-
 Data Security
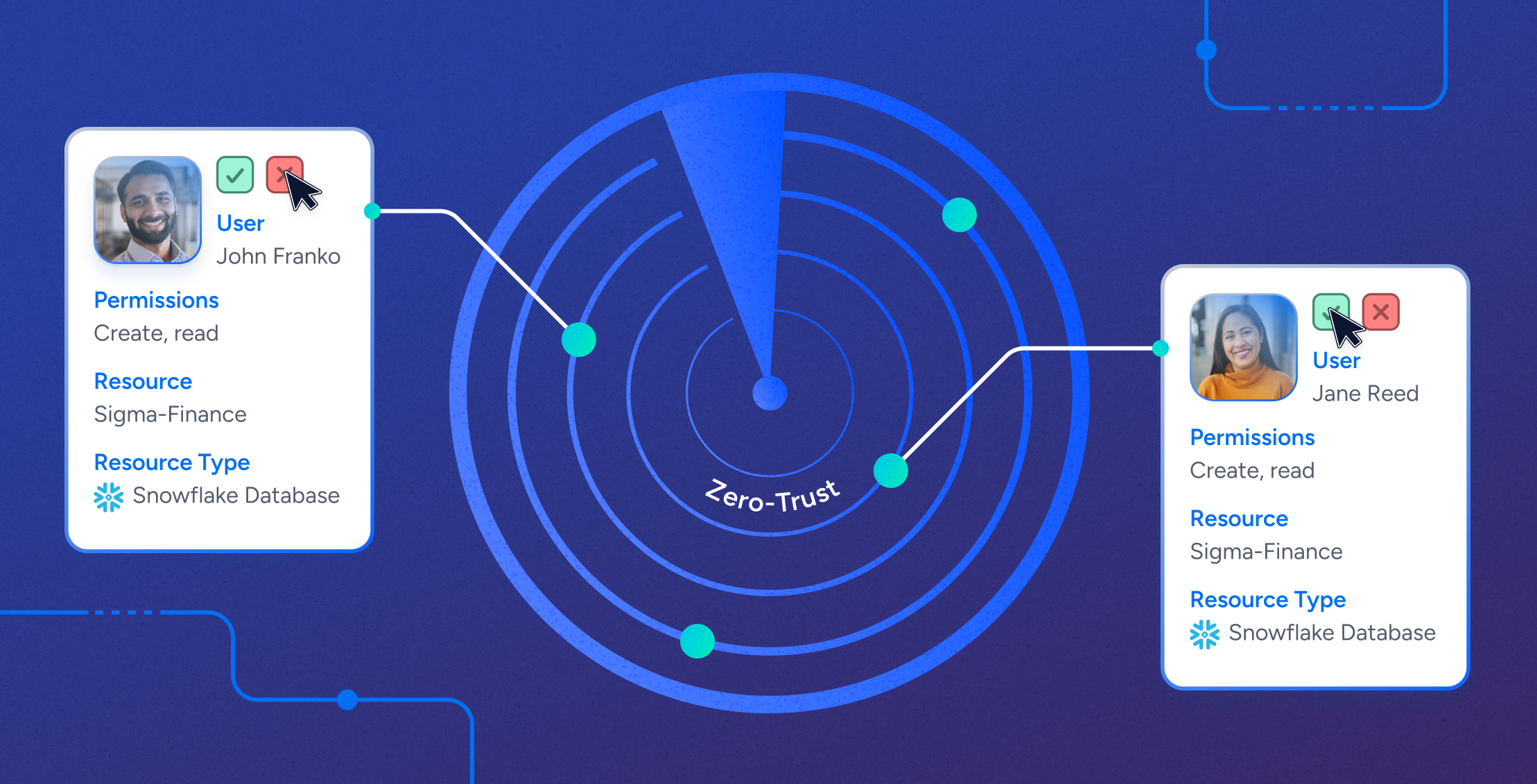
Data SecuritySecuring Snowflake: A CISO’s Guide to Effective Access Control
Learn more -
 Thought Leadership
Thought LeadershipAI for Identity Security: My Journey, Our Perspective, and Veza’s Strategy
Learn more -
 Identity Security
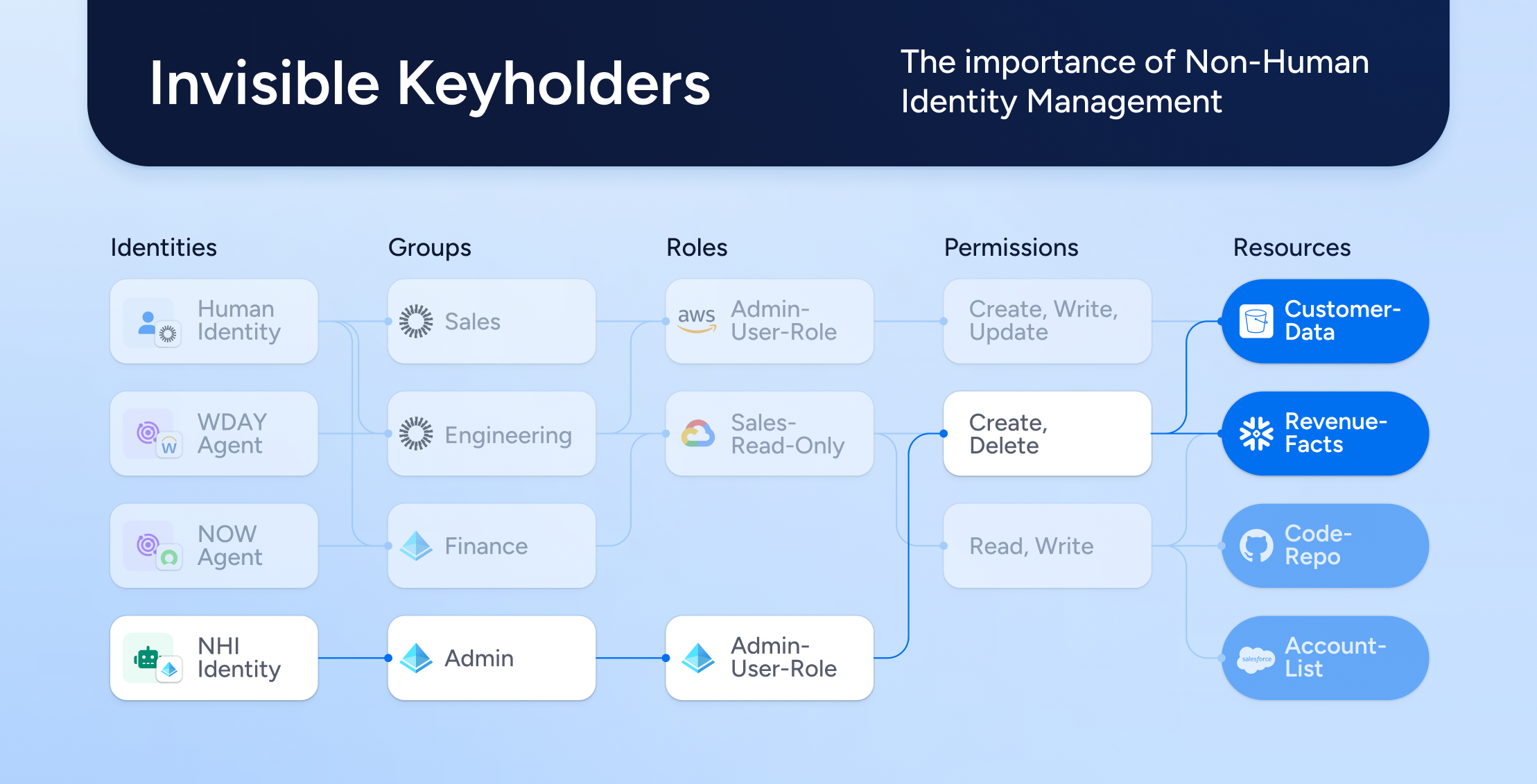
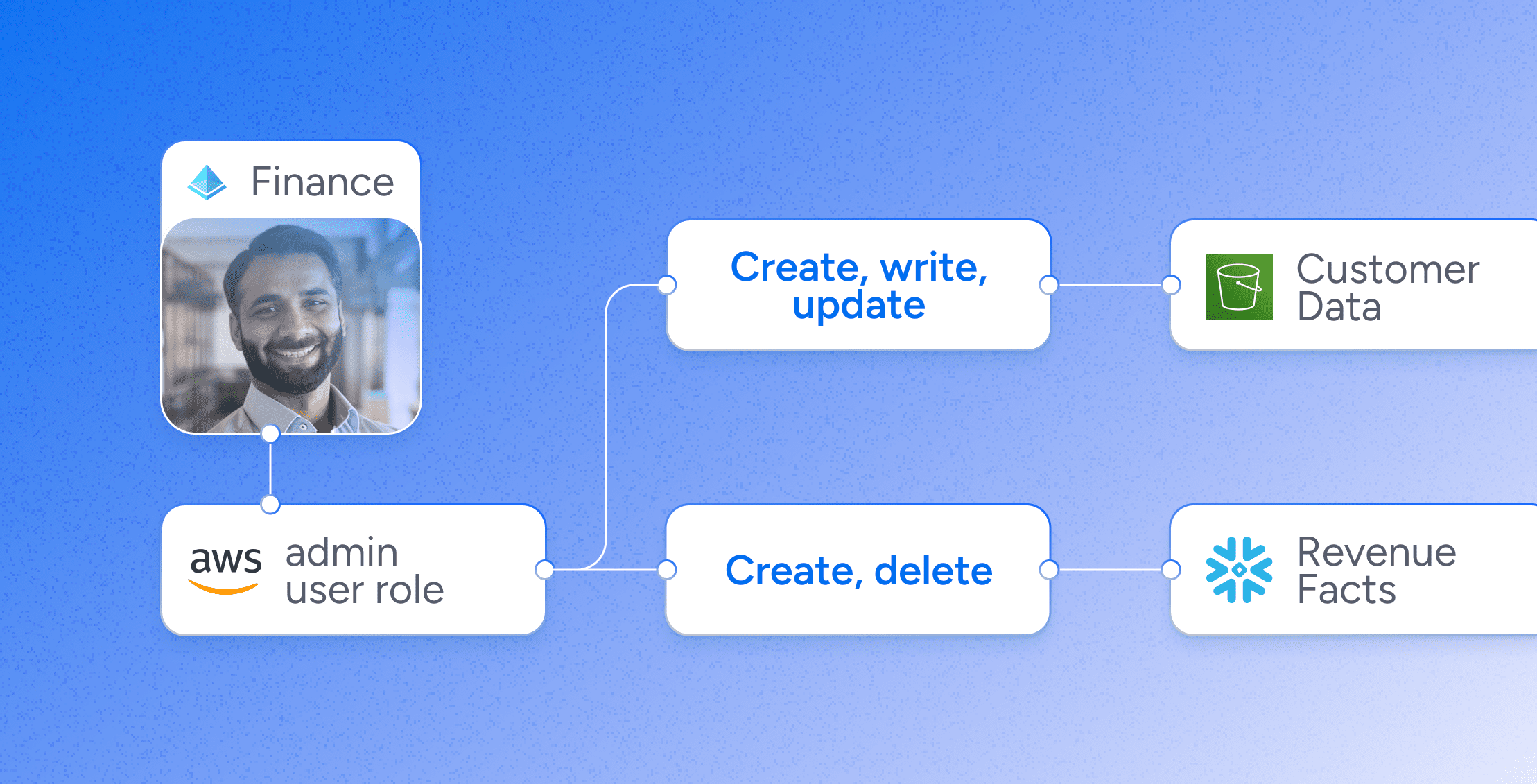
Identity SecurityEmpowering Business Initiatives with Modern Identity Security
Learn more -
 Identity Security
Identity SecurityIdentity Security Spotlight: Ransomware attack on Ascension
Learn more -
 Thought Leadership
Thought LeadershipHow to leverage Intelligent Access to de-risk the breach
Learn more -
 Product
ProductA field guide to bad permissions part 4: policy-violating permissions
Learn more