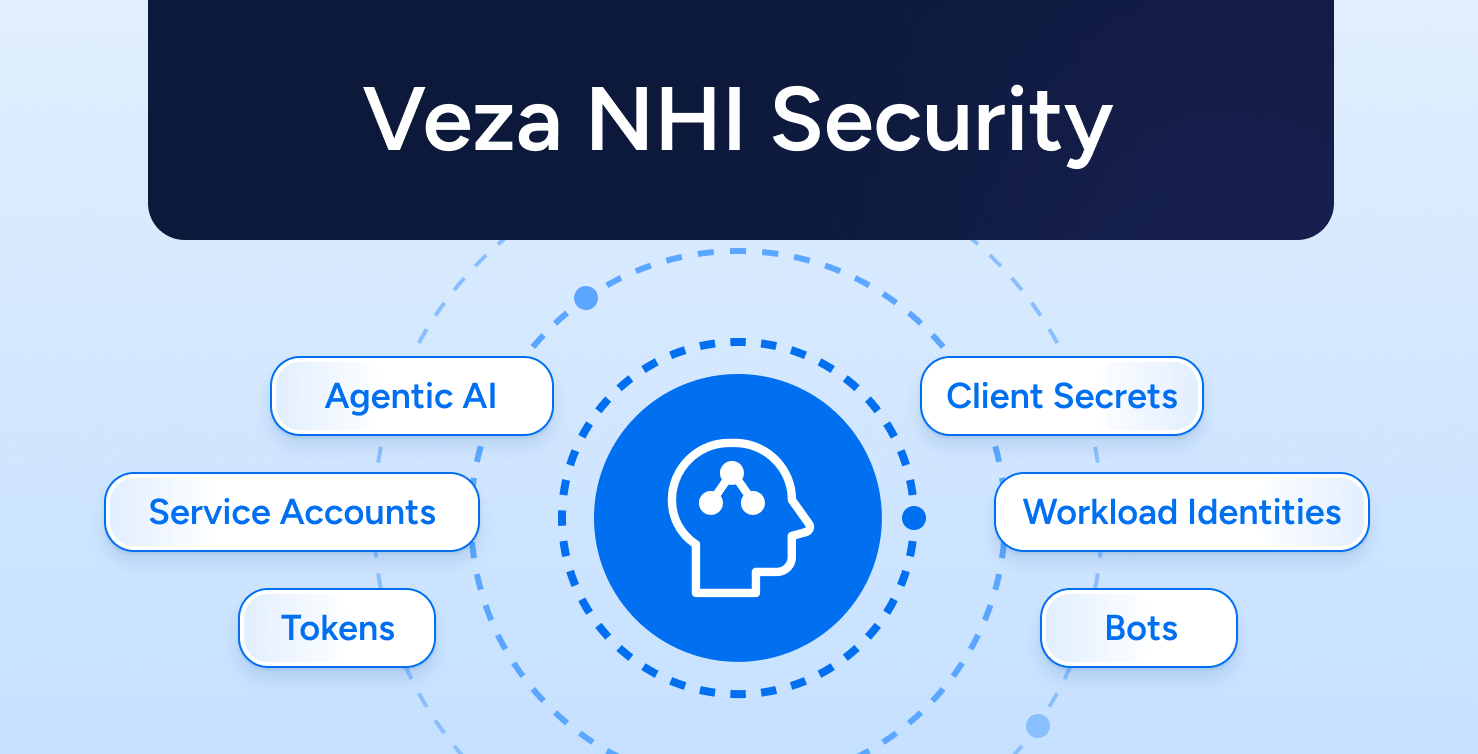
Modern identity governance is built for hybrid infrastructure, nonhuman identities, and security at scale.
Veza delivers the execution layer for next-gen IGA. With real-time access intelligence, automation, and full support for nonhuman identities, Veza helps you replace or augment legacy IGA without compromising control, visibility, or speed.
Why Legacy IGA Falls Short
Traditional IGA solutions were designed for static infrastructure and predictable access patterns. They were never built to govern access across modern, cloud-first, identity-driven environments. As organizations adopt multicloud architectures and expand third-party integrations, these legacy platforms are showing their age.
Common challenges include:
Manual, infrequent access reviews that result in stale entitlements and missed risk
Lack of visibility into nonhuman identities like service accounts, bots, and automation tools
Siloed access data across SaaS apps, cloud platforms, and internal systems
High operational overhead to configure, maintain, and scale
Weak enforcement of least privilege and standing privilege policies
Compliance gaps with frameworks such as SOX, GDPR, SOC 2, HIPAA, and PCI DSS
Legacy IGA tools can no longer scale to meet the access governance demands of today’s hybrid enterprises.
Veza Key Capabilities Driving Next-Gen IGA Deployments
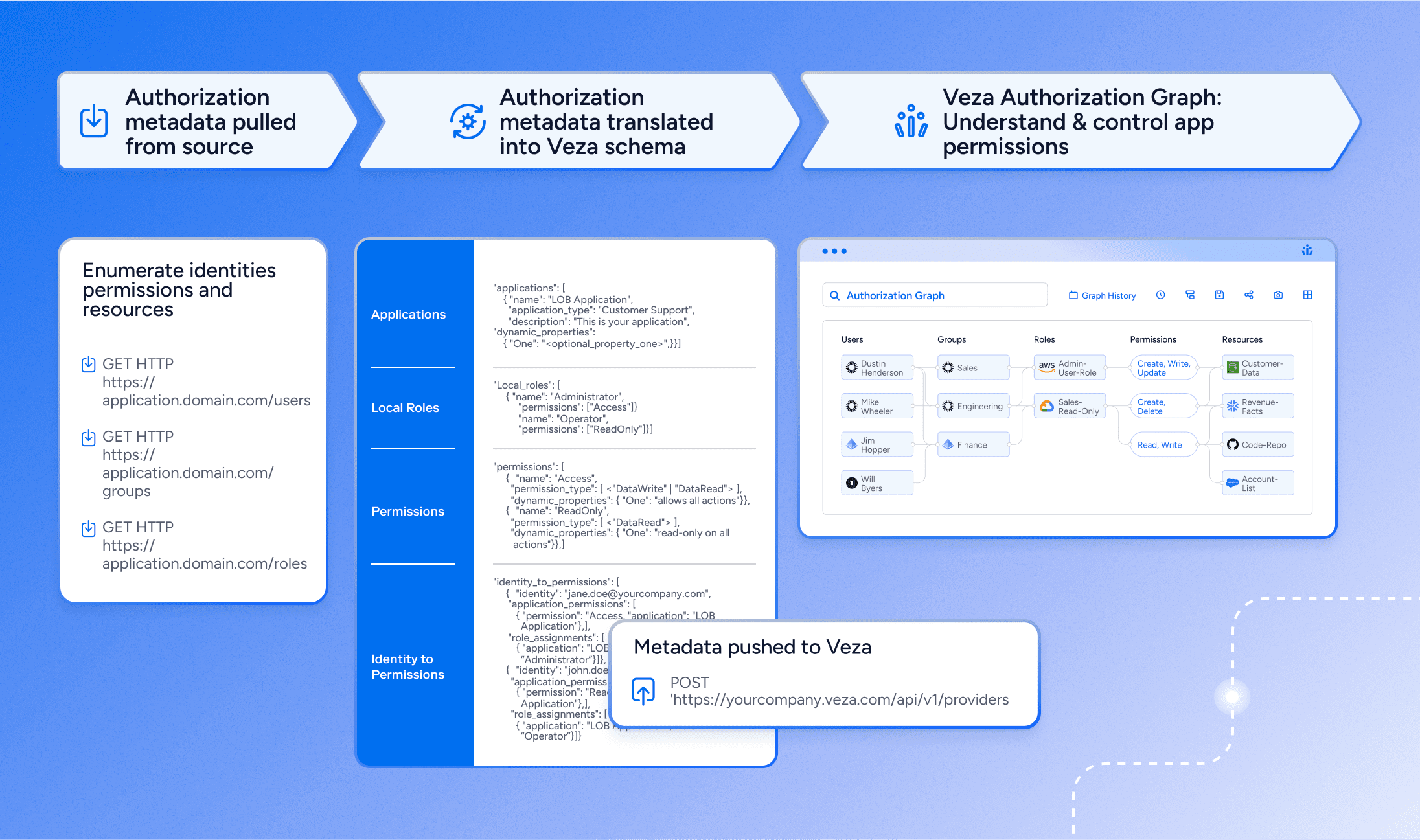
Modern IGA demands both agility and depth. According to Gartner, organizations adopting next-gen IGA should focus on reducing risk, increasing automation, and accelerating time to value. Veza delivers on this by overlaying your existing IAM, directory, and infrastructure systems with an identity-aware access control plane—whether you’re replacing a legacy IGA, augmenting a lightweight tool, or launching your first governance program, Veza provides the critical components to get it right from day one.
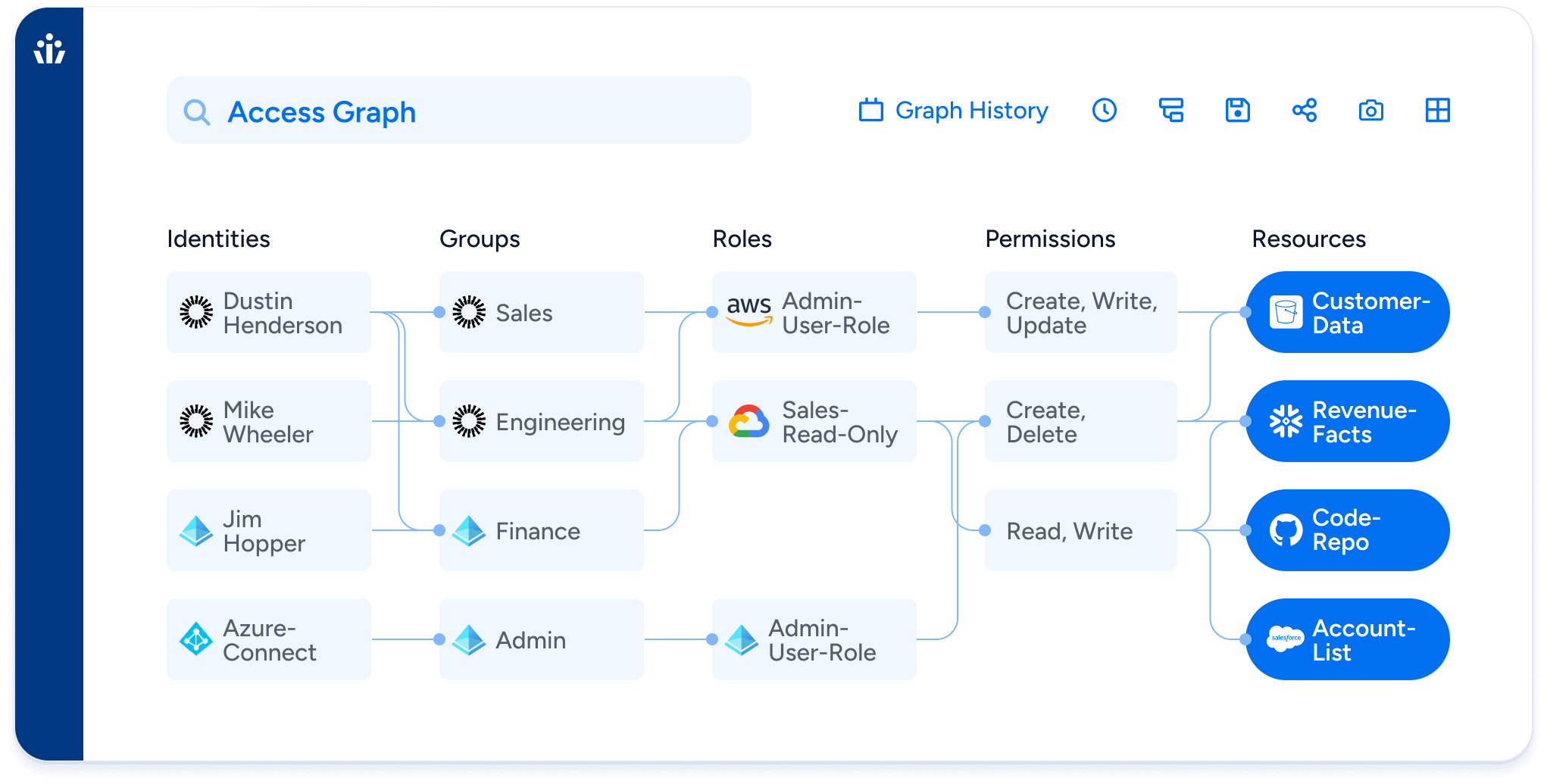
Unified Access Visibility
Gain real-time insight into who has access to what, across both human and nonhuman identities. Veza’s Access Graph maps entitlements, groups, and roles across AD, Okta, Entra ID, AWS, Snowflake, and more.
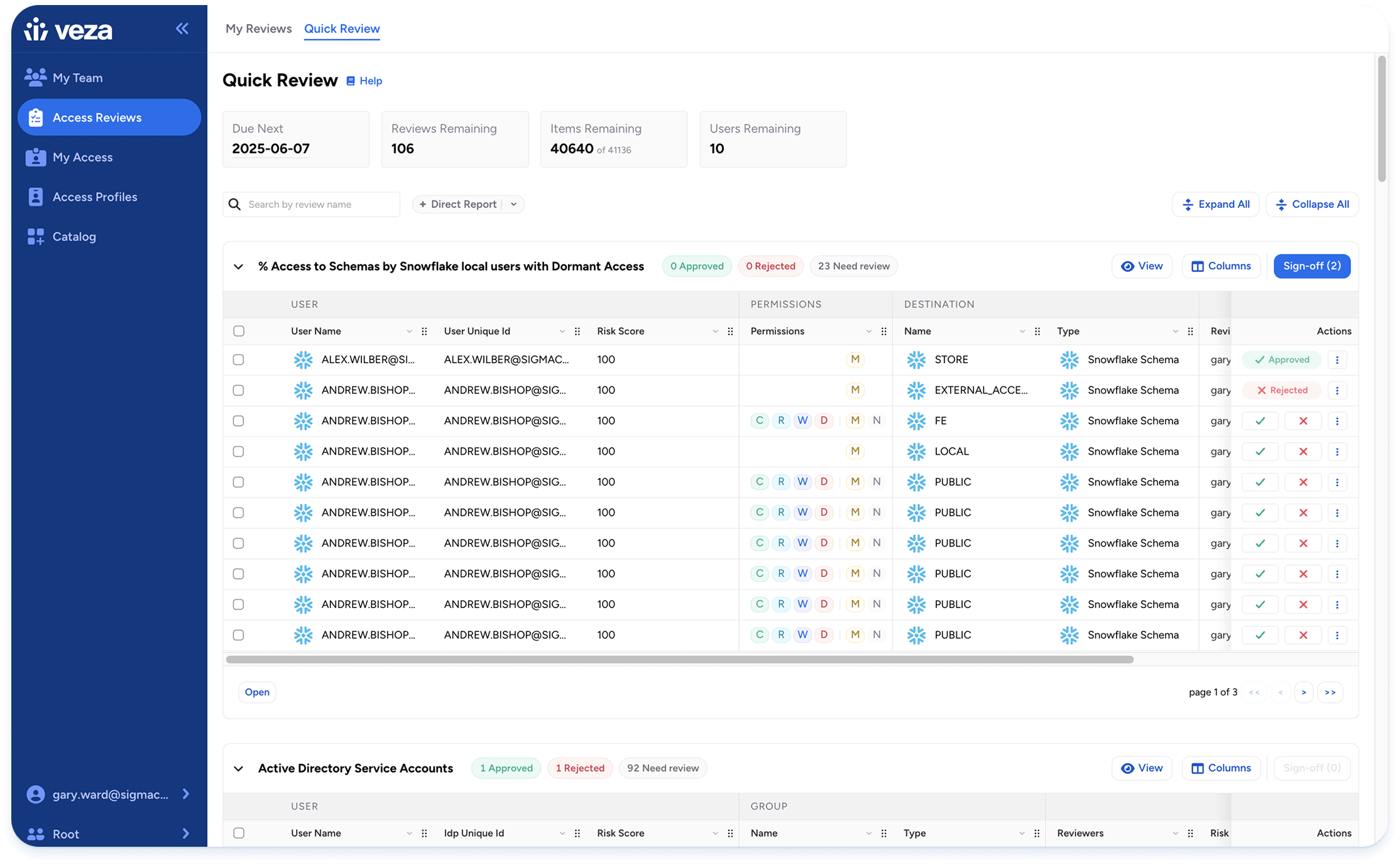
Automated Access Reviews
Streamline certification campaigns with intelligent scoping, dynamic delegation, and policy-based automation. Reduce cycles by up to 7x and improve reviewer accuracy using contextual data, peer comparisons, and usage insights.
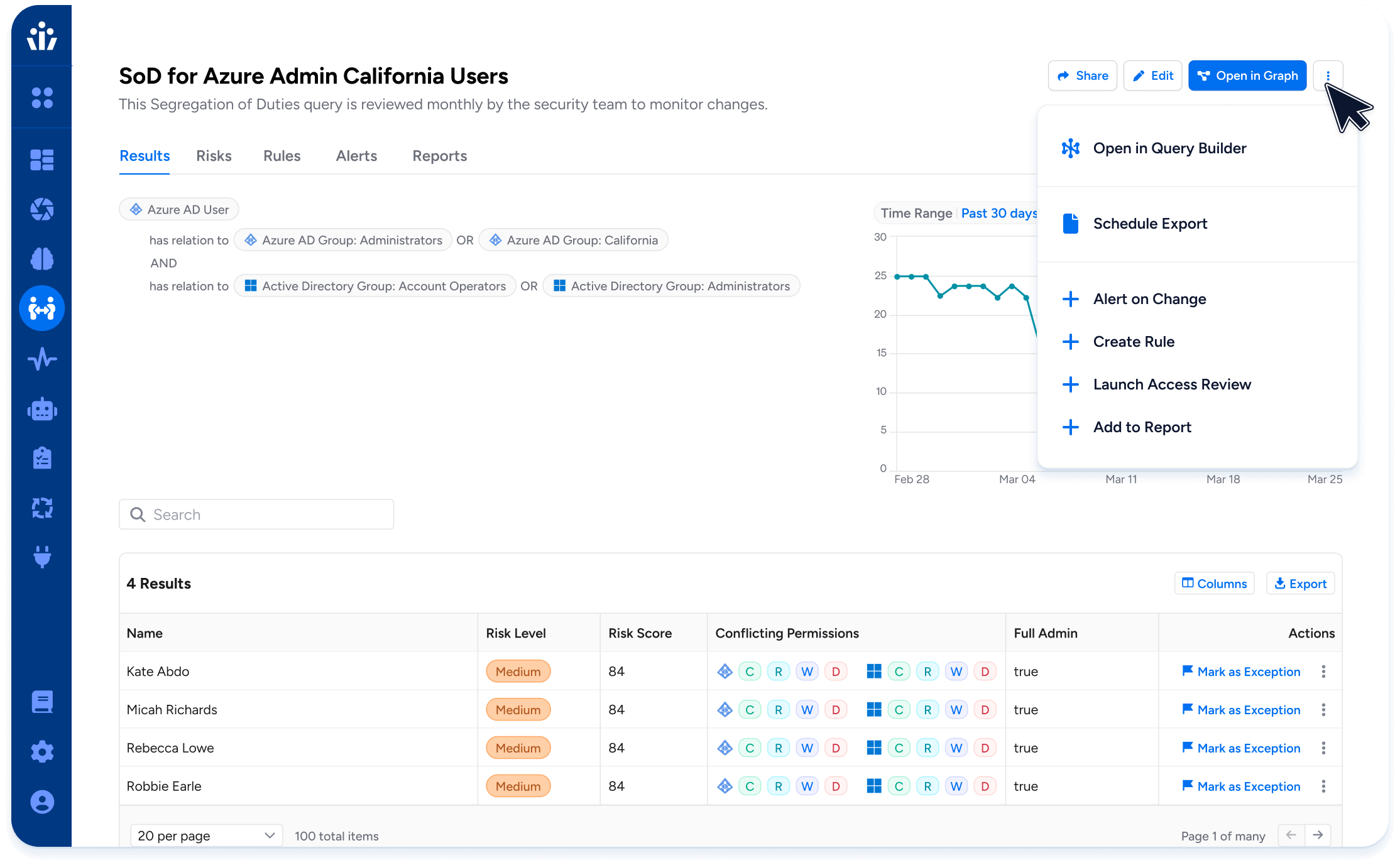
Policy-Based Enforcement and Risk Detection
Enforce least privilege with policies that detect SoD violations, excessive access, and dormant accounts. Trigger remediation workflows in real time via ITSM integrations like Jira and ServiceNow.
Governance for Nonhuman Identities
Discover, classify, and govern machine identities and service accounts at scale. Apply the same access reviews, policies, and enforcement used for human users on the identities that legacy IGA platforms often ignore.
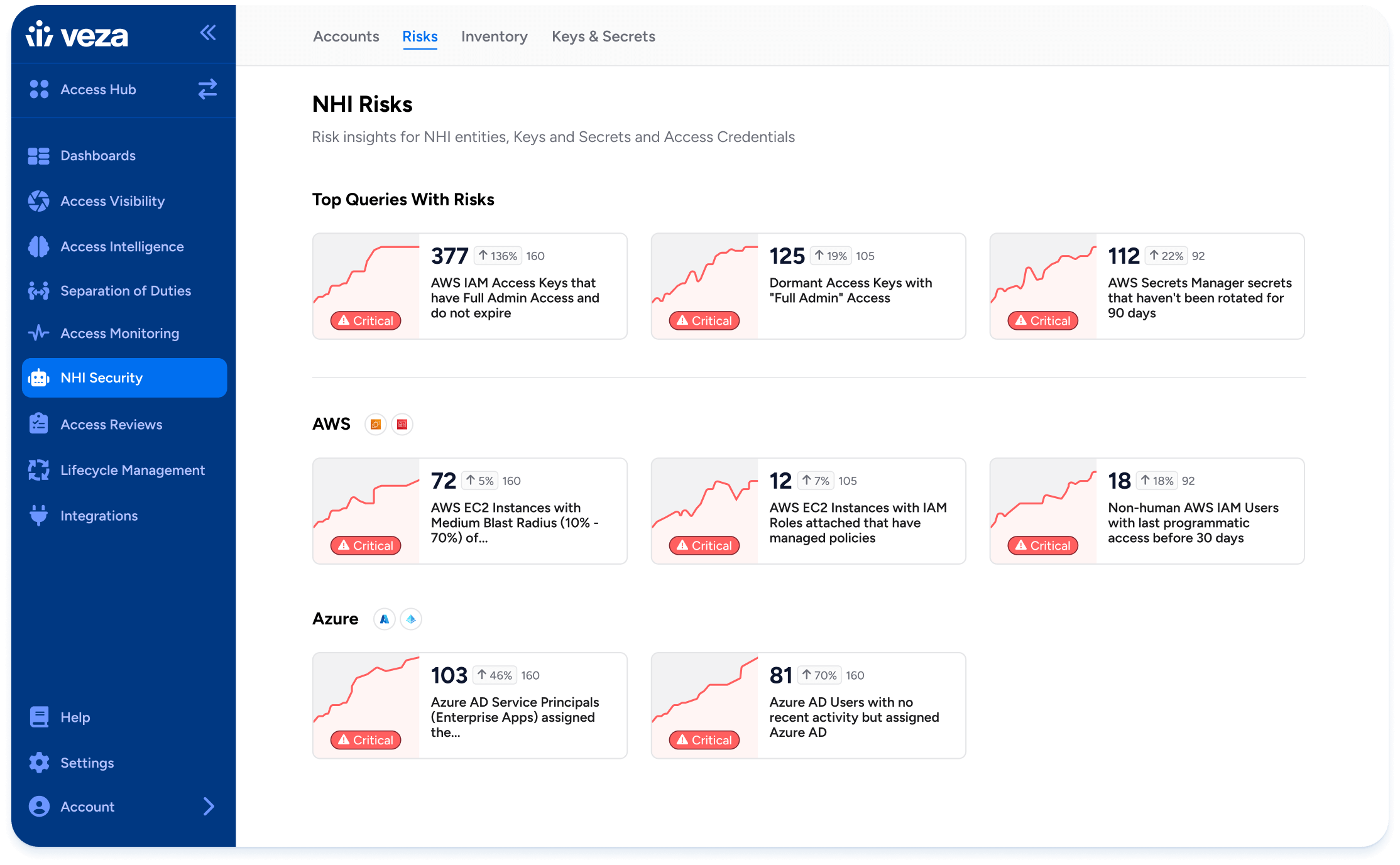
Access Profiles
Model job roles and responsibilities with reusable, fine-grained access templates. Enforce least privilege without relying on brittle role engineering or static policies.
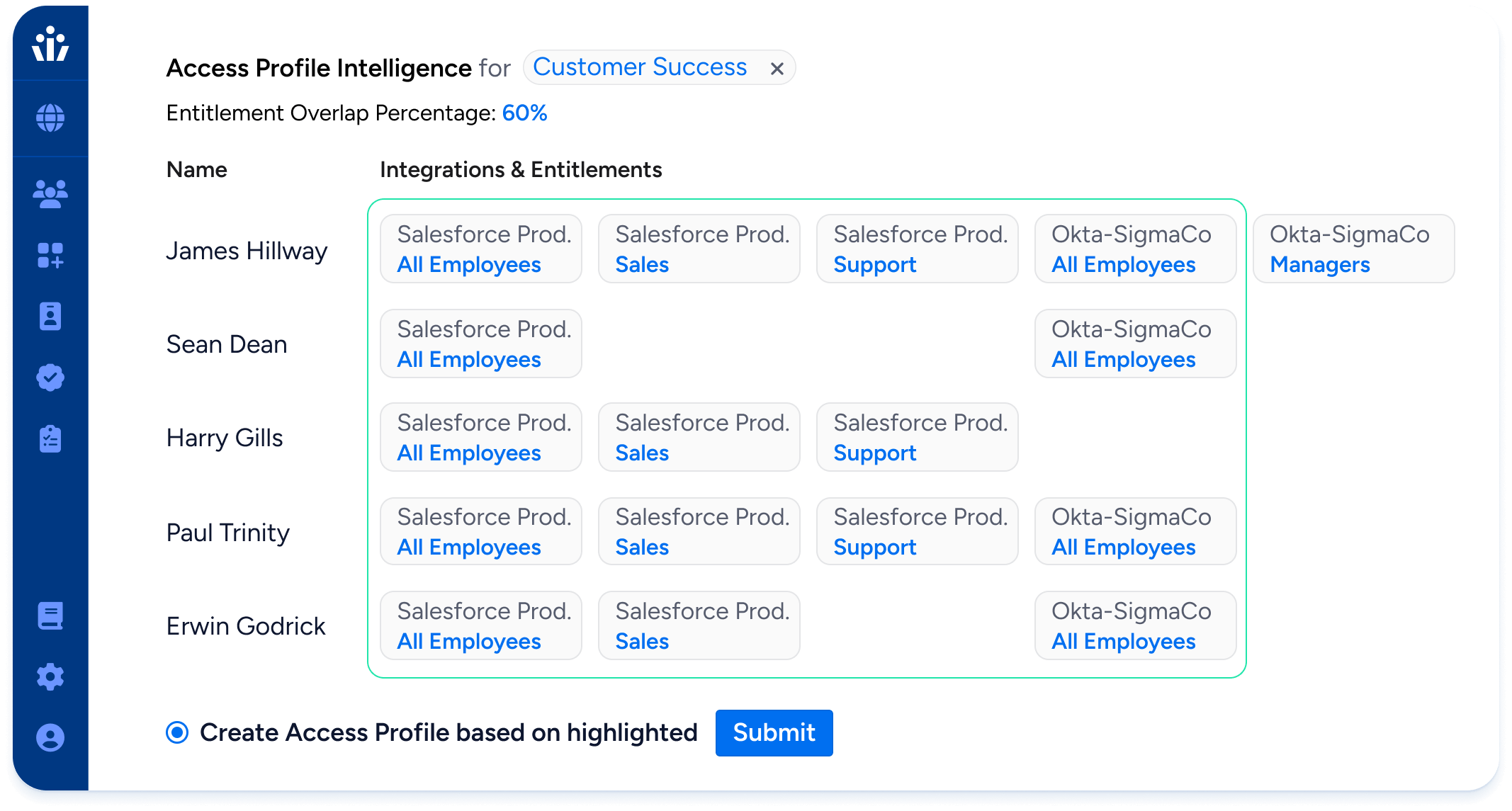
Audit-Ready Compliance Reporting
Deliver exportable, real-time reports for SOX, GDPR, HIPAA, SOC 2, PCI, and more. Cut audit prep time and ensure continuous assurance with up-to-date access visibility.
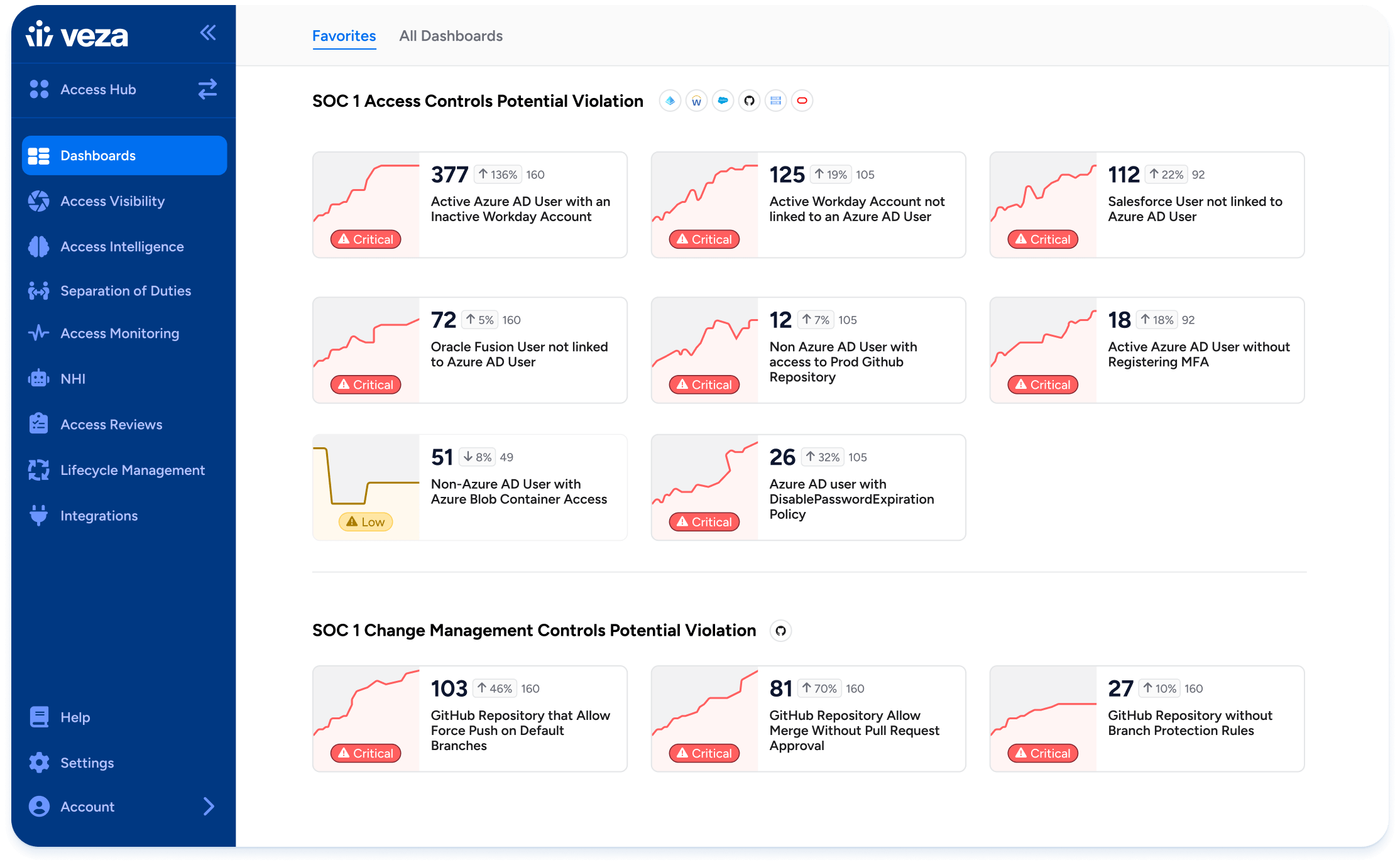
DevOps & Workflow Integration
Embed access governance into CI/CD pipelines and infrastructure-as-code with Veza’s Open Authorization API (OAA). Automate provisioning, deprovisioning, and access decisions across ITSM and DevOps tools.
Customer Success Stories
Learn More About Modern IGA
Modern identity governance requires more than role modeling and static workflows. Veza enables security, identity, and compliance teams to govern access with intelligence, speed, and scale, without the legacy IGA baggage.