Identity Security Posture Management (ISPM)
Move from fragmented identity visibility to continuous access governance.
Veza helps you operationalize ISPM with real-time observability, risk scoring, and automated remediation across your hybrid environment.
Why ISPM? Why Now?
ISPM—Identity Security Posture Management—helps organizations continuously understand, score, and reduce identity risk, rather than react to it after an incident.
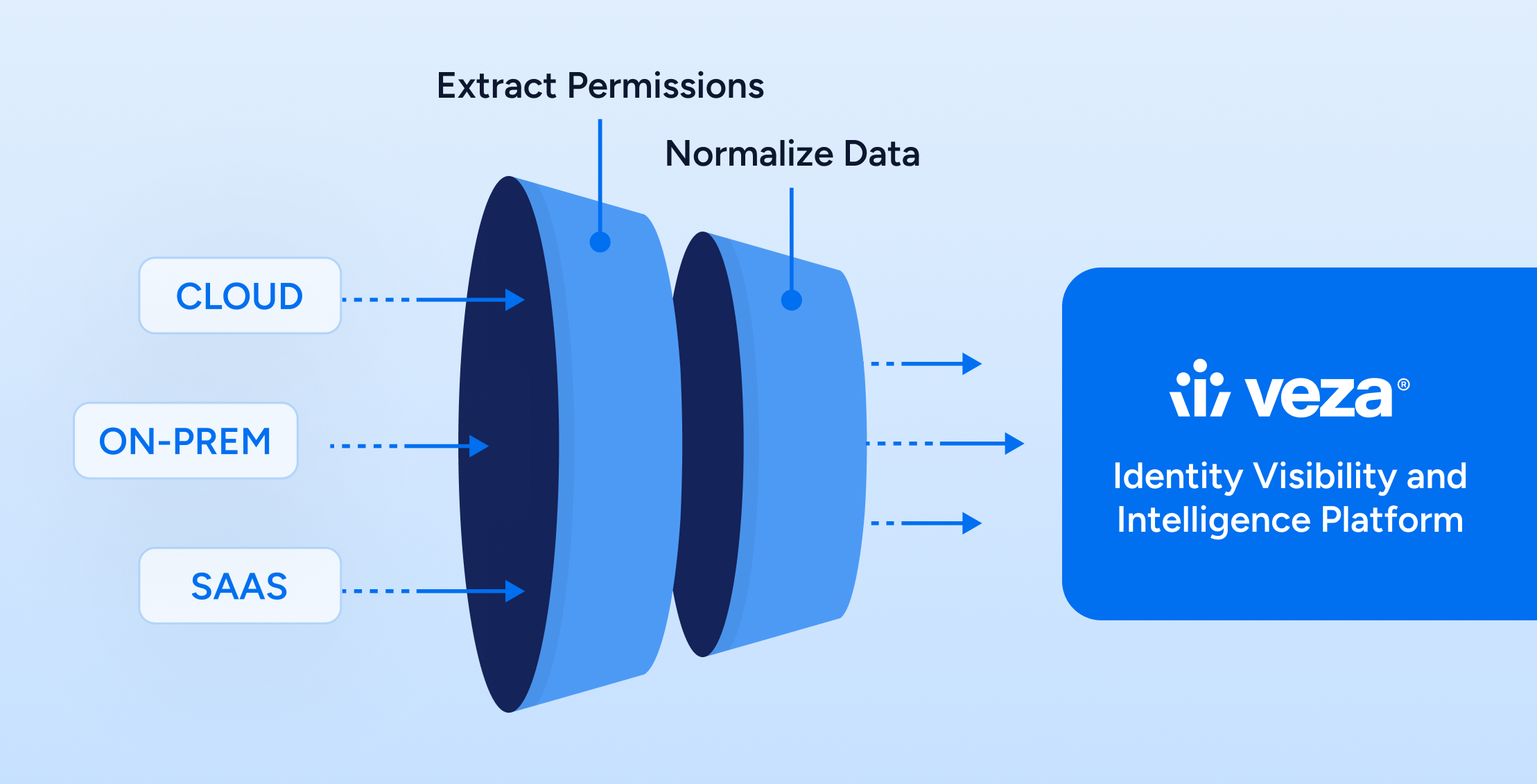
The identity perimeter has overtaken the network perimeter as the primary security boundary. Yet most organizations still rely on fragmented IAM tools that were never built for real-time visibility or non-human identity sprawl.
“For CXOs, ISPM represents a strategic investment in proactive security to reduce risk, provide measurable results, and support zero trust and regulatory initiatives.”
1. Establish Unified Identity Visibility
ISPM Requirement:
Aggregate identity and access data across all systems.
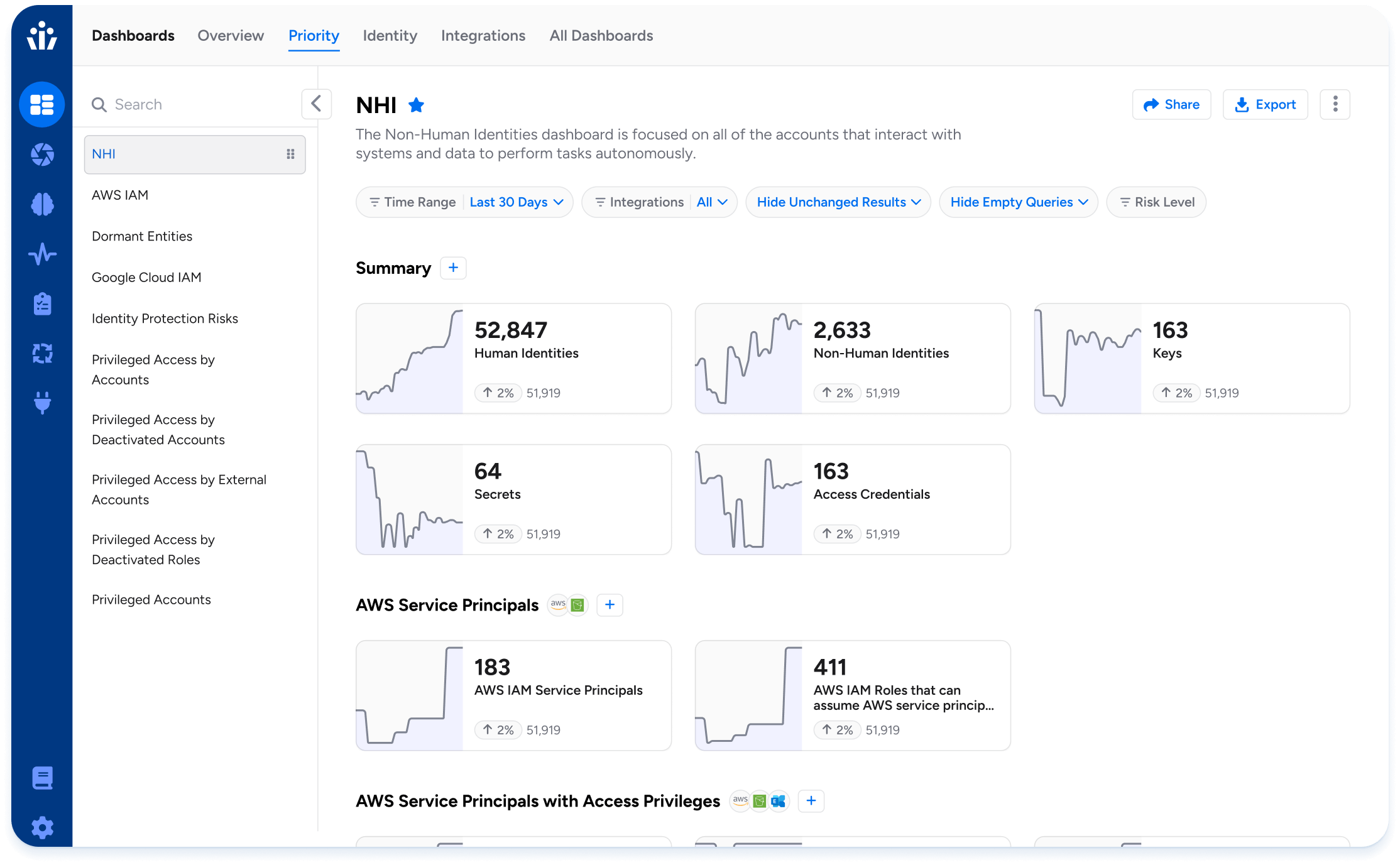
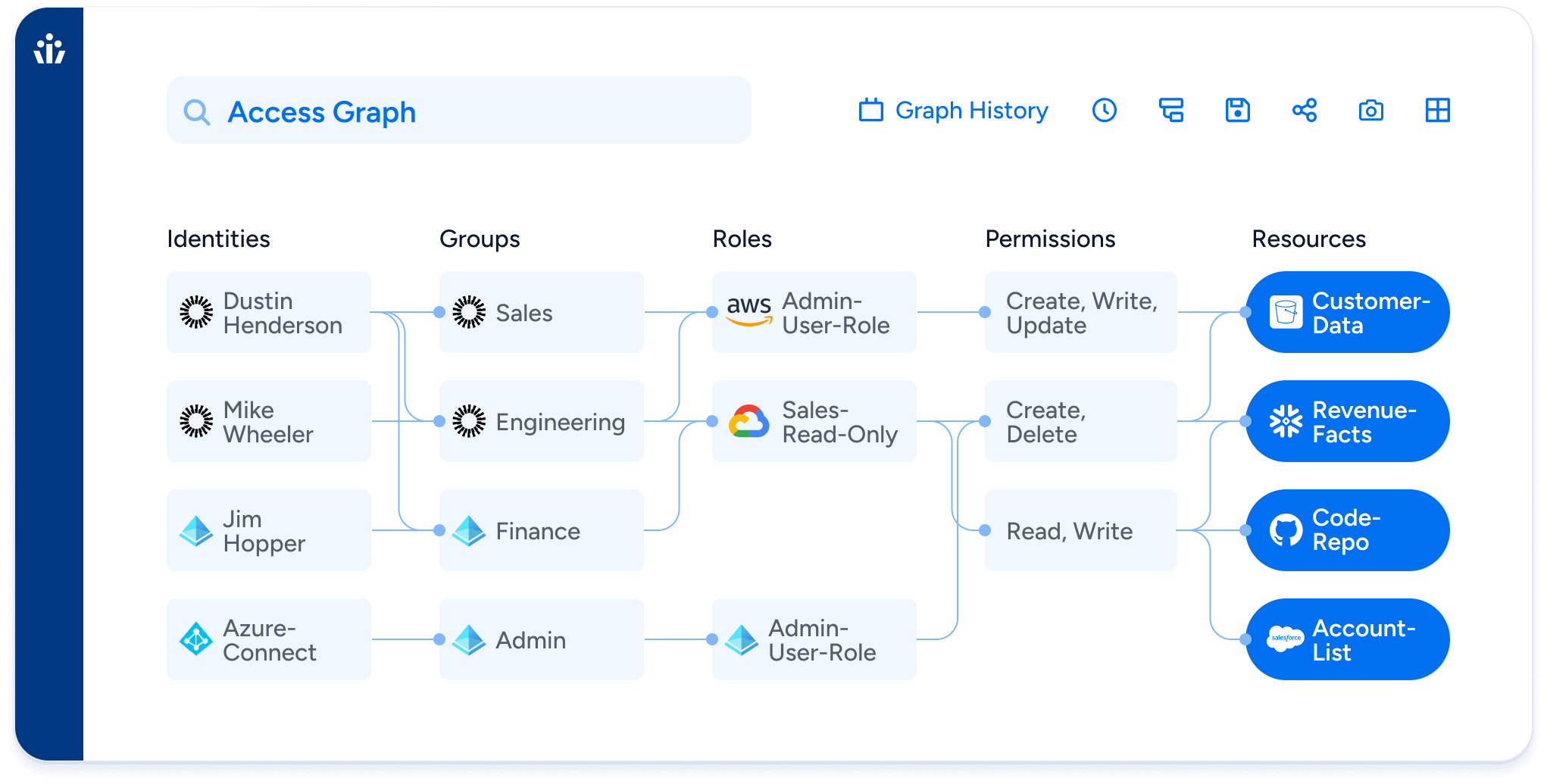
Veza’s Access Graph provides real-time visibility into every identity and what it can access across Active Directory, Okta, AWS IAM, GitHub, service accounts, and more. It connects the dots between user roles, permissions, and actual entitlements.
- Feature Highlight: Access Graph
- Supporting Blog: The Missing Layer in the IAM Stack
2. Continuously Score Identity Risk
ISPM Requirement:
Measure the security posture of identities, not just their existence.
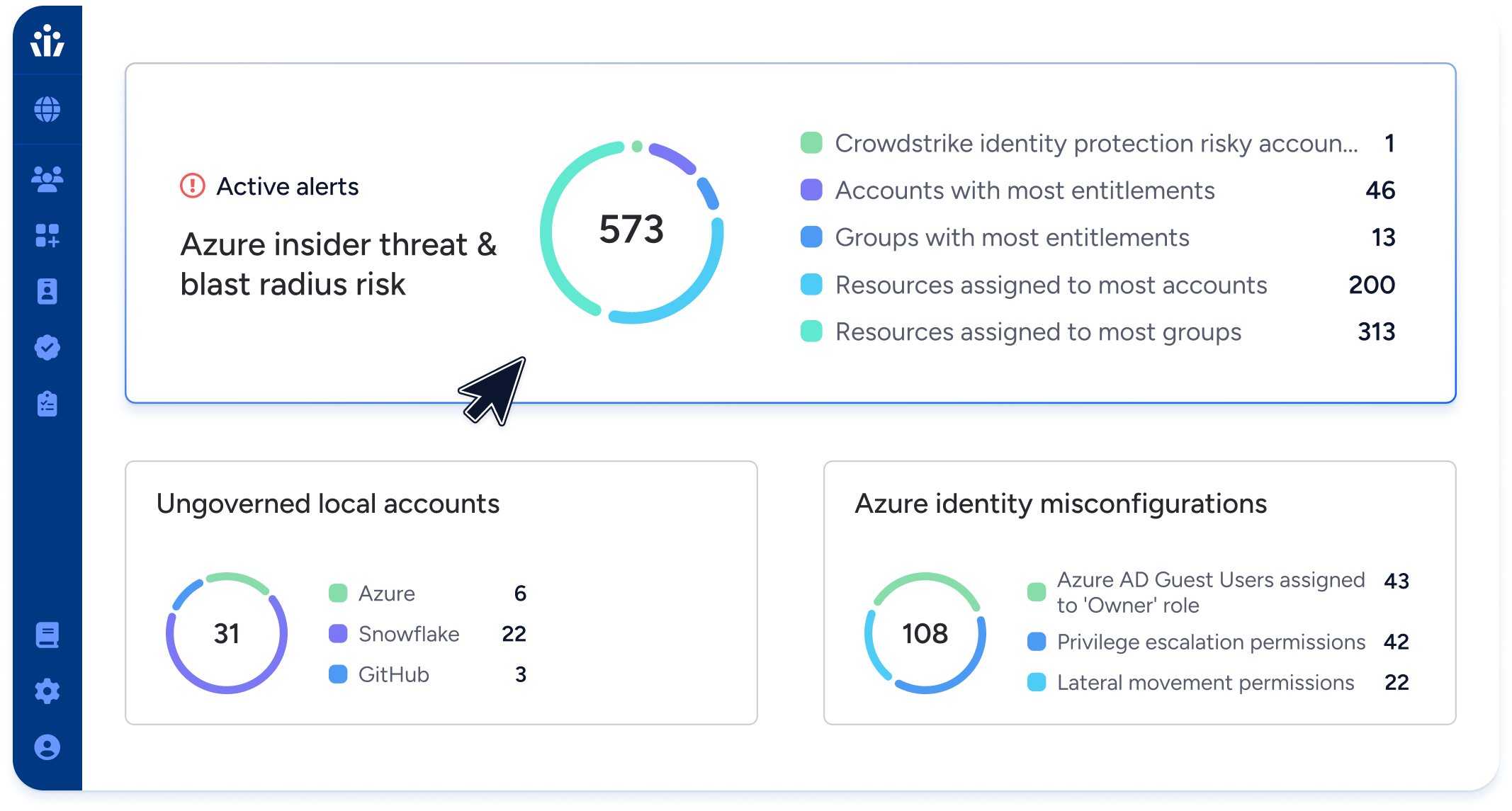
Our risk engine continuously monitors changes in access and evaluates posture in real time. You’ll immediately spot dormant accounts, toxic permission combinations, or deviations from policy.
- Feature Highlight: Next-Gen IGA
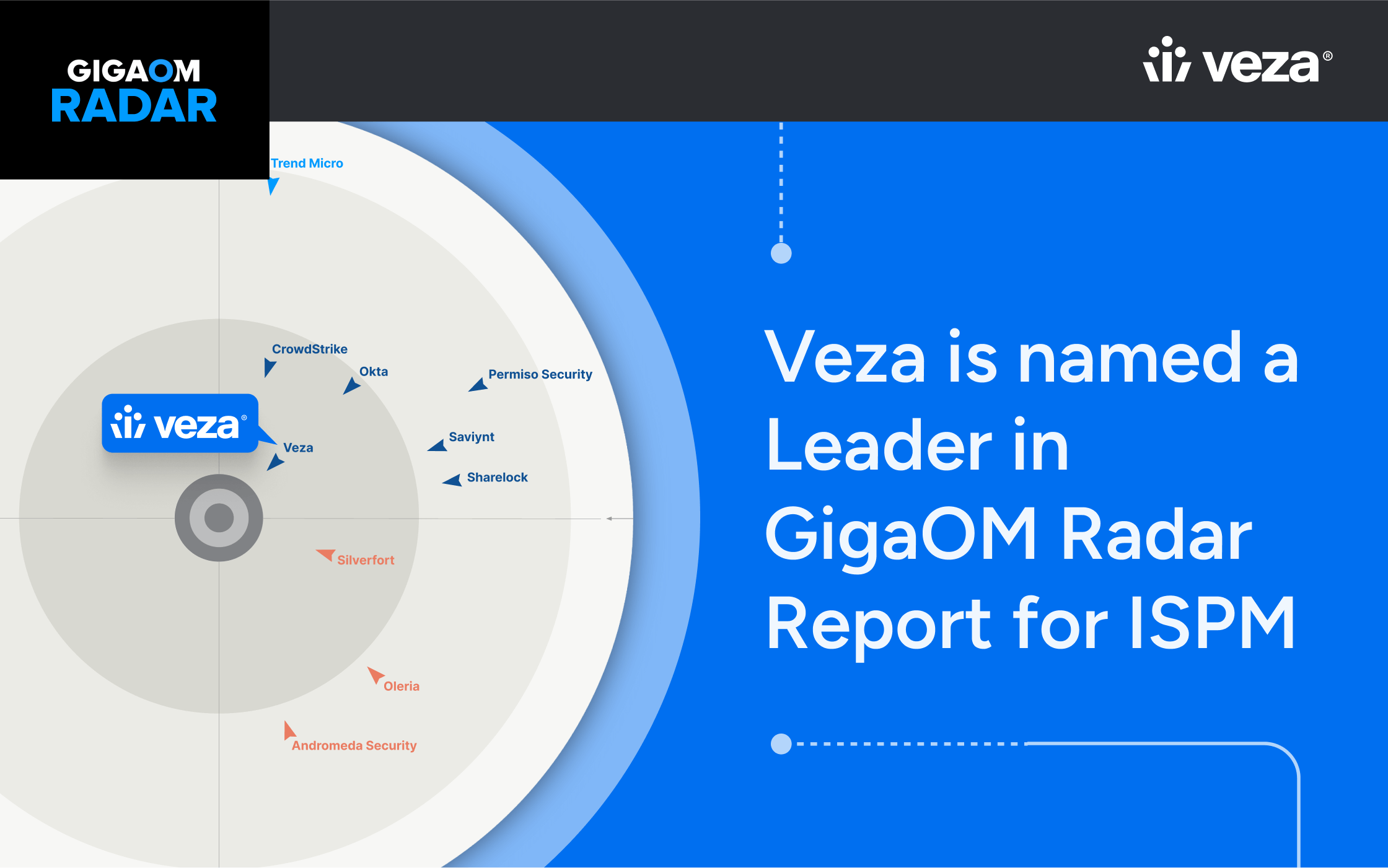
- Supporting Report: GigaOm ISPM Radar 2025
3. Automate Enforcement and Remediation
ISPM Requirement:
Use policy-based controls to reduce over-permissioning.
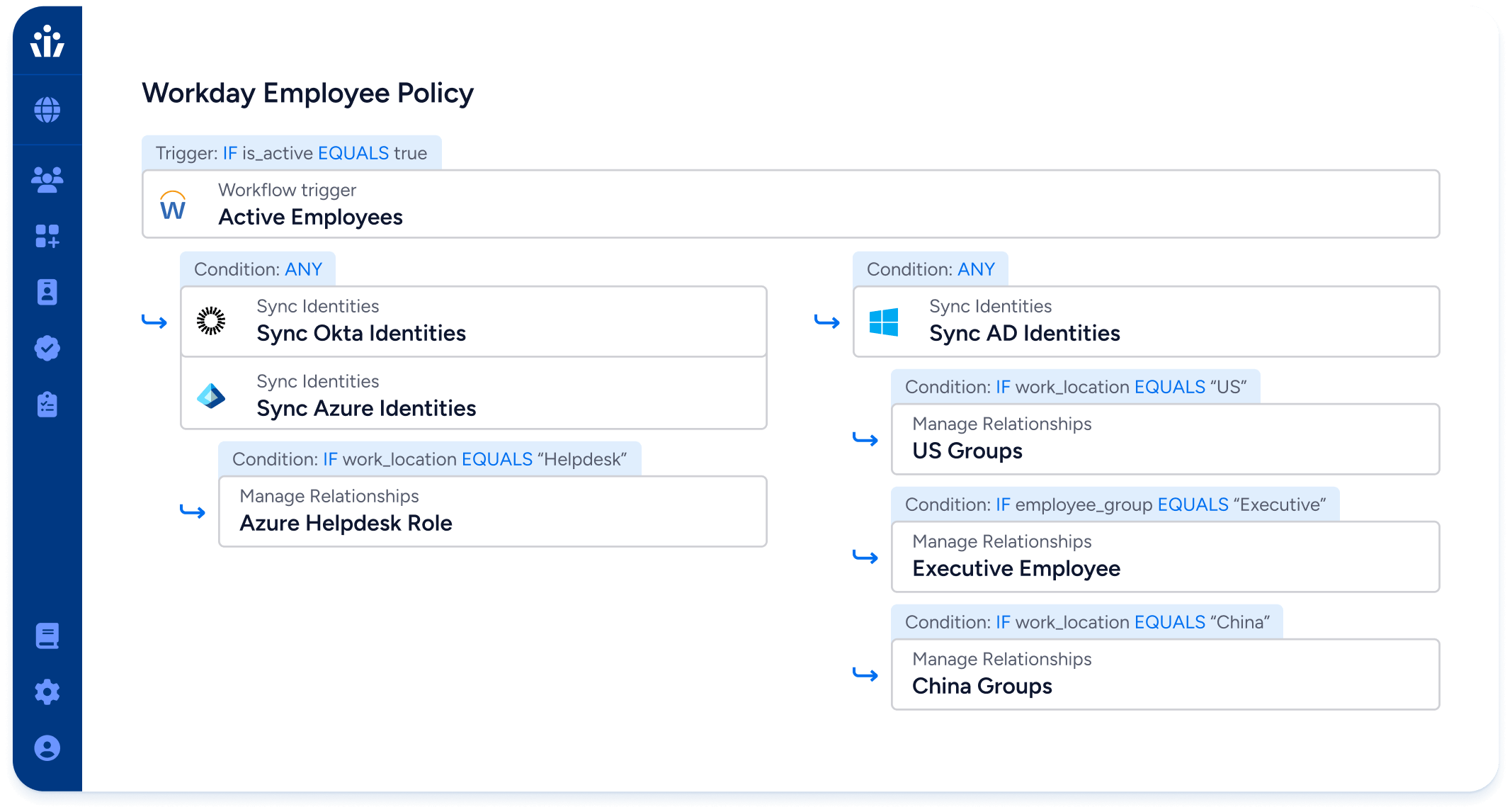
Veza’s Lifecycle Management lets you automate identity reviews and enforce least privilege across both users and systems. It integrates with your IAM stack to close gaps faster, with full audit traceability.
- Feature Highlight: Lifecycle Management
- Supporting Blog: Closing the Identity Gap
4. Secure Non-Human and AI Identities
ISPM Requirement:
Include service accounts, bots, and machine identities in your posture strategy.
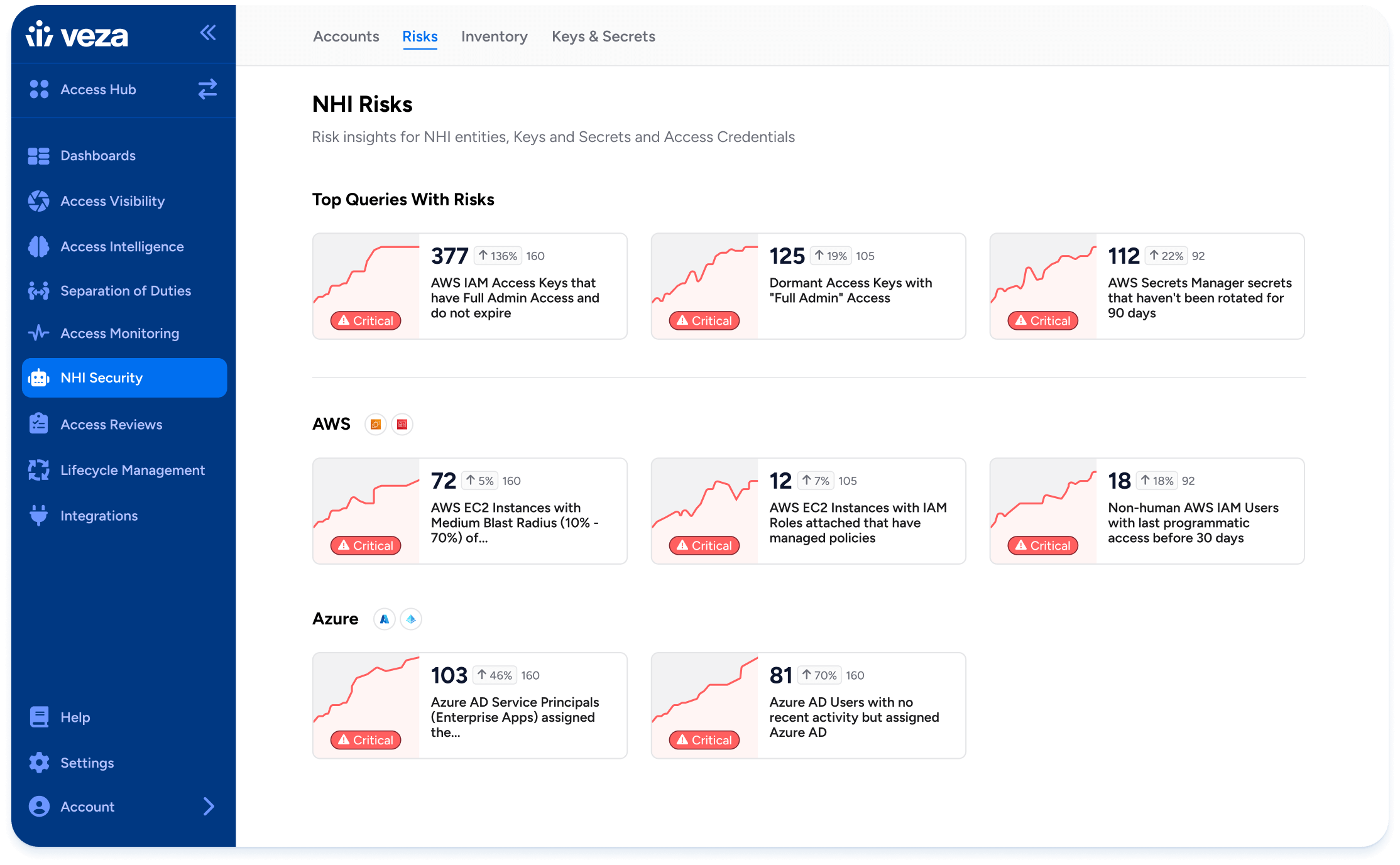
Our platform identifies and governs non-human identities—API keys, AI agents, and service accounts. It ties them back to real entitlements, detects unused or risky access, and supports AI governance.
- Feature Highlight: Non-Human Identity Management
- Supporting Use Case: Agentic AI Security
5. Align with Audit and Governance Objectives
ISPM Requirement:
Provide evidence of access control for internal and external audits.
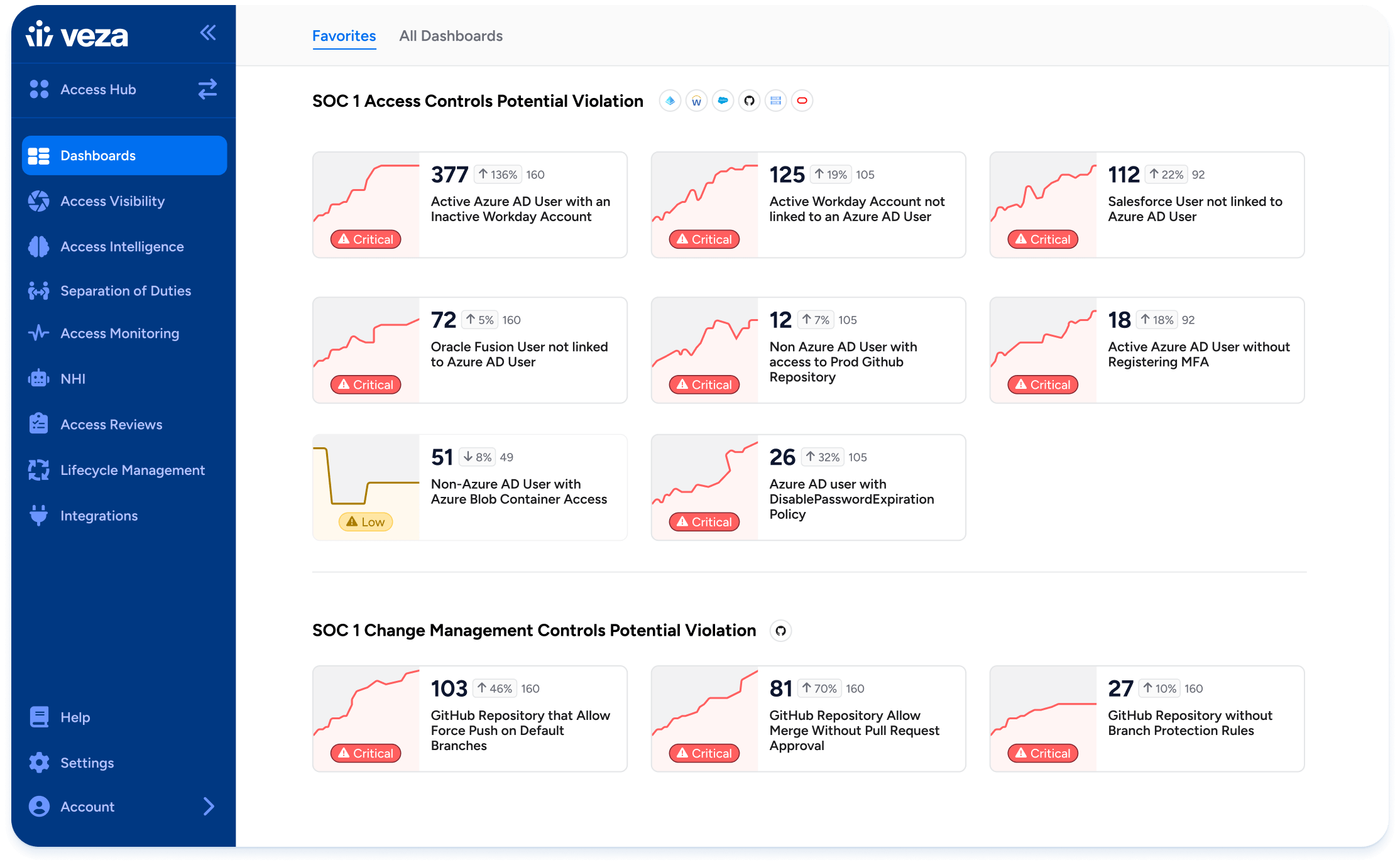
Veza gives you point-in-time and real-time access snapshots. From SOX to HIPAA, ISO 27001, or internal GRC programs, Veza ensures you’re audit-ready at all times.
- Feature Highlight: Access Intelligence
- Supporting Blog: How Veza Strengthens SOC 1 Compliance
| ISPM Requirement | Veza Capability | Value |
|---|---|---|
| Unified visibility | Access Graph | Eliminate identity blind spots |
| Risk posture scoring | Next-Gen IGA | Prioritize high-risk identities |
| Policy-based remediation | Lifecycle Management | Automate least privilege enforcement |
| NHI coverage | NHI Management | Secure AI agents and service accounts |
| Compliance evidence | Audit Reporting | Accelerate audits and reduce cost |