
According to The IBM X-Force Threat Intelligence Index 2024, there was a 71% increase year over year in the volume of attacks using valid credentials. For the first time in history, abusing valid accounts has become the most common entry point for cybercriminals into victim environments.
Privileged access management (PAM) software addresses this risk by restricting access to critical systems and sensitive data. Additionally, PAM software monitors and logs all privileged activities, enabling organizations to detect and respond swiftly to unauthorized actions or suspicious behavior.
In this article, you’ll discover how PAM software functions and explore the top PAM software to safeguard your organization from both internal and external threats.
What is Privileged Access?
According to the National Institute of Standards and Technology, privileged access refers to a user who is authorized and trusted to perform functions that ordinary users are not authorized to perform. Basically, privileged access is special access or permissions beyond that of a standard/non-privileged user.
In organizations, these permissions are typically given to senior managers, system administrators, and IT personnel, authorizing them to bypass and override certain security restraints and perform high-level tasks like installing new software or configuring business systems.
What is Privileged Access Management?
Privileged access management is an identity security solution designed to control and monitor users with special or elevated access to critical parts of computer systems or networks. These users, known as “privileged users,” can access sensitive information, change system settings, and perform critical tasks. They include administrators, SSH keys, and service accounts that are essential for keeping an organization running smoothly.
The main goal of privileged access management is to:
- Prevent unauthorized access to critical systems and data
- Ensure compliance with security regulations
- Protect against privileged credential theft
- Control and monitor third-party access
- Secure remote access to sensitive resources
However, while PAM tools can be highly useful, they have a significant limitation: they’re often blind to most identities and their permissions. Simply put, most PAM tools cannot see the complete picture of permissions across all applications and systems.
To address this, organizations need software that can analyze authorization data from every system to gain a complete picture of access privileges.
What are Privileged Access Management software tools?
Privileged access management software tools restrict access to critical systems and sensitive data, ensuring that only authorized users with verified credentials can gain access. PAM software monitors and logs all privileged activities so organizations can quickly detect and respond to unauthorized attempts or suspicious behavior.
Additionally, PAM software tools allow you to:
- Identify and govern privilege accounts across multiple applications and systems
- Control shared and emergency access to privileged accounts
- Control and filter privileged users’ actions, tasks, and commands
- Provide single sign-on to privileged account users to prevent credential theft
- Randomize and vault credentials like passwords and encryption keys
PAM software can also be classified into five categories which include; privileged account and session management (PASM, privilege elevation and delegation management (PEDM), remote privilege access management (RAPM), secrets management, and cloud infrastructure entitlement management (CIEM).
Let’s examine PAM further to better understand its role in securing an organization’s digital assets.
How does Privileged Access Management (PAM) software work?
Regardless of their specific function or category, there’s a standard process to the way privileged access management software works. Here’s how:
- Authorization and authentication: PAM software uses robust authorization and authentication mechanisms to verify the identity of users trying to use a privileged account. When a user is authenticated, the software authorizes what they have access to based on predefined security policies
- Secure password management: With PAM software, your organization can automate managing privileged account passwords. The software enforces strong-complex password policies, rotates passwords at intervals, and securely stores passwords to mitigate unauthorized access through compromised account credentials.
- Session monitoring and recording: PAM software gives visibility into privileged users’ sessions by monitoring and recording activities in real-time. This enables organizations to maintain an audit trail and quickly detect any anomalous activity.
- Least privilege and access controls: To reduce insider threats, attack surfaces, and the impact of possible security breaches, PAM uses access control to enforce the principle of least privilege
- Alerts and reports: In many organizations, an average of 99 days passes between a security breach and detection. PAM software shortens detection time by automatically generating alerts for suspicious activity and reports on privileged account sessions. Organizations can detect threats in real-time, respond quickly, and maintain compliance reports.
Privileged access management is essential for securing critical systems and sensitive data. However, while most PAM tools are effective in monitoring and controlling access to privileged accounts, their usefulness depends on first identifying all privileged accounts, not just those designated as such by design. Therefore, organizations need a software that can identify all privileged accounts.
Best Privileged Access Management software solutions
Now that you know how PAM software works, let’s look at the best privileged access management software for your organization:
1. Veza

Veza is the Identity Security company that’s transforming the way businesses manage access control and permissions for digital identities, helping organizations secure access across the enterprise, including cloud infrastructure, data systems, SaaS apps, and on-prem apps. It goes beyond the limitations of traditional PAM tools by capturing access metadata from all enterprise systems.
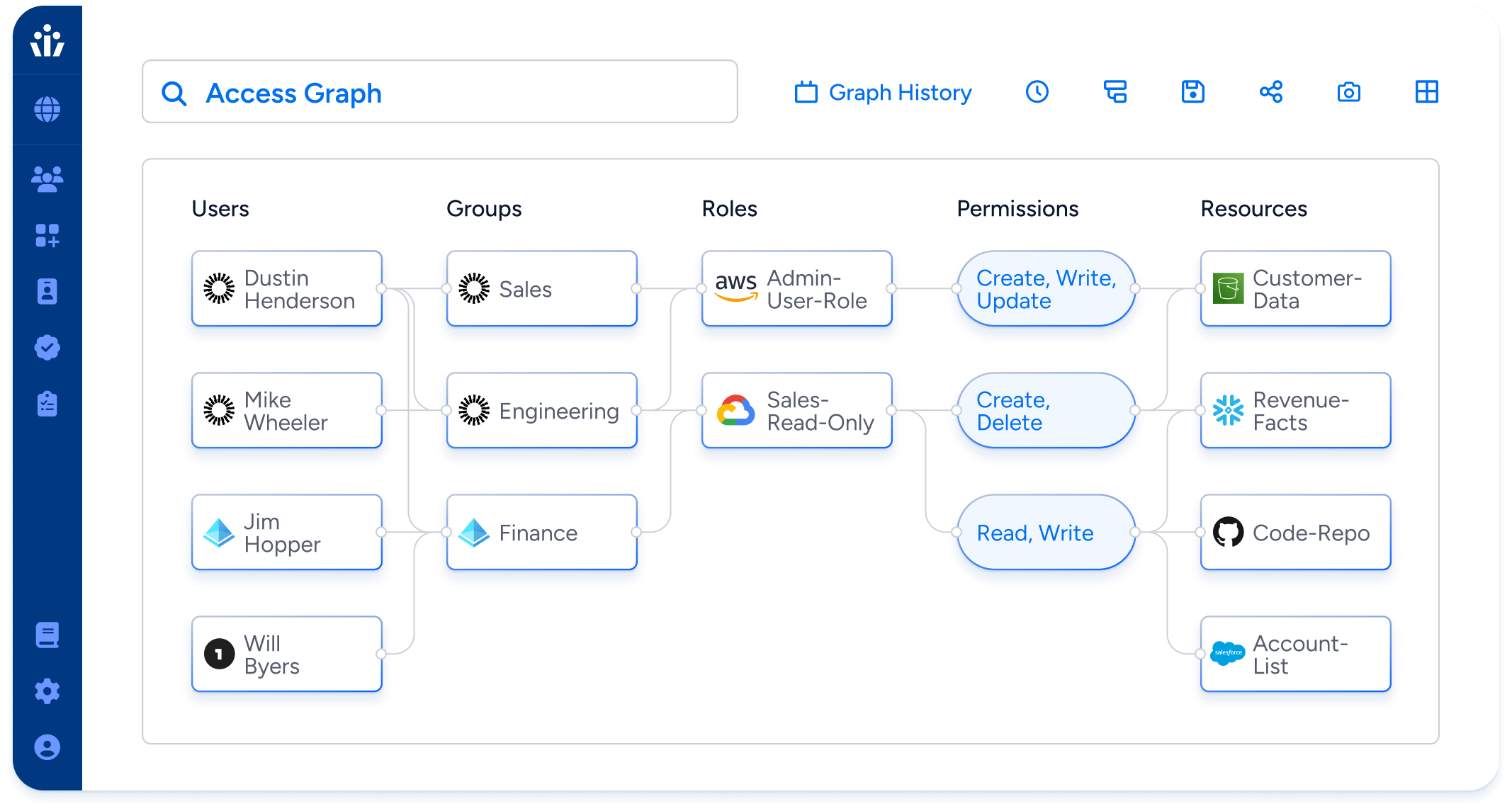
It helps you visualize the data using a unique, interactive graph that helps you answer the million-dollar question: Who can take what action on what data?
Veza’s Access Graph ensures secure access across your systems environment for both human and non-human identities (NHIs) through:
- Comprehensive connectivity: Easy connection to any business system for a comprehensive overview of access.
- Comprehensive identity monitoring: Keep tabs on all identities, including human and non-human identities (NHIs), giving you a complete picture of access.
- Precise permission control: Dive deeper than user groups & roles to understand fine-grained permissions to apps and resources.
- Simplified context: Translate complex permissions into clear business terms like create, read, update, delete.
- Streamlined automation: Automatically monitor and resolve access issues and boost productivity.
Veza provides a REST API for users to integrate Veza with their existing tools to automate processes, support existing workflows, integrate with ticketing systems, and provide data enrichment for other solutions. It also offers 275+ integrations with other solutions, such as AWS, Google Cloud, Microsoft Azure, Snowflake, and Okta.
Key Features:
- Access Search: Visualize and control access to data across all your enterprise systems
- Access Intelligence: Detect privileged users, dormant permissions, misconfigurations, and policy violations with up to 500+ pre-built queries
- Activity Monitoring: Monitor who can access and who has access to your key business resources to identify unnecessary permissions, remove dormant entities and right-size roles, and trim unneeded entitlements
- Lifecycle Management: Automatically grant and revoke access when a user leaves or changes role to prevent access mistakes and policy violations
- Access Reviews: Automate user access certifications, creating comprehensive campaigns in record time
Cons?
Veza has a 4.9 out of 5 rating on Gartner and a 5 out of 5 rating on Capterra and Software Advice, with no drawbacks. Users are generally happy with the platform, highlighting how Veza renders support to them in record time and always implements user feedback.
Enterprises across all industries require a centralized way to manage access across disparate systems and all types of identities.
That’s finally possible with Veza.
2. CyberArk

CyberArk is an identity security solution that runs on Cora AI, an AI-powered identity security intelligence tool. Its PAM platform provides least privileged security control and an identity-oriented audit and compliance solution. It also enables users to monitor and isolate privileged sessions and remediate risky activities.
CyberArk operates on Windows and Mac desktops and Windows servers and provides remote access to IT assets without VPN or passwords. It offers an API for developers to integrate into their platform’s security and also integrates with tools like AWS, Sailpoint, and Azure.
Key Features & Benefits:
- Adaptive multi-factor authentication and single sign-on
- Automated password rotation
- Endpoint privilege security
- Identity governance and administration
Cons?
CyberArk users experience several challenges using the platform. Here are some key challenges based on user reviews on G2:
- Poor password rotation compared to other tools
- Does not provide in-depth activity reports
- Clunky UI, which makes the platform difficult to navigate
3. Delinea

Delinea offers centralized authorization intelligence for cybersecurity, DevOps, and IT management teams. Its PAM platform provides privileged remote access, privilege control for cloud entitlements, privilege control for servers, and privilege behavior analytics.
Delinea offers enterprise-scale cloud endpoint privilege management, which enables users to enforce least privilege rights on endpoints and remove local administrative rights. It has a mobile app and an open API and integrates with ActiveDirectory, ServiceNow, Secret Server, and Virus Total.
Key Features:
- Privilege control for servers
- Privilege behavior analytics
- Identity threat protection
- User Access Control (UAC) override
Cons?
Based on G2 reviews, some issues you might experience with Delinea include:
- Difficult to reduce assets from the Cloud Console
- Poor training and user onboarding
- It has a high learning curve
4. Arcon

Arcon is a converged identity platform for global enterprises. It is built for businesses in telecom, government, financial, utilities, and healthcare industries. It also ensures compliance with regulations like GDPR, HIPAA, and PCI DSS.
Arcon’s PAM platform offers granular access control of digital identities in an organization’s IT infrastructure. It offers threat analytics, zero-trust authentication, and credential management. It enables users to maintain centralized security by integrating with databases, file transfer, web browsers, and DevOps platforms.
Key Features & Benefits:
- Multi-factor authentication
- Credential management
- Single sign-on
- Access control
Cons?
Key issues Arcon reviewers on G2 highlight about the software are:
- Poor user interface
- It is expensive
- Implementing the platform is tough
5. BeyondTrust

BeyondTrust is built for businesses to manage, visualize, and protect paths to privileged access accounts. It is an identity security tool for users to find blindspots and critical risk exposure points in their security posture. It offers AI-powered identity threat detection and response.
BeyondTrust offers a free identity risk assessment and privilege discovery tool. It also provides cloud security for multi-cloud IT environments and integrates with cloud platforms like AWS, Ping Identity, and ServiceNow.
Key Features & Benefits:
- Identity threat detection and response
- Endpoint security
- Secure remote access management
- Workforce passwords
Cons?
BeyondTrust users experience several challenges using the platform. Here are some key ones, based on user reviews on Gartner:
- The usability of its API is restricted
- The web version is unstable
- Initial setup and onboarding can be difficult for non-technical users
6. Iraje Privileged Access Manager

Iraje is a privileged access manager for enterprises to control, manage, and monitor privileged access. It is a browser—and desktop-neutral platform built to run on any browser and can be accessed on Windows, LINUX, and MAC desktops. It works through zero-trust security, fail-safe architecture, an application server, and a vault server.
Iraje also offers certification courses on PAM for users to learn how to troubleshoot and maintain the platform. It offers other services like independent audits, training, and implementation of external security systems.
Key Features & Benefits:
- Multi-factor authentication
- Live session viewing and termination
- PAM bypass alerts
- Compliance reports
Cons?
Iraje PAM reviews on Gartner highlight some key issues with using the platform, such as:
- Complex GUI
- It is expensive compared to other platforms
- Does not allow passwords to be changed to URLs
7. One Identity

One Identity offers SaaS-delivered and on-prem privileged access management for organizations to secure, analyze, and govern PAM tools across multiple platforms or IT environments. It provides on-demand, remote PAM with privileged analytics, password vaulting, and session management.
One Identity has an open API and also integrates with cloud infrastructure like AWS and Azure, access management tools like Okta, data tools like Dropbox, and other enterprise solutions like finance and ERP platforms.
Key Features & Benefits:
- Identity governance
- Privilege identity management
- Privilege account analytics
- Centralized identity management
Cons?
According to reviews on G2, major issues with One Identity include:
- Poor active directory management
- High learning curve
- The product documentation is not detailed
8. ManageEngine

ManageEngine is an enterprise PAM tool for developers, compliance and audit, and cyber insurance readiness teams. It offers cloud infrastructure entitlement management, identity threat detections and readiness, and zero trust privileged access management. It also offers least privileged workflows for access provisioning.
ManageEngine also supports remote security posturing with its remote access function, which enables users to launch direct connections to remote hosts without browser plug-ins. It provides a developer platform for users to build custom integrations through APIs and SDKs.
Key Features & Benefits:
- Privileged account and session management
- Enterprise password manager
- Privilege account governance
- Privilege user behavior analytics
Cons?
ManageEngine users experience several challenges using the platform. Here are some key ones, based on user reviews on G2:
- The platform has a high learning curve
- It has a lot of features that are overwhelming to use
- High cost of customization
9. StrongDM

StrongDM offers continuous zero-trust authorization and privileged access for security, developer, and IAM teams. It offers a cedar-based policy engine for users to create and implement fine-grained access controls. The platform also provides a dashboard for visibility and transparency across IT infrastructure.
StrongDM supports no-code integration with the existing tech stack and integrates with platforms like Slack, Cyberark Vault, Okta, and AWS Keystore Vault. It also has product documentation and an API for custom integrations.
Key Features & Benefits:
- Privilege session management
- Permissions management
- Vendor privilege access
- Zero trust PAM
Cons?
StrongDM user reviews on G2 highlight a number of issues, the major ones being:
- Audit logging issues
- Initial setup and implementation is time-consuming
- Documentation is not up to date sometimes
10. Teleport

Teleport is an on-demand, least-privilege solution that offers cryptographic identity, zero-trust access, secretless authentication, and built-in identity governance. It is specifically designed for businesses in e-commerce and entertainment, financial services, and SaaS providers.
Teleport provides compliance with FedRAMP, SOC 2, and HIPAA. It is also strategically partnered with Amazon Web Services (AWS) to enable businesses to control access to critical AWS resources. Teleport integrates with other security solutions like databases, Devtools, data services, and secret vaults.
Key Features & Benefits:
- Passwordless authentication
- Identity governance for CI/CD automation systems
- Cryptographic identity for applications, servers, and databases
- Single sign-on
Cons?
Reviews on G2 say that Teleport has the following issues:
- Poor product documentation
- It is difficult to add new database types
- High learning curve
Benefits of Privileged Access Management
Implementing a PAM process and deploying privileged access management software in your organization will help you maintain a robust cybersecurity position. Three major benefits of PAM are:
Reduced insider threats and attack surfaces
Privileged accounts are more likely to be targeted by internal employees and ex-employees trying to steal critical corporate assets. IBM reports that 60% of data breaches are caused by insider threats.
Privileged access management lets companies set up an effective monitoring system with established rules and time limits for privileged access users so that security administrators can quickly identify internal suspicious activity. It also condenses attack surfaces by storing privilege credentials in a separate, secure, and centralized repository to reduce the risk of credentials being stolen by external hackers.
Improved compliance
Many industries enforce strict regulations for handling sensitive information and controlling system access. For instance, GDPR’s Article 29 mandates that data processors access only the data necessary for their specific tasks, while ISO 27001 emphasizes the “need-to-use” principle in its annex on privileged access. Similarly, HIPAA restricts access to healthcare data based on user roles, and PCI-DSS limits access to the minimum data needed for job performance.
Privileged access management helps organizations meet these regulatory requirements by enforcing stringent security policies, such as the principle of least privilege, and maintaining comprehensive records of privileged user activities. This ensures that access to sensitive data is meticulously controlled and monitored, aiding organizations in achieving regulatory compliance and safeguarding their critical assets.
Stronger incident response
Every organization needs an incident response plan customized to its IT environment to reduce response time to incidents like data leaks, breaches, and theft, making it easier to remediate and recover from attacks. The best way to implement a response plan is through effective privilege access management.
Privileged access management tools offer real-time alerts and reports on any suspicious or anomalous activity so that organizations can detect incidents faster, trace the compromised account, and revoke access.
Features to look for in PAM solutions
The key features you need to look out for when choosing a PAM solution include:
- Access control: PAM software can provide robust access controls. This will ensure that privileged accounts have specific permissions tailored to their roles and responsibilities, help segregate roles, and reduce the risk of unauthorized access.
- Privilege sessions monitoring: For PAM to be effective, it needs to happen in real-time. Privileged access management solutions allow you to monitor privilege sessions on the go. You can track and audit user activities, detect issues, and respond promptly to security risks.
- Password management: A great part of PAM is enforcing strong passwords and password rotation to prevent unauthorized access. PAM software automates this process and securely stores credentials in a database.
- Auditing and reporting: For compliance, you must maintain audit trails and detailed log reports of privileged accounts activities. If you implement PAM software with this functionality, you won’t have to worry about compliance, as the software automatically generates compliant reports.
- Robust integration capabilities: Your PAM software must integrate seamlessly with your organization’s existing security tools and IT infrastructure. This enables you to build a connected ecosystem with centralized security measures across all applications, devices, systems, and servers.
- Workflow automation: The goal of PAM is to reduce or even eliminate manual intervention. You need PAM software that automates and streamlines privileged access workflows. This enables you to automatically manage and review access requests, approval, and removal across all privileged accounts.
Learn more about PAM tools and vendors
Here’s more information on PAM tools and vendors:
What are the different types of privileged accounts?
It is quite normal for some IT employees to have access to multiple accounts, sometimes logging in as a superuser to perform admin tasks or as a standard user to do routine tasks. This creates multiple privilege accounts in an organization, such as:
- Local administrative accounts: These are accounts that provide administrative access to the local host. IT staff use them to perform routine maintenance.
- Domain administrative accounts: Provides administrative access to all servers and workstations within the domain.
- Privileged user accounts: Provides administrative privileges on one or multiple systems on an organization’s network.
- Emergency accounts: Provides unprivileged users administrative access to secure systems in case of emergencies
- Service accounts: These are domain accounts or privileged local accounts that applications use to communicate with the operating system.
- Application accounts: Provides access to databases, other applications, or running batch jobs/scripts
- Domain service or active directory accounts: For enabling password changes to all accounts
What is PAM vs PIM?
Privileged access management enables organizations to manage privileged accounts and makes it hard for threat actors to steal privileged credentials. It provides fine-grained controls for you to monitor privileged users and see what their accounts are being used for.
Privileged identity management focuses on approval-based and time-based role activation to reduce the risk of unnecessary and excessive access to privileged accounts. It enforces just-in-time access, policies like multi-factor authentication, and just-enough access.
Basically, PAM is used to enforce the principle of least privilege, and PIM ensures time-bound access to privileged accounts.
What is PAM used for?
PAM is used for controlling and monitoring access to an organization’s resources through the concept of least privilege, which states that employees should be limited to just enough access to do their assigned tasks. In situations where a non-privileged user requires permission to a privileged account, PAM is also used to ensure that such access is given in a secure and auditable IT environment.
Which PAM tool is best?
While many PAM tools offer valuable features, Veza is a more intelligent access tool. Unlike traditional PAM tools that often struggle to identify all privileged accounts, Veza provides a comprehensive view of access across your entire organization.
With Veza, you get a clear view of who has access to what data and services so only the right people can see or use sensitive information, monitors any changes in access or permissions and alerts you if something happens that could risk your compliance status. Veza also helps you automate time-consuming and error-prone compliance activities, most notably your quarterly access reviews, giving you clear and audit-ready proof of compliance.
Veza is rated 5.0 stars on Capterra, and users praise Veza for its ease of use, customer service, robust integrations, and value for money.
How much does PAM software cost?
The cost of PAM software depends on the vendor you go for, but the cost is typically made up of an initial license fee and additional fees depending on your IT environment, security goals, and internal resources.
Choose the best PAM solution for your organization
Choosing the best PAM solution requires you to choose a more intelligent access tool that goes beyond traditional PAM solutions. The future needs Intelligent Access, where you can grant and revoke access permissions at the speed of business for all identities–across all systems–while enforcing security policies.
Veza’s Access Graph helps organizations can easily visualize who has access to what—including privileged access—and investigate identity threats quickly. You can automate access reviews for smarter access decisions and find and fix risky permissions and policy violations in just a few clicks. It secures access to data in virtually any system, whether on-premise or in the cloud, and it does so for all identities, whether human or machine.
Modern organizations use Veza to:
- Integrate quickly and easily with a cloud architecture, flexible deployment model, and modern developer experience
- Translate system-specific roles and permissions into plain language, understandable by business users
- Monitor all human and non-human identities, including local accounts, to get the most comprehensive view of permissions to granular resource
- Go deep, beyond relying on group or role names, into the permission metadata and Access Control Lists of systems to build the most accurate view of what identities truly can do
- Connect to any enterprise system: cloud infrastructure platforms, structured data systems, unstructured data systems, data lakes, SaaS apps, custom apps, or on-prem systems.
David Tyburski, the VP of information security and CISO at Wynn Resorts, says, “Veza is looking forward to us. It allows us to understand who, what, where, when, and why. If you can do that, you can secure any environment. And when you’re talking about a global organization, that’s what you need.”
Discover why global enterprises like Wynn Resorts, Expedia, and CrowdStrike trust Veza for privileged access monitoring and schedule a demo today.






