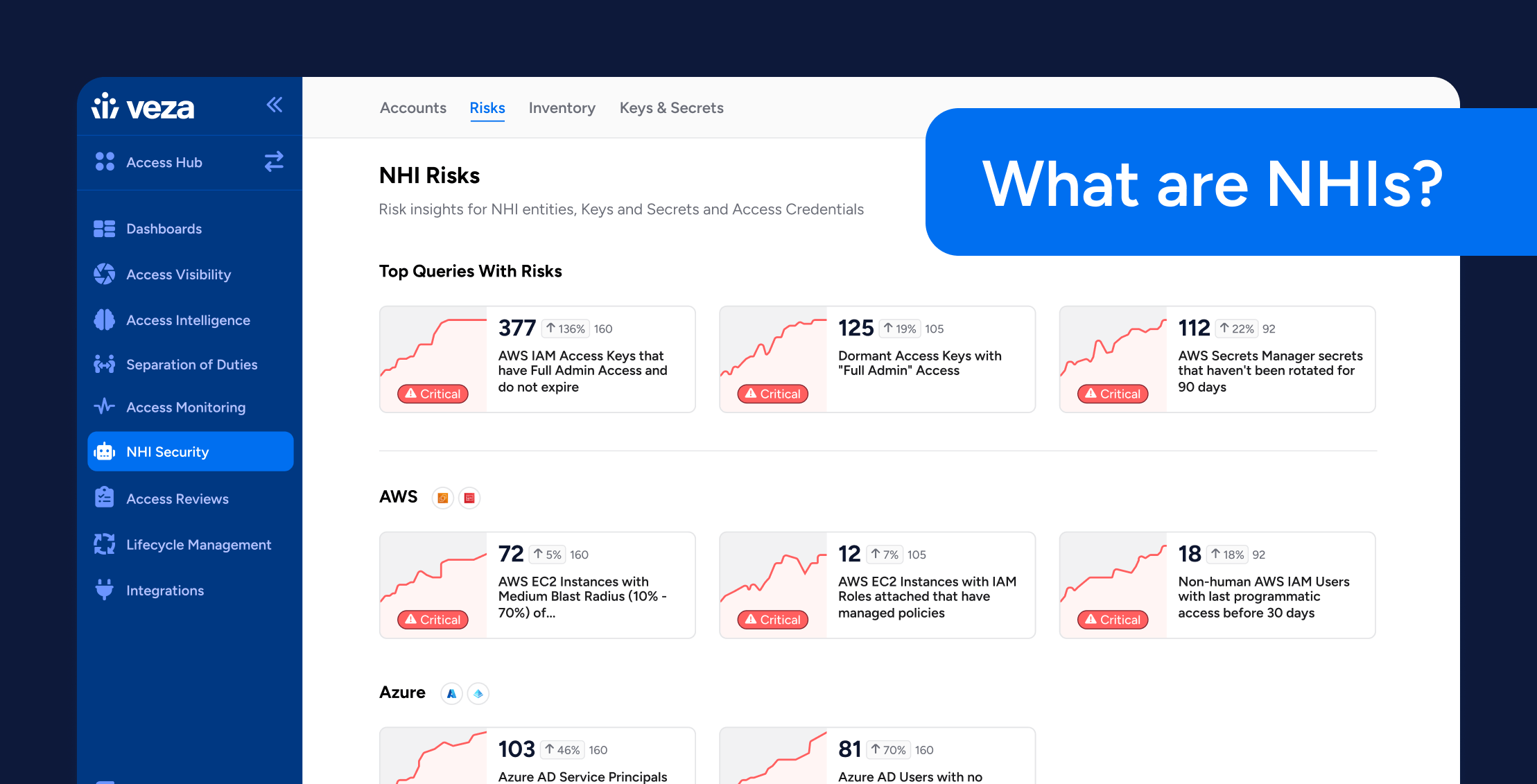
Many may not realize it, but non-human identities are everywhere, powering essential digital processes. This invisible workforce of systems, scripts, and services keeps modern enterprises running smoothly, handling everything from automated data transfers to cloud service operations. Now, with reliance on automation and integration at an all-time high, managing NHIs is fast becoming non-negotiable for securing modern IT environments.
However, just 15% of companies are highly confident in their ability to prevent NHI attacks—a fraction compared to the more than two-thirds concerned about risk exposure. For many, a troubling reality is emerging: Just because businesses recognize NHI risks doesn’t mean they know what to do about them. For many, a better understanding of non-human identities and how they work will help teams manage them more effectively without adding complexity.
This article covers all the essentials of NHIs: what they are, how they work, and the risks they introduce. It also explores different types of NHIs with use cases and examples and offers best practices for non-human identity management.
What is a Non-Human Identity?
A non-human identity (NHI) is a type of digital identity created for machines, applications, or devices to help keep enterprise systems, applications, and workflows running smoothly. Like human users, they execute essential functions like accessing data, completing tasks, and communicating with other systems.
Today, NHIs make up a significant portion of the total users in most enterprise environments, often outnumbering human identities by an average of 17-to-1.
Unlike human users, NHIs operate without direct oversight or interactive authentication. Some run continuously, using static credentials without safeguards like multi-factor authentication (MFA). Because most NHIs are assigned elevated permissions automatically, they’re often more vulnerable than human accounts—and more attractive targets for attackers.
When organizations fail to monitor or decommission them, however, these identities can linger unnoticed, creating easy entry points for cyber threats.
How Do Non-Human Identities Work?
NHIs take many different forms and perform specific functions. Each non-human identity is created to fulfill a particular purpose in automated workflows, system processes, or application connections. Whenever a cloud workload spins up a virtual machine, for example, or a CI/CD pipeline deploys new code, there’s a non-human identity behind the scenes, facilitating that action.
In fact, NHIs enable thousands of routine business processes across industries in nearly every organization every day. Yet, despite how essential they are to enterprise operations, NHIs are often overlooked. Most of the time, that’s because people simply don’t understand what they do. Here are some common types of NHIs to help clarify:
- API Keys: Allow applications to exchange data securely, often between internal systems or third-party services.
- Service Accounts: Used by applications or background services to perform tasks like data backups, reporting, or scheduled jobs.
- Service Principals: A specific service account commonly found in cloud environments that lets apps authenticate and access cloud resources.
- Tokens: Temporary credentials that authorize access to specific services or data for a limited time, often used in OAuth-based authentication.
- Certificates: Validate the identity of software, devices, or systems to establish secure connections, often with encryption.
An NHI is created every time an application, system, or administrator identifies the need for an automated digital process, like syncing data between an application and a cloud database. After it’s generated, each NHI is assigned credentials and permissions that define what it can access and what actions it can perform.
Once authenticated, the NHI completes its assigned task, which could involve retrieving data, initiating a file transfer, scaling infrastructure, or triggering a deployment. In some cases, NHIs might keep these connections open after the task is completed so data can flow smoothly between apps and systems in real time to support AI, automation, and analytics engines.
To keep NHIs secure, some organizations apply the same access governance principles used for human identities. Limiting permissions, regularly rotating credentials, monitoring usage, and deactivating NHIs when no longer needed are fundamental.
Without these controls, NHIs can accumulate excessive access and, eventually, introduce significant security risks.
Types of Non-Human Identities
How non-human identities function ultimately depends on the environment in which they operate. Some NHIs manage virtual infrastructure while others keep cloud apps connected or handle continuous deployments. Each serves a unique purpose, and that variability is exactly what makes managing them at scale so challenging.
All NHIs are key for automation, security, and integration, granting permissions that allow systems to connect, pull data, and execute tasks. Here are some key places NHIs often show up and the specific actions they perform.
1. Devices
Laptops, mobile devices, servers, and Internet of Things (IoT) devices use NHIs to authenticate securely, access networks, and communicate with other systems. These identities help maintain data availability and security across distributed environments with thousands of connected devices.
An IoT device, for example, might collect sensor data and send it to a cloud platform using a certificate-based NHI.
2. Software-defined Infrastructure (SDI)
In software-defined infrastructure environments, NHIs control virtual resources like storage, compute, and networking. They handle provisioning, managing, and decommissioning automatically. These identities make it possible to scale infrastructure without human intervention.
For instance, an NHI might spin up a virtual machine in response to a workload demand and then shut it down once the task is complete.
3. DevOps Tools
DevOps environments use NHIs to automate continuous integration and delivery (CI/CD) processes. NHIs initiate builds, run tests, and deploy code across environments. A tool like Jenkins, for example, might use a service account to trigger deployment scripts or update container images—no human required.
Without the proper controls, however, these accounts can become powerful, persistent, and hard to track.
4. Service Accounts
Service accounts, including cloud service principals, are among the most common and high-risk NHIs. Often used in enterprise systems like Active Directory, service accounts help apps query databases, monitor system health, or generate automated reports—critical tasks usually requiring elevated privileges.
If compromised, improperly scoped service accounts can expose sensitive systems to security risks and unauthorized access.
5. System Accounts
System accounts power IT operations in the background, allowing operating systems and services to run updates, execute scheduled jobs, or maintain uptime for web servers and databases. These accounts are typically long-lived and may go untouched for years, making them easy to overlook during audits or decommissioning cycles.
6. Application Accounts
Application accounts let software applications communicate securely with external systems. For example, a customer relationship management (CRM) tool might use an application account to pull user data from a separate analytics platform. These identities often use API keys or certificates to authenticate and authorize access and are essential for integrating modern SaaS ecosystems.
Non-Human Identity Use Cases
NHIs are deeply embedded in day-to-day digital operations. They keep systems connected, workflows moving, and infrastructure running, often without anyone noticing. Although technical, NHIs also support business processes in tangible ways.
Here are a few NHI use cases with real-world examples to illustrate the importance of securing and managing them properly.
Integrating Applications
A marketing team needs data from their CRM to trigger email campaigns in their automation platform. An API key—an NHI—facilitates that connection, automatically syncing customer records in real time. If this identity is misconfigured or unmanaged, it could expose sensitive data across tools without anyone realizing it.
Automating Digital Workflows
In financial services, Robotic Process Automation (RPA) bots process invoices, reconcile transactions, and update internal systems, using NHIs to access and move data across departments. If those permissions aren’t assigned correctly, a compromised bot could move laterally across high-value systems.
Managing Cloud Service Operations
A cloud engineering team configures NHIs to manage virtual machines, storage, and scaling operations. These service accounts launch infrastructure during peak hours and shut it down when demand drops. Without proper tracking, these identities can accumulate unused privileges or stay active long after they’re needed.
Ensuring Consistent Software
During each code deployment, NHIs embedded in the CI/CD pipeline run tests, validate build artifacts and push updates to production. If an expired certificate or forgotten service principal breaks the chain, the release stalls—or worse, unverified code slips through.
How Are Non-Human Identities Different From Human Identities?
Managing non-human identities takes a very different approach from managing human ones. Both need to be secured and well-governed, but NHIs introduce a unique set of challenges stemming from how they’re created, used, and maintained. Here are some of the key differences between NHIs and human identities.
Authentication and Access Control
Human users authenticate access with credentials like usernames, passwords, and MFA. NHIs, on the other hand, use static credentials that can’t respond to prompts or change periodically. These credentials, like API keys, certificates, and service account passwords, often remain intact far longer than they should, increasing the risk of unauthorized access if not rotated or monitored.
Visibility and Monitoring
Security teams use tools like Security Information Event Management (SIEM) systems to detect suspicious human behavior, but those same tools often struggle to track NHIs. Automated tasks generate high volumes of activity, which makes it harder to distinguish normal behavior from anomalies. As a result, an NHI used maliciously can go undetected for far longer than a compromised human account typically would.
Lifecycle Management
Human identities are typically tied to Identity and Access Management (IAM) systems and follow defined processes with clear onboarding, updating, and de-provisioning steps to prevent stale accounts. But NHIs typically lack these controls. Instead, they’re created for a specific task and then forgotten—even if they keep access to critical systems. Without proper lifecycle management, these dormant yet privileged accounts can linger indefinitely.
Privilege Management
Humans are generally assigned access based on job function to enforce least privilege through role-based access control (RBAC). NHIs, however, often need elevated or specialized permissions to perform automated tasks. Because they support so many workflows, it can be difficult to apply consistent access controls and even harder to know when permissions should be revoked.
Documentation and Oversight
Most organizations have well-documented policies and processes for managing human identities, such as user access reviews, access requests, or privilege escalation. NHIs, on the other hand, are often created ad hoc, without formal approval, ownership, or tracking.
Unfortunately, that lack of documentation can create long-term visibility and compliance risks by making it harder to understand what each identity does, who created it, and whether it’s still in use.
Challenges and Security Risks of Non-Human Identities
The most significant NHI challenges and risks often stem from a lack of visibility and inconsistent governance. Even when organizations understand the risks associated with NHIs, managing them at scale is another matter. Often living outside traditional identity governance frameworks, these identities are difficult to track, assess, and control over time.
Here are some of the most persistent operational and security challenges that teams managing NHIs face today.
1 – Uncontrolled Growth and Sprawl
There’s no central checkpoint for creating a new NHI in most environments. Instead, developers, engineers, and automation tools spin them up on demand, often without standard naming conventions, ownership assignments, or expiration dates. And, as usage scales, so does the sprawl.
Without a clear inventory, teams can quickly lose track of which identities exist, what they can access, and whether they’re still in use.
2 – Persistent High Privileges
Because NHIs often serve critical business functions, they’re often granted broad or elevated permissions to make sure processes run smoothly. One granted, however, those privileges rarely get revisited.
A service account created for a time-bound project, for instance, may still have admin-level access years later, well beyond its intended use. Forgotten but privileged, these identities can easily become soft targets for attackers.
3 – Blind Spots in Monitoring
Many NHIs are indistinguishable from human accounts in system logs. Plus, most traditional monitoring tools aren’t built to flag anomalous behavior from automated identities. So, if an NHI is compromised or misused, it can access sensitive systems or data for weeks or months without triggering alerts.
4 – Inconsistent or Missing Ownership
Unlike human users, NHIs aren’t tied to departments or job titles. If the original creator leaves the company or switches teams, whoever replaces them may not realize they’re responsible for dozens of service accounts or tokens. When ownership isn’t clearly assigned, it’s nearly impossible to verify whether an NHI should still exist or what might break if it’s removed.
5 – Static Credentials That Don’t Age Well
Many NHIs rely on credentials that aren’t rotated regularly, if at all. Living in configuration files, scripts, or infrastructure, these hardcoded credentials often persist long after their usefulness. If leaked, they can give attackers long-term, unaudited access to core systems.
6 – Operational Risk from Orphaned Identities
Non-human identities are typically tied to a specific function, task, or tool. Yet, when those systems are retired or replaced, NHIs remain, often with the same permissions they were granted at creation.
In some cases, these ‘orphaned identities’ last far longer than intended, some retaining active access even though no one remembers why. Beyond risk, orphaned identities can also create operational friction during audits, incidents, and system upgrades.
7 – Gaps in Tooling and Governance
Even teams with strong secrets management and identity governance practices discover NHIs that fall outside their normal processes. These tools assume a clean inventory and consistent metadata—neither of which exists for most NHIs. Without widespread visibility, unmanaged identities can slip through the cracks.
Key Takeaways for Managing Non-Human Identities
Most security teams don’t need more reminders that NHIs are risky. But they do need practical ways to manage them in fast-moving environments where NHIs aren’t always documented, owned, or even visible. Here are actionable best practices to help organizations build a more secure non-human identity strategy.
- Build a complete, contextual inventory. Use automation to discover all NHIs across your environment, including cloud platforms, SaaS apps, on-prem systems, and custom applications. Go beyond active service accounts to surface long-forgotten tokens, expired certificates, and orphaned credentials. Group NHIs by type, label them consistently, and prioritize them based on access level and usage risk.
- Assign ownership and define accountability. Every NHI should have a clearly designated human owner who understands what the identity does, why systems it touches, and what the business impact would be if it were removed. Review and remediation efforts can quickly stall without ownership, and risky identities can linger unchecked.
- Right-size access based on real-world usage. Avoid the temptation to provision broad access “just to make things work.” Monitor actual activity to understand what each NHI needs and remove anything it doesn’t use. Tracking “last used” timestamps, privilege levels, and system touchpoints can help eliminate access without disrupting automation.
- Establish clear lifecycles with expiration and renewal. NHIs created for temporary projects, one-off integrations, or short-lived workflows should expire by default. Set up automated expiration and credential rotation policies and implement renewal workflows tied to ownership, frequency, and current use cases.
- Integrate NHIs into identity security frameworks. Don’t manage NHIs in isolation. Instead, fold them into access reviews, certification campaigns, compliance audits, and policy enforcement. Apply the same rigor and expectations you use for human identities—but with the tooling designed to meet the scale and variability of NHIs.
The most effective way to manage non-human identities is to treat them like first-class identities: discoverable, ownable, auditable, and subject to the same access governance standards as human users. For most, that starts with more visibility, but it doesn’t end there. Because the real challenge isn’t identifying NHIs, it’s putting the right structure in place to manage them without breaking or slowing things down.
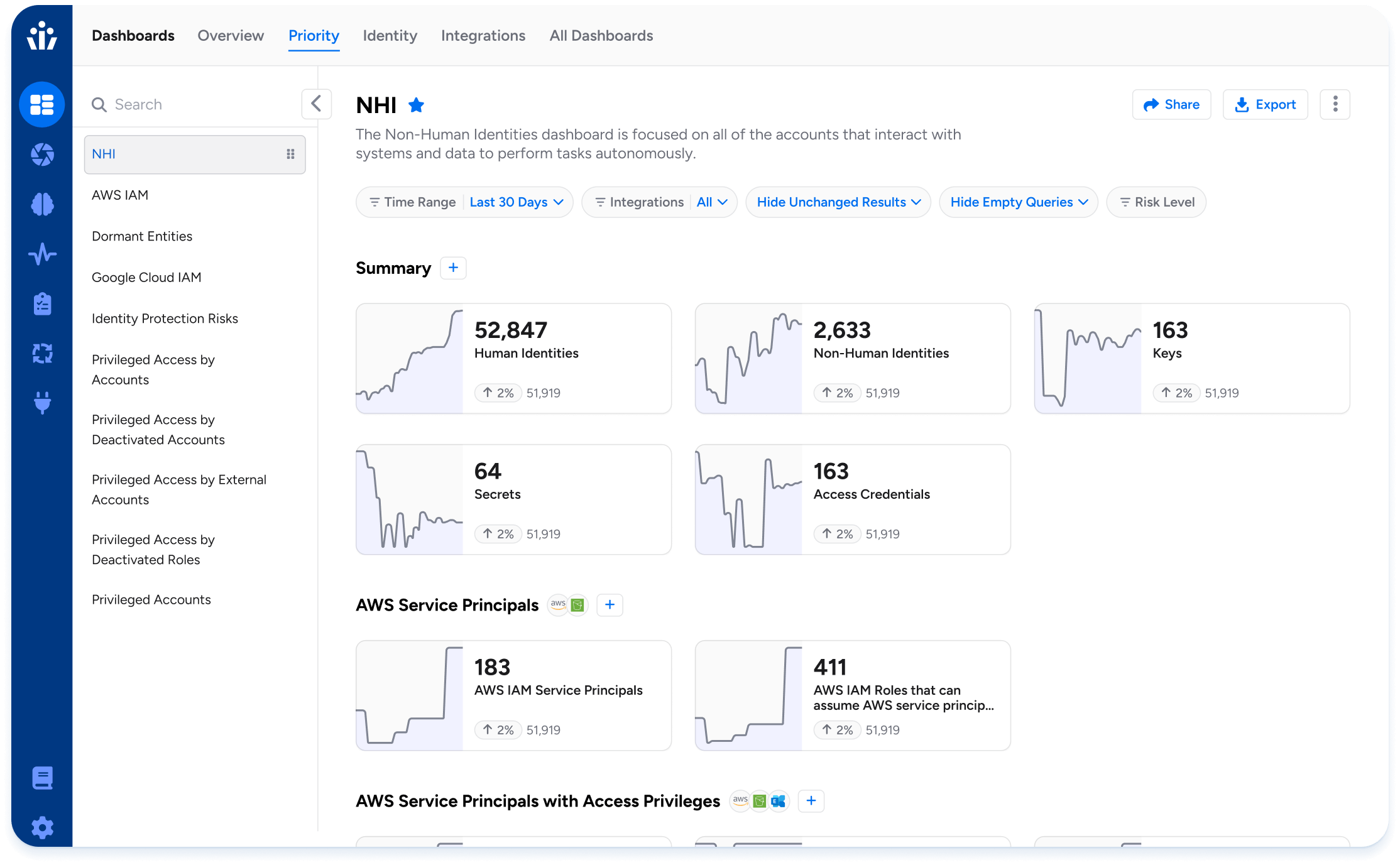
Discover NHIs across your stack with intelligent access
Strengthen Your Non-Human Identity Management
NHIs might operate out of sight and out of mind, but every single one adds volume to your attack surface. As they multiply across cloud services, applications, and automation pipelines, NHIs quietly accumulate privileges and introduce access risks. Yet the security teams responsible for managing them often lack the tools, context, or ownership structures to do so effectively.
Few organizations can confidently answer basic questions like: How many NHIs are active? What systems can they access? Who’s responsible for them? Without clear answers, access risk can grow, audits can stall, and security can become yet another bottleneck to innovation.
Now, Veza makes straightforward non-human identity management possible. Veza, the Identity Security company, captures access metadata from all enterprise systems and organizes it into a unique Access Graph, so you can answer, in real-time: who–including NHIs–can take what action on what data?
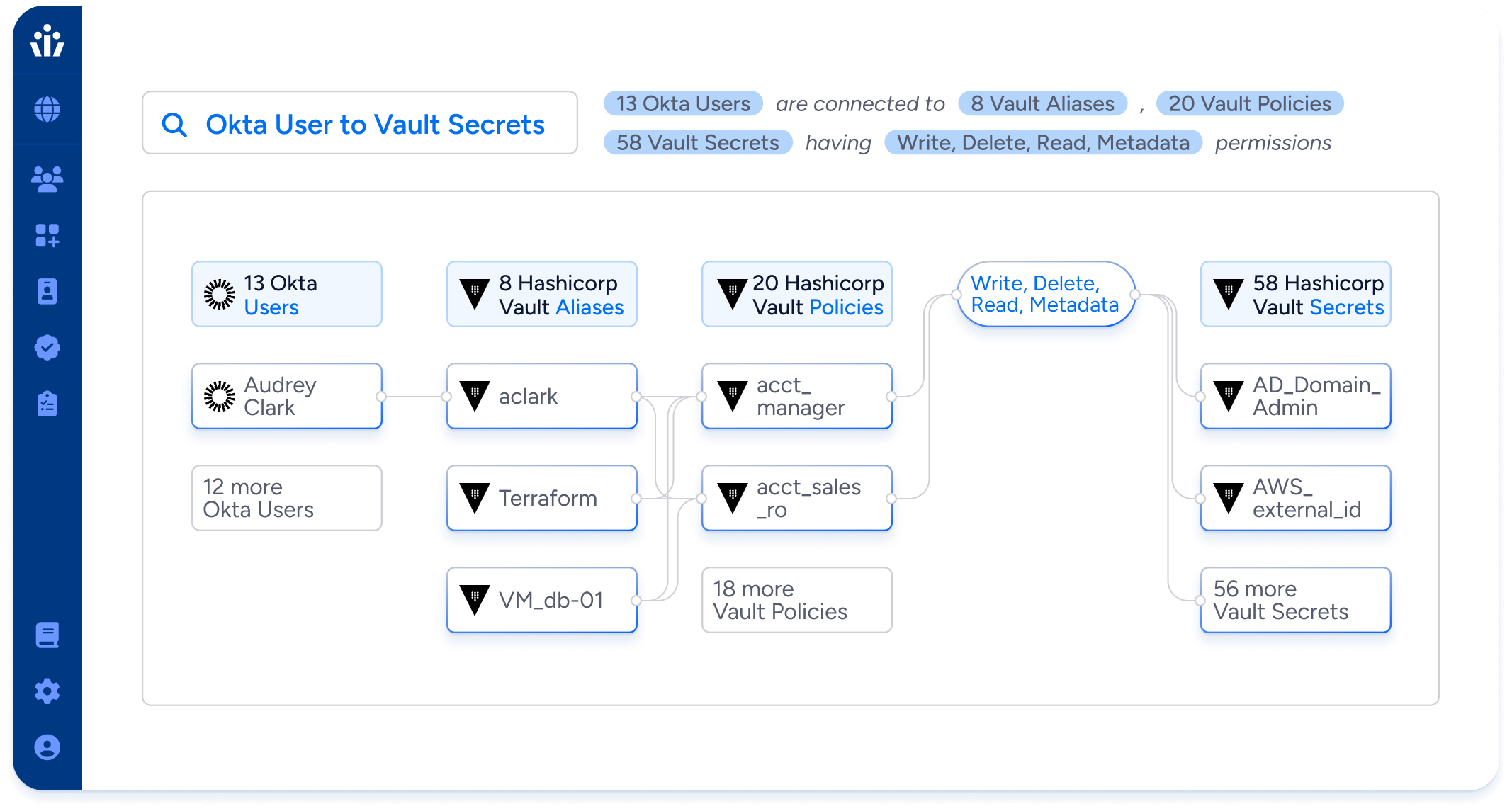
With Veza, you can:
- Discover NHIs across your stack. Quickly identify non-human identities across on-prem, SaaS apps, custom apps, and cloud infrastructure. Import data from CMDBs or external spreadsheets to label identities and assign human owners.
- Eliminate unmanaged or undocumented NHIs. Detect NHIs not tracked by your secrets manager and align them with your access policies and governance standards.
- Enforce least-privilege access. Analyze real permissions usage to remove unnecessary or overly broad access without disrupting critical processes or automation workflows. Restrict the power to create and provision virtual machines, certificates, and secrets.
- Streamline governance and certification. Run ownership reviews, confirm business needs, and validate that permissions reflect actual usage and role requirements.
- Simplify lifecycle management. Monitor key indicators like “Time Last Used” and “Time Last Rotated” to drive regular access reviews, credential rotation, and timely deprovisioning.
With Veza, you can turn visibility into action, ownership into accountability, and governance into something that actually scales.
Learn more about how Veza can help bring NHIs into your security strategy, reduce identity risks, and simplify access control.
About the Authors
This article was developed in collaboration between Mariah Brooks, an independent consultant and researcher focused on identity security, and Matthew Romero, Technical Product Marketing Manager at Veza.
Mariah brings deep experience translating complex technical challenges into practical, real-world insight. With a background spanning identity governance, cyber risk, and responsible AI, she’s spent 5 years working alongside CISOs and security architects to unpack emerging issues like Non-Human Identities (NHI). Her clarity, context, and credibility make her a trusted voice for security leaders navigating high-stakes access decisions.
Matthew brings a strategic marketing lens grounded in the realities of modern enterprise security. At Veza, he helps define go-to-market positioning for identity-first security solutions, bridging the gap between technical innovation and customer relevance. His work focuses on connecting product capabilities to the risks and operational demands security teams face every day.
Learn more about their work:
Mariah Brooks – LinkedIn
Matthew Romero – LinkedIn






