
User access reviews (UARs) have become a frontline defense in modern identity security. As identity threats grow in both volume and sophistication, security teams need better ways to verify that every user, human or not, has only the access they truly need.
These reviews aren’t just about compliance checkboxes anymore.
90% of organizations experienced an identity-related security incident last year, and 84% reported direct business impact, according to the Identity Defined Security Alliance. Whether you’re facing increased scrutiny under GDPR, SOX, HIPAA, or NIS2, regularly verifying access is essential to protect critical systems, maintain operational integrity, and reduce lateral movement risk.
But as cloud sprawl accelerates and non-human identities proliferate, managing user access reviews has become increasingly complex—and the stakes have never been higher. Choosing the right UAR software can help automate oversight, reduce manual work, and improve security posture across the board.
In this guide, we’ll break down how UAR tools strengthen security, what features matter most, and how 12 top platforms compare.
Benefits of user access review software
User access review software helps security teams move from tedious manual processes to a streamlined, scalable way to manage access risk. The right platform does more than prepare you for audits; it actively strengthens your organization’s identity security posture by ensuring the right people have the right access at the right time.
Key benefits of modern UAR tools include:
- Minimizing unauthorized access: Automatically identify and remove excessive, outdated, or inappropriate permissions to reduce the attack surface.
- Improved compliance: Automate review cycles and generate audit-ready reports to meet regulatory requirements such as GDPR, HIPAA, and SOX, and provide detailed audit trails for compliance reporting.
- Reduced manual processes: Free up IT and security teams from repetitive tracking, reminders, and documentation tasks by automating these processes.
- Proactive risk mitigation: Detect anomalies, dormant accounts, and risky access patterns early to prevent potential security incidents.
Features to look for in user access review tools
User access review software has become a cornerstone of effective identity governance. When evaluating solutions, focus on these critical features to ensure your tool can keep pace with today’s complex identity environments:
Comprehensive visibility across all identities
Your UAR solution must provide a full picture of access rights across every identity type—full-time employees, contractors, local accounts, and, importantly, non-human identities like service accounts and machine identities. Without this, gaps in coverage create blind spots that attackers can exploit.
Automated, reliable review workflows
Manual reviews are slow and prone to errors, but blindly rushing through automated ones can cause problems too. Look for platforms that balance automation with intelligent controls, ensuring permissions are validated accurately without rubber-stamping.
Separation of Duties (SoD) enforcement:
To reduce fraud and risk, your UAR tool should detect separation of duties (SoD) conflicts automatically and flag potential violations for remediation. This is critical for regulatory compliance and internal control integrity..
Built-in compliance support
The platform should streamline adherence to legal frameworks like GDPR, SOX or HIPAA, by automating review schedules, tracking changes, and providing comprehensive audit trails. This helps avoid costly fines and protects your organization’s reputation.
Robust audit trails and reporting
Detailed logs and reports provide transparency and enable security teams to investigate suspicious activities, demonstrate compliance during audits, and continuously improve access governance processes.
Selecting a platform with these capabilities is foundational to managing identity security posture effectively in complex, hybrid, and cloud environments.
Top user access review software
Here, we explore the top user access review software tools that can help your organization manage identity governance and regulatory requirements at once:
1. Veza

Veza is the identity security platform specializing in comprehensive permission visibility and governance across all identity types—including human users, service accounts, and other non-human identities. By mapping effective permissions through its unique Access Graph technology, Veza reveals what each identity can do across cloud, SaaS, data systems, and on-premises environments.
Veza’s Access Reviews and Access Intelligence automates user access review workflows with risk-based decision-making capabilities, incorporating separation of duties policies, activity monitoring, and pre-built queries to auto-approve or flag risky access. This streamlines governance and reduces manual overhead.
The platform supports flexible deployment with a cloud-native architecture and seamless integrations to major cloud providers (AWS, Azure, GCP), SaaS applications, data platforms, and traditional enterprise systems. By translating complex permission data into clear, natural language, Veza enables business users and technical teams alike to collaborate effectively on access decisions.
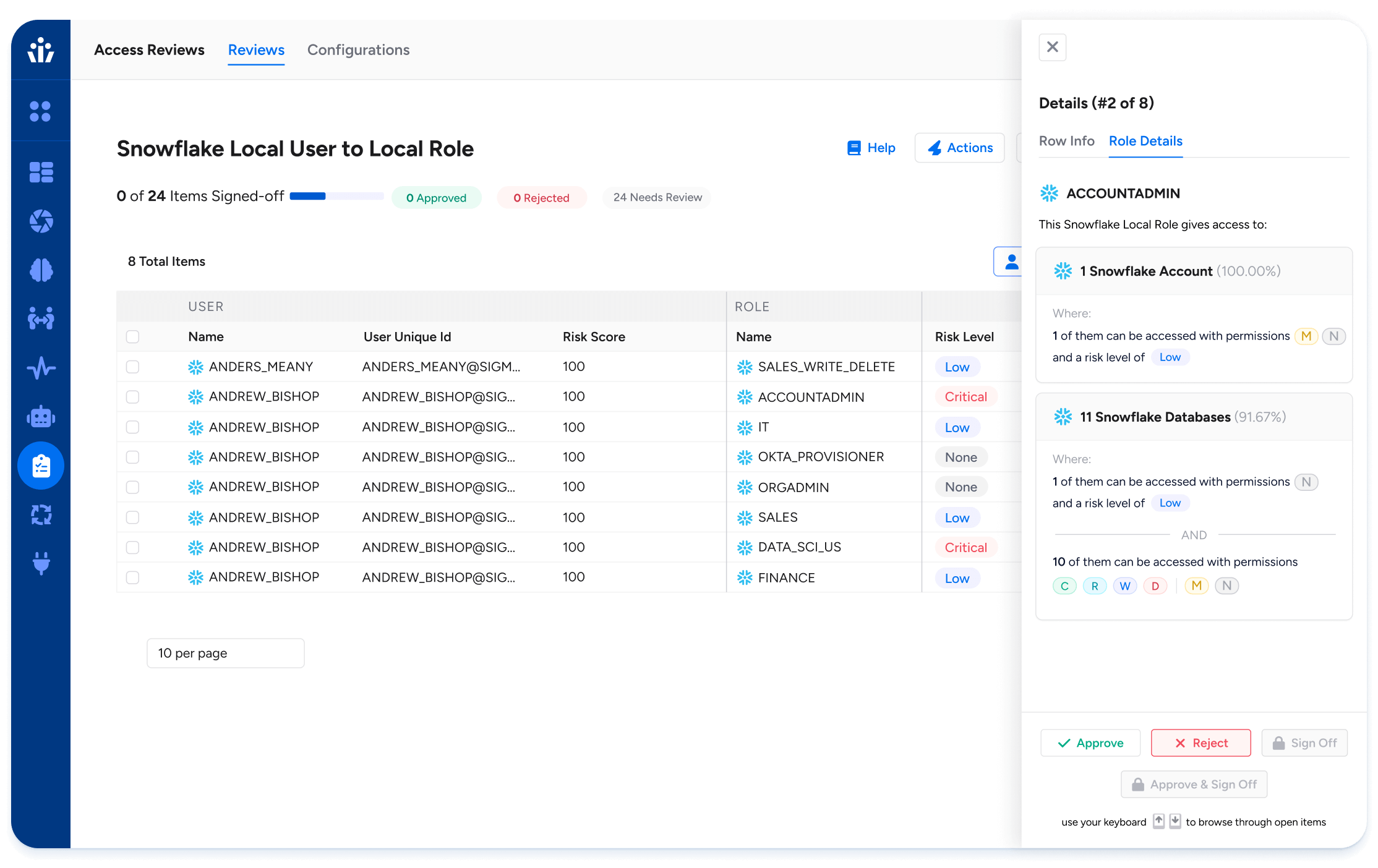
Key Features and Benefits:
- Intelligent Access: Leverage user risk scores, policy violations, and usage insights to prioritize and automate risk-based access reviews. This ensures that high-risk permissions get the attention they deserve without overwhelming your team.
- Quick Time to Value: Veza’s cloud-native architecture enables fast integration and flexible deployment options, backed by a modern developer experience that accelerates onboarding and custom workflows.
- Natural Language Permissions: Complex role and permission metadata are translated into plain language, empowering business users to understand exactly what access entails and make informed decisions during reviews.
- Comprehensive Identity Monitoring: Veza monitors all identity types—including human users, local accounts, service accounts, and machine identities—for complete visibility across your environment.
- Granular Permission Insights: Veza goes beyond basic group or role names to show detailed, effective permissions, reducing blind spots and enabling precise access control.
- Seamless Integrations: The platform connects with a wide array of enterprise systems—cloud infrastructure providers (AWS, Azure, GCP), SaaS applications, databases, and on-premises environments—ensuring consistent governance everywhere access exists.
Customer Ratings:
Veza consistently gets positive feedback from customers. Here are a few customer reviews to consider:
“The authorization platform for data security! Veza has been an outstanding company to work with. Their commitment to quality and customer satisfaction is unparalleled, and their innovative approach to business ensures that they remain at the forefront of their industry.”
- Customer in the Healthcare and Biotech Industry
“Their integration with pretty much any system out there in the IT realm is impressive. The ability to have end-to-end visibility across our whole cloud footprint and understand who can access what resource, whether on-premise or in the cloud, has been invaluable.”
- Customer in the IT Services Industry
Best for: Veza is ideal for organizations looking to modernize access management across the board, including privileged access monitoring, cloud access governance, data security, and comprehensive management of both human and non-human identities. With Veza, security and IT teams gain clear visibility into who has access to what, enabling rapid threat investigation and automated, risk-aware access reviews that drive smarter, faster decisions.
2. Sailpoint

SailPoint is a well-established identity governance platform that offers robust capabilities for managing user identities and access rights across complex enterprise environments. It’s designed to provide centralized identity lifecycle management, automated access certifications, and comprehensive policy enforcement.
Key Features & Benefits:
- Centralized Identity Management: Supports user provisioning, role-based access control (RBAC), and lifecycle management to streamline identity governance workflows.
- Automated Access Reviews: Automates user access certification campaigns to help meet regulatory and compliance requirements efficiently.
- Policy and Risk Management: Enables organizations to define, enforce, and monitor access policies to reduce risks like segregation of duties (SoD) violations.
- Extensive Integration Ecosystem: Integrates with a broad range of enterprise systems, applications, and cloud platforms, supporting hybrid IT environments.
- Analytics and Reporting: Offers detailed audit trails and reporting capabilities for compliance and operational insight.
Customer Ratings:
Here’s what customers have to say about SailPoint:
- Pros: Users appreciate SailPoint’s comprehensive governance capabilities and centralized management features once the platform is fully deployed.
- Cons: Deployment complexity, occasional system bugs, and a steep learning curve are commonly cited challenges.
Best for: Organizations seeking a mature, enterprise-grade identity governance solution with strong compliance features and policy enforcement will find SailPoint a solid choice. However, its complexity and resource requirements may be a consideration for smaller teams or those seeking rapid time-to-value.
3. SecurEnds
SecurEnds is a cloud-native Identity Governance and Administration (IGA) platform designed to automate identity governance processes, including access reviews, provisioning, and lifecycle management. It aims to simplify permission management by leveraging role-based access controls aligned to job functions.
Key Features & Benefits:
- Automated access reviews: Streamlines periodic reviews to ensure appropriate user access.
- User lifecycle management: Automates provisioning and deprovisioning to reflect onboarding, role changes, and offboarding.
- Role-Based Access Control (RBAC): Facilitates permission management by associating access rights with predefined roles.
- Connector library: Supports integration with numerous enterprise systems for identity and access data synchronization.
Customer Ratings:
Here’s what customers have to say about SecurEnds:
- Pros: Cost-effective with easy administration and comprehensive connectors.
- Cons: Inability to preview campaigns before template creation and limited editing options for names and descriptions after creation.
Best for: SecurEnds suits organizations looking for a cost-effective, straightforward IGA solution with a focus on RBAC and lifecycle automation. However, its traditional IGA approach may lack the granular permission visibility and non-human identity management critical for securing complex hybrid environments today.
4. ConductorOne

ConductorOne is a cloud-native identity security and automation platform designed to streamline identity governance, access management, and compliance workflows. It emphasizes automation of user lifecycle processes and risk-aware access reviews to reduce manual overhead and improve security posture.
Key Features & Benefits:
- Automated Access Reviews: Simplifies access certification campaigns with automated workflows and built-in risk assessments.
- User Lifecycle Management: Provides onboarding-to-offboarding identity lifecycle automation, reducing orphaned accounts and access sprawl.
- Policy Enforcement: Supports segregation of duties (SoD) and other policy controls to mitigate risk and ensure compliance.
- Integration Library: Connects with popular enterprise applications and infrastructure, though coverage varies across tech stacks.
- Collaboration and Workflow: Facilitates coordinated access decisions between IT, security, and business stakeholders.
Customer Ratings:
Here’s what customers have to say about ConductorOne:
- Pros: Responsive vendor collaboration on integrations, user-friendly automation features.
- Cons: Limited ability to modify access during live reviews and gaps in integration coverage for some environments.
Best for: Mid-sized organizations aiming to automate access reviews and identity lifecycle provisioning with a modern, cloud-first platform, especially those willing to invest in building out integrations and workflows for full coverage.
5. Zilla Security
Zilla Security is a cloud-based identity governance and administration (IGA) platform designed to simplify identity and access management across hybrid environments. It focuses on automating access reviews, managing user identities, and enforcing security policies like segregation of duties.
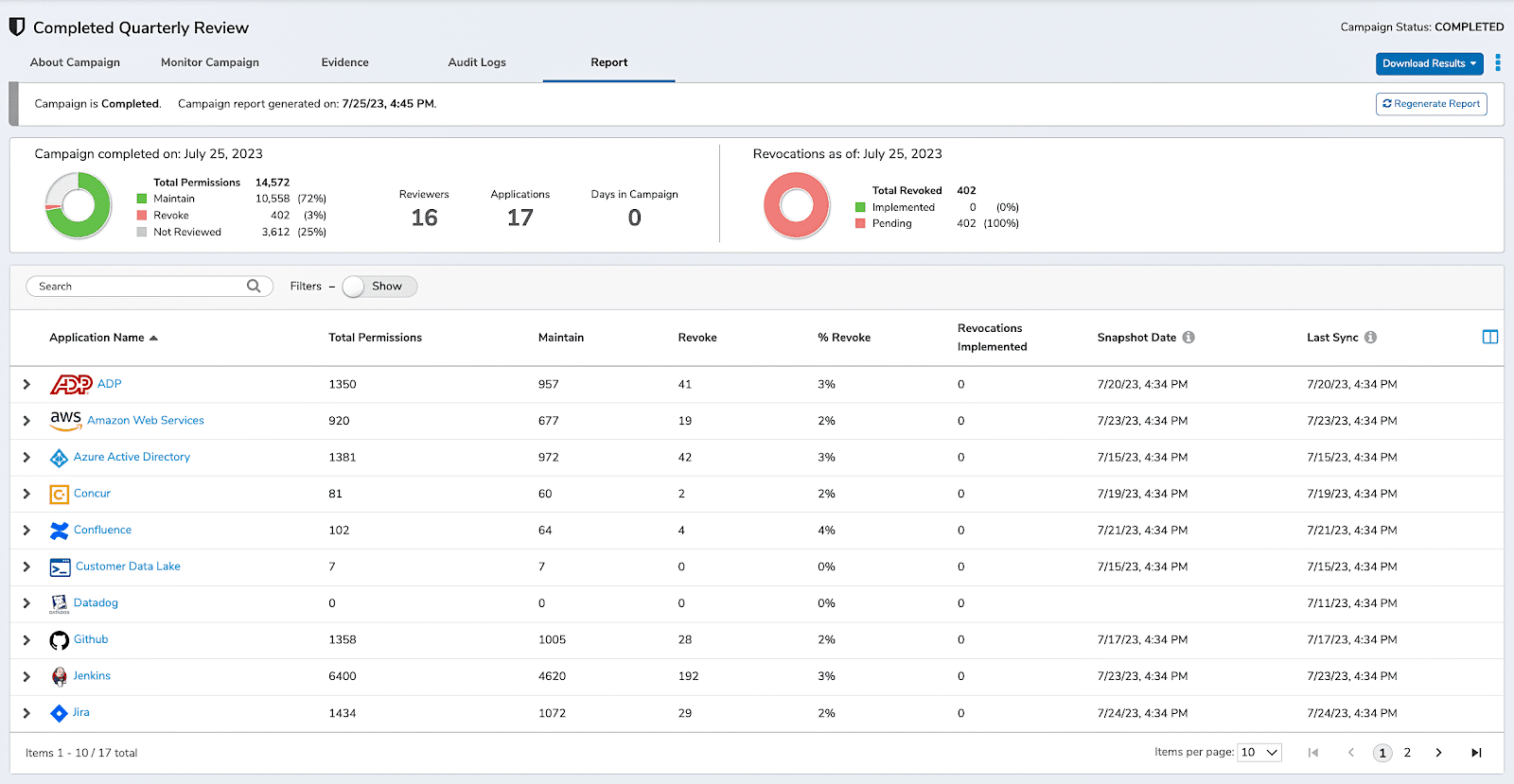
Key Features & Benefits:
- Centralized Identity Management: Streamlines management of user identities, provisioning, roles, and access rights in a single platform.
- Automated Access Reviews: Enables periodic access certification campaigns with audit-ready reporting.
- Policy Enforcement: Supports SoD policies and other compliance rules to reduce risk from excessive or conflicting permissions.
- IT and Security Integrations: Connects with a variety of IT and security tools to provide comprehensive visibility and control.
- User-Friendly Interface: Designed for ease of use by both security teams and business stakeholders involved in access decisions.
Customer Ratings:
Here’s what customers have to say about Zilla:
- Pros: Responsive support team actively addressing customer feedback; improving platform stability and features.
- Cons: Limited dashboard and reporting options; lack of API integrations with BI tools like Tableau or Power BI; manual processes for some access review workflows.
Best for: Mid-sized organizations seeking centralized identity governance with a focus on access risk management and policy enforcement, though it may require additional customization for complex workflows.
6. Zluri
Zluri is a SaaS management platform that helps organizations discover, manage, and optimize their SaaS applications. It offers features for visibility into SaaS usage, spend optimization, and automated workflows for user onboarding, offboarding, and access reviews.
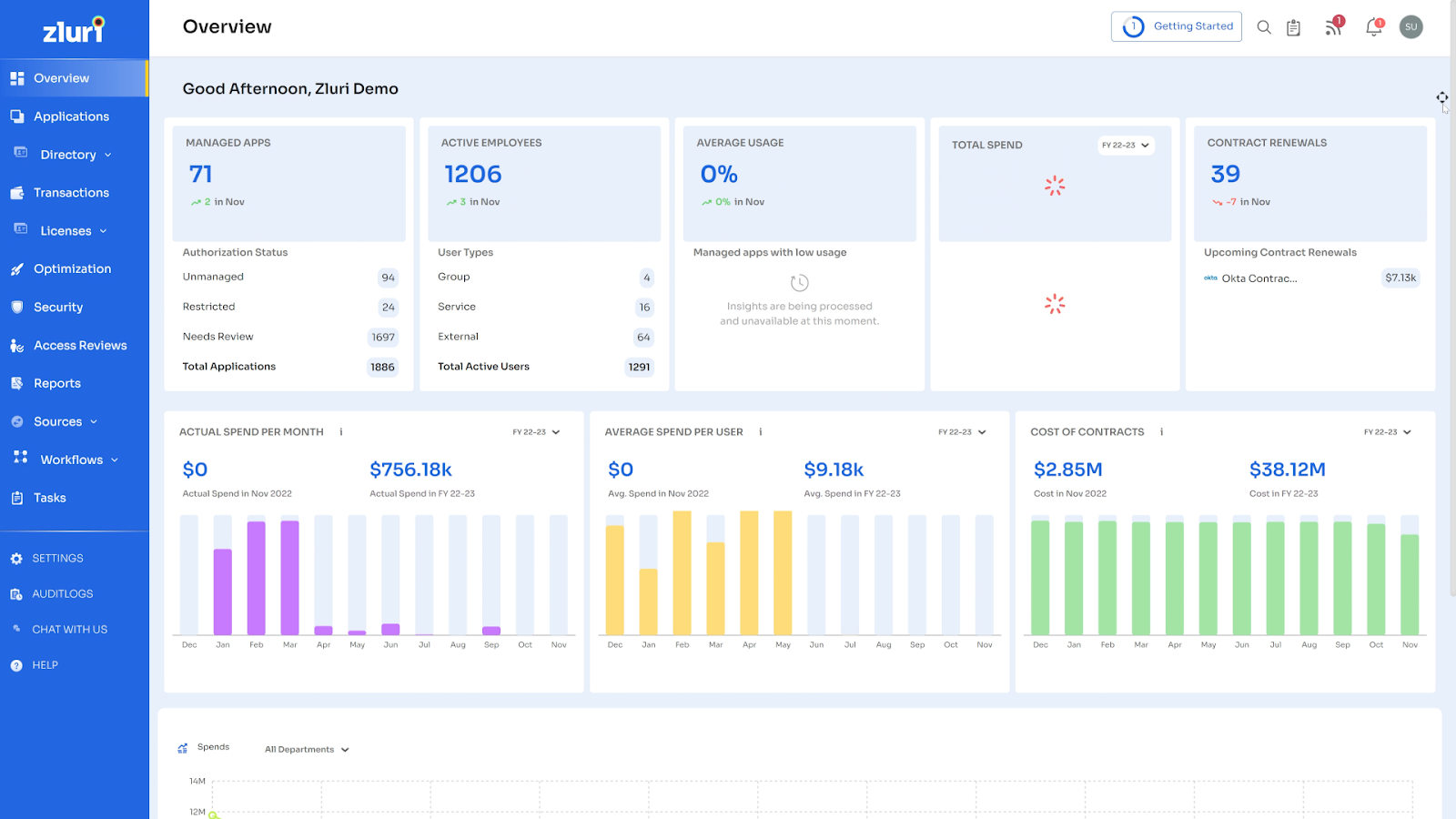
Key Features & Benefits:
- Application discovery and usage tracking: Automatically identifies all SaaS applications in use, including shadow IT, by integrating with SSO, financial systems, and browser extensions.
- Spend optimization: Provides detailed insights into SaaS spending to help control costs.
- Automated workflows: Supports automation of user onboarding, offboarding, and periodic access reviews for SaaS apps.
- Integration ecosystem: Extensive integrations enable connection with a broad range of SaaS applications.
Customer Ratings:
Here’s what customers have to say about Zluri:
- Pros: Extensive number of integrations.
- Cons: Needs more support for a wide range of specific product integrations, time-consuming implementation, and difficulties integrating with certain applications (like NetSuite).
Best for:
Zluri is well-suited for mid-sized organizations focused on SaaS management and optimizing software spend. While it offers automated access review capabilities, its scope is primarily within SaaS environments and may not extend comprehensively to on-premises systems or non-human identity governance.
7. Lumos
Lumos is a SaaS-focused access management platform designed to help IT and security teams discover, manage, and govern SaaS applications and user access. It emphasizes simplifying SaaS visibility and control to reduce risk from shadow IT and unauthorized app usage.
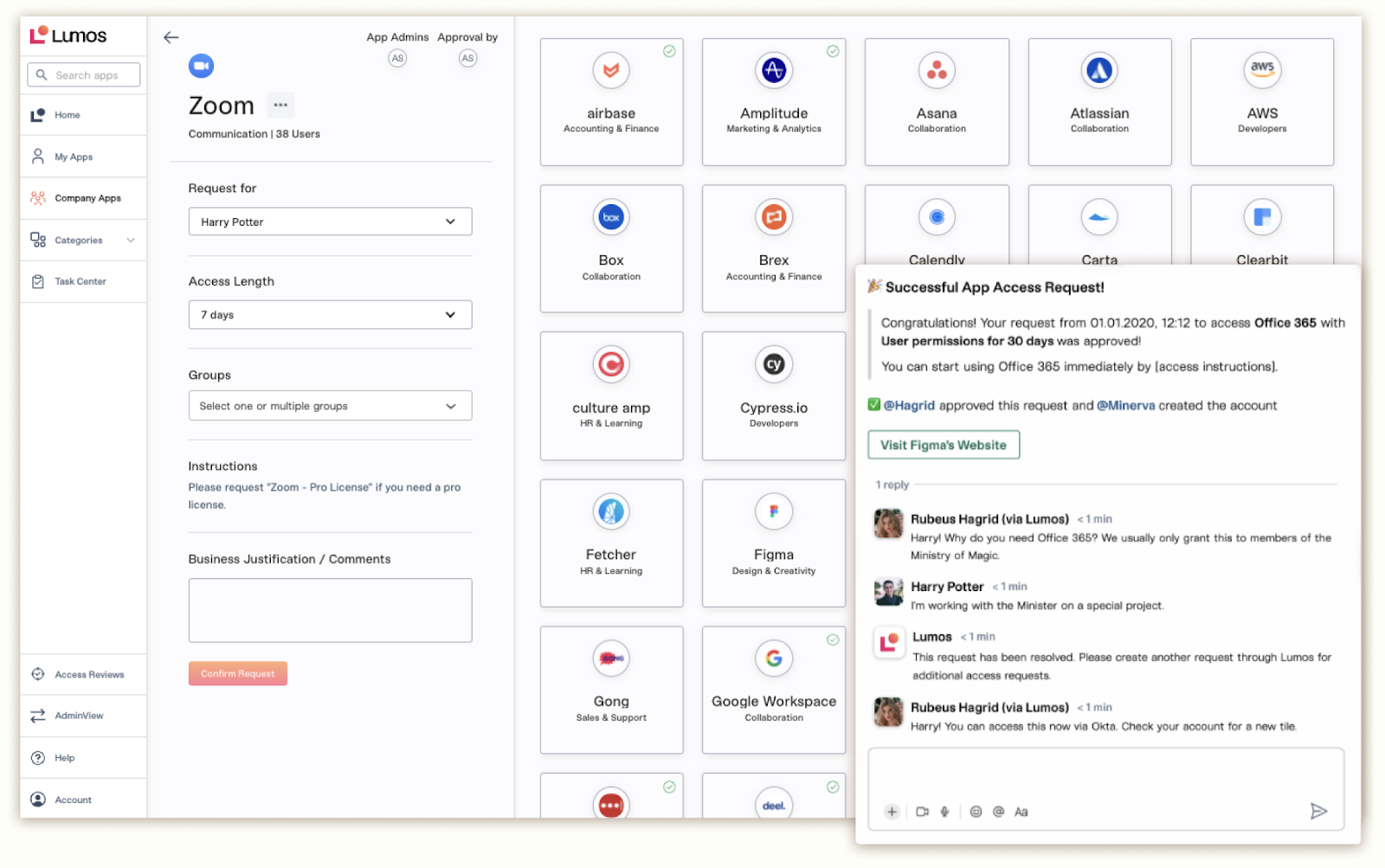
Key Features & Benefits:
- SaaS Application Discovery: Automatically identifies all SaaS apps in use—including shadow IT—to maintain an up-to-date inventory.
- User Access Reviews and Certification: Facilitates periodic access reviews to verify compliance with internal policies and regulations.
- Workflow Automation: Automates onboarding and offboarding processes to ensure timely access provisioning and revocation.
- Spend Optimization Insights: Provides analytics to optimize SaaS license usage and reduce waste.
- Integration Ecosystem: Connects with a range of SaaS platforms and identity providers for streamlined management.
Customer Ratings:
Here’s what customers have to say about Lumos:
- Pros: Responsive to customer feedback, actively improving the product; addresses SaaS access control challenges effectively.
- Cons: Limited integrations with some popular SaaS apps; occasional bugs requiring support intervention.
Best for: Organizations prioritizing SaaS application governance and streamlining SaaS user access management.
Choosing Intelligent User Access Review Software in 2025
Modern identity security demands more than just periodic access reviews. The shift toward dynamic, risk-aware governance calls for solutions that offer centralized visibility, real-time insights, and the ability to act swiftly across all identity types and systems—whether cloud, on-premises, SaaS, or data platforms.
These days, frameworks like Identity Security Posture Management (ISPM) and Identity Visibility and Intelligence Platforms (IVIP) are helping shape how organizations think about access governance, encouraging continuous visibility and smarter automation to keep risks in check without slowing down the business.
Veza’s platform embodies these principles by delivering deep, permission-level visibility through its Access Graph, powering risk-based access reviews that align with business velocity and security policies. This centralized, intelligent approach accelerates decision-making and remediation, reducing the manual burden while enhancing your organization’s overall identity security posture.
Choosing a user access review tool that supports these emerging frameworks is no longer just strategic; it’s essential. For organizations aiming to lead in identity security, Veza offers a robust, forward-thinking solution to unify access governance, meet compliance demands, and drive continuous improvement.
Learn more about how Veza can help your organization conduct more intelligent user access reviews.
About the Authors
This article is a collaborative effort between Quoc Hoang, Principal Product Manager, Competitive Intelligence at Veza; Mariah Brooks, independent consultant specializing in identity security; and Matthew Romero, Technical Product Marketing Manager at Veza.
Together, they bring a balanced mix of market research, technical know-how, and strategic marketing to provide clear, actionable insights into user access review and modern identity security challenges. Their combined expertise supports security teams navigating today’s complex identity governance landscape, helping organizations make smarter, more informed decisions.




