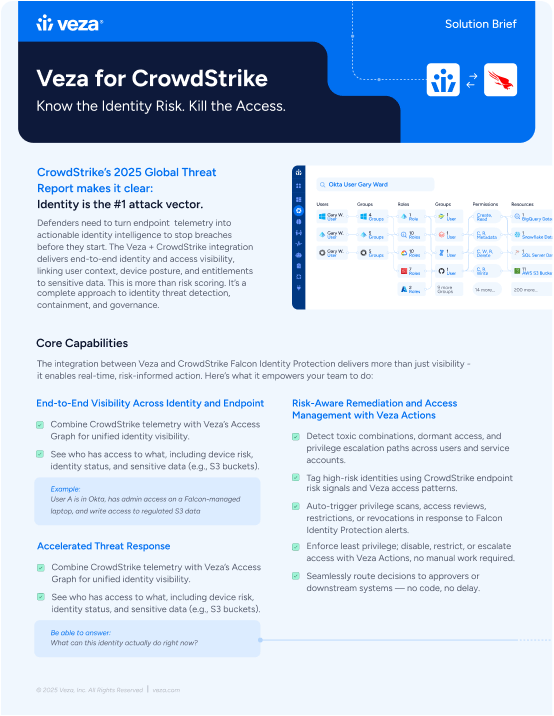
Veza + Crowdstrike Integration
Leverage CrowdStrike Falcon Identity Protection’s risk scores and severities in Veza to quickly identify, manage, and restrict access to critical applications, systems, and data in the event of an identity-based threat.
Benefits
Determine blast radius from a compromised identity
- Veza instantly helps visualize effective permissions of a compromised human or machine user identified by CrowdStrike Falcon Identity Protection across cloud and on-premise applications (i.e. Snowflake tables, GitHub repositories, CRM applications such as Salesforce).
- Visualize permissions and conduct automated access reviews and certifications to quickly mitigate impact by a compromised user or a machine identity.
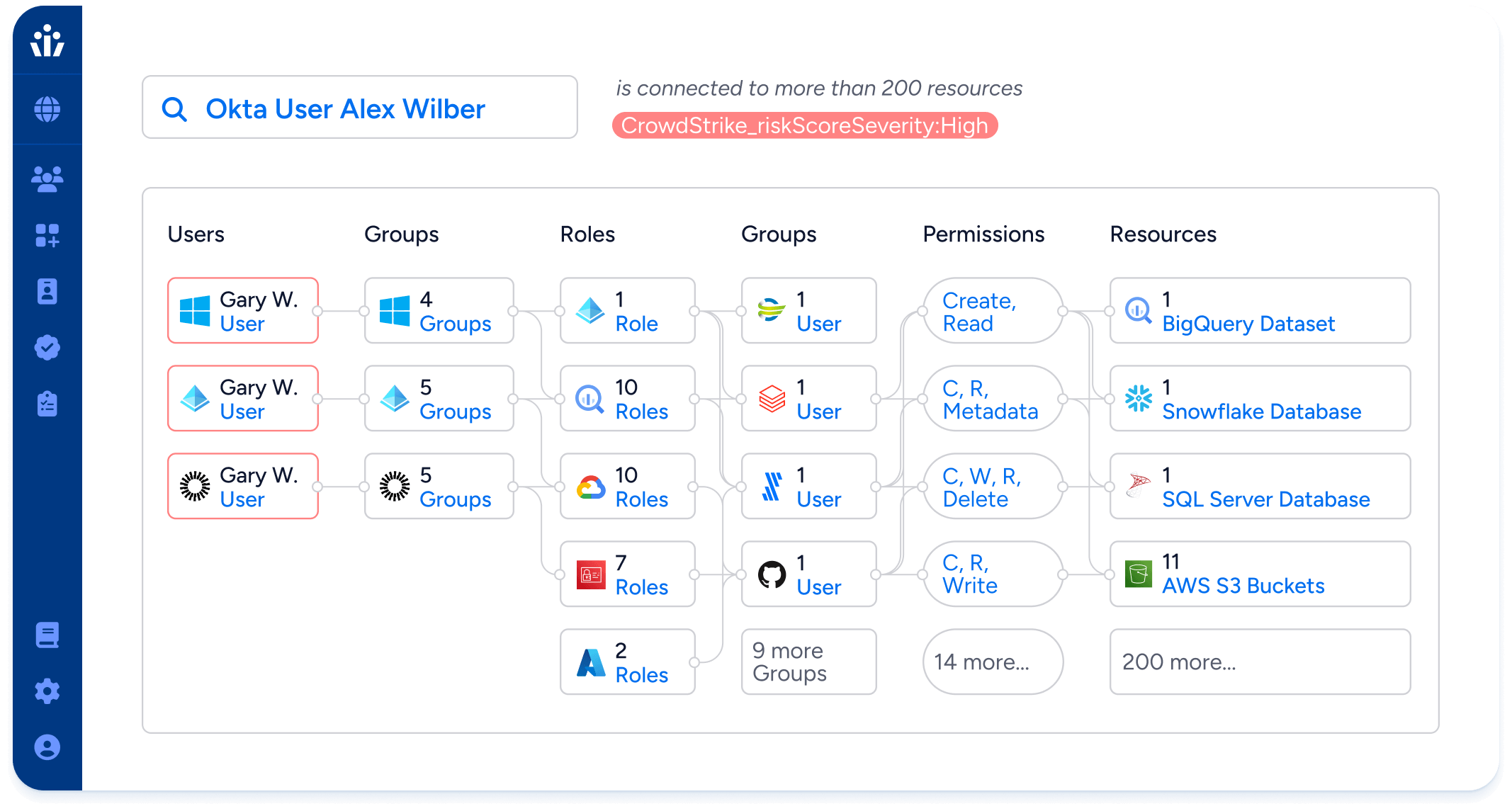
Prioritize threat response based on user access
- Use the Veza Access Graph to prioritize remediation for users with the most access to sensitive data.
- Streamline remediation and minimize the attack surface to prevent breaches of sensitive data.
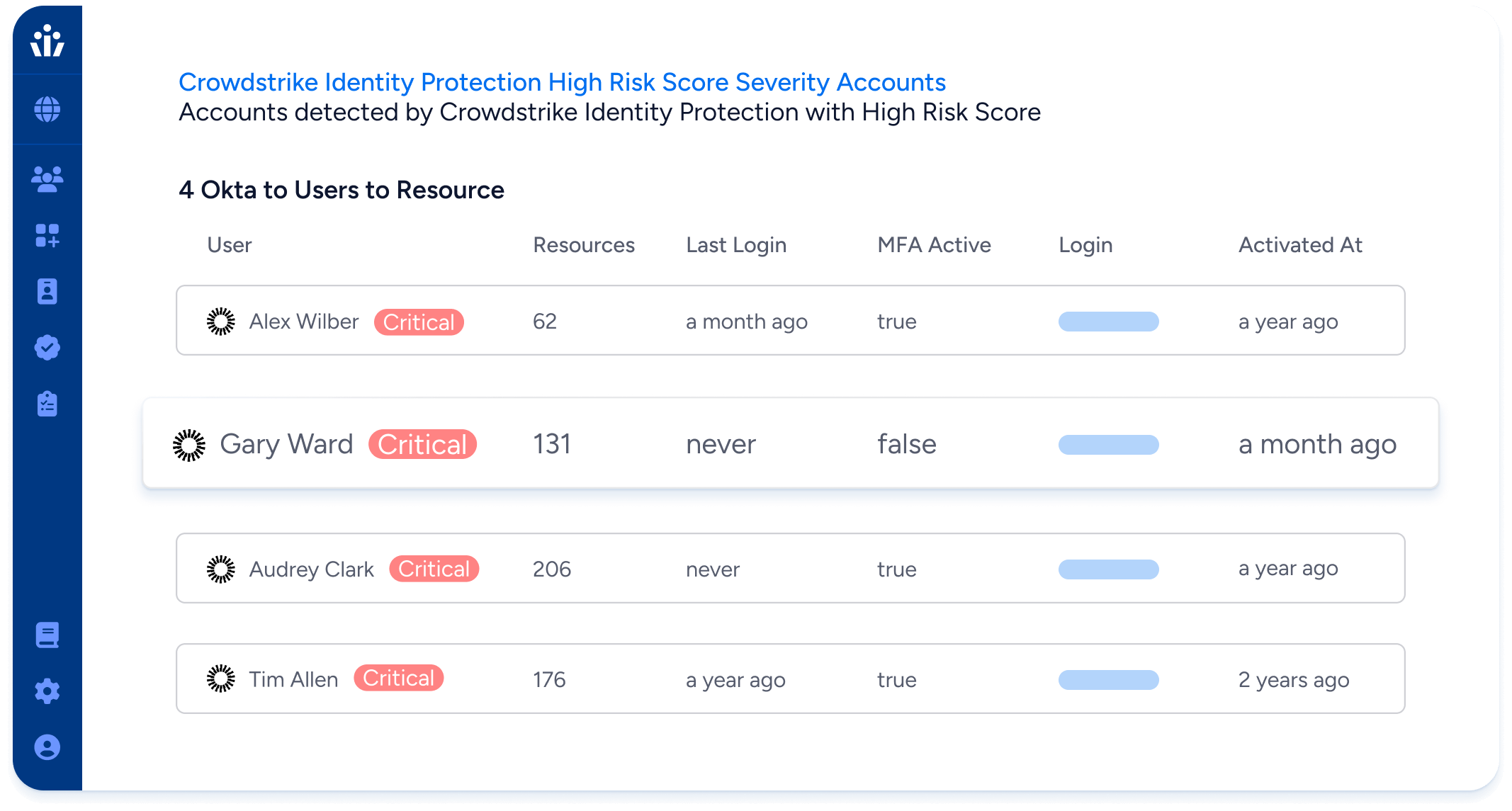
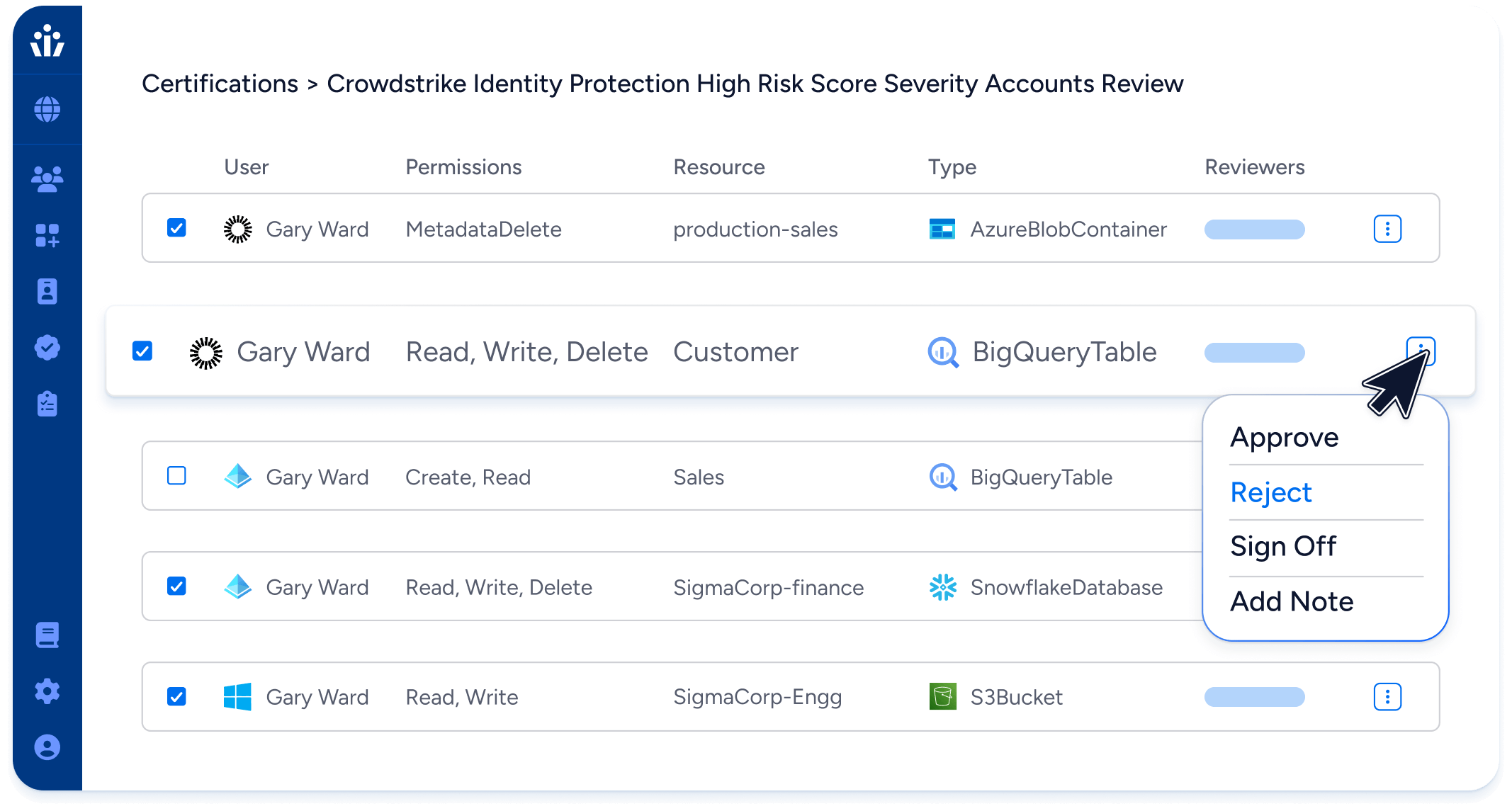
Conduct micro-certifications and just-in-time access reviews
- Modernize identity access and identity governance processes by immediately reviewing at-risk access from CrowdStrike’s identity-based risk scores.
- Improve security posture and prevent risk exposure without waiting for the next full access review.
Learn More
-
 Product
Product2025: The Year of Product Innovation
Learn more -
 IAM
IAM11 Best Zero Trust Providers for 2026
Learn more -
 Company
CompanyVeza Identity & Access Research Report Reveals Identity Permissions Sprawl has Reached Critical Levels Amid Explosion of Machine and AI Agent Identities Across the Enterprise
Learn moreThe average identity now holds ~100K permissions, 38% of all accounts are dormant, 16.5% of total permissions belong to inactive users, and 27.8% of permissions remain ungoverned REDWOOD SHORES, Calif. – December 11, 2025 — Veza, the pioneer in identity security, today released the definitive identity and access permissions research report showing that enterprises are […]