
Identity security isn’t just about provisioning and deprovisioning users anymore. It’s about governance at scale, enforcement access across sprawl, and identity visibility everywhere – especially in an era where your systems span SaaS, IaaS, on-premises, legacy, shadow IT, AI Apps, AI AGents, and homegrown apps, all duct-taped together over the past two decades.
Veza’s answer? 300+ permission-aware integrations, plus the tooling to build your own.
Let’s talk about what makes this different and why it matters to real-world IT and security teams trying to stay compliant, reduce identity risk, and enforce least privilege across the board.
Integration Without Limits
Veza ships native, read-only integrations across virtually every layer of the modern stack:
- Cloud Platforms: AWS, GCP, Azure
- Data & Infra: Snowflake, Databricks, Kubernetes, Oracle DB
- SaaS Systems: Workday, Salesforce, GitHub, ServiceNow, Zendesk
- Identity Sources: Entra ID, AD, LDAP, Ping, Okta, Duo
- Storage & Collaboration: Google Drive, Box, Confluence, SharePoint
- Custom & Legacy Systems: Anything that talks API, database, or flat files
- AI Infrastructure: Veza for Open.AI, Veza for Azure Open.AI
The point isn’t just breadth, it’s permission-aware depth for these integrations – as least privilege is rooted in permissions and entitlements, not users and groups. Veza doesn’t just grab user lists. It ingests full privilege models across these integrations: group memberships, policies, object-level permissions, access tokens, federated identity mappings, roles, scopes, you name it.
That’s what powers the Access Graph and enables near real-time answers to questions like:
- “Who can make changes to production data in Snowflake and also push code to GitHub?”
- “Which contractor accounts have admin privileges in Oracle EBS?”
- “Are there SoD violations between our SAP finance users and NetSuite roles?”
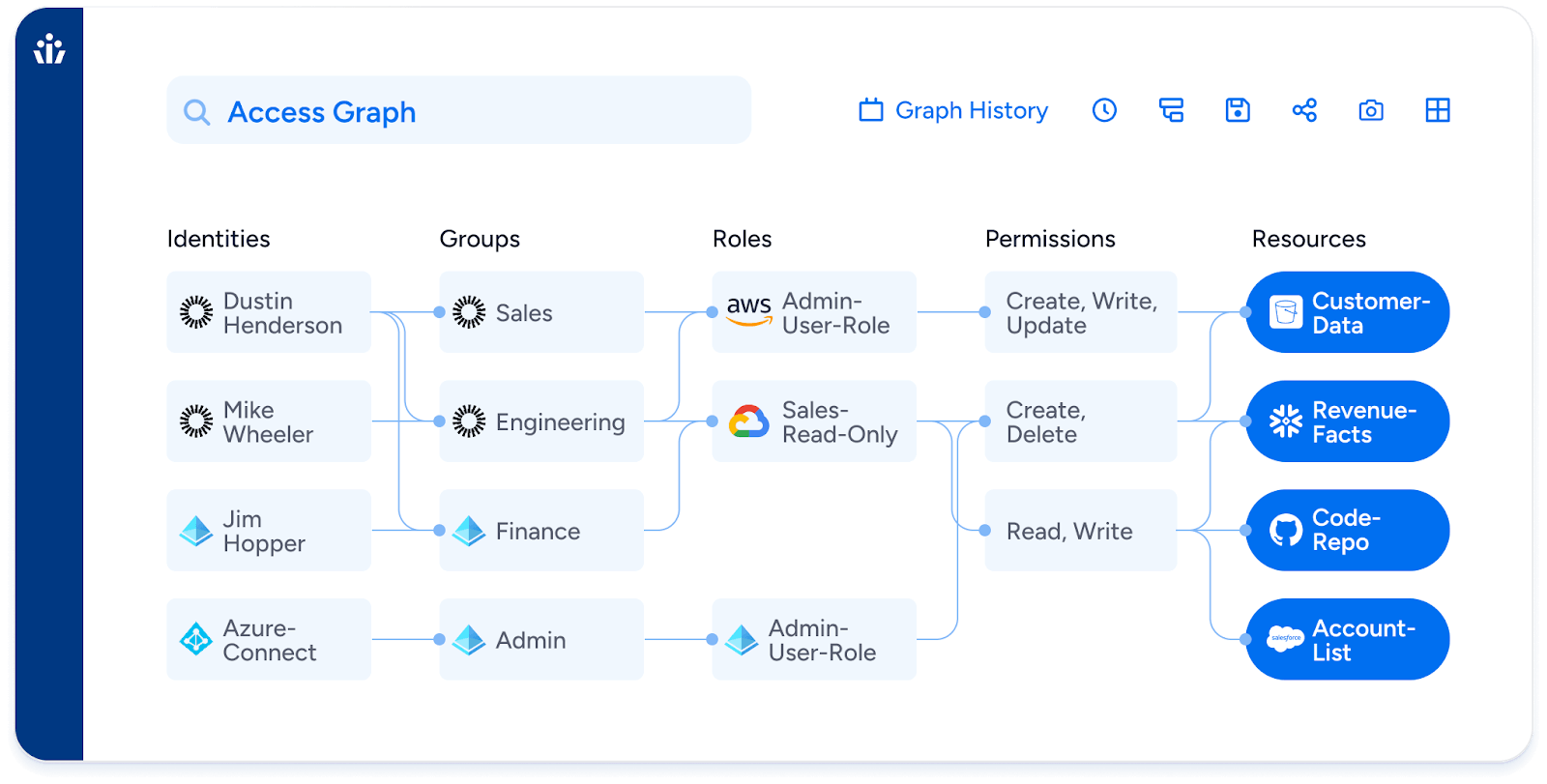
That’s real identity security posture management (ISPM). And it lays the foundation for what Gartner’s now calling IVIP – the Identity Visibility and Intelligence Platform.
But here’s where it gets really interesting.
OAA: Your Easy Button for Low-Code and No-Code Integrations
Every org has that system. The homegrown ERP from 2008. The custom claims-processing portal was built in ColdFusion. The departmental app that a vendor wrote years ago but never documented.
These are the gaps where most identity tools wave the white flag.
But with Veza, we hand you a wrench and say: Let’s build it.
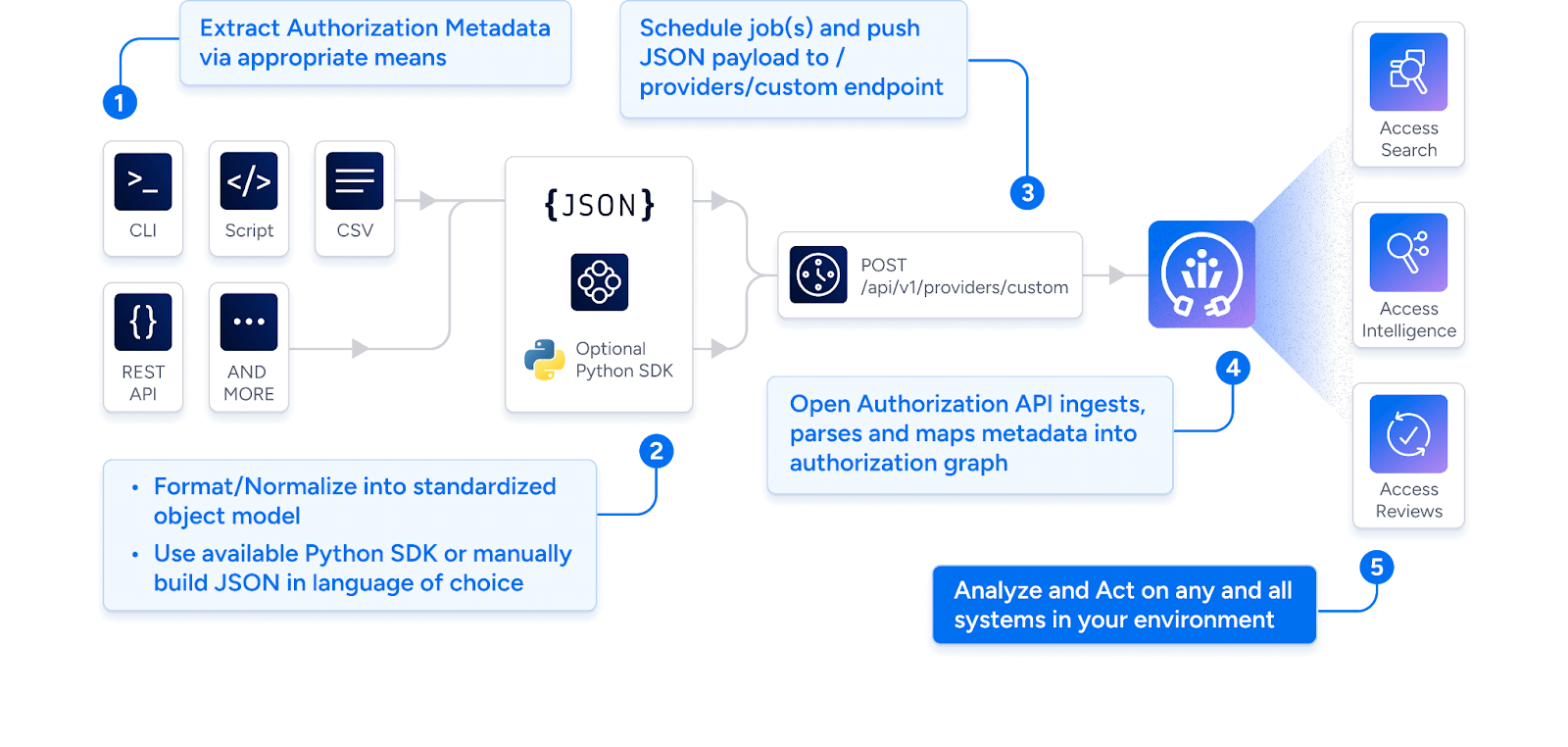
Enter the Open Authorization API (OAA)—a secure, developer-friendly integration framework that lets you bring any system into Veza’s access graph, on your terms.
What OAA Provides
- Schema-driven integration: Define objects, users, roles, and entitlements via simple JSON
- RESTful data ingestion: Post your system’s identity + permission data via HTTPS
- AuthZ-first thinking: Focus on what a subject can do, not just who they are
- Language-agnostic SDKs: Build in Python, .NET, Go, whatever your teams already use
- Scalable & secure: OAuth2-based access, scoped secrets, and audit trails
Or Just Upload a CSV – No Integration Required
Not every team has time to build an integration, and with Veza, they don’t have to. For organizations that just need to get data in quickly, Veza’s revamped CSV uploader provides a simple alternative. Directly from the UI, customers can upload existing CSV exports (from legacy systems, HRIS, or homegrown apps) and define how Veza should interpret and map the data.
No code. No APIs. Just upload and go.
Why Extensibility Is a Big Deal
Most identity vendors sell you a box of pre-built connectors, and if they don’t support granular permissions and entitlements, those integrations are just shallow!
Veza Integrations go all the way – users → groups → roles → policies/permissions → resources.
1. Future-Proof Your Stack
Adding a new app? Customizing a legacy one? OAA lets you bring it online without waiting for vendor roadmap cycles. You can plug anything into the platform within hours, not quarters.
2. Break the “Black Box” Model
OAA gives you full visibility into what’s integrated and how. You control how identities and permissions are modeled and ingested. That’s critical for industries with bespoke systems—like healthcare, defense, or manufacturing—where no off-the-shelf IGA tool ever fits right.
3. Community-Powered Integrations
Here’s the kicker: over 40% of Veza’s integrations are now built by customers and partners. That means the ecosystem isn’t just growing—it’s compounding. You benefit from what others have built, and contribute back if you want to.
That’s not just extensibility. That’s the network effect for identity security.
Supporting the IVIP & ISPM Models
When Gartner introduced the Identity Visibility and Intelligence Platform (IVIP) model, it validated what Veza had already built:
- A real-time access graph across all systems
- Machine-readable access context with policy, permission, and privilege details
- Extensible ingestion that covers the full surface, without waiting for vendor hand-holding
And for ISPM, this is mission-critical. Veza provides the “how” to implement posture management policies, enforce least privilege, monitor privileged activity, and track dormant or toxic access conditions at scale, across all your systems, not just the easy ones.
This is why Veza doesn’t just help you check the compliance box; it helps you operationalize it.
Example: Bringing a Custom Claims App into Veza
Let’s say you’ve got a healthcare claims management portal built in Java. It manages PHI, handles provider reimbursements, and runs in your private cloud.
Traditionally, you’d be stuck with:
- Custom scripts to pull logs
- Manual user list exports
- No visibility into object-level access
With Veza + OAA, you can:
- Define the access schema: users, claims, privileges (e.g. read, write, approve)
- Build a lightweight REST adapter to export your access model in JSON
- Authenticate securely with Veza using scoped tokens
- Post data directly into the platform on a scheduled basis
- Immediately surface risks, stale access, and SoD violations
And now this mission-critical app becomes fully integrated into your certifications, risk dashboards, and audit workflows – no replatforming required.
Final Word: Why This Matters for App Onboarding
Modern identity governance isn’t about rigid platforms or brittle integrations. It’s about open, extensible, permission-aware access intelligence that spans your real-world environment—warts and all.
With 300+ integrations and a developer-friendly Open Authorization API (OAA), Veza meets you where you are, takes app onboarding 10x speed, brings everything into one place, and empowers you to build forward—without compromise.
That’s what makes Veza different. And it’s why security teams, auditors, and IT pros alike are using Veza not just as a tool, but as their identity backbone.
Explore the catalog: https://veza.com/integrations
Start building with OAA: https://developer.veza.com





