
With identity security growing increasingly complex, with the continuous rise in sophisticated identity-based cyber-attacks, expanding attack surfaces, and increased exposure to third-party vulnerabilities. As organizations grow and adopt new technologies, securing both human and non-human identities (NHIs) becomes critical.
Identity security software solutions can help organizations build a unified, scalable, and resilient defence that protects them from unauthorized access and bad actors.
In this comprehensive guide, we’ll review the top identity security software, showing their key features and benefits to help you select the best fit for your business.
What is identity security software?
Identity security is the combination of people, processes, and technologies that protect organizations’ data from unauthorized access or misuse via identities. It ensures only the right individuals can access the right resources at the right times.
Effective identity security software manages and automates identity security policy and permission management. These platforms help enforce the principle of least privilege: that identities should only be able to access the apps and data needed for their job.
Types of identity security software
The umbrella term “identity security” software includes solutions for managing authentication, access, governance, risk, and more. But these aren’t competing solutions; rather, they complement each other. For instance, a complete identity security stack can include a cloud SSO provider, Active Directory for on-prem/legacy, an IAM tool for your cloud provider, a governance platform, and then an identity threat detection and response (ITDR) tool for comprehensive protection.
Let’s get into more detail.
On-premises identity security software
Businesses can manage their identities effectively with on-prem identity security software. These systems allow organizations to manage user access and permissions within their local infrastructure. On-prem identity security software is usually custom-built to fit specific needs.
On-prem identity security software supports automated provisioning and de-provisioning, ensuring efficient user lifecycle management and compliance with security policies.
Cloud identity security solutions
Leveraging the cloud for identity security and management offers several benefits, such as scalability and simplified user provisioning. Cloud identity security solutions may offer SSO capabilities for streamlined access across multiple applications. They differ from other identity management tools due to their scalability, flexibility, and ability to integrate seamlessly with cloud-based services.
Identity Threat detection and response (ITDR)
ITDR software specializes in detecting and responding to identity-related threats like credential theft and unauthorized user access. It provides an integrated information technology (IT) and data risk detection solution and incorporates threat intelligence, endpoint security, and continuous monitoring.
ITDR software reduces identity-related security risks, ensuring that potential threats are identified and mitigated before they escalate into larger security incidents.
Key features of identity security software
Identity security software offers several features. Here are some of the key ones:
- Authorization and continuous auditing/monitoring: Automate access control authorization and ongoing audit with real-time alerts for suspicious activity monitoring.
- Authentication: This feature ensures only users with appropriate levels of authorization are authenticated to access sensitive systems and data.
- Access management: Trust and access should be earned, not assumed. Access management ensures users can only access resources necessary for their role by assigning specific permissions. It also includes access reviews and least privilege enforcement.
- Non-human identity management: Non-human identities make up approximately 90% of identities on a typical cloud platform. Identity security and management software have features for managing these identities through automated provisioning, monitoring, and lifecycle management.
- Identity governance: The identity governance feature enforces compliance with security policies, such as least privilege access and regulatory requirements.
- Risk monitoring and detection: Organizations are exposed to many identity-related risks, like credential theft, unauthorized access, and vulnerabilities arising from third-party integrations. The risk detection feature allows users to monitor, identify, and mitigate these threats.
- Identity lifecycle management: Identity management is a continuous process in every business. This means it’s not something you do when you hire a new employee; it’s an ongoing process of creating, adapting, and deleting digital identities based on changing circumstances. It involves provisioning new access for joiners, adjusting access for movers, and removing access for leavers.
Best identity security software
Rather than choosing a single solution, businesses typically use a combination of tools. For example, they may rely on cloud SSO for authentication, on-premises identity management for legacy systems, cloud IAM for cloud resources, governance platforms for compliance, and TDR solutions for threat monitoring. This multi-layered approach ensures robust identity security across all environments.
Veza

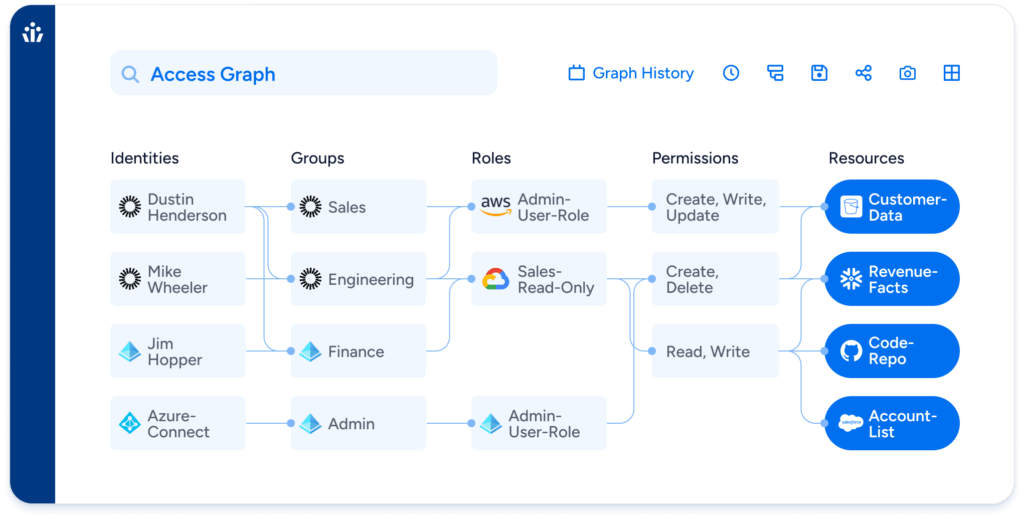
Veza is the identity security company helping organizations secure access across the enterprise, including cloud infrastructure, data systems, SaaS apps, and on-prem apps. Powered by the Access Graph, Veza’s platform delivers visibility and control of permissions so that organizations can finally achieve least privilege.
Veza’s AI-powered platform captures access metadata from all enterprise systems and visualizes the data using a unique, interactive graph that helps you answer the million-dollar question: Who can take what action on what data? For instance, users can ask, “Show users who disabled MFA,” and this information is immediately displayed.
Veza gives more visibility to access risks with its Access Intelligence feature, which discovers risky users, resources, and trends. The AI-powered risk intelligence dashboards provide real-time insights into potential security threats and help you understand effective permissions.
For non-human identities, Veza offers intelligent access at scale. It finds and fixes misconfigured cloud identities and roots out inactive, dormant, and over-permissioned accounts, including robotic process automation (RPA) identities and SaaS integrations.
Veza integrates with various platforms, like AWS, Google Cloud, Microsoft Azure, Okta, and other identity providers, allowing you to connect all your identities, including those on your cloud infrastructure, apps, and data systems.
Key features:
- Access Search: Build queries with Access Search with the option to filter and sort results and also visualize current permissions for all identities in all systems in near real-time with a simple natural language query.
- Access Intelligence: Visualize and manage access for all identities within your system. Access Intelligence also detects and corrects issues like excessive privileges, dormant permissions, over-permissioned identities, and policy misconfigurations.
- Activity Monitoring: Monitor access to data as well as who has accessed what data to enable right-sizing of permissions for both users and roles and clean up dormant entities and SaaS licenses to save cloud costs.
- Access Reviews: Review the permissions of both human and machine users and delegate reviews to user managers. Users can also automate access review suggestions based on past decisions.
- Lifecycle Management: Enhance access provisioning and de-provisioning with lifecycle management, Users can grant consistent birthright access for new employees, prevent privilege creep, and automate access removal when users leave a role or the organization.
- Privileged Access Monitoring: Find and fix privileged violations within your data systems, SaaS apps, and cloud services. With Veza’s privilege access monitoring feature, you can also discover local users and admin created outside of your identity systems and identify users who have not enrolled for MFA.
- Non-Human Identities Management: Identify and fix issues with your riskiest non-human identities like service accounts. Users can also find and fix misconfigured cloud identities and root out inactive, dormant, and over-permissioned non-human identities like service accounts, RPA identities, and SaaS integrations.
- Cloud Access Management: Simplify access management in cloud environments with Veza’s cloud access management feature. Veza shows you who accesses what across AWS, Google Cloud Platform (GCP), Microsoft Azure, and Oracle Cloud.
- Data System Access: Understand and control unstructured data stored outside of your SQL tables, such as data stored in data lakes, ML datasets, cloud storage, and even shared drives. Manage access to these data with Veza’s data system access feature.
- SaaS Access Security: Visualize and control data access across all systems, proactively mitigating risks for both human and machine identities.
- Next-gen IGA: Optimize your identity governance and administration with next-gen IGA. Accelerate access review processes and enforce least privilege and compliance through effective permission-based access reviews, identity hygiene, and advanced analytics (role/group analytics, user/group comparison).
Software type: Veza can replace your governance tool and brings visibility and access to all your other identity solutions
Veza’s Intelligent Access enables you to grant and revoke access permissions at the speed of business for all identities across all systems while enforcing security policies.
Ready to explore Veza? Schedule a demo
Okta

Okta Identity Governance is a workforce identity security software that includes lifecycle management, access requests, and access reviews.
Okta Lifecycle Management automates identity-related tasks, such as provisioning and de-provisioning of user accounts. It enables users to manage identities from various sources, like an existing Active Directory or a Human Resource Information System (HRIS). It also streamlines the process of assigning users to groups and granting permissions and access based on predefined user groups.
Key features:
- Single sign-on for access to multiple platforms
- Adaptive multi-factor authentication
- Identity governance for managing user identities ‘
- Privilege access for unified access to privileged resources
- Identity threat protection
Software type: Cloud identity and access management solution
Entra ID

Microsoft Entra ID (formerly Azure Active Directory) is a Microsoft product that focuses on identity security. It extends on-premises Active Directory environments into the cloud. Microsoft Entra ID has multi-factor authentication enabled, with options like phone calls, text messages, mobile app notifications, verification codes, or third-party OAuth tokens for authentication.
Entra ID also features a Resource Manager with a built-in Role-Based Access Control (RBAC) system to manage permissions and access securely.

Key features:
- Single sign-on and reverse proxy
- Multi-Factor Authentication
- Entra role-based access control (Entra RBAC)
- Security monitoring, alerts, and machine learning-based reports
- Consumer identity and access management
- Privileged identity management
Software type: Hybrid/On-Premises legacy solution
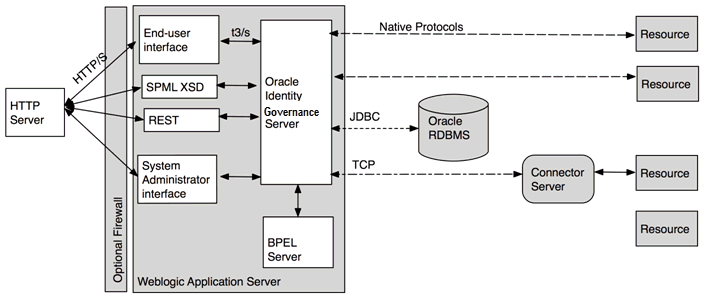
Oracle Identity Governance

Oracle Identity Governance is an identity security and management software that enables user lifecycle management across an organization’s service ecosystems and in both on-premises and cloud environments. It has self-service and customizable options to manage user provisioning and de-provisioning and features microservices to discover common access patterns.
Oracle Identity Governance also allows users to initiate application onboarding for access using REST APIs and other connectors.
Key Features
- User-friendly self-service connectivity for identities management across cloud and on-premises environments
- Role-based access provisioning for access request workflow planning and management
- Machine learning-based role management for role-based access control.
- Customizable certification for continuous compliance with regulations such as GDPR and SOX
- Open application model using Docker or Kubernetes for flexible deployment.
Software type: On-premises and cloud identity solution.
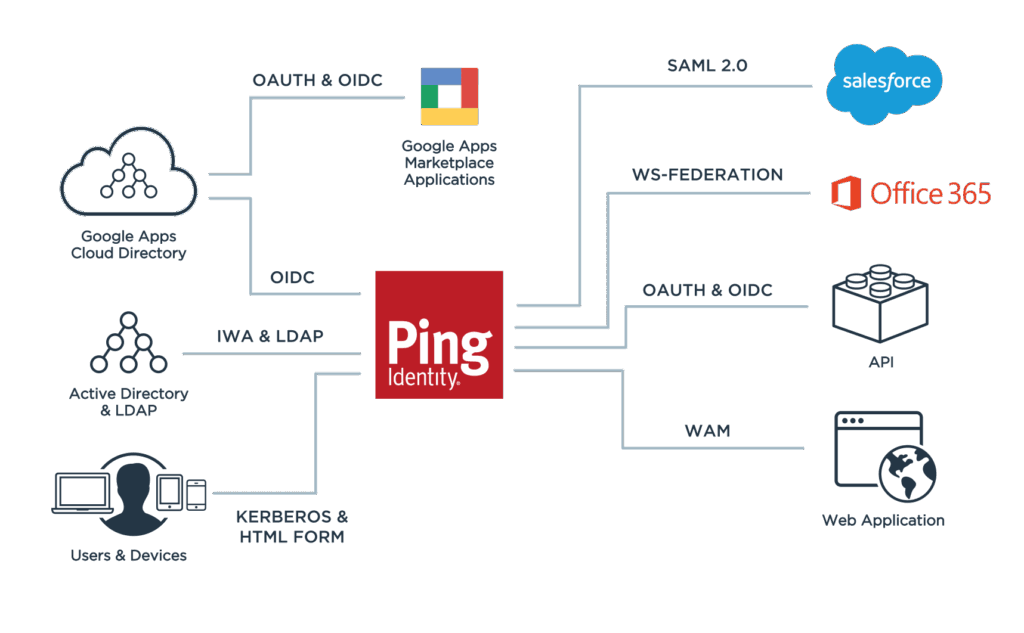
Ping Identity

Ping Identity is an identity access and management software with flow templates and drag-and-drop integrations for cross-application navigation. Ping Identity supports new user registration, onboarding, sign-in, profile management, and account recovery. It also has identity orchestration tools for automating identity workflows and threat protection capabilities for fraud prevention. Ping Identity also works as an identity directory solution to create unified user profiles. Ping Identity can be deployed as a multi-tenant SaaS, a dedicated tenant cloud service, or a cloud-ready platform for on-premises, hybrid, and fully cloud environments.
Key features:
- Lifecycle identity management
- Identity directory to create a single source of truth for identities
- Single sign-on (SSO) for users to access multiple applications
Software type: On-premises and cloud identity solution.
One Identity Manager

One Identity is an identity management software that offers solutions for identity governance and administration, access management, privileged access management, and Active Directory management. It also provides on-demand identity management products focused on user access governance, risk mitigation, and strengthening security compliance in a SaaS model. One Identity protects unstructured data and enables users to synchronize passwords across systems, networks, and servers through its One Identity Password Manager product.
Key features:
- Behavior-driven governance to enhance the principle of least privilege
- Privileged access governance to close the gap between privileged access and standard user identities
- Adaptive authentication for systems and application access control
- Log management for collecting, storing, and managing logs from systems across the enterprise
Software type: On-demand SaaS identity software
IBM Security Verify

IBM Security Verify, formerly IBM Cloud Identity), is a cloud-native, software as a service (SaaS) product that forms part of the IBM identity and access management product suite. It offers AI-powered context for workforce identity and access management and risk-based authentication. IBM Security Verify allows users to choose between having MFA as an additional security layer or going passwordless and it can either be deployed on-premises in a virtual or hardware appliance or even containerized with Docker. But Docker has some image limitations, which will require users to get more fine-tuned DevOps assistance.
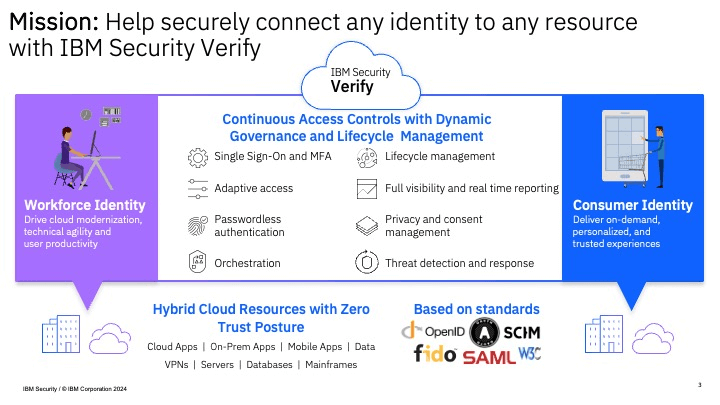
Key features:
- Orchestration for integration with other tools and software
- Single sign-on for centralized access control
- Adaptive access with machine learning
- Passwordless sign-in and multi-factor authentication
- Lifecycle management for user identities
- Identity analytics for scanning risks across users and other entitlements
Software type: Cloud identity and access management solution
Microsoft Active Directory

Microsoft Active Directory is an on-prem identity management product by Microsoft. It is designed to store information about objects on the network and make this information easy for administrators and users to access and manage. Active Directory plays a central role in managing domain-based networks and provides core functions such as authentication, authorization, and directory services.
AD is widely used to manage users, computers, groups, and policies within enterprise environments. It enables IT administrators to control access to resources, enforce security policies, and provide centralized user management.
Key features:
- Domain Services (AD DS)
- Group Policy configuration
- Kerberos-based authentication
- Integration with on-prem infrastructure and legacy apps
Software type: On-prem directory
Oasis
Oasis is an identity security platform built to manage and secure non-human identities. It works by creating an inventory of non-human identities within your environment and conducting a security posture assessment. It also offers out-of-the-box remediation plans for resolving issues with non-human identities, such as excessive permissions and credential vulnerabilities. Oasis also supports the orchestration of the lifecycle of non-human identities, managing NHI onboarding, continuous monitoring, and secure decommissioning.
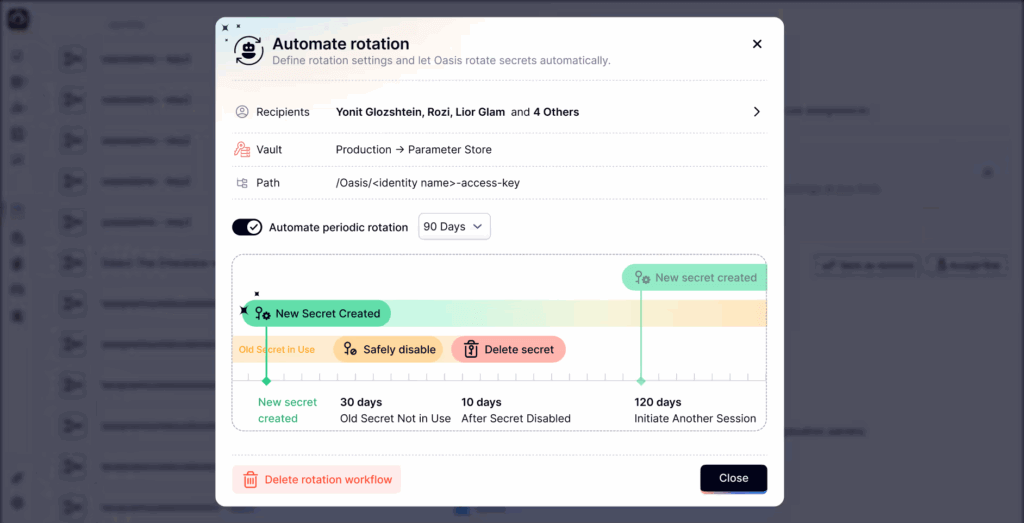
Key features:
- Auto-discovery of nonhuman identities
- Integrations with existing environment and workflows
- Non-human identities onboarding, monitoring, and decommissioning
- Out-the-box remediation plans for non-human identities
Software type: NHI management software
Astrix

Astrix focuses on non-human identities such as APIs and machine-to-machine credentials. Astrix supports non-human identity discovery both within your internal environment and from third-party integrations. It also has a feature for secret scanning of non-human identities. Additionally, Astrix includes a next-gen secret scanning tool for detecting exposed secrets across IaaS, SaaS, PaaS, and on-premises environments.
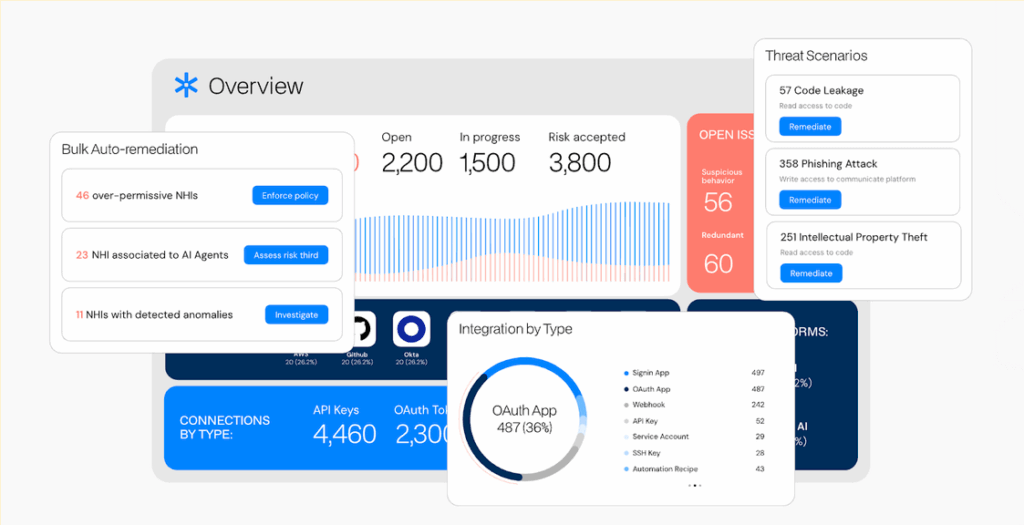
Key features:
- Non-human identities discovery
- Non-human identities posture management
- Non-human identity threat detection and response (ITDR)
- Non-human lifecycle management
- Auto remediation
- Secret scanning
Software type: NHI management software
SailPoint

SailPoint Security Cloud (ISC) is a microservices SaaS identity security platform for cloud enterprises. It offers solutions that automate user access discovery, management, and control. SailPoint Identity integrates with Microsoft Teams so users can request, approve, or deny access in the Microsoft Teams application. It also leverages AI and machine learning for identity security.
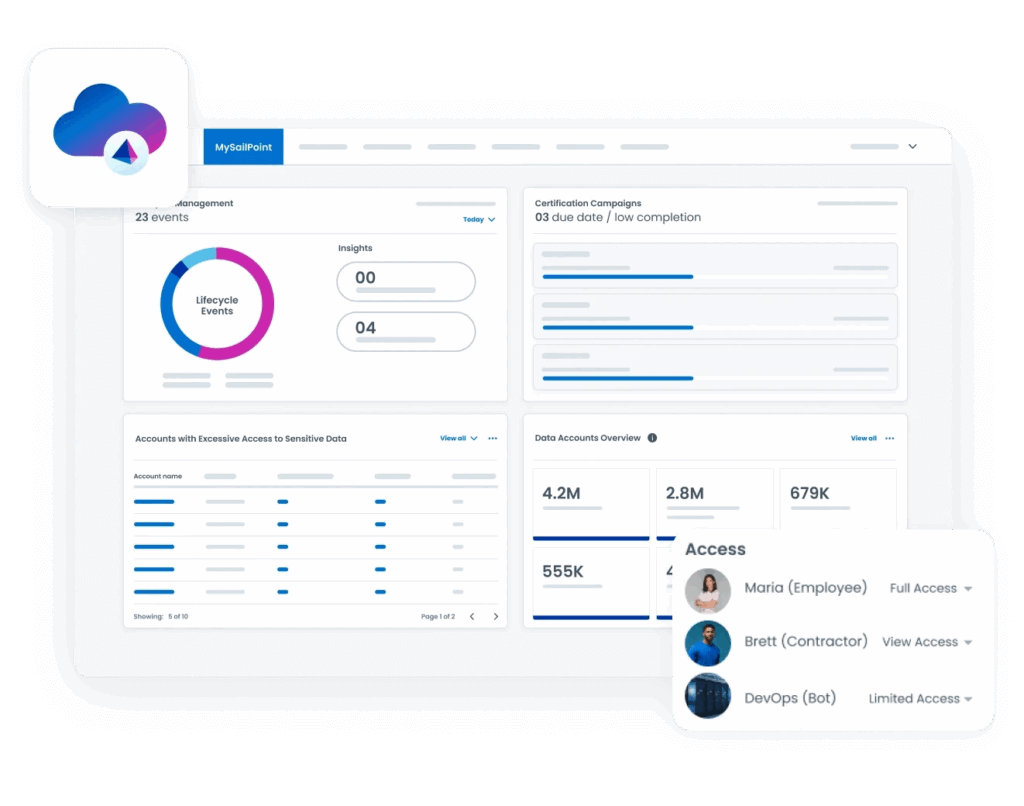
Key features:
- Generative AI descriptions for entitlements
- Role creation to build and maintain access roles in a least-privilege environment
- SailPoint identity security cloud for tailored configurations
- Lifecycle Manager for automating management and control of complex identity security challenges
Software type: Cloud-based identity software
CrowdStrike

CrowdStrike is a cloud-native cybersecurity platform that offers solutions for cloud security, identity protection, and Security Information and Event Management (SIEM). For identity protection, CrowdStrike provides insight into users’ active directory environment to identify stealthy administrators and gain visibility into malicious account activity.
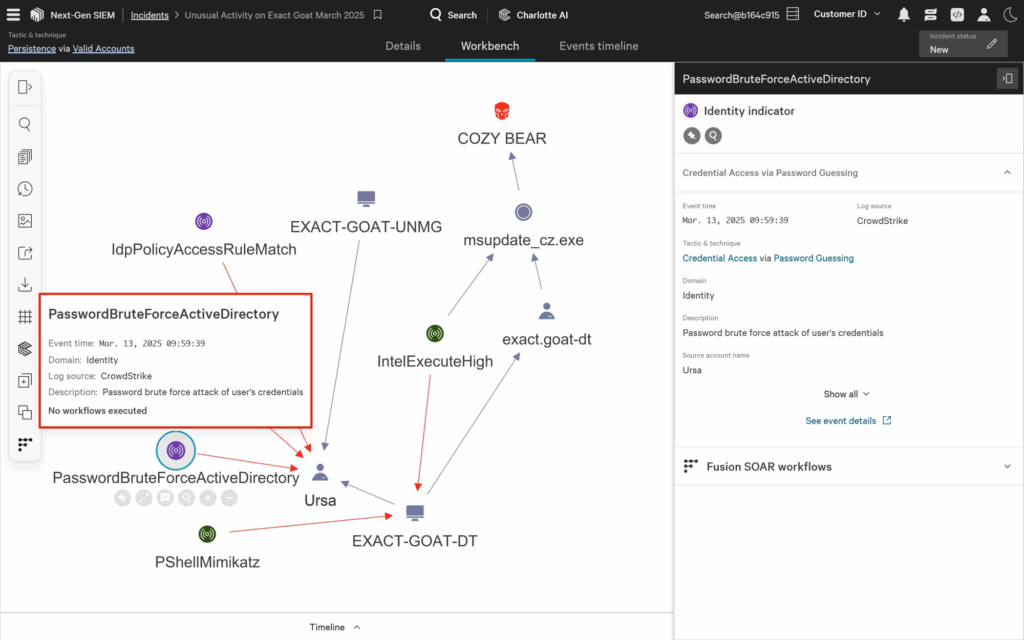
Key features:
- Frictionless multi-factor authentication into legacy apps
- Identity-based attack detection
- Risk-based conditional access
- Identity landscape visibility
- Customized access policies
Software type: TDR software
Benefits of using identity security tools
With the rate of identity and credential-related data breaches rising, implementing an identity security tool or software is no longer a question of convenience but a necessity. Here are some of the top benefits of using identity security tools:
Improved security posture
Proper identity security and management help maintain your organization’s identity security posture. Identity security tools help enforce security policies by automating and monitoring access control, managing and securing identities, controlling user permissions, and ensuring compliance.
The best identity security tools provide near real-time visibility of user provisioning and de-provisioning, allowing you to easily spot anomalies or gaps that could weaken your security posture.
Streamlined compliance
Maintaining compliance with regulatory standards like GDPR and SOX can be challenging if you’re manually managing user identities. Identity security tools can streamline compliance by automating user access reviews and management, enforcing access policies, and continuously monitoring identity-related activities.
Centralized access governance
Many identity security tools have directories that unify identity management, allowing users to have centralized access reviews and governance. Some identity security platforms even automate this process, so all you may have to do is review and approve access changes through automated workflows.
Enforced least privilege
The principle of least privilege states that users should only have the minimum levels of access necessary to perform their job functions. Identity security software helps enforce least privilege–without requiring IT teams to manually configure permissions.
Comprehensive identity management
Manual identity management typically only covers some human identities and, as such, leaves so much room for exposure. With identity security tools, you get comprehensive identity management for both human and non-human identities.
Choose the best identity security solution
While each identity security solution focuses on identity security and management, they often take distinct approaches. No matter your identity security tech stack, today’s complex threat landscape requires a next-gen IGA tool so you can see the reality of access.
Veza provides broader coverage than the average identity security software by functioning as an identity governance tool that manages both human and non-human identities, while also giving you enhanced visibility into your existing identity systems like Okta and Entra ID (formerly Azure AD)
With Veza, you don’t have to worry about replacing existing solutions; instead, you can enhance the functionality of your current infrastructure. Veza’s identity security platform:
- Offers a quick time to value with seamless integration into cloud architecture through a flexible deployment model and a modern developer experience
- Simplifies complex roles and permissions through natural language translation, making them easily understandable for business users
- Monitors all identities, including human and nonhuman identities, and even local accounts, to provide the most comprehensive view of permissions down to granular resources
- Dives deep into permission metadata and Access Control Lists (ACLs) to offer a detailed and accurate understanding of granular and local permissions, beyond just group or role names
- Connects with all systems, including cloud infrastructure platforms, structured and unstructured data systems, data lakes, SaaS apps, custom apps, and on-prem systems
Unlock the Future of Identity Security
Dive into our comprehensive whitepaper to understand how Veza’s platform addresses modern identity security challenges across hybrid, SaaS, and multi-cloud environments.
Download the Veza Security Technical Whitepaper
Explore Real-World Applications of Veza
Watch our on-demand webinar to see how organizations are leveraging Veza to enhance their identity security posture and streamline access governance.
Watch the Webinar: Identity is the New Battleground
Experience Veza in Action
Schedule a personalized demo to see how Veza can provide intelligent access control tailored to your organization’s needs.
About the Contributors
This article was led by Quoc Hoang, Principal Product Manager for Competitive Intelligence at Veza, who brings over a decade of experience in enterprise software, market research, and competitive analysis to his work in identity and access governance.
Samuel Sope supported content development, leveraging his expertise as a business analyst and technical writer to bring structure, clarity, and actionable insight to the piece. With a background in data visualization and process optimization, Samuel ensures complex ideas are communicated with precision and purpose.
Special thanks to Madeline Hogan for coordinating and delivering supporting content assets. Her tenacity and attention to detail ensured this piece met the bar for publication—no small feat given the last-minute demands and high standards thrown her way.




