
SailPoint, Saviynt, and Veza are three prominent players in the identity security space. Each offers solutions for managing and securing user access to applications and data.
Today, identity security is arguably one of the most important barriers between your organization’s sensitive information and cybercriminals. According to Expel’s Annual Threat Report, identity-based incidents accounted for 64% of all investigated in 2023—a volume increase of 144% from 2022.
The right identity security strategy can significantly reduce the risk of security breaches and ensure that your organization stays compliant with regulatory requirements. When considering using an identity security solution, it’s important to consider factors such as ease of implementation, scalability, accuracy and whether it can manage on-premise and cloud environments.
This article takes a closer look at SailPoint, Saviynt, and Veza, exploring their features, pros, and cons so you can determine the best fit for your organization’s identity security and management needs.
SailPoint vs Saviynt vs Veza
Although SailPoint, Saviynt, and Veza are leading contenders in the identity security space, they’re not the same. We’ll provide an overview of each platform, highlighting key features and benefits to help you understand what sets them apart.
What is Veza?

Veza is the identity security company designed to tackle one of cybersecurity’s most challenging questions: Who can take what action on what data? While this might seem straightforward, the complexity of today’s enterprise environments makes it difficult for most organizations to answer this question accurately.
Veza’s platform is built to provide a comprehensive, near real-time view of all permissions across your enterprise, including cloud infrastructure, data systems, SaaS apps, and on-premise apps. Powered by the Access Graph, Veza connects to your Identity Provider (IdP), HR platform, and every application and data system, capturing detailed authorization metadata. This allows organizations to enforce least privilege by monitoring all human and non-human identities, including local accounts, across every system.
Veza goes beyond traditional IGA tools by offering a deep dive into permission metadata and Access Control Lists, translating complex system-specific roles into plain language that business users can easily understand. With this level of granularity, you can accurately assess who has access to what resources, no matter how or where their identity is managed.
Veza’s platform also accelerates your time to value with quick and easy integration into your existing cloud architecture. Enterprises like Wynn Resorts, Expedia, and Blackstone trust Veza to manage privileged access, monitor cloud entitlements, govern data lakes, secure SaaS access, and automate access reviews and provisioning.
Learn more about how Veza can help your organization achieve least privilege and reduce the time to complete access certification by 86%.
What is SailPoint?

SailPoint solutions, including IdentityIQ and Identity Security Cloud (formerly known as IdentityNow), help organizations manage identities, secure sensitive data, and ensure compliance. The platform facilitates role creation and provides an overview of identities, including accounts from non-authoritative systems not mapped to a single identity, helping with effective access management.
SailPoint extends identity security coverage across an organization’s ecosystem, connecting IT resources with an AI-driven identity security solution. Its Identity Security Cloud offering can also automate identity security processes through a low-code SaaS workflow interface.
However, traditional IGA tools like SailPoint are limited in today’s complex IT environments. They often rely on data models suited for on-premises architectures and fully trusted networks, where users are governed via groups and role names.
This approach can lead to blind spots like assuming all employees are listed in a single source of truth (like Active Directory) and that role definitions accurately reflect permissions.
What is Saviynt?
Saviynt is an identity governance and administration (IGA) platform known for its cloud-native architecture and ability to support compliance across complex IT environments. Saviynt’s Enterprise Identity Cloud is designed to govern identities, manage access, and ensure security for both cloud-based and on-premise applications and data.
Saviynt’s platform integrates with various IT ecosystems, enabling seamless governance for cloud-based, hybrid, and on-premises environments. This integration capability supports organizations in their digital transformation efforts by providing a unified approach to identity management.
However, while Saviynt offers a robust set of features for identity governance and administration, it also faces limitations similar to other traditional IGA tools. Saviynt primarily integrates with IdPs like Okta, leaving it unable to detect local accounts. This can result in blind spots if local accounts exist.
Additionally, Saviynt often requires complex implementation processes, costly professional services fees and long deployment times, making integration with existing systems challenging and delaying time-to-value.
SailPoint vs Saviynt vs Veza: Quick Overview
| Features | Veza | SailPoint | Saviynt |
| Identity Governance | ✓ | ✓ | ✓ |
| Access Request Management | ✓ | ✓ | ✓ |
| Automated Access Reviews | ✓ | ✓ | ✓ |
| Near Real-Time Monitoring | ✓ | ✓ | ✓ |
| Effective Permissions Management | ✓ | ||
| AI-Driven Automation | ✓ | ✓ | ✓ |
| Cloud-Native Architecture | ✓ | ✓ | ✓ |
| Integration with 200+ Systems | ✓ | ✓ | ✓ |
| Zero Trust Implementation | ✓ | ✓ | ✓ |
| Third-Party Access Governance | ✓ | ✓ | ✓ |
| Quick Deployment Time | ✓ | ||
| Open Authorization API | ✓ |
SailPoint vs Saviynt vs Veza: Complete Review
Here, we provide a detailed overview of SailPoint, Saviynt, and Veza, focusing on their features, pros, and cons. This comparison highlights the strengths and weaknesses of each platform, helping you understand why Veza stands out as the best choice for identity governance and continuous compliance.
Veza
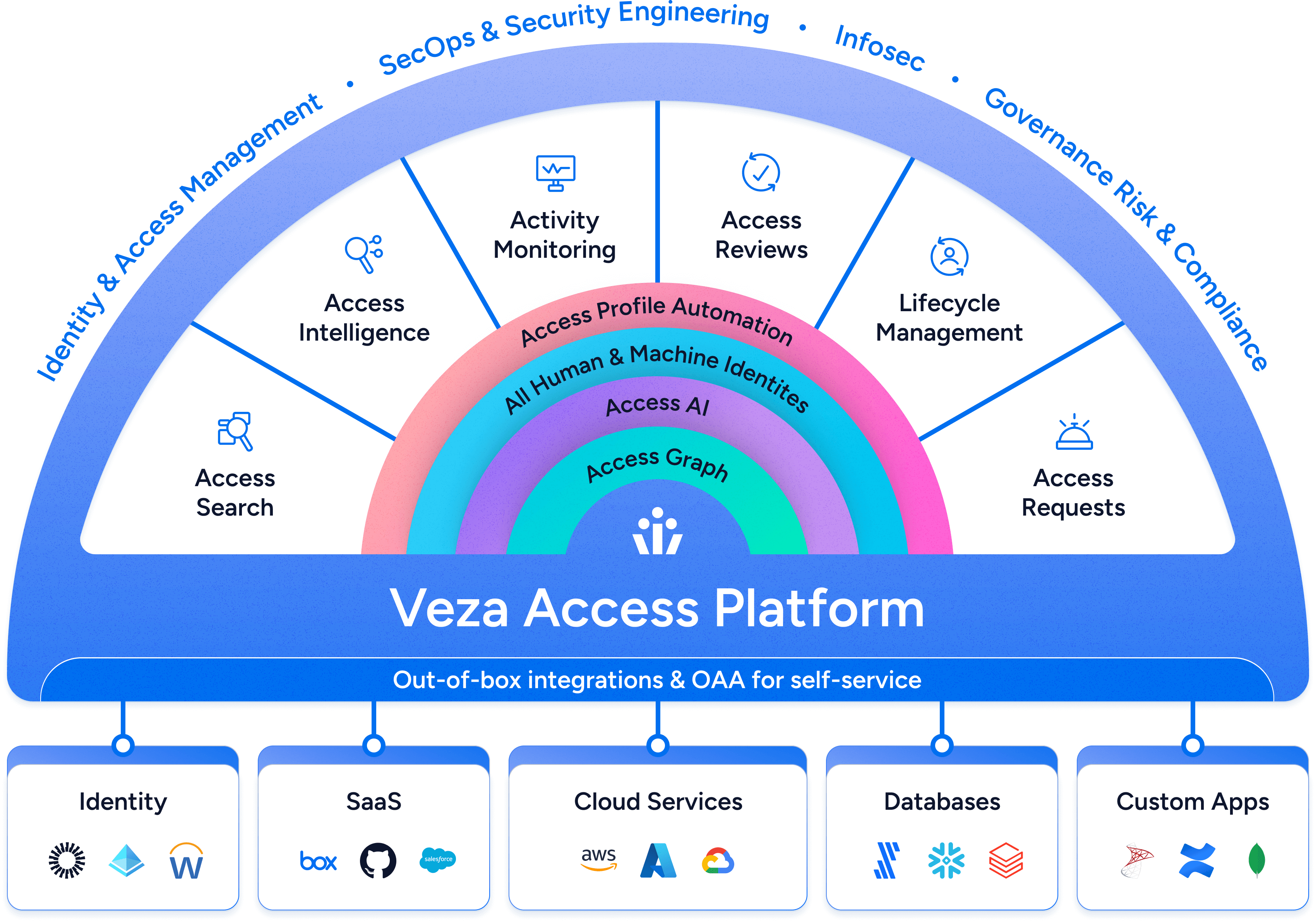
With more than 200 native integrations including Okta, AWS, Azure AD, Snowflake, Salesforce, Github, and more, Veza provides a truly complete picture of user permissions. It also offers an Open Authorization API (OAA) for custom integrations with proprietary applications. It helps identify and manage access more effectively so that permissions are correctly assigned and that unauthorized access is prevented.
Organizations can also use Veza’s insights to proactively protect apps and data by monitoring access in real time. It can automatically create notifications and tickets when new access is detected, allowing you to address potential security issues immediately. Ultimately, this can help prevent problems like privilege creep and unauthorized access before they can cause harm.
Additionally, Veza improves user access reviews by providing detailed insights into user permissions. Traditional IGA tools often result in the recertification of most user access, even though a small percentage of permissions are actually used. With Veza, managers can review and approve or deny specific actions users can perform on resources, so only necessary permissions are granted, and rejected permissions are removed promptly.
Veza can also automate access review outcomes so you can truly understand who can and should have access to what apps and data in your organization. You can even continuously monitor who has access to your data Crown Jewels to find and eliminate excess privilege for all your identities across all your environments and to conduct faster and more effective access reviews and certifications. Veza also streamlines audit reporting with audit-ready access reports that demonstrate compliance with SOX, ISO 27001, SOC 2, GDPR, and more.
Deploying Veza is easy, and it delivers immediate value in visibility and remediation without long implementation cycles or extensive professional services. As a cloud-native SaaS platform, Veza is designed for scalability and security. The platform’s API-first approach and out-of-band deployment ensure minimal administrative overhead and no risk of downtime. It also integrates with tools like ServiceNow and JIRA to remediate dormant, excessive, or policy-violating permissions.
Veza empowers managers and supervisors to make access decisions based on effective permissions and helps IAM teams streamline end-to-end access reviews from certification to renewal in a unified workflow. This helps delegate decisions to line-of-business managers and remove excessive or dormant permissions during certification. It also prioritizes reviews of privileged accounts and automates evidence collection for ongoing audits.
With Veza, governance, risk, and compliance (GRC) teams can define and enforce separation of duties policies, validate entitlements for sensitive resources, and create governance workflows to comply with regulations. Veza also follows industry best practices, including penetration testing, data encryption, strict role-based access controls, and complete tenant isolation. It is SOC 2 Type II and ISO 27001 certified, underscoring its commitment to security and compliance.
Features
Here are some key features of Veza:
- Identity Governance: Provides comprehensive management of user identities and access rights, ensuring adherence to internal policies and regulatory requirements.
- Access Request Management: Streamlines the process of requesting, approving, and provisioning access to applications and data, enhancing operational efficiency.
- Automated Access Reviews: Simplifies the access review process with automation, reducing manual effort and ensuring continuous compliance.
- Real-Time Monitoring: Offers real-time visibility into access patterns and potential security risks, enabling prompt response to threats.
- Effective Permissions Management: Analyzes and manages effective permissions to ensure that users have appropriate access, reducing the risk of over-privileged accounts.
- AI-Driven Automation: Uses artificial intelligence to provide intelligent recommendations and automate identity-related tasks, improving decision-making and efficiency.
- Cloud-Native Architecture: Designed for the cloud, Veza provides scalability and flexibility without the need for extensive on-premises infrastructure.
- Integration with 200+ Systems: Supports a wide range of integrations with on-premises, cloud services SaaS applications, and data lakes, ensuring comprehensive coverage.
- Zero Trust Implementation: Facilitates the adoption of Zero Trust security principles by continuously verifying user identities and access privileges.
- Privileged Access Monitoring: Secures and manages privileged accounts, preventing unauthorized access to critical systems and data.
- Access Intelligence: : Detects privileged users, dormant permissions, policy violations, and misconfigurations to help ensure only authorized users can access critical information.
- Third-Party Access Governance: Provides visibility and control over vendor and contractor access, mitigating risks associated with third-party access.
- Control Exchange for Compliance: Offers a repository of controls mapped to various regulations and standards, simplifying compliance management.
- Quick Deployment Time: Delivers immediate value with rapid deployment, avoiding the lengthy implementation times common with traditional solutions.
- Open Authorization API: Allows for quick custom integrations with proprietary applications, providing flexibility and extensibility.
Pros
Here’s a closer look at some of the benefits of using Veza:
- Rapid deployment with immediate value delivery.
- Extensive integration options with over 200 systems.
- Comprehensive real-time monitoring and automated access reviews.
- Effective permissions management improves security.
- Cloud-native architecture reduces administrative overhead.
- Strong focus on continuous compliance and Zero Trust implementation.
Cons
Here are some of the potential drawbacks of using Veza:
- Relatively new in the market.
- May require customization for specific use cases.
SailPoint
The platform automates the process of adjusting user access, allowing security teams to focus on high-value initiatives. With Access Recommendations, business managers and application owners can make informed decisions, reducing certification fatigue and improving productivity. SailPoint uses workflows to automate identity security programs, aligning with the pace of modern business.
SailPoint ensures that only the right people have the right access by automatically removing access when an employee leaves the organization. The Request Center streamlines access requests, enhancing efficiency for managers and employees. Additionally, SailPoint’s Access Risk Management identifies Separation of Duties (SoD) conflicts and sensitive access risks across systems like SAP. The platform leverages actionable insights to proactively discover identity outliers and initiate timely access adjustments.
SailPoint’s Non-Employee Risk Management secures access control for managing third-party non-employee identities.
SailPoint supports specific industry needs, such as healthcare, by streamlining access requests and managing third-party identities in compliance with sector regulations. Its AI-driven security features provide autonomous governance, ensuring the right identities have the right access to the right data at the right time.
Features
Here are some of the features of SailPoint:
- Identity Governance: Provides tools for managing user identities and access rights to support compliance with internal policies and regulatory requirements.
- Access Request Management: Streamlines access request processes, allowing users to request, approve, and provision access.
- AI-Driven Automation: Leverages artificial intelligence to automate identity-related tasks and provide intelligent recommendations for access decisions.
- Cloud-Native Architecture: Supports cloud-based deployment.
- Privileged Access Management (PAM): Manages and secures privileged accounts, protecting critical systems and data from unauthorized access.
- Data Access Governance (DAG): Extends governance capabilities to files and data stored on-premises and in the cloud.
- Access Modeling: Uses AI to analyze and model access patterns.
- Access Insights: Provides valuable insights into identity data.
- Recommendation Engine: Offers intelligent suggestions for access requests and approvals.
Pros
Here are some of the benefits that come with SailPoint:
- Comprehensive identity governance capabilities.
- Strong AI-driven automation for enhanced decision-making.
- Flexible deployment options for on-premises, cloud, and hybrid environments.
- Proven track record with an established customer base.
- Extensive feature set supporting various aspects of identity management.
Cons
Here are some of the drawbacks to consider when using SailPoint:
- Cannot detect local accounts, leaving potential security gaps if IdP accounts are disabled.
- Often requires lengthy deployment and complex integration processes.
- Has limited capabilities for real-time monitoring and automated access reviews.
- Managing updates and compliance activities can be resource-intensive and costly.
- Requires a higher initial investment and extensive customization.
- Less suited for today’s SaaS and off-premise tools, making integration challenging without major restructuring.
Saviynt
Saviynt offers features designed to improve security and compliance across various environments. It implements Zero Trust strategies by continuously verifying user identities and access privileges. It also offers Application Access Governance (AAG) to manage the identity lifecycle across major SaaS applications and infrastructures like SAP, Oracle, Workday, Azure, AWS, and Google Cloud Platform (GCP).
The platform also includes Data Access Governance (DAG) so organizations can create data access policies based on data sensitivity, ensuring only authorized users can access critical information. Saviynt’s Cloud Privileged Access Management (PAM) integrates with DevOps tools to secure the CI/CD pipeline, mitigating risks associated with privileged user access in development and production environments.
Saviynt’s Third Party Access Governance (TPAG) provides visibility into vendor access risks, allowing organizations to manage and secure third-party access. The platform also features a Control Exchange for out-of-the-box controls mapped to various regulations and industry standards.
Features
Here’s a close look at Saviynt’s features:
- Identity Governance: Manages user identities and access rights to ensure compliance with policies and regulatory requirements.
- Access Request Management: Streamlines processes for requesting, approving, and provisioning access to various applications and data.
- Automated Access Reviews: Automates the access review process.
- Real-Time Monitoring: Provides real-time visibility into user access and activities.
- AI-Driven Automation: Uses artificial intelligence to automate identity governance processes and manage users.
- Cloud-Native Architecture: Built for the cloud without extensive on-premise infrastructure.
- Zero Trust Implementation: Continuously verifies user identities and access privileges.
- Privileged Access Management (PAM): Manages and secures privileged accounts.
- Data Access Governance (DAG): Creates data access policies based on sensitivity.
- Third-Party Access Governance: Manages vendor and contractor access.
- Control Exchange for Compliance: Provides a repository of controls mapped to various regulations and standards.
- Application Access Governance (AAG): Manages the identity lifecycle across major SaaS applications and infrastructures such as SAP, Oracle, Workday, Azure, AWS, and Google Cloud Platform.
- Saviynt Enterprise Identity Cloud: A cloud-native IGA platform that supports comprehensive identity governance and administration across diverse environments.
- Continuous Monitoring and Remediation: Monitors compliance and automatically remediates identity-related issues.
Pros
Here are some of the benefits of using Saviynt:
- Zero Trust implementation and compliance controls.
- Integrations with major SaaS applications and cloud platforms.
- Monitoring and remediation of compliance activities.
- Cloud-native architecture offers scalability and flexibility.
Cons
Here are some of the drawbacks of using Saviynt:
- Primarily integrates with IdPs like Okta, leaving it unable to detect local accounts.
- Often requires a complex implementation process with longer deployment times.
- May necessitate extensive customization and professional services.
- Generally involves a higher initial investment compared to other solutions.
- Integration with existing systems can be challenging and time-consuming.
The Bottom Line on SailPoint vs Saviynt vs Veza
While SailPoint and Saviynt offer features of managing identities and ensuring compliance, they rely on traditional IGA models that may struggle with the dynamic needs of today’s hybrid and multi-cloud environments.
Veza stands out as the superior choice with its next-generation approach to identity governance. Unlike traditional IGA tools, Veza leverages authorization metadata to provide a comprehensive and accurate picture of access permissions across all systems.
This allows for real-time monitoring, automated access reviews, and proactive security measures that eliminate blind spots and reduce risk. Veza’s rapid deployment and extensive integration capabilities make it an efficient and scalable solution for modern enterprises.
Explore how Veza can transform your identity security strategy.





