For many organizations, NIST compliance is an essential part of a resilient cybersecurity strategy. Its numerous cybersecurity frameworks—from the NIST 800 series to the NIST Cybersecurity Framework (CSF)—are trusted resources for identifying, detecting, and responding to cyber threats.
However, achieving NIST compliance isn’t a simple task. The complexity and comprehensive nature of these standards often pose significant challenges for organizations, especially those with limited resources or expertise. For instance, many organizations struggle with NIST’s identity security requirements, which mandate controlling user permissions and access for compliance.
This article explores what NIST compliance entails, who is required to follow it, and the benefits of following these standards. It provides a detailed NIST compliance checklist, discusses common challenges organizations face, shares best practices, and compares NIST with other popular security frameworks like ISO, SOC 2, CIS, and COBIT.
Whether your organization is just getting started with NIST compliance or looking to update its approach, this guide can offer valuable insights and practical steps to improve your cybersecurity strategy.
What is NIST compliance?
NIST compliance means following security standards and best practices set by the National Institute of Standards and Technology (NIST). These include popular frameworks such as NIST 800-171 for protecting Controlled Unclassified Information (CUI), NIST 800-53 for security and privacy controls for federal information systems, and the NIST CSF for managing and reducing cybersecurity risks.
Ultimately, these guidelines are designed to improve the security and privacy of data and systems and are especially important for organizations dealing with sensitive information.
What is NIST?
NIST, or the National Institute of Standards and Technology, is a non-regulatory government agency within the U.S. Department of Commerce. Although NIST standards are primarily focused on data security for the science and technology industries, they are applicable across various sectors, providing a foundation for strong cybersecurity practices.
What does NIST do?
NIST creates and updates security guidelines and frameworks, conducts research to support the development of new technologies, and provides educational resources to help organizations implement these standards. Its mission is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technologies.
This work is essential for setting benchmarks in cybersecurity and ensuring that organizations can effectively protect their data and systems.
Who needs to comply with NIST?
Depending on the type of organization, compliance with NIST frameworks could be voluntary or mandatory. For instance, federal contractors must comply with NIST 800-171, while federal agencies are required to follow NIST 800-53.
The private sector is also highly encouraged to follow these guidelines to improve their identity security posture and protect sensitive information from cyber threats.
Benefits of being NIST compliant
Being NIST-compliant offers numerous benefits, including:
- Improved security: Better protection against cyber threats by implementing NIST’s security practices.
- Increased trust: Greater confidence from clients and partners, knowing your organization follows recognized security standards.
- Regulatory alignment: Simplified compliance with other regulatory requirements by reducing the complexity of managing multiple frameworks.
- Competitive advantage: Demonstrating a commitment to security standards can set your organization apart.
Overall, organizations that follow NIST standards are typically better equipped to protect their data and maintain a strong security posture.
Types of NIST compliance
NIST’s frameworks help organizations of all kinds meet their cybersecurity goals by providing guidance on activities and outcomes. Here’s a brief overview of the most common NIST compliance frameworks:
NIST 800-171
NIST 800-171 focuses on protecting Controlled Unclassified Information (CUI) in non-federal systems and organizations. This framework was designed to make sure sensitive information stays secure when handled by contractors, universities, and other entities outside the federal government.
It outlines 14 families of security requirements to protect CUI from unauthorized access and disclosure, including access governance, incident response, and media protection.
NIST 800-53
NIST 800-53 provides a catalog of security and privacy controls for federal information systems and organizations. This framework is widely recognized for its depth and breadth, encompassing controls across multiple areas such as access control, audit and accountability, and risk assessment.
NIST 800-53 is designed to improve the security posture of federal information systems by implementing baseline controls tailored to various impact levels (low, moderate, and high).
NIST Cybersecurity Framework (CSF)
The NIST Cybersecurity Framework (CSF) is a voluntary framework that helps organizations—regardless of size, sector, or maturity—better understand, assess, prioritize, and communicate their cybersecurity efforts. The flexibility of the CSF allows it to be adapted to different organizational contexts, fostering better communication and collaboration around cybersecurity risk management.
Additionally, the CSF’s emphasis on continuous improvement helps organizations stay ahead of evolving threats and regulatory requirements.
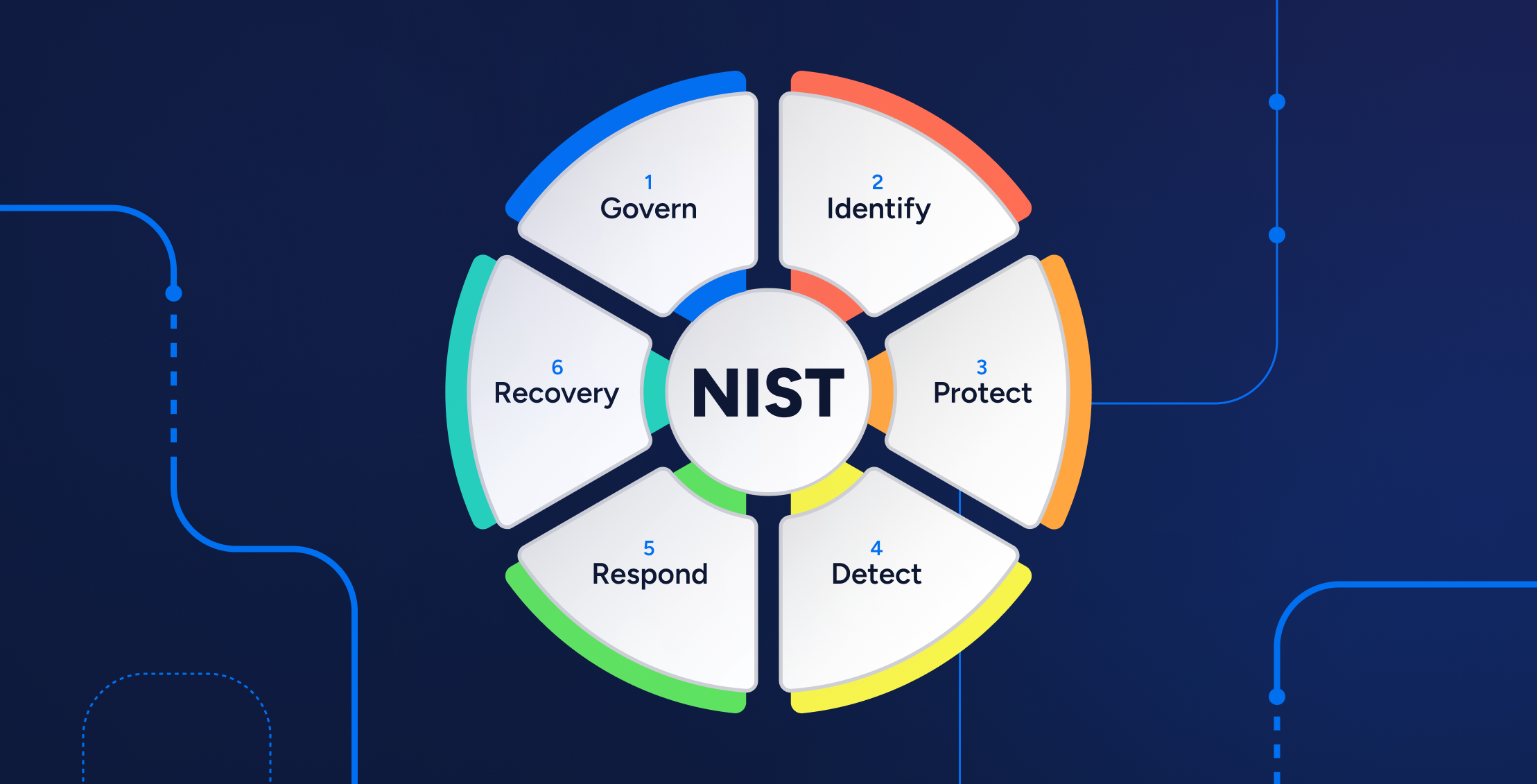
NIST Cybersecurity Framework
First published in 2014, the NIST CSF underwent a significant revision with the release of NIST CSF 2.0 in 2024. This update includes the CSF 2.0 Small Business Quick Start Guide, helping small-to-medium-sized businesses (SMBs) kick-start their cybersecurity risk management strategy. The framework is organized into six primary functions:
Govern
This function establishes, communicates, and monitors the organization’s cybersecurity risk management strategy, ensuring a clear understanding of objectives and responsibilities.
Identify
This function helps organizations understand their cybersecurity risks by creating an inventory of all equipment, software, and data. It involves sharing a cybersecurity policy outlining roles and responsibilities and steps to protect against attacks.
Protect
This function controls access to the network, uses security software to protect data, encrypts sensitive data, conducts regular backups, and updates security software. It also includes safe disposal policies and cybersecurity training for users.
Detect
This function monitors for unauthorized access and investigates unusual activities to quickly identify potential threats.
Respond
This function emphasizes having a plan for responding to incidents, notifying affected parties, maintaining operations, reporting to authorities, containing the attack, and updating policies based on lessons learned.
Recovery
This function focuses on repairing and restoring affected systems and keeping stakeholders informed about response and recovery activities.
NIST’s Guidelines on Zero Trust Architecture
NIST has recently developed comprehensive guidelines on Zero Trust Architecture (ZTA), emphasizing the critical role of identity management in modern cybersecurity frameworks. Special Publication 800-207, “Zero Trust Architecture,” outlines the foundational principles of ZTA, which include:
- Data sources and computing services are considered resources.
- Communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All source authentication and authorization are dynamic and strictly enforced before access is allowed
- The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications and uses it to improve its security posture.
These points underscore the necessity of robust identity verification and continuous monitoring to ensure secure access to resources.In addition to principles, NIST has published several documents to assist organizations in implementing ZTA:
- NIST Special Publication 800-207A, titled “A Zero Trust Architecture Model for Access Control in Cloud Environments,” provides guidance on applying ZTA principles specifically within cloud environments.
- NIST Special Publication 18-35, titled “Implementing a Zero Trust Architecture,” offers practical guidance and best practices for deploying ZTA across various organizational settings.
These publications collectively emphasize that identity management is central to the Zero Trust model, advocating for continuous authentication and authorization.
NIST compliance checklist: How to become NIST compliant
Achieving NIST compliance involves following a set of guidelines designed to improve your organization’s security posture. This checklist will guide you through the essential steps to ensure your systems and processes align with NIST Compliance Standards:
1. Identify and analyze risks
The first step towards NIST compliance is identifying and analyzing the risks your organization faces. This involves conducting a thorough risk assessment to identify potential vulnerabilities in your systems and processes. Document all findings and create a risk management plan that prioritizes the most significant threats to your infrastructure.
2. Implement access control strategies
Effective access control is crucial for maintaining the security of sensitive information. Implement strategies that restrict access to critical systems and data based on the principle of least privilege. Make sure that only authorized personnel have access to specific resources. Use tools and technologies that support access visibility and access intelligence to monitor and manage permissions effectively.
3. Prioritize identification and authentication
Strong identification and authentication mechanisms are vital for securing access to your systems. Implement multi-factor authentication (MFA) to add an extra layer of security. Ensure that all users, both human and non-human, are authenticated before gaining access to sensitive data.
Regularly update and review your authentication protocols to align with the latest security best practices.
4. Create and document incident response plans
An effective incident response plan is essential for mitigating the impact of security breaches. Develop a comprehensive incident response strategy that outlines the steps to take in the event of a security incident. Document the roles and responsibilities of team members, communication protocols, and procedures for reporting incidents. Regularly test and update your plan to ensure its effectiveness.
5. Include physical protection
Physical security is an often overlooked aspect of cybersecurity. Ensure that your organization’s facilities are secure from unauthorized access. Implement measures such as physical access controls, surveillance cameras, and secure storage for sensitive information.
Regularly review and update your physical security protocols to address new threats.
6. Offer security training
Ongoing security training is critical for maintaining a strong security posture. Educate your employees about the latest cyber threats and best practices for protecting sensitive information. Training should cover topics such as authentication, data protection, and incident response.
Encourage a culture of security awareness where employees understand their role in safeguarding the organization’s data.
7. Assess security effectiveness
Assessing the effectiveness of your security measures regularly is crucial for maintaining NIST compliance. Conduct periodic security audits and assessments to identify weaknesses in your defenses. Use the findings to make informed decisions about where to allocate resources and how to improve your security posture.
8. Implement continuous monitoring and maintenance
Continuous monitoring is essential for identifying and responding to security threats in real time. Implement monitoring tools that provide visibility into your network and systems. Review logs and alerts regularly to detect unusual activities and potential breaches. Maintain your security infrastructure by applying patches and updates promptly to protect against known vulnerabilities.
NIST challenges to look out for
While achieving NIST compliance can significantly improve your organization’s security posture, several challenges must be considered during the process. Ultimately, understanding these challenges will help you develop effective strategies to address them.
- Complexity of implementation: NIST guidelines are notoriously comprehensive and detailed, requiring significant efforts to interpret and apply. This complexity can be overwhelming, especially for small and medium-sized businesses.
- Resource allocation: Compliance requires considerable resources, including time, money, and personnel. Organizations may struggle to allocate these resources without impacting regular operations.
- Continuous monitoring and maintenance: NIST compliance is an ongoing process that demands continuous monitoring, regular security assessments, policy updates, and staff training. Keeping up with these requirements can be daunting for organizations with limited cybersecurity expertise.
- Integration with existing systems: Integrating NIST requirements with legacy systems can be challenging. Ensuring compatibility and making necessary adjustments without disrupting operations requires careful planning.
- Managing subcontractors and third parties: Making sure subcontractors and third parties comply with NIST standards adds even more complexity. Coordinating and monitoring these external parties is essential to avoid compliance gaps and potential vulnerabilities.
NIST best practices to know
To achieve and maintain NIST compliance, organizations can adopt several best practices that align with NIST compliance standards.
- Comprehensive identity management: Manage both human and non-human identities (NHIs) across all systems. Keep an inventory of all identities, review access rights regularly, and make sure permissions follow the principle of least privilege. Automate identity provisioning and deprovisioning to reduce the risk of unauthorized access.
- Access visibility and monitoring: Improve your understanding of who has access to what within your organization. Use tools that provide real-time insights into access permissions and detect unusual access patterns. Continuously monitoring access activities helps identify and address potential threats promptly.
- Zero Trust Architecture: Continuously verify the identity of users and the integrity of their access requests, ensuring that trust is consistently earned. To effectively implement zero trust, organizations need granular visibility and control over identities and permissions. This visibility and control helps them continuously monitor access, enforce intelligent access controls, and automate remediation processes.
- Strong authentication mechanisms: Use multi-factor authentication to add extra security for all users. Regularly update and enforce strong password policies, and consider using biometric verification methods. Strong authentication mechanisms are critical for protecting sensitive information from unauthorized users.
- Regular access reviews and audits: Conduct regular access reviews and audits to make sure access permissions are current and appropriate. Periodically verify that users have the necessary access to perform their roles and revoke permissions that are no longer needed.
- Automated compliance reporting: Simplify your compliance reporting by automating the collection and analysis of access-related data. Automated reporting tools can help generate audit-ready reports, making it easier to demonstrate compliance with NIST standards.
- Least privilege access: Implement and enforce a least privilege access model, where users only have access to the data and systems necessary for their roles. Regularly review and adjust permissions to ensure minimal access rights are granted.
NIST vs. ISO vs. SOC 2 vs. CIS vs. COBIT
When comparing NIST compliance to other security frameworks like ISO, SOC 2, CIS, and COBIT, it is important to understand the unique focus and strengths of each.
NIST Compliance
NIST compliance involves adhering to the NIST Compliance Standards, which provide comprehensive guidelines for managing and reducing cybersecurity risks. NIST frameworks, such as NIST 800-171 and NIST 800-53, are widely used by federal agencies and contractors to protect sensitive information.
ISO
The International Organization for Standardization (ISO) offers the ISO/IEC 27000 series, which focuses on information security management systems (ISMS). ISO 27001 is the most well-known standard, providing a systematic approach to managing sensitive company information and ensuring its security.
SOC 2
Service Organization Control 2 (SOC 2) is a set of standards developed by the American Institute of CPAs (AICPA) for managing customer data. SOC 2 compliance is particularly important for service providers, as it ensures that data is managed based on five “trust service principles”: security, availability, processing integrity, confidentiality, and privacy.
CIS
The Center for Internet Security (CIS) provides a set of Critical Security Controls (CIS Controls) that are prioritized and actionable guidelines to mitigate the most pervasive cyber threats. These controls are designed to improve cybersecurity posture by focusing on fundamental and high-impact areas.
COBIT
The Control Objectives for Information and Related Technologies (COBIT) is a framework developed by ISACA for IT governance and management. It provides a comprehensive approach to ensuring that IT is aligned with business goals, delivers value, and manages risks effectively.
Maintain NIST compliance with Veza
Maintaining NIST compliance can be a complex and ongoing process, but with the right tools and strategies, it can also be manageable. With Veza’s access platform, your organization can achieve and sustain NIST compliance.
By transforming how businesses manage access control and permissions for digital identities, Veza ensures secure access across your systems environment for both human and non-human identities. It easily connects to any business system for a full overview of access across your organization so you can implement access control strategies that align with NIST compliance standards.
Monitor and manage permissions with precision with the platform’s access visibility and access intelligence features. See who has access to what, so only authorized individuals can interact with sensitive data, and get essential insights for maintaining continuous NIST compliance and protecting against cyber threats.
At Veza, we’ve simplified the compliance process by automating time-consuming tasks such as quarterly access reviews and providing clear, audit-ready proof of compliance. With the capability to track and respond to changes in access or permissions, Veza’s platform ensures that your organization remains compliant with evolving NIST standards.
Learn more about how Veza can help improve your organization’s security posture, streamline compliance, and protect against identity-based threats.






