enforcement involves analyzing user activity to identify which permissions employees actually use. Rather than relying on manual audits, AI continuously evaluates access patterns and highlights permissions that are unnecessary or rarely used. Then, it automatically removes or adjusts these permissions to reduce the risk of unauthorized access and simplify compliance.
Veza automates this process with real-time visibility into who has permission to access sensitive data and why. It monitors usage across all enterprise systems and proactively recommends adjustments to user permissions. With Veza’s automatic role recommendations, security teams can easily enforce least privilege without slowing teams down.
Challenges to manage when using AI in identity security and IAM
Ultimately, AI’s effectiveness depends on the quality of data it uses, how transparent its decisions are, and how well it adapts to changing cybersecurity threats.
Dependency on data
AI systems need large amounts of high-quality training data to work properly. If the data is incomplete or flawed, AI might make mistakes, which can lead to false alerts or missed threats.
This can be especially challenging for smaller organizations that don’t have access to vast data sources. Without reliable data, AI can’t provide the protection organizations expect, leaving gaps in access management and security. But with accurate, diverse data, AI can help continuously monitor and update access controls in real time.
Potential for bias
AI can also be affected by bias. If trained on biased or incomplete data, it can make unfair or inaccurate decisions, especially in areas like identity verification and authentication. This can raise legal and ethical concerns and undermine trust in AI systems. Ensuring that AI is trained on unbiased, representative data is key to making sure it works fairly and effectively.
Complexity
AI systems can sometimes act like “black boxes,” where it’s hard to see how decisions are being made. This lack of transparency can make it difficult for organizations to fully understand or trust AI’s decision-making processes, especially in identity security settings. The complexity of these technologies also makes it harder to audit and ensure compliance with regulations. To maximize the capabilities of AI, organizations must balance its cutting-edge functionality with clear oversight.
Benefits of using AI in IAM
Integrating AI into identity and access management (IAM) can introduce some major benefits and make it easier for organizations to protect their systems and data. That’s because artificial intelligence can automate complex tasks, improve visibility, and help ensure compliance—all while boosting overall efficiency.
Automated workflows
AI makes managing user identities simpler by automating tasks that once required manual effort, like assigning roles, granting permissions, and onboarding new employees. Instead of relying on IT teams to set permissions individually, AI systems automatically determine and provide the right level of access, reducing errors and freeing up staff to focus on more strategic security tasks.
Veza automates identity tasks from start to finish—adding new users, adjusting their access when roles change, and removing permissions when employees leave. By continuously updating permissions to match real-world needs, Veza cuts down on manual work and keeps organizations secure without slowing productivity for a modern approach to identity governance.
Better visibility
AI provides clear, real-time visibility into exactly who can access sensitive data across an organization. Instead of manually reviewing complex permission lists, AI-driven tools quickly analyze vast amounts of data to reveal who can do what within every system and application.
Veza provides a simple visual map of user permissions across the entire organization. Security teams can easily understand and track user access across cloud environments, data systems, and apps in real time. By clearly showing how permissions connect identities to data, Veza uses intelligent access to help organizations proactively manage risks and prevent breaches before they happen.
Improved compliance
AI helps organizations keep up with compliance regulations by automatically tracking who can access sensitive data and how they use that access. Instead of manually reviewing permissions, which takes time and can lead to mistakes, AI continuously checks that employees and apps only have the access they actually need.
Veza clearly maps out permissions across all systems, showing exactly who can create, view, edit, or delete sensitive data in easy-to-understand terms. It also provides automated, detailed audit trails that make it easier to meet standards like GDPR, HIPAA, and PCI DSS with less effort. With Veza, security teams can spot and correct compliance issues immediately, reducing the risk of regulatory violations or fines.
Implement AI into your identity security infrastructure
Adding AI to an identity security strategy comes with clear advantages. But making AI effective takes clear visibility into who has access to sensitive information and how they use that access. Traditional identity management tools often fall short, leaving gaps that attackers can exploit.
Instead, Veza shows organizations exactly who can do what with their data, across every system. Built around the Access Graph, Veza’s identity security platform is like a detailed map that shows all users and their permissions. Instead of guessing or relying on fragmented information, security teams can immediately see who can view, edit, or delete sensitive data in simple, clear terms.
Instead of complicated searches, teams can simply ask Veza questions in plain language, like “Who has access to this sensitive financial data?” Access AI instantly returns clear answers, making complex security tasks more straightforward. It continuously monitors user behavior, identifies unnecessary permissions, and automatically suggests role adjustments to enforce the principle of least privilege.
With automated access reviews and detailed reporting, security teams can quickly demonstrate compliance with regulations like GDPR, HIPAA, and PCI DSS. By simplifying these tasks, Veza can help your organization focus on securing data proactively, not managing paperwork.
Discover how Veza can help your organization unlock the power of AI to manage identity security and stay ahead of threats.
About the Authors
This article was developed in collaboration between Mariah Brooks, an independent consultant and researcher focused on identity security, and Matthew Romero, Technical Product Marketing Manager at Veza.
Mariah brings deep experience translating complex technical challenges into practical, real-world insight. With a background spanning identity governance, cyber risk, and responsible AI, she’s spent 5 years working alongside CISOs and security architects to unpack emerging issues like Non-Human Identities (NHI). Her clarity, context, and credibility make her a trusted voice for security leaders navigating high-stakes access decisions.
Matthew brings a strategic marketing lens grounded in the realities of modern enterprise security. At Veza, he helps define go-to-market positioning for identity-first security solutions, bridging the gap between technical innovation and customer relevance. His work focuses on connecting product capabilities to the risks and operational demands that security teams face every day.
Learn more about their work:
Mariah Brooks – LinkedIn
Matthew Romero – LinkedIn