A Checklist for your identity security approach
Intelligent Access for Microsoft Azure
If Microsoft Azure is a core pillar of your environment, your biggest risk isn’t the cloud – it’s who can do what inside it. The control plane spans Microsoft Entra ID for identity and Conditional Access, Azure RBAC with targeted ABAC conditions for authorization, Microsoft Defender for Cloud for posture and workload protection, and Microsoft Purview for discovery, classification, and data governance.
This guide explains Azure security, access control, compliance, and roles in practical terms. It is practitioner-first and outcome-driven: remove standing privilege, right-size custom roles, contain inheritance and group sprawl, and automate evidence. Knowing who has access is table stakes; real control comes from understanding the effective permissions every human and non-human identity can exercise across subscriptions, resource groups, and resources.
Managing access at Azure scale is doable when you can answer one question on demand: who can take what action on which service and which data. For a quick refresher, read The Principle of Least Privilege, Explained.
Is Microsoft Azure secure?
Short answer: Yes – at the platform layer.
Long answer: Security is a partnership.
That’s vendor-speak for “use it wisely.” Microsoft secures the platform; you’re on the hook for how you configure and operate it. Be smart about identity, least privilege, data protection, and monitoring. Use Microsoft’s security tools, but layer your own controls and reviews. If you want the formal model, see Azure security fundamentals.
What Microsoft secures (their side of the shared model)
Microsoft locks down the foundation: physical data centers, custom hardware and firmware, the backbone network, the hypervisor and control plane, and service-level patching with round-the-clock monitoring. Translation: the platform is hardened, updated, and watched. It is solid. It is not a substitute for how you secure your tenants, subscriptions, and apps.
What you secure (your side of the shared model)
You control how Azure is used in your org. That means identity and access, authorization design, data protection, network exposure, and workload posture. In practice, you enforce strong authentication, apply least privilege, encrypt with disciplined key management, segment aggressively, and review continuously. The blast radius is the direct result of your configuration choices.
Day to day, what that looks like – and where gaps creep in. Here’s your checklist:
Start with identities; that’s where most trouble starts. Your admins shouldn’t live in elevated roles; they should borrow them briefly when work demands it. MFA everywhere, Conditional Access without “special cases,” and elevation that leaves a paper trail. If someone breaks glass at 2 a.m., you know who, why, and for how long. That one habit removes an embarrassing amount of quiet risk.
Authorization comes next. Stop thinking in titles and start thinking in scopes. Give people the smallest role at the smallest place; it still works, then use attributes to dodge a zoo of custom roles. Quick gut check: if this identity were compromised, what could actually happen? If the answer is “a lot, everywhere,” keep shrinking until it isn’t.
Check your posture–its the grind where you actually win. New subscriptions should land with the right policies already attached, not added later. Findings need owners and deadlines, or they become wallpaper. Exemptions end by default. If an alert fires and nobody can say what “good” looks like, you don’t have posture, you have settings.
Secrets and data protection stay boring only if you keep them that way. Keys and tokens belong in Azure Key Vault with rotation on a calendar, not on a wish list. If an app can’t survive a key role, that’s a bug to fix, not a reason to skip rotation. Encrypt by default. Nothing sensitive belongs in code, config, or screenshots.
Availability and exposure are where convenience loves to cut corners. Public endpoints should be deliberate and few. Put the important ones behind Azure DDoS Protection, segment networks, and prefer private paths. If you ever hear “it’s just dev,” remember, attackers don’t read your environment labels.
Finally, detection and response is where you buy back time. Centralize the logs, tune the noise, automate the obvious actions, and rehearse when nothing’s on fire. Treat your runbook like code, not lore. For operations at scale, use Microsoft Sentinel for SIEM/SOAR and Microsoft Defender XDR for XDR.
They integrate, but they solve different jobs.
Why this matters (your outcomes)
Even with a hardened platform, the real blast radius comes from who can do what. Inherited permissions, non-human identities, and stale roles quietly expand risk. The next sections go deep on RBAC vs ABAC, time-bound privilege with PIM, and continuous access reviews, so you can shrink effective permissions without breaking the business.
How secure is Azure?
Azure is built as a robust cloud platform, but like any platform, it has its shared responsibility model. Microsoft secures the underlying infrastructure, and you secure how you configure and use it.
Microsoft takes care of the physical security, the hardware, and the networks. They also manage the hypervisor and apply patches regularly.
But the real security question is always about who can do what in your environment.
That’s where your configuration comes into play.
In the next sections, we’ll break down how to manage role-based and attribute-based access control, use time-bound privileges, and run meaningful access reviews. That way, you can shrink your risk without adding complexity.
What is Azure security architecture?
Think of Azure security architecture as the map, not the maze. It shows how to design, implement, and run controls that actually hold up in production: identity and access, authorization, network boundaries, data protection, and threat detection. Microsoft’s security start here guide lays out the official patterns; use it as a baseline, then tailor it to how your teams ship and operate.
In practice, a durable architecture lines up a few planes that work together:
Identity and access: Entra ID policies, Conditional Access, and elevation that is time-bound and auditable.
Authorization: RBAC at the smallest scope that works, with ABAC where it cuts sprawl.
Network and exposure: private by default, segmented routes, deliberate public entry points.
Data protection: classification that drives controls, keys in a vault, and encryption by default.
Threat visibility: posture management that prevents drift, logging that arrives with the resource, and a response you can rehearse.
The point is clarity. When you can answer who can do what, where traffic can flow, what data is sensitive, and how you respond when something breaks, you have an architecture. Everything else is settings.
Challenges with Azure security
Azure gives you incredible control, and that is the problem. The more knobs you get, the easier it is to create a system where no one can say with confidence who can actually do what.
Complexity that compounds
Azure’s granularity is a gift until it is not. Role assignments inherit down management groups, subscriptions, resource groups, and resources. Group nesting hides who is actually in scope. Custom roles multiply to solve edge cases, then drift as services evolve. A harmless-looking group grant can become broad DataActions three layers down. If you have ever wondered why a user can read or delete data when their title suggests they should not, this is usually why. For the precise difference between Actions and DataActions, Microsoft’s role definitions explain the model clearly: Azure role definitions.
The fix starts with clarity. Assign roles at the smallest place where they still work. Keep custom roles rare and documented. Review effective permissions, not just the assignments you meant to make. When exceptions are necessary, put an expiry on them so “temporary” does not turn into “forever.”
Scale that outgrows human review
Most identities in cloud estates are not human. Recent reporting shows machine identities can outnumber people by double digits in typical environments, and can reach 80 to 1 in extreme cases. These accounts hold durable rights, do not change jobs, and rarely expire.
That imbalance breaks manual review. Group lookups and one-time audits miss where power actually sits: the effective permissions assigned to service principals and automations across subscriptions and resources. The sources and mechanics are covered in Identity Attack Surface Analysis and Invisible keyholders: The Importance of non-human identity management. For broader trend data, use State of Access 2024.
The practical takeaway is simple. Treat non-human identity hygiene as table stakes. Make issuance explicit, scope rights to the smallest place they work, rotate credentials on a schedule, and expire what is not used. If you cannot answer who can do what for these identities, you cannot prove risk down or close incidents with confidence. simpler and less time-consuming.
Collaboration that never ends
Azure makes cross-tenant work easy, which is why guest access lingers. A vendor needs a week, a partner needs a month, a project slips, and those invites become part of the furniture. External identities inherit roles, pick up broad scopes, and extend your blast radius beyond your walls.
The fix is lifecycle, not heroics. Treat every guest as temporary. Issue access through a package with approvals and an expiry. Scope it to the smallest place it still works. Apply Conditional Access for guests. Review it on a schedule and remove what is not used. If you need the mechanics of external collaboration, Microsoft’s B2B overview is a good baseline.
Plain English: make external access deliberate, time-bound, and easy to end. If you cannot say which guests still need what, you are hosting strangers in your house.
Configuration drift by default
Drift is not an event. It is the slow slide from “how we meant to run” to “how it actually runs.” New subscriptions appear without the right policies. Exceptions stack up. Alerts get noisy, so teams mute them. None of that is malicious. It is how busy systems age unless you make maintenance boring and automatic.
Start at the top of the tree. Put policy assignments in management groups so every new subscription lands with guardrails already on. Treat policy as code. Initiatives live in version control. Changes ship through pull requests. Deny what must never happen. Use DeployIfNotExists for the things you expect to see but often forget to configure.
Tackle exemptions the same way you treat production changes. Each one has an owner, a reason, and an expiry. The default is to end. If an exemption is still needed, it is reapproved with eyes open.
Make drift visible. Baselines are documented and testable. New resources trigger checks as part of deployment. Findings have owners and deadlines, not just dashboards. When the system rolls forward, your guardrails roll with it. That is what “boring and automatic” looks like in practice.
Standing privilege everywhere
It is always faster to grant a high scope role now and “fix it later.” Later rarely arrives. The result is admins who live in elevated roles, service principals with wildcard rights, and a production environment that relies on trust instead of guardrails. If you want the business case in plain numbers, this breakdown of the cost of over-provisioned access shows how waste and risk travel together: The hidden cost of over-provisioned access.
Fix the habit, not just the incident. Make admin something people borrow for a short window, with approvals and MFA, and then give it back. Keep everyday accounts low. Put emergency access behind break glass with strict controls and regular tests. If a role must be powerful, make it eligible, not active, and require a ticket to light it up.
Treat machines like people with better memory. Keep service principals narrow in scope. Use managed identities where you can. Rotate secrets on a schedule. Remove rights that are not used. If an automation needs broad access for a one-time job, give it the access for the job and then end it.
Review what is actually happening, not what you intended. Look at effective permissions. Retire roles that no longer match how the system works. When you see “Owner at subscription” or “Contributor everywhere,” replace it with smaller roles at smaller scopes.
Standing privilege is a choice. Make a different one, and the blast radius shrinks.
Visibility gaps that stall remediation
Most enterprises cannot tell you the effective permissions each identity holds across systems. You can list assignments, but that is not the same as knowing what a person or service can actually do after inheritance, group nesting, conditional policies, and data actions take effect.
The averages are not comforting. Identities can carry roughly 1,400 permissions on paper, and a single workforce account is often surrounded by many more machine identities with durable rights. At that scale, manual reviews collapse under their own weight. Tickets pile up. Incidents take longer to scope. The blast radius stays unknown until something breaks.
This is where Identity Security Posture Management (ISPM) helps. Treat effective permissions as inventory, not an afterthought. Make visibility continuous and policy-driven instead of ad hoc. If you want a practical buyer’s lens on what ISPM should deliver — inventory, risky entitlement detection, review workflows, and proof on demand – this guide is a useful frame: ISPM Buyer’s Guide.
Close the gap by making visibility a routine. Onboard new subscriptions and resources to logging at creation time. Run access reviews that remove unused and high-risk access, not just check a box. Most of all, measure progress in plain terms that matter to operations: fewer standing privileges, fewer high scope roles, and faster time to prove impact when an account is compromised.
Why this matters in 2025
Attackers do not break in as often as they log in. Compromised credentials remain a leading way breaches start, as summarized in Verizon’s 2025 Data Breach Investigations Report. What happens next depends on what that identity can actually do. Keep effective permissions small, and the impact stays small. At the same time, the dollar stakes remain high, per IBM’s Cost of a Data Breach 2025, which is why shrinking permissions and being able to prove it is operationally mandatory.
Where Veza helps
Veza turns Azure’s mesh of assignments, groups, conditions, data actions, and scopes into clear answers to who can do what. It maps human and non-human identities, surfaces standing privilege, and highlights risky inheritance you forgot about. Reviews focus on unused and high-risk access, not paperwork. Changes are right-sized rather than blunt. The result is practical: smaller effective permissions, faster incident scoping, and audit evidence that appears as a byproduct of how you operate.
How does Microsoft Azure approach compliance?
Azure provides documented controls, attestations, and product features mapped to common frameworks. The jumping-off point is Microsoft’s Azure compliance library, which lists certifications, responsibilities, and service-level guidance you can hand to assessors.
What is Azure governance and compliance?
Governance is how you run Azure: policies, processes, and technical guardrails that keep environments aligned to security, compliance, and operational standards. Compliance is meeting external obligations and proving it with evidence. For a plain-language primer that pairs with Microsoft’s docs, see What is Access Governance? For the data side, Microsoft’s What is data governance? sets the context well.
Is Microsoft Purview part of Azure?
Microsoft Purview is Microsoft’s unified data governance platform. It integrates tightly with Azure but also spans on-prem, multicloud, and SaaS, covering discovery, classification, lineage, and policy enforcement. In practice, Purview gives the data context your security and compliance teams need to decide which controls apply and to prove they are enforced.
Challenges with Azure compliance
Practical moves that help auditors and operators
Anchor your control set to Azure compliance artifacts and map each control to a policy, pipeline check, or playbook.
Put policy at the management group level so new subscriptions inherit guardrails on day one; manage initiatives as code and ship changes with pull requests.
Treat data governance as part of security. Use Purview to classify data and drive controls such as encryption, retention, and access policies.
Make access to evidence routine. Capture effective permissions for human and non-human identities, run periodic access reviews, and expire exceptions by default.
Keep an audit shelf: store policy assignments, exemption justifications with expiry, access-review results, and incident test logs so evidence is ready when asked.
The point is clarity. When you can answer who can do what, where traffic can flow, what data is sensitive, and how you respond when something breaks, you have an architecture. Everything else is settings.
What is Azure access control?
Azure access control is about setting up rules and tools in the Azure cloud so that only the right identities can access your data and services. Azure does this mainly through two systems: Azure Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC).
RBAC allows you to manage access according to jobs or roles, such as manager or technician, and list what each role can do. ABAC adds another layer of complexity by considering other factors, like the time of day or the location of the person trying to access the data, before allowing access.
What are the types of RBAC controls in Azure?
Azure RBAC provides three primary types of roles: Owner, Contributor, and Reader. These roles define the level of access users have to Azure resources. Additionally, there are numerous built-in roles tailored to specific Azure services, and custom roles can be created to meet specific access requirements.
What is the difference between Azure RBAC and IAM?
Azure RBAC is a specific feature within Azure’s broader Identity and Access Management (IAM) framework. While RBAC focuses on managing user access and permissions through roles, IAM encompasses a wider range of identity services, including authentication, authorization, and the management of user identities and their permissions.
What is Azure RBAC and ACL?
Azure access control is how you decide who can do what across subscriptions, resource groups, and resources. The core is Role-Based Access Control (RBAC), with Attribute-Based Access Control (ABAC) conditions for added precision, where it helps. Start here: Azure RBAC overview and ABAC conditions in Azure.
RBAC in Azure vs directory roles
Azure has two planes of admin: Azure RBAC for resource authorization and directory roles for tenant-level administration in Entra ID. Keep them separate, and avoid granting tenant-wide directory roles to solve resource-level problems. Microsoft’s mapping is here: RBAC and directory admin roles.
RBAC vs ACLs (where each fits)
RBAC governs actions on Azure resources. Some data planes add Access Control Lists (ACLs) for file- or object-level decisions. A common example is Data Lake Storage Gen2, which layers POSIX-style ACLs on top of RBAC. Use RBAC for “can this identity manage or read this storage account or container,” and ACLs for “can this identity read this specific folder or file.” Reference: Access control in Azure Data Lake Storage.
Challenges with Azure access control
In practice: use RBAC to answer “who needs what at the smallest place it still works,” layer ABAC where it reduces role sprawl, keep directory roles out of resource problems, and use ACLs for data-plane precision when the service supports them.
What are Roles in Azure?
In Azure, roles define what actions an identity can perform and where. Think of them as job functions with a permission set: view data, change settings, deploy resources, delete, and so on. Azure ships many built-ins, and you can create custom roles when you truly need a tailored set. For a clear catalog of what exists today, Microsoft’s reference is the best source: Built-in roles for Azure RBAC.
Roles help teams keep access aligned to work, but only if you stay disciplined about scope (assign at the smallest place it still works) and intent vs. effect (verify what the role actually enables after inheritance and data actions).
Challenges with Azure roles
In practice: start with built-ins, keep custom roles rare and versioned, assign at the lowest workable scope, and regularly confirm effective permissions. If you want a compact, operations-minded checklist for tying roles to compliance evidence and reviews, this primer is useful: Access Control Compliance Guide (2025).
Role problems do not fix themselves. You need a simple way to see what a role is for, where it applies, and what it can actually do after inheritance and DataActions.
Use the tracker below to make intent explicit, surface write paths, and set a review cadence you can hold teams to. When the table is current, “we think this is read only” becomes “we know exactly what it enables,” with owners and dates to prove it.
Azure role hygiene tracker (template)
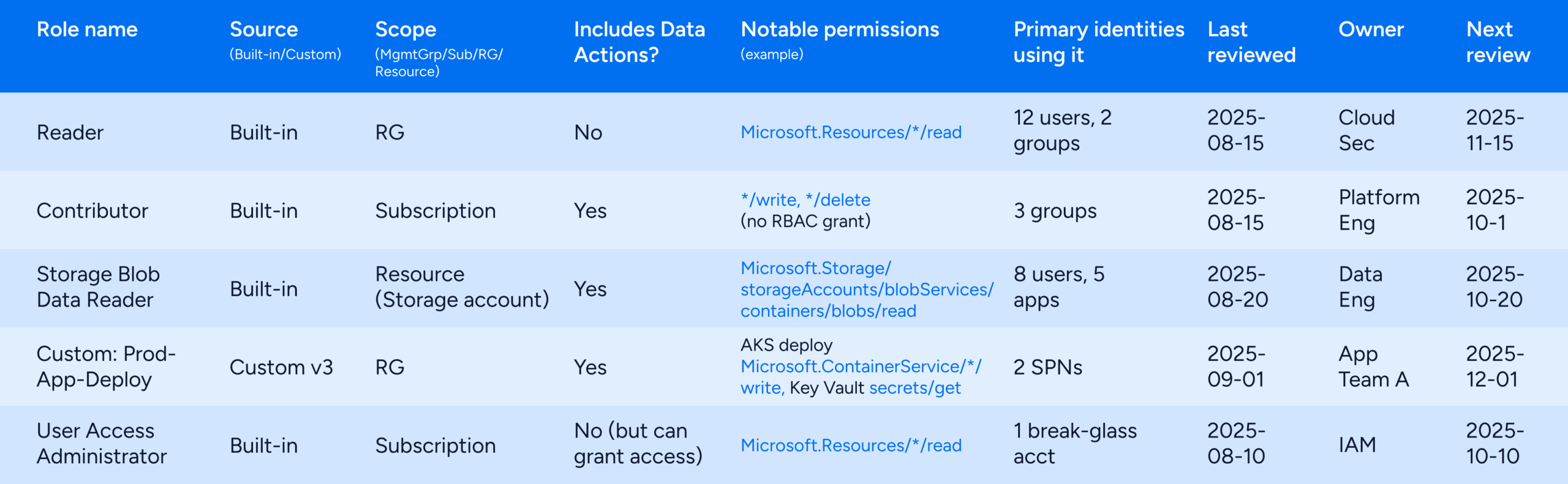
How to use this table
- Source: prefer built-ins; keep customs rare and versioned (v1, v2, v3).
- Scope: assign at the smallest place where it still works. Avoid subscription “just to unblock.”
- DataActions: call them out. They often introduce read→write surprises on data planes.
- Primary identities: list groups and service principals, not only users.
- Owner & cadence: assign a team owner and a realistic review cycle (60–90 days for high-impact, 180 days for low-risk).
Quick operating checks
- If a role includes */write or */delete, justify the scope in one sentence. If you cannot, shrink it.
- For customs, keep a short intent note (what job the role enables) and a link to its JSON in version control.
- When a project ends, the next review should retire or downscope its roles and remove stale assignments.
When the table is current, you have intent, scope, and DataActions in plain view. What you still need is scale. Reviews must run on a schedule, changes need to be captured as evidence, and effective permissions should be visible without a hunt. That is the moment to pair a simple process with continuous access intelligence.
Download this Azure Role Hygiene Tracker Template and start using it in your organization.
Complete Azure access intelligence with Veza
The role hygiene tracker gives you intent, scope, and DataActions in plain view. What it cannot give you is scale. Azure estates change daily. New subscriptions appear, identities multiply, exemptions stack up, and reviews slip. The real work is knowing who can do what at any moment, shrinking standing privilege, and producing evidence on demand without turning your team into spreadsheet operators.
Veza reduces that overhead. It continuously resolves Azure assignments and conditions into human-readable, effective permissions, highlights over-permissioned identities, and automates reviews and evidence so your process keeps pace with the platform.
Azure Security
Security outcomes depend on authorization, not only configuration. On the data side, Microsoft’s primer What is database security? frames the risks. For identity and authorization complexity, this explainer is a good baseline: What is identity security and why is it so complicated?
How Veza helps
Surface highly privileged and risky identities, remove dormant permissions, and prevent surprises when incidents hit.
Azure access control
Azure authorization starts with RBAC and gets precise with conditions and data-plane controls. Microsoft’s baseline is the Azure RBAC overview, and the day-to-day mechanics live here: Role assignments in the portal. Principle to operate by: least privilege. The control you are actually trying to measure is effective permissions; this primer explains why it matters: Why it’s important to understand effective permissions.
How Veza helps
Translate layered assignments into plain who-can-do-what answers, flag scope creep, and auto-suggest removals so reviews remove risk, not just check a box.
Azure compliance
Evidence matters as much as enforcement. Reviews, attestations, and configuration snapshots must be repeatable and tied to your control set. For a plain-language primer, see Access governance.
How Veza helps
Run time-bound access reviews, capture evidence as a byproduct, and alert on new privileged accounts so auditors see both intent and effect.
Azure roles
Roles define what an identity can do and where, but labels do not guarantee outcomes once inheritance and DataActions stack up. The operating model you want is predictable roles, small scopes, and reviews that catch drift.
How Veza helps
Convert complex permissions into effective permissions, you can read, highlight over-permissioned accounts, and keep custom roles aligned with actual needs.
Non-human identities
Most estates now have far more machines than people, and those identities hold durable rights. For definitions and operating basics, start with What are Non-Human Identities? For visibility pitfalls and why they matter in practice, this perspective frames the iceberg you do not see: Non-Human Identity visibility.
How Veza helps
Inventory service principals and managed identities, find durable rights, and expire or scope down access automatically.
Looking forward
Access control is moving toward continuous, evidence-first operations. For a forward view on patterns and operating models, read The future of access control. For near-term steps you can ship without adding bureaucracy, use 5 actionable strategies to improve security posture.
How Veza Complements Azure Security and Access Control
Managing security and access in Azure means keeping two truths in view. First, Azure’s controls are powerful. Second, outcomes still hinge on knowing who can do what, shrinking standing privilege, and proving it with evidence. RBAC, ABAC, ACLs, and reviews will take you far, but scale, inheritance, and non-human identities make prediction and upkeep hard to sustain by hand.
Veza turns that overhead into routine work. It resolves layered assignments into effective permissions you can read, points to where risk concentrates, and helps you remove what is not needed without breaking production. If you want a field-tested taxonomy of the problems you will actually find, this primer is a useful lens: A Field Guide to Bad Permissions, Part 1: Ungoverned Permissions. Reviews stop being paperwork and start removing access you do not use.
Azure security without Veza
- Permission design is complex and hard to validate at scale.
- Predicting real access outcomes is slow and manual.
- Violations are found late, after alerts pile up.
- Compliance evidence takes a hunt to assemble.
- Over-permissioned humans and non-human identities hide in the noise.
Azure security with Veza
Conclusion
Azure gives you the controls. The real work is using them so operations stay fast while the blast radius stays small. If you can answer who can do what, remove what is not needed, and prove it on demand, incidents get smaller and audits get easier. That is intelligent access in practice: clear outcomes, less standing privilege, and evidence as a byproduct of how you work.
Next Steps
Start where you are and pick one forward move: