Veza’s Access Graph
For the modern hybrid cloud enterprise, the scale of identity and access has moved beyond what can be accomplished with legacy tools built on old technology. Veza’s Access Graph was built to understand access permissions at scale and forms the foundation for Intelligent Access.
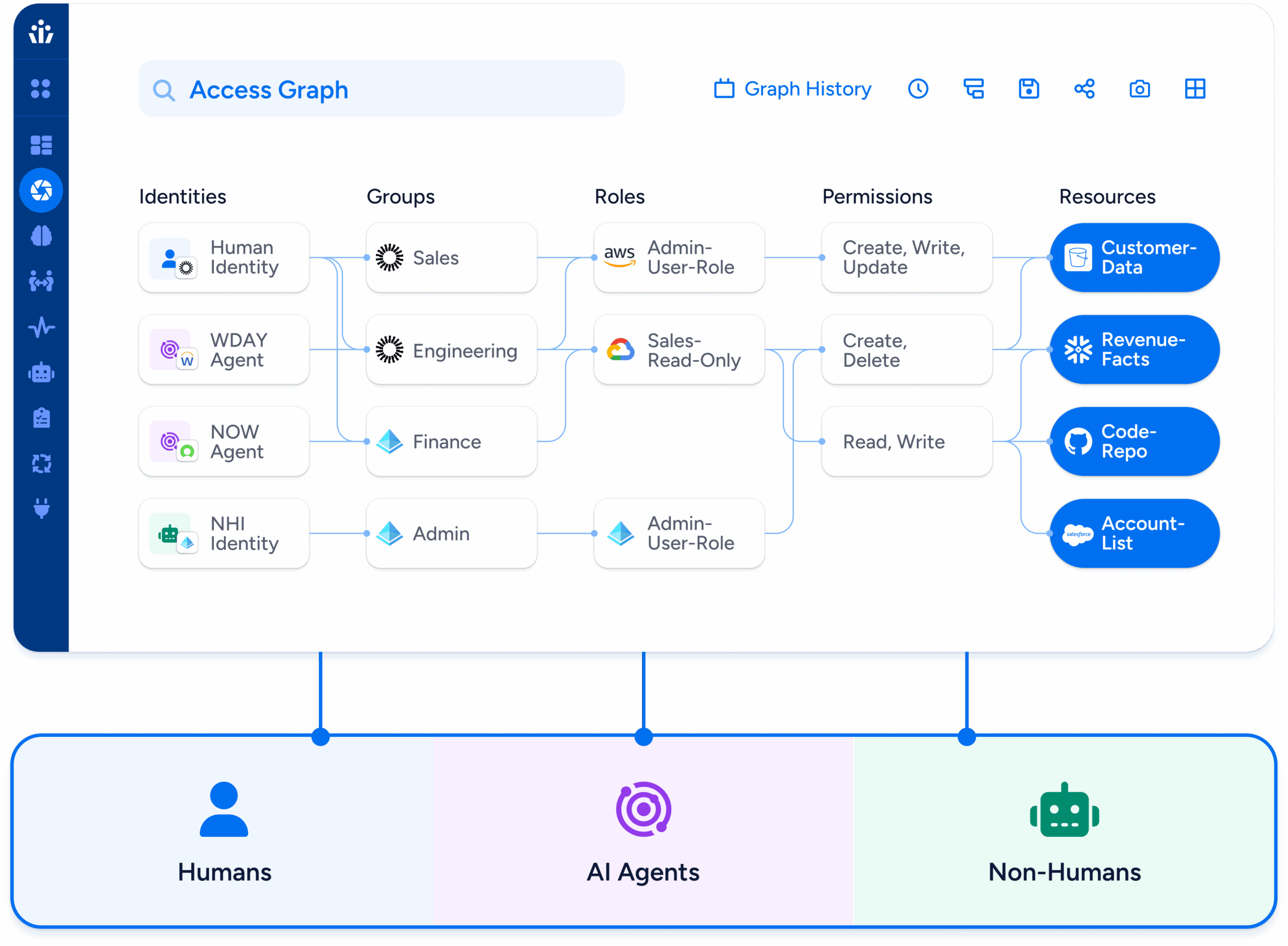
Access Graph Advantages
Best-in-class graph database
Legacy identity systems are built on relational databases. Okay to track a few group assignments per employee, but not for the complex web of identities, groups, roles, policies, and resources that make up your access fabric today.
Veza’s graph database is specifically engineered to store and query the relationships between billions of nodes, from identity—through groups, roles and policies—to specific permissions on individual resources. Veza can tell you not only what permissions an identity has but also how they got them, unravelling complicated access structures like nested roles that can obscure the reality of access.
Effective permissions
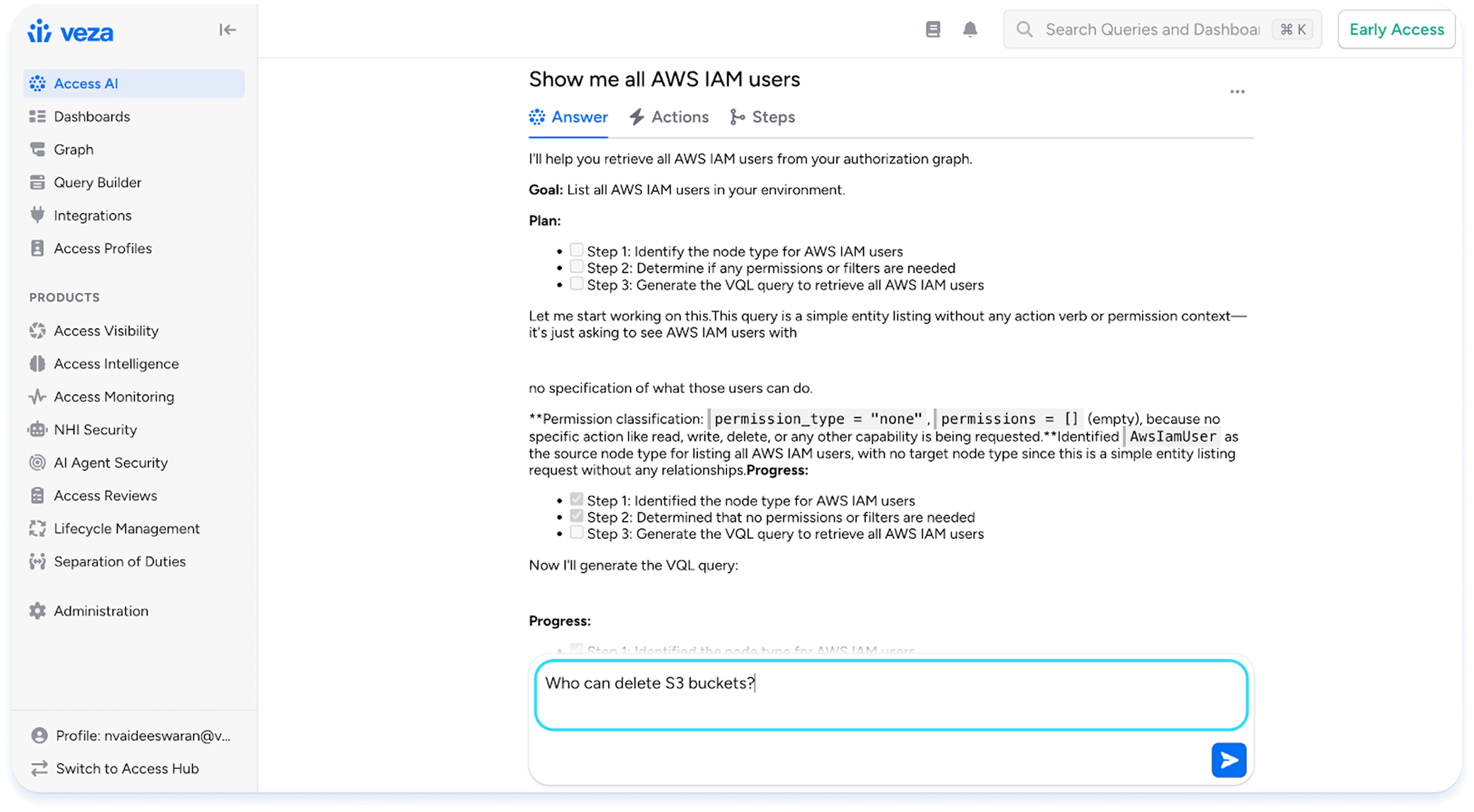
Permissions in the cloud are complex, and no single policy decides if an action is permitted. In fact, AWS uses a process of more than twelve discrete steps to decide if an identity is allowed to perform a particular action. Veza’s integrations with the major cloud providers resolve identity and object-based policies to give you accurate information about access outcomes.
In addition, the Access Graph gives decision-makers data on “effective permissions”, interpreting system-specific language—like the hundred different permissions possible for an AWS S3 bucket—into universal business language of “create”, “read”, “update”, and “delete”
300+ Integrations
To be able to effectively spot overprivileged identities you need to be able to see the full picture of their access, across all systems. Tools that just cover on-prem, or just SaaS, or just Cloud Infrastructure aren’t enough. Veza has more than 300 integrations to the top identity platforms, cloud data platforms, SaaS apps, cloud infrastructure, and on-prem enterprise apps.
For custom apps, there’s Veza’s Open Authorization API, a lightweight way to import access metadata from any system into Veza, with one simple JSON schema.
Full support for federated identities
Veza’s Access graph brings together metadata about federated identities, from your IdP, and metadata about roles and permissions, from your business systems. This means that Veza can tell you the true granular permissions of federated identities, which neither your IdP nor your business systems can tell you alone.


“Veza is looking forward for us. It allows us to understand who, what, where, when, and why. If you can do that, you have the ability to secure any environment. And when you’re talking about a global organization, that’s what you need.“
David Tyburski | VP of Information Security and CISO


“Having a world-class cybersecurity program that protects our brand, reputation, investors and intellectual property is of paramount importance to our firm, and we are continuing to incorporate innovative technology solutions. Our team is always looking for ways to develop a more comprehensive view of access across all of our applications and cloud infrastructure to allow us to modernize the firm’s access controls. We are excited to partner with Veza to help us accomplish this.”
Adam Fletcher | Chief Security Officer

“Using Veza, our security teams have gained valuable visibility across our systems – apps, infrastructure, and data, to better understand who can access what, helping drive stronger privileged access security practices.“
Jenner Holden | CISO, Axon


“Stitching together identities with data sources and showing the connections between them in a way that’s easy to consume — it’s a simple idea, but a complex problem to solve. Veza makes the process of understanding who has access to what really, really easy.“
Dave Farrow | VP, Information Security, Barracuda Networks