For most CISOs and their teams, answering “Who has access to what?” has become increasingly complex. After so many years and so much invested in process, teams, and tooling, it should be simple. But it’s not.
In today’s enterprise, a single developer routinely accesses code in GitHub, provisions resources in AWS, queries data in Snowflake, collaborates in Microsoft 365, and connects to on-premises servers. Their associated service accounts operate continuously across these same systems. Multiply this pattern by thousands of human users and tens of thousands of non-human identities.
The result is identity sprawl that spans every platform, cloud provider, and system. Yet most security teams address this challenge with tools designed for simpler times, tools that provide visibility into only fragments of the whole identity landscape.
The Business Reality: Digital Success Demands Unified Identity
Step back from the security lens for a moment. How does modern business operate?
Sales teams live in Salesforce but pull customer insights from Databricks. Marketing orchestrates campaigns through HubSpot while analyzing results in Tableau connected to AWS data lakes. Product teams collaborate in Jira, deploy through GitHub to Azure, and monitor performance via Datadog. Finance runs SAP on-premises but increasingly leverages cloud-based analytics tools.
No business unit operates on a single platform. No critical business process stays within one technology boundary. Digital transformation hasn’t just moved businesses to the cloud—it’s created intricate webs of interconnected systems where value flows horizontally across platforms.
Consider a simple business scenario: launching a new product. It requires:
- Market research data from the data warehouse
- Financial modeling in cloud-based planning tools
- Product specs in collaboration platforms
- Code repositories and CI/CD pipelines
- Customer data from the CRM
- Supply chain information from ERP systems
Each step involves multiple identities accessing multiple systems. The business thinks horizontally—”How do we get this product to market?” But if identity security thinks vertically—protecting each silo independently, there’s fundamental misalignment with how businesses create value.
This misalignment isn’t just a security problem. It’s a business velocity problem. When identity security can’t keep pace with business needs, one of two things happens: security becomes a bottleneck that slows innovation, or business units find workarounds that increase risk. Neither outcome is acceptable.
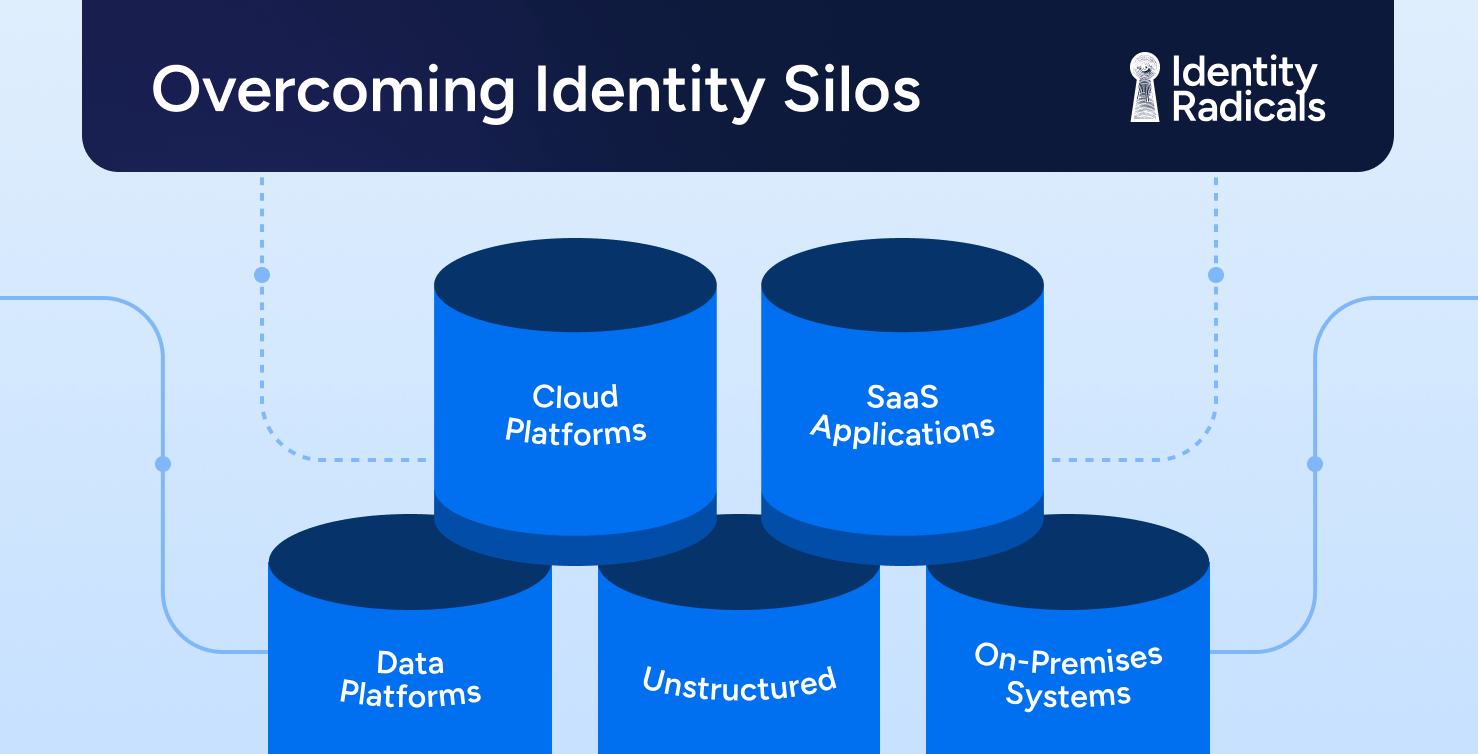
The Five Silos of Enterprise Identity
To understand why unified identity matters, it helps to recognize the five technology archetypes that define modern enterprise infrastructure. Each has evolved its own identity constructs, creating distinct silos with unique challenges:
1. Cloud Platforms (e.g., AWS, GCP, Azure)
- Identity constructs: IAM users, roles, service principals, managed identities
- The challenge: Decentralized teams create accounts, policies, and entitlements outside of central IT guardrails
- The risk: Shadow identities and over-privileged service accounts proliferate unchecked
- Traditional tools: Cloud-native CSPM, CIEM solutions that stop at the cloud boundary
2. SaaS Applications (e.g., Salesforce, Workday, ServiceNow)
- Identity constructs: SaaS-native usernames, groups, role hierarchies
- The challenge: Each SaaS app has its own permission model with inconsistent terminology, and is often owned and managed by a business unit
- The risk: “Entitlement creep” inside business-critical apps that operate outside central IAM/PAM visibility
- Traditional tools: CASB, SaaS security posture management (SSPM) focused on individual apps
3. Data Platforms (e.g., Snowflake, Databricks, Informatica)
- Identity constructs: Database accounts, service accounts, data roles, schema-level permissions
- The challenge: Access spans both structured and semi-structured data with highly granular entitlements, with broad administrative autonomy to data owners
- The risk: Sensitive data exposure to identities managed outside traditional IAM
- Traditional tools: Data governance and catalog solutions with limited identity context
4. Unstructured Content (e.g., Windows file shares, SharePoint, Google Drive, Box)
- Identity constructs: File ACLs, group-based access, sharing links
- The challenge: Shared drives and inherited permissions create sprawling, opaque access paths
- The risk: Orphaned access persists even after employees leave or roles change
- Traditional tools: DLP and file access governance that miss the identity lifecycle
5. On-Premises Systems (e.g., SAP, Oracle ERP, manufacturing/OT systems)
- Identity constructs: Local accounts, domain accounts, role-based entitlements per system
- The challenge: Legacy environments often resist integration with modern SSO/IAM
- The risk: Privileged standing access is rarely monitored consistently with cloud/SaaS
- Traditional tools: Legacy IAM and PAM solutions disconnected from modern platforms
Each silo makes sense in isolation. The problem? Identities don’t respect these boundaries. A single user often has accounts across all five archetypes, while service accounts and machine identities create hidden bridges between them. No single tool can see these connections—yet attackers exploit them every day.
The Silo Problem Is an Architecture Problem
Walk into many security and identity teams and find the same setup:
- A cloud security tool that understands AWS and Azure identities
- A SaaS security platform tracking Salesforce and Microsoft 365 permissions
- A data governance solution monitoring Snowflake and Databricks access
- Legacy IAM managing Active Directory and on-premises systems
- Privileged access tools for infrastructure and servers
Each tool excels in its domain. Each provides a piece of the puzzle. But identities don’t respect these boundaries.
When investigating an incident or conducting an access review, security and identity teams become archaeologists—excavating permissions from half a dozen consoles, correlating IDs across systems, and praying nothing has been missed. It’s not just inefficient; it’s dangerous.
Why Horizontal Visibility Matters
Consider a typical access review scenario. A compliance assurance test or an auditor asks: “What can contractor Sarah access?“
In a siloed world, teams must check:
- AWS IAM for her cloud permissions
- Okta for her SaaS application access
- Active Directory for network shares
- Snowflake for data warehouse permissions
- GitHub for repository access
- ServiceNow for her service accounts
Six systems. Six different permission models. Six opportunities for something to slip through the cracks.
But Sarah doesn’t think in silos. Neither do attackers. They think in paths: “If Sarah’s credentials are compromised, they provide access to this SaaS app, which has an API key to that cloud service, which can assume a role that touches sensitive data in the warehouse.“
The attack path is horizontal. Visibility and intelligence should be, too.
The Non-Human Identity Multiplier
Here’s where it gets worse. For every Sarah, there are dozens of non-human identities—service accounts, API keys, OAuth tokens, workload identities, and now AI agents. These machine identities often have broader access than humans, never take a vacation, and rarely get reviewed.
A single microservice might:
- Pull secrets from HashiCorp Vault
- Read from an S3 bucket
- Write to a PostgreSQL database
- Call three different APIs
- Push logs to Splunk
Tracking its effective permissions across these systems with siloed tools? Nearly impossible. Yet this service account might be the biggest risk—especially if it’s over-privileged, dormant, or worse, forgotten.
From Silos to System Thinking
The answer isn’t more tools. It’s a different approach—one that recognizes identities as the common thread across all platforms.
Think of it this way: In the physical world, an employee badge works everywhere—the lobby, the data center, the executive floor. One identity, multiple access points, centrally managed. Digital identity should work the same way.
A unified approach means:
- One place to ask “Who can access what?”—whether that “who” is human or machine, and whether that “what” is in the cloud, on-premises, or in a SaaS application
- Consistent risk assessment across platforms—over-privilege in AWS is evaluated the same way as over-privilege in Salesforce
- Complete attack paths—from initial identity to final data access, regardless of how many systems sit in between
- Efficient workflows—one access review that covers all systems, not six separate exercises stitched together in spreadsheets
The Architectural Imperative
Modern enterprises are hybrid by default. Multi-cloud by necessity. SaaS-first by choice. On-premises by legacy. Identities flow across all these boundaries every second of every day.
Security architecture must match this reality. That means:
- Modeling identities independent of platform
- Normalizing permissions across different systems
- Building a canonical source of truth for access
- Maintaining real-time accuracy as permissions change
When this is achieved, something powerful happens. Questions that took days to answer become queries. Patterns invisible in silos become obvious in aggregate. Risk concentrations surface automatically. Access reviews transform from archaeology to intelligence.
The Path Forward
Breaking down identity silos isn’t a project—it’s a paradigm shift. It requires recognizing that in a world where identities traverse every boundary, security tools limited to single platforms address only part of the challenge.
The siloed approach:
- Five separate tools for five platform types
- Access reviews that miss cross-platform connections
- Incident response that requires manual correlation across systems
- Risk assessments blind to horizontal attack paths
- Compliance reporting stitched together from multiple exports
In contrast, the horizontal advantage:
- Single source of truth for all identities across all platforms
- Access reviews that reveal the full scope of permissions—from SaaS to cloud to data
- Incident response that instantly traces access paths across platform boundaries
- Risk scoring that understands cumulative exposure across silos
- Unified compliance reporting that matches how auditors actually think
When organizations achieve horizontal, identity-centric visibility:
- Shadow access becomes visible: That service account in AWS that connects to Snowflake, pulls data, and pushes to a SaaS app? Now it’s mapped.
- Toxic combinations surface: The contractor with read-only cloud access who also has admin rights to the data platform? Flagged automatically.
- Orphaned access is eliminated: Deprovisioned users whose database accounts lingered? Found and remediated.
- Investigation time drops significantly: “Show me everything this identity can access” becomes one query, not five separate investigations.
The enterprises that implement this approach gain a fundamental advantage: complete visibility across their entire access landscape. They manage identity risk the way businesses actually operate—horizontally, across all platforms. They answer compliance, security, and audit questions not with spreadsheets and assumptions, but with real-time intelligence.
This represents security aligned with digital reality—comprehensive, efficient, and built for how modern enterprises actually work. Because while attackers don’t respect architectural boundaries, effective identity security shouldn’t be constrained by them either.
Breaking Down Silos: Where to Go Next
Understand the Risk of Silos
Identity sprawl isn’t just technical debt – it’s a velocity killer. Download the State of Access Report to see how five distinct identity silos (cloud, SaaS, data, content, and on-premises) create blind spots that attackers exploit.
See How to Achieve Horizontal Visibility
Traditional IAM and IGA tools stop at silo boundaries. Explore the Identity Visibility and Intelligence Platform (IVIP) Resource to learn how unified identity visibility closes the gaps, maps attack paths, and aligns security with how businesses operate.
Collapse Silos in Your Environment
Don’t just read about it – see it in action. Request a demo of Veza and watch how we unify access visibility across cloud, SaaS, data, and on-prem systems, so you can answer “Who has access to what?” in one query, not six.
About the Author
Mike Towers is the Chief Security & Trust Officer at Veza, where he leads cybersecurity strategy, data protection, and digital trust initiatives. With nearly three decades of global experience across healthcare, biopharma, and technology, Mike has been recognized as one of the industry’s top security executives and an influential voice on identity, resilience, and digital trust. He is a board member, advisor, and frequent industry speaker, helping organizations everywhere secure identity and align security with business innovation.






