
Choosing the right identity security platform for your organization can be challenging—especially considering the significant rise in identity-related security incidents.
SailPoint, an identity security platform, offers identity security solutions for enterprises. However, a closer look at SailPoint reveals that it may not be a suitable choice in today’s complex and modern environment.
This article provides an in-depth review of SailPoint, including its features, pricing, and key product reviews. Additionally, we highlight some of the top alternatives to SailPoint so you can make an informed choice that best suits your organization’s requirements.
What is SailPoint?

SailPoint is an enterprise identity security solution that uses artificial intelligence and machine learning to automate access management. It aims to grant the appropriate level of access to the right identities at the right time. The SailPoint platform integrates with your existing systems and workflows, allowing organizations to view various identities and their access rights.
The company currently offers several products including:
- SailPoint Identity Security Cloud (formerly known as SailPoint IdentityNow): This solution manages and secures access to critical data and applications for enterprise identities.
- SailPoint IdentityIQ (IIQ): This solution provides lifecycle and compliance management for identity security, automating processes such as provisioning, access requests, access certification, and separation of duties.
SailPoint review
Here’s an overview of SailPoint, its pros and cons, pricing, and customer reviews.
What is SailPoint used for?
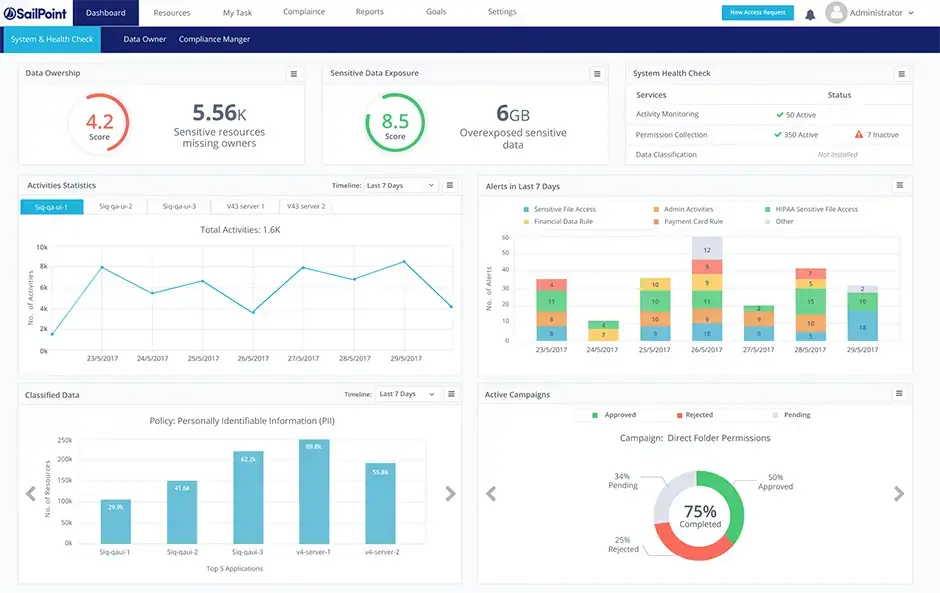
Here are the primary functionalities of SailPoint:
- User Lifecycle Management: Automates the process of onboarding and offboarding users, as well as provisioning, de-provisioning, and managing user roles and access rights for both on-premise and cloud applications. This includes creating, modifying, and removing user accounts and access rights across various systems.
- Self-Service and Automated Access Requests: Allows users to request access to applications and automatically provisions access if policy requirements are met. It includes approval workflows for business stakeholders and managers to approve or reject access requests.
- Role and Policy Management: Enables the establishment of roles that define authentication rights for users, enforces user-access policies based on roles or group memberships, and ensures compliance with organizational security policies.
- Reporting and Administration: Offers standard and customizable reporting to track user activities and ensure appropriate access rights.
Pros
Here are some of the benefits that come with using SailPoint:
- Customization: SailPoint’s extensive customization capabilities might be overwhelming for some users. However, for those who need to modify the product code, it offers the ability to access and understand the backend code and create custom logic and events.
- Security: While SailPoint includes several security features
- Features: The platform offers a range of features, including the ability to adjust workflows and rules. However, some users might find the extensive options more complex than necessary for their needs.
- Identity management: It supports managing user identities throughout their lifecycle, providing tools for identity access management and security, which can be beneficial. However, the learning curve can be steep.
Cons
Here are some of the drawbacks that come with using SailPoint:
- Cache issues: Users often face cache issues when working on rules or workflows. If multiple tabs are open and changes are made without saving promptly, the system may only load without saving the updates. Even after saving, changes might not reflect immediately, causing frustration and inefficiency.
- Limited role organization: SailPoint only goes to the role or group name level. That means users must rely on the SailPoint glossary or role name to understand what a role can do–which isn’t very effective since a role can be misnamed. For example, it can be named “engineering read only,” but when you look at the underlying metadata, you might discover that the role can actually delete data. This limited visibility complicates the accurate management and assignment of roles, leading to potential security risks and inefficiencies in role-based access control.
- Inability to see all identities: Cannot detect all identities, like local accounts, leaving potential security gaps if IdP accounts are disabled.
- Cost: SailPoint is at one of the higher price points on the market, which separate pricing for licensing, implementation, and professional services, which can all add up.
- Implementation time: It can take an extensive amount of time from when you first purchase SailPoint to when you can implement it to when you can actually see all your identities (up to six months or longer in some cases). Implementation is so complex that organizations may even have to hire another company to set it up.
- Technical Issues: Debugging code in SailPoint can be time-consuming. Additionally, servers can frequently go down due to load issues, incorrect loggers, or improperly uploaded code, leading to disruptions in service and increased maintenance efforts.
- Performance issues: SailPoint occasionally exhibits erratic behavior due to high cache levels and minor bugs. The user interface is not very intuitive, making it challenging for users to navigate and manage access effectively.
- Bugs: Given the product’s complexity, it comes with numerous bugs and cache issues. Resolving these problems often requires raising vendor tickets and scheduling calls with SailPoint support, a lengthy and sometimes ineffective process.
SailPoint pricing
SailPoint is notably more expensive than many of its competitors, with its pricing being 37% higher than the average IAM product. This significant cost difference can be a considerable drawback for budget-conscious organizations.
For instance, according to AWS Marketplace, the cost of SailPoint SaaS for 2,500 identities over 36 months is a steep $825,000. This high price point may deter some businesses, especially smaller ones, as they might find it difficult to justify such a substantial investment in their identity security infrastructure.
SailPoint reviews
Customer reviews of SailPoint highlight both its strengths and weaknesses.
One user appreciated the extensive customization options:
“In SailPoint, we can have a complete hand on backend code so we can manipulate the Workflow and rules and can customize our requirements. SailPoint gives you single sign-on and privileged access management features and many more.”
However, technical issues can be a significant drawback:
“The thing which I don’t like is the cache issue while working on a rule or workflow. Suppose you are working on different tabs and simultaneously updating any rule, and you make a delay to save it will load and load only but will not save. Sometimes after saving also, it will not reflect the changes.”
Debugging and server stability are also concerns:
“Debugging the code can be time-consuming. Servers getting down every now and then due to load issues or wrong loggers attached or due to incorrect code uploaded.”
And the learning curve for SailPoint can be steep:
“There is a ton of training needed to fully understand and utilize the product to its full potential. All the training offered to use the product is free, but you need to pay for more training to gain a better understanding.”
Best SailPoint alternatives
When evaluating identity security solutions, it’s essential to consider alternatives that might better suit your organization’s unique needs.
Here are some of the top alternatives to SailPoint, each offering distinct features and capabilities designed to improve identity governance and access management.
1. Veza

Veza is an identity security company that powers Intelligent Access, allowing organizations to visualize, manage, and control access across the enterprise. Veza’s access platform goes beyond traditional user and group permissions to understand effective permissions, helping companies identify and address risky permissions and policy violations.
It secures access to data across both on-premise and cloud systems for all identities, including human and non-human.
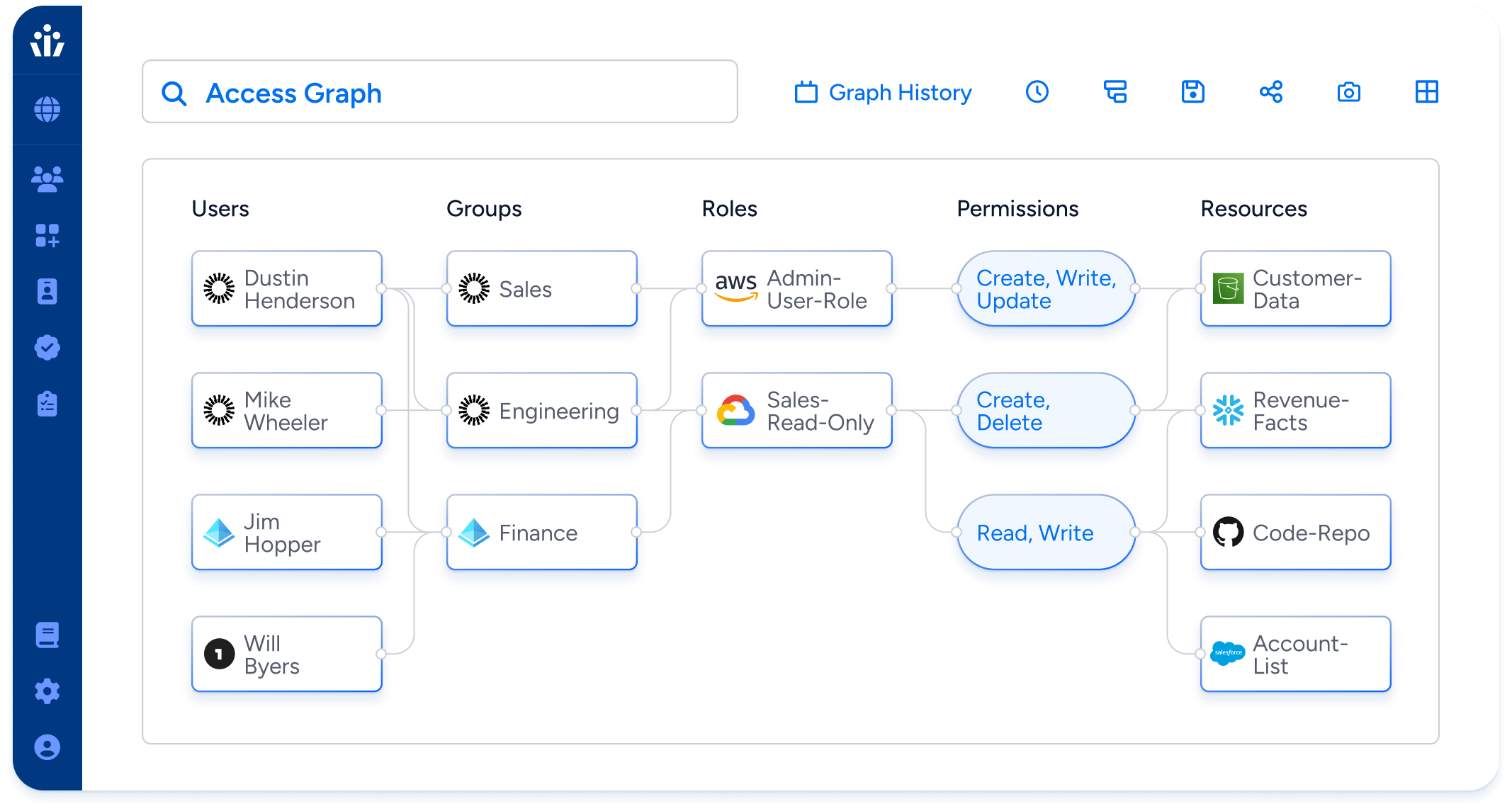
Key Features:
Here are some standout features from Veza:
- Access Graph: Provides a comprehensive view of who has access to what, their permissions are across all systems and resources.
- Threat Investigation: Enables quick and efficient investigation of identity threats, allowing for rapid response and mitigation.
- Automate Access Reviews: Facilitates automated access reviews, streamlining collaboration with business units for smarter access decisions.
- Lifecycle Management: Manages provisioning and de-provisioning of access throughout the entire identity lifecycle for all enterprise systems.
- Effective Permissions Analysis: Ingests and analyzes authorization metadata to reveal effective permissions, giving a clear picture of access mechanisms across the enterprise. Teams no longer have to rely on role names or out of date glossaries.
- Historical Tracking: Uses the Veza access graph to record history and watch for new privileges in near real-time, creating alerts and triggering workflows as needed.
SailPoint vs Veza
Identity governance at scale presents significant challenges due to the diverse ways access can be granted across various systems and applications. Traditional IGA tools like SailPoint risk becoming outdated if they don’t adapt to these complexities.
Veza offers a next-generation identity security solution that addresses these challenges through several key areas:
- Comprehensive System Coverage: Connects to all enterprise systems, including cloud services, on-premise applications, SaaS apps, and data lakes, providing a unified governance view that traditional tools often lack due to budget constraints.
- Inclusive Identity Monitoring: Monitors all types of identities, including non-human identities like service accounts and IoT devices, which are often overlooked by traditional IGA tools but are crucial for comprehensive security.
- Granular Permissions Visibility: Reveals true permissions down to the data object, table, or resource level, offering a more detailed and accurate view of access rights than traditional tools that only focus on users and groups.
- Democratized Information: Translates complex technical permissions into simple business terms, making it easier for identity teams to manage access without needing system-specific expertise.
- Automation: Automates the monitoring, notification, and remediation of policy violations, aiming for continuous compliance. This proactive approach contrasts with the manual and infrequent access review processes typical of traditional IGA tools.
In summary, while SailPoint provides substantial identity security features, Veza offers a more comprehensive and adaptive solution. It addresses modern identity governance challenges with greater granularity, broader coverage, and enhanced automation capabilities.
2. Saviynt
Saviynt provides access governance and intelligence solutions for managing critical data, workloads, DevOps resources, and application access in cloud and enterprise environments. It combines IGA, application access, cloud security, and privileged access management (PAM) into one platform built in the cloud using a microservice-based architecture.
The platform integrates with existing infrastructure, applications, and tools to manage identity governance, risk, and compliance (IGAP), offering a unified view of enterprise identity activities. However, despite its comprehensive features, users might find the deployment process complex and time-consuming, with a steep learning curve and potential integration challenges.
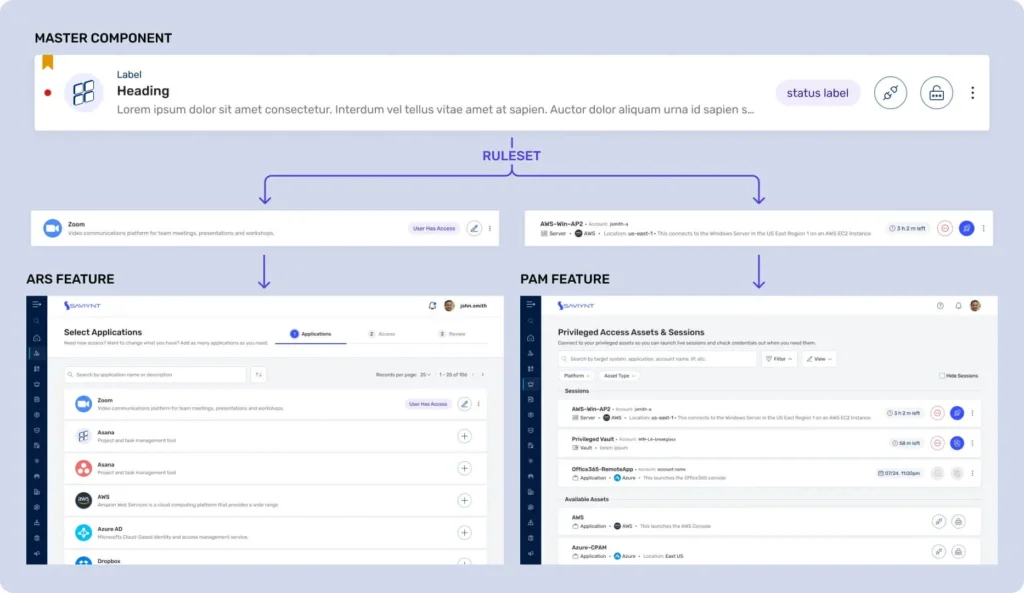
Key Features:
Here are some of Saviynt’s features:
- Application Onboarding: Aims to simplify application onboarding by reducing common challenges such as lack of visibility, controls, and automation.
- Identity Governance and Management: Offers identity governance and management capabilities, including recognized compliance controls.
- Data Protection: Provides data protection capabilities, such as data access governance and intelligence.
- Third-Party Access Management: Provides third-party access management with features like third-party access request management.
3. IBM Security

IBM Security Verify Governance is an identity governance solution designed to manage user access and activity through provisioning, auditing, and reporting capabilities for both on-premises and cloud environments. While it aims to enhance lifecycle management, compliance, and analytics, the platform can be complex and challenging to implement effectively.
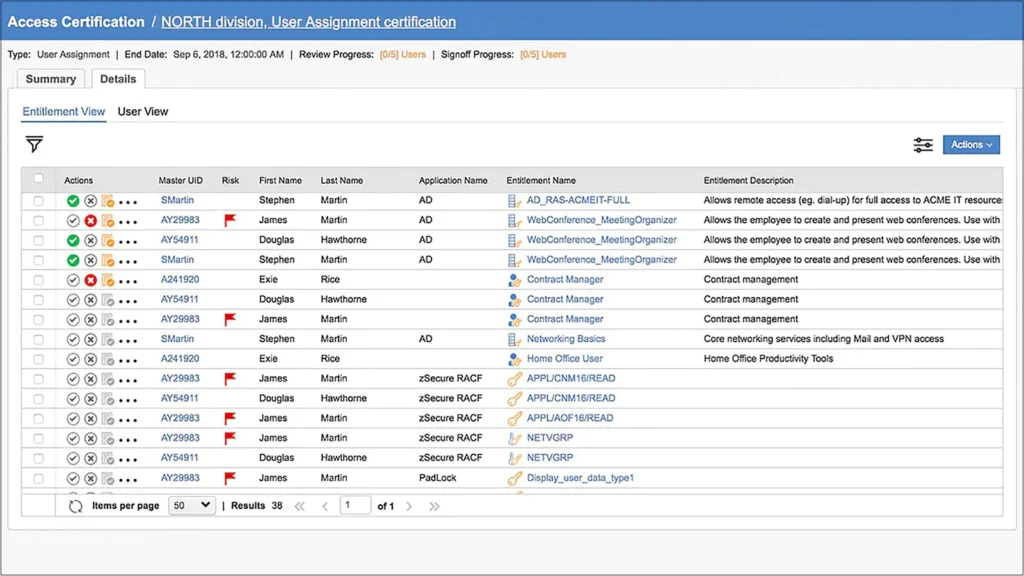
Key Features:
Here are some of the features that come with IBM Security Verify Governance:
- Risk Modeling: Uses business activities for risk modeling instead of traditional role-based policies.
- User Provisioning and Self-Service: Provides provisioning and self-service requests for onboarding, offboarding, and managing employees.
- Regulatory Compliance: Offers tools for closed-loop compliance, data governance, and GDPR-specific controls.
- Identity Analytics: Gives visual insights into risky users and insider threats.
- Access Certification: Runs access certification campaigns with a customizable dashboard.
4. One Identity

One Identity by Quest provides a unified identity security solution for managing access rights, verifying identities, and adapting to evolving threats. Despite its comprehensive features, users might find the platform’s complexity and implementation challenges somewhat daunting.
Key Features:
Here’s a closer look at One Identity’s features:
- Identity Governance and Administration: Manages user identities, data, and privileged permissions across on-prem, hybrid, and cloud environments.
- Active Directory Management: Simplifies AD and Azure AD management but can be complex to fully integrate, especially for non-Windows systems.
- Privileged Access Management (PAM): Offers tools to secure, control, and monitor privileged access.
- Access Certification: Streamlines governance processes and manages user identities and privileges.
- Data Governance: Extends governance to privileged accounts and provides detailed, real-time audit reports.
5. Oracle

Oracle Identity and Access Management solutions secure access to enterprise applications for both cloud and on-premises deployments. While it offers flexible protection options and scalability, the complexity and integration challenges may pose difficulties for some organizations.
Key Features
Here are some of the features that come with Oracle:
- Protection for Workloads: Provides various deployment options, including cloud-native identity as a service (IDaaS) and hybrid environments.
- Scalability: Designed to scale to millions of users.
- Identity Management: Enables management of user access and entitlements across cloud and on-premises applications.
- Zero Trust: Enforces access policies with SSO, password enforcement, and multifactor authentication.
- Access Governance: Provides visibility and governance for cloud and on-premises environments.
More about SailPoint
Here’s a closer look at some frequently asked questions about SailPoint:
What does SailPoint do?
SailPoint provides identity security solutions designed to manage and control user access to various technology resources. It aims to streamline processes like user provisioning, access requests, and compliance management. However, users often encounter complexities and technical issues that can impede efficiency.
Who owns SailPoint?
SailPoint is currently owned by private equity firm Thoma Bravo, which acquired the company in 2022. This ownership might influence the company’s strategic decisions and priorities, which could impact service and product development.
Choose the best SailPoint alternative
When it comes to choosing an identity security solution, it’s essential to find a platform that not only meets your needs but also simplifies your processes without overwhelming you with complexity.
Many alternatives to SailPoint, such as IBM Security Verify Governance, Saviynt, One Identity, and Oracle Identity and Access Management, come with their own set of challenges. These platforms often present significant integration hurdles, steep learning curves, and complex deployment processes that can impede rather than enhance your identity governance efforts.
However, Veza stands out as a superior choice. Veza’s access platform is designed to provide a seamless, user-friendly experience, going beyond traditional user and group permissions to offer comprehensive insights and control.
With Veza, you can easily visualize, manage, and secure access across all your systems, whether on-premises or in the cloud. Its intuitive interface, powerful automation, and real-time threat detection capabilities ensure that your identity governance is both effective and efficient.
Choose Veza for a streamlined, intelligent approach to access management that truly meets the needs of modern enterprises.
Schedule a demo and see how Veza can transform your identity security strategy.





