Veza for GitHub
Your source code is probably some of the most sensitive data your organization holds. It’s not only the cornerstone of your intellectual property, but also a potential launching pad for supply chain attacks, especially with the rise of Infrastructure-as-Code. Veza definitively answers the question : Who can take what action on source code in GitHub?
Identity security challenges in GitHub
Four key source code risk factors
In addition to being valuable IP in itself, source code in GitHub or other version control systems is a uniquely valuable tool for attackers and a compromised repository can be a springboard for further attacks.

Exposure of auth secrets
Source code frequently contains authentication secrets used by machine identities that can be leveraged by a hacker to access other systems.

Attack path analysis
If an attacker can download and analyze your source code they can find and exploit vulnerabilities and back doors in your system.

Supply chain attacks
Storage of packages in GitHub repositories, combined with wide adoption of open-source gives attackers a way to inject malicious code into your source.

Infrastructure-as-Code (IaC)
The blueprint of your production environment itself may be stored in a GitHub repository, making GitHub central to your operational security.
How Veza can help
Veza is powered by its Authorization Graph, which gives organizations the ability to visualize authorization relationships between all identities and systems by connecting users, groups, roles, and permissions.
- Reduced Risk: Surface and prioritize identities with the greatest levels of access to source code in GitHub repositories.
- Monitor external users: Compare GitHub users back to your identity provider to easily identify and manage external contributors and make sure access is limited to public repositories.
- Least Privilege: Automatically detect inappropriate access, including new privileged users on critical repositories like your production codebase or IaC repo.
- Team Efficiency: Use Veza to delegate access decisions and reviews to business managers who best understand each repository.
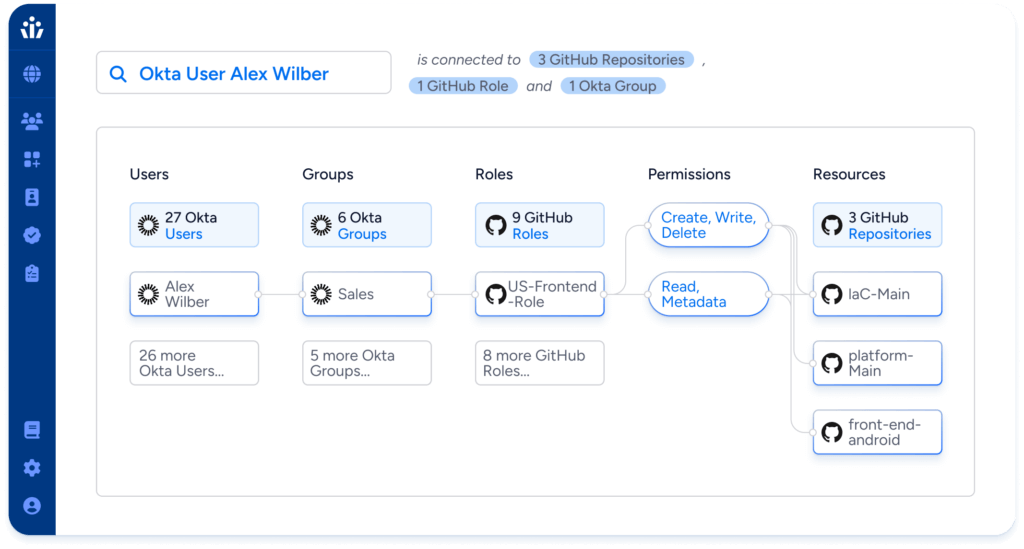
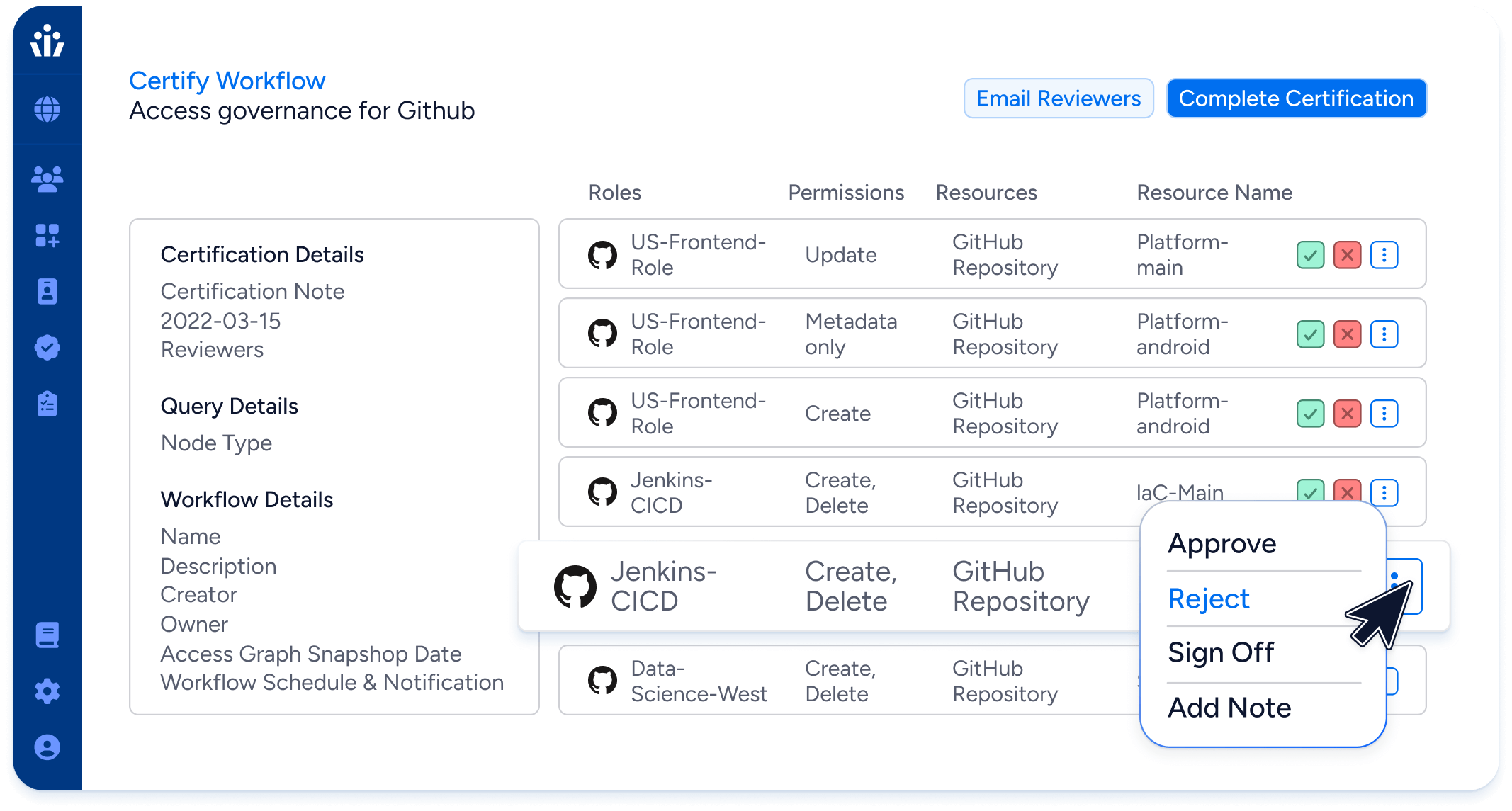
- Effective permissions: Translate GitHub RBAC permissions into simple, human-readable language—”create, read, update, delete”.
- Automated monitoring: Watch continuously for policy violations and new privileged accounts, so you can comply with internal controls and external regulations without burdening security and governance teams.
- Activity monitoring: Identify roles and users in GitHub with unused privileges to remove dormant identities, right-size access, and cut unused permissions.
- Agentless read-only connections to both GitHub and your identity providers, give a complete picture of the access granted to federated identities, revealing governance blindspots, like local and external users.


“To secure our customers’ data and stay compliant with global regulations, it’s critical to maintain the integrity and confidentiality of our source code. Veza enables us to monitor and enforce our access policies across GitHub and other data systems, allowing us to manage role-based access control at scale. With Veza, we can understand the combined effect of our access control layers to maintain least privilege.“
Frank Dellé | Head of Global Compliance