Glossary
-
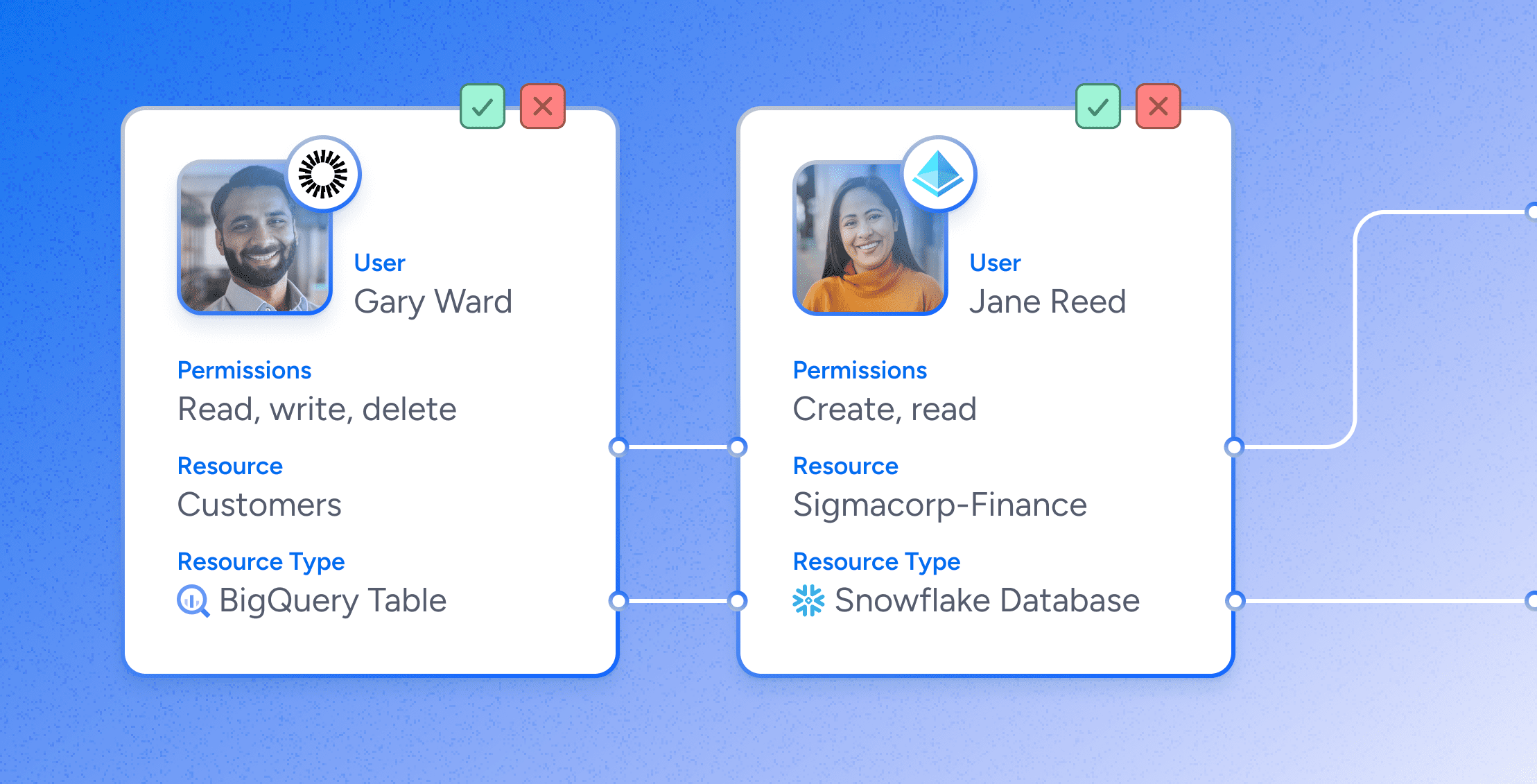
User Access Reviews: How They Work & Best Practices
Learn more -

Identity Security Spotlight: Cisco announces “Identity Intelligence”
Learn more -

Veza @ Blackstone: Modernizing IGA with Automation and Intelligence
Learn more -
A field guide to bad permissions part 4: policy-violating permissions
Learn more