Veza’s Access Graph
For the modern hybrid cloud enterprise, the scale of identity and access has moved beyond what can be accomplished with legacy tools built on old technology. Veza’s Access Graph was built to understand access permissions at scale and forms the foundation for Intelligent Access.
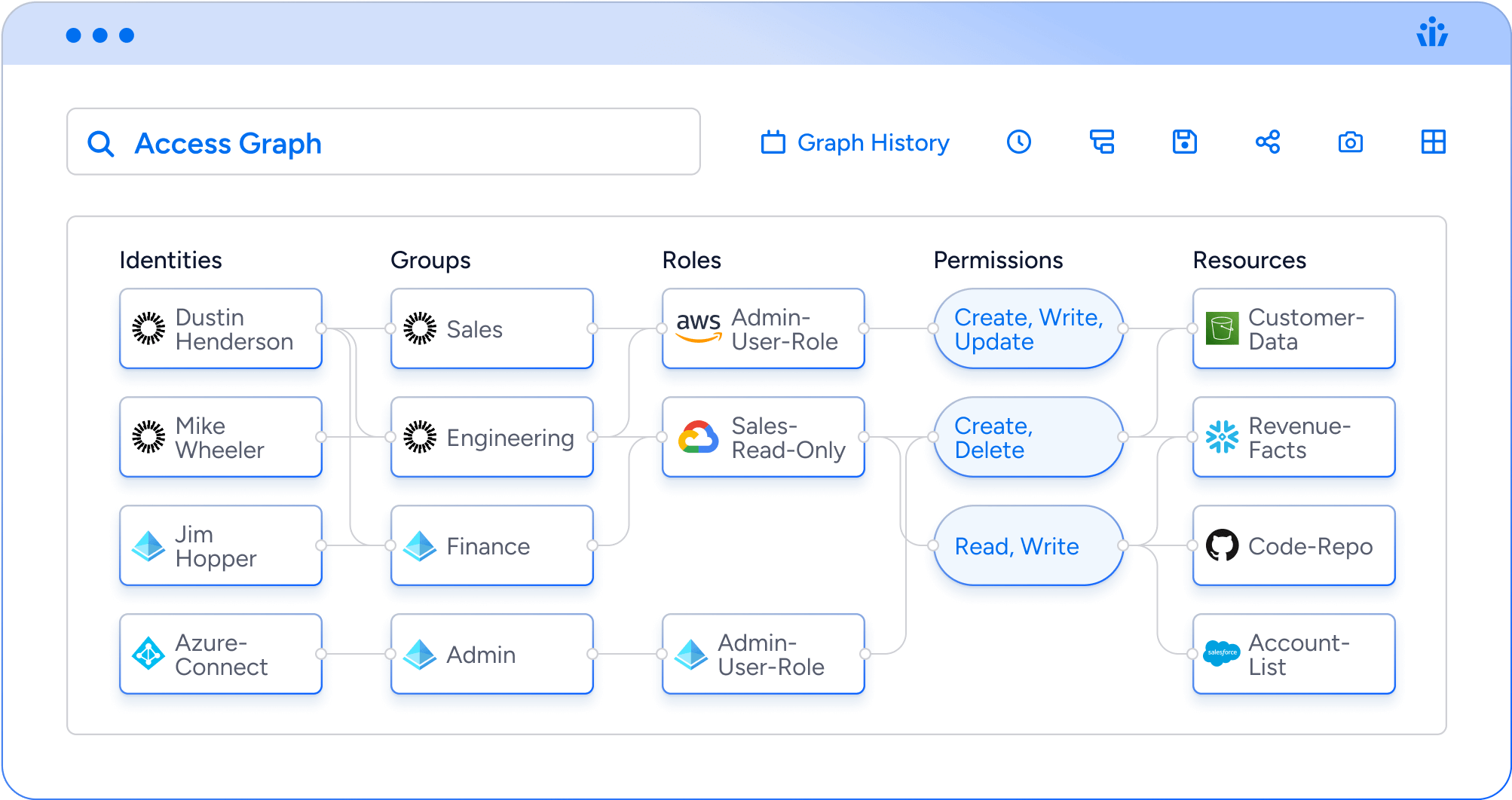


“Veza is looking forward for us. It allows us to understand who, what, where, when, and why. If you can do that, you have the ability to secure any environment. And when you’re talking about a global organization, that’s what you need.“
David Tyburski | VP of Information Security and CISO


“Having a world-class cybersecurity program that protects our brand, reputation, investors and intellectual property is of paramount importance to our firm, and we are continuing to incorporate innovative technology solutions. Our team is always looking for ways to develop a more comprehensive view of access across all of our applications and cloud infrastructure to allow us to modernize the firm’s access controls. We are excited to partner with Veza to help us accomplish this.”
Adam Fletcher | Chief Security Officer

“Using Veza, our security teams have gained valuable visibility across our systems – apps, infrastructure, and data, to better understand who can access what, helping drive stronger privileged access security practices.“
Jenner Holden | CISO, Axon


“Stitching together identities with data sources and showing the connections between them in a way that’s easy to consume — it’s a simple idea, but a complex problem to solve. Veza makes the process of understanding who has access to what really, really easy.“
Dave Farrow | VP, Information Security, Barracuda Networks
Learn More
-
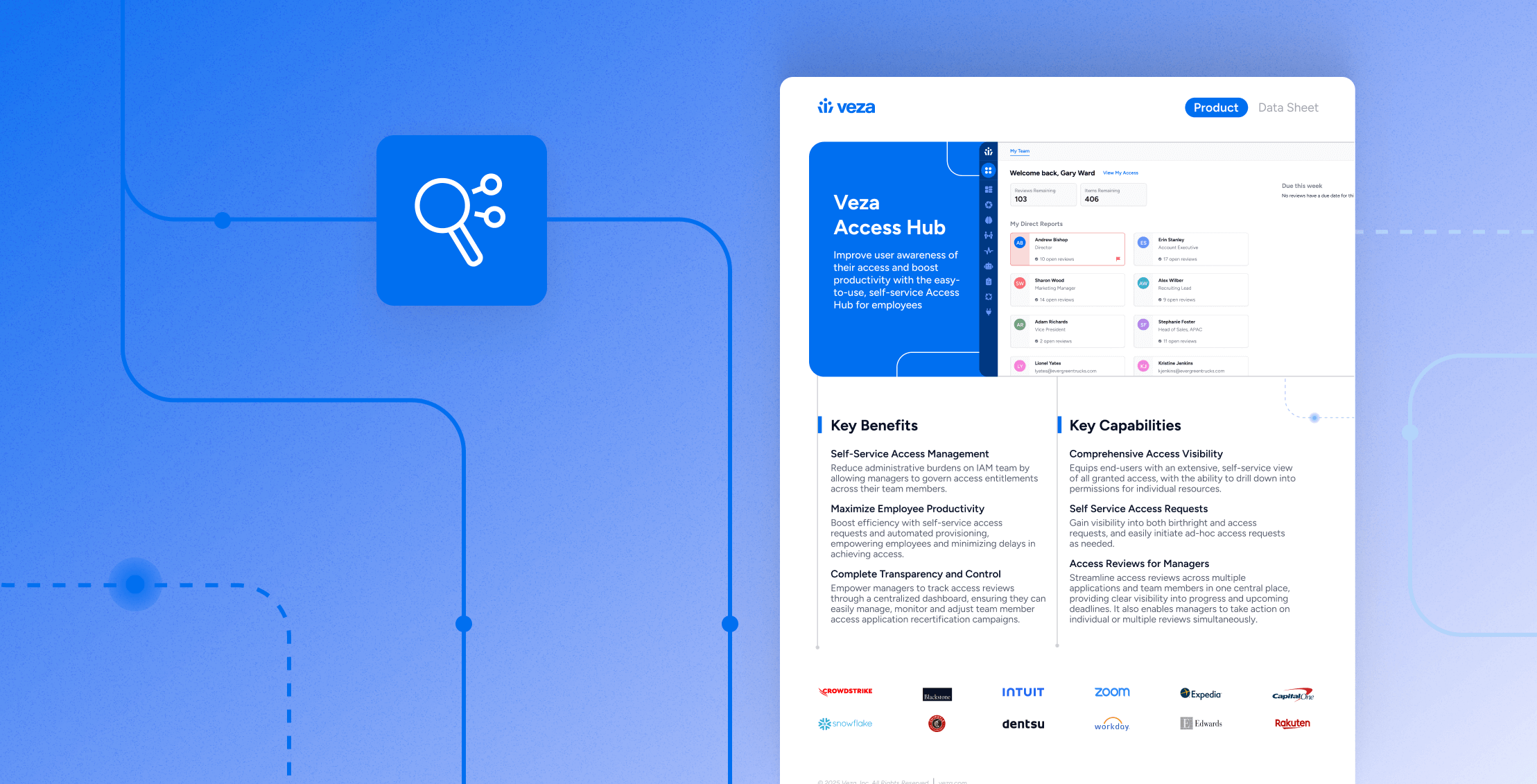 Data Sheet
Data SheetAccess Hub Data Sheet
Learn more -
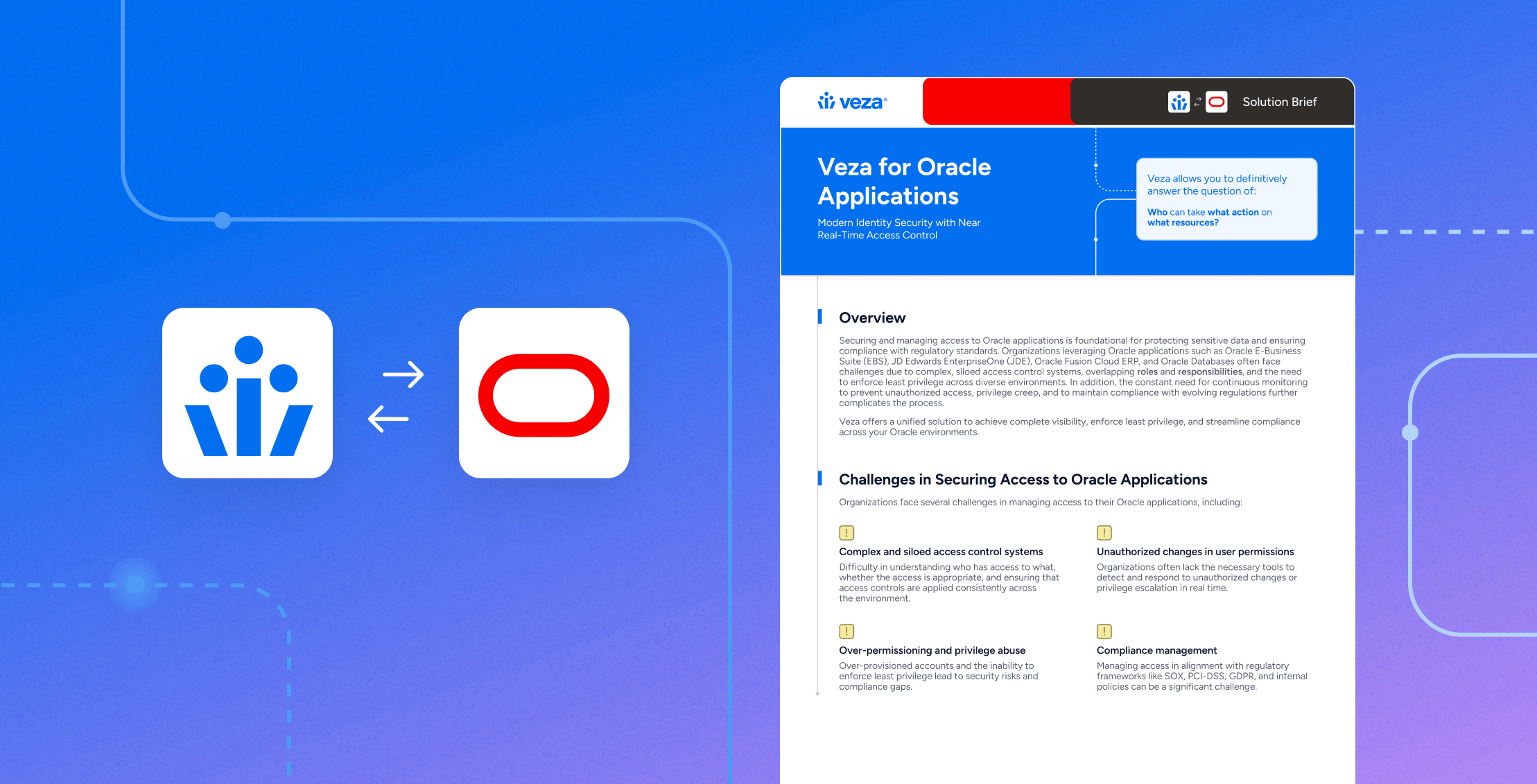 Solution Brief
Solution BriefVeza for Oracle
Learn more -
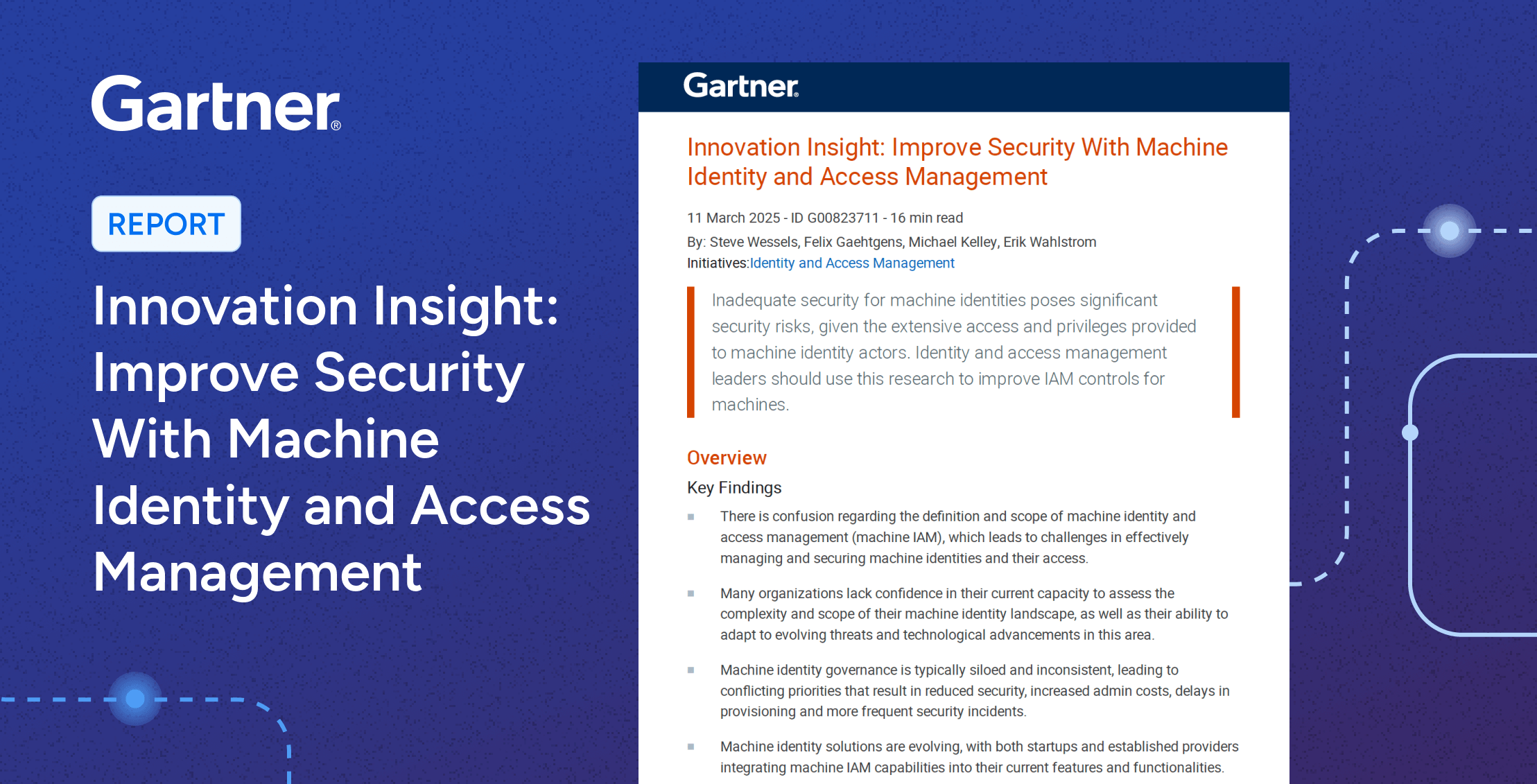 Report
ReportGartner® Report – Innovation Insight: Improve Security With Machine Identity and Access Management
Learn moreMachine identities now outnumber human identities — and most organizations aren’t ready.Gartner explains why machine IAM is critical to prevent breaches, outages, and compliance failures. Learn how to discover, govern, and secure machine identities before risks spiral out of control. In our opinion, the report explains: Gartner, Innovation Insight: Improve Security With Machine Identity and […]