Glossary
-

SailPoint vs Saviynt vs Veza [2025 Review]
Learn more -

What is Privileged Access Management? [2025 Guide]
Learn more -

12 Top IGA Software Vendors [2025 Guide]
Learn more -

SOC 2 Compliance Requirements [2025]
Learn more -
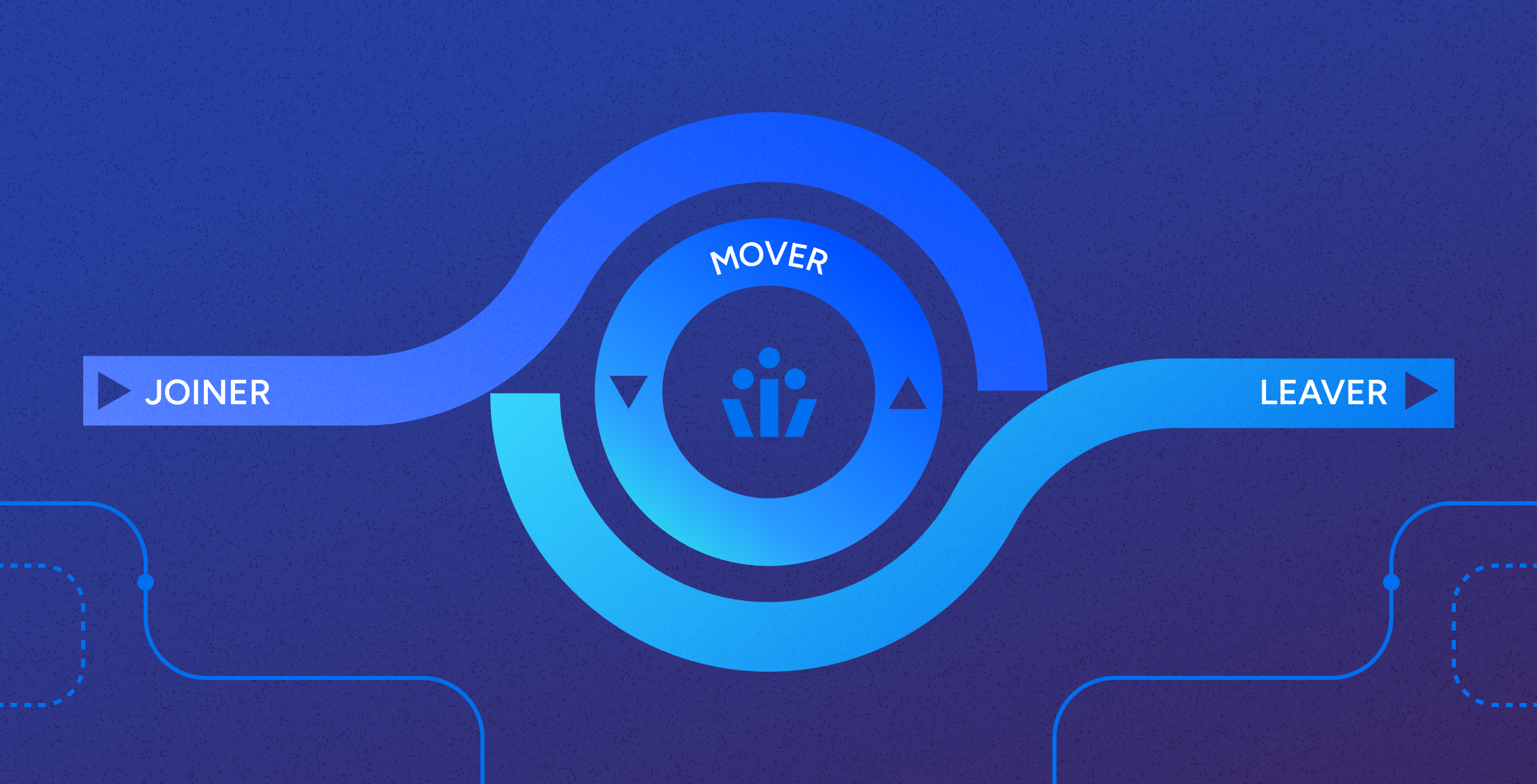
Identity Lifecycle Management: Beyond Provisioning & Deprovisioning
Learn more -
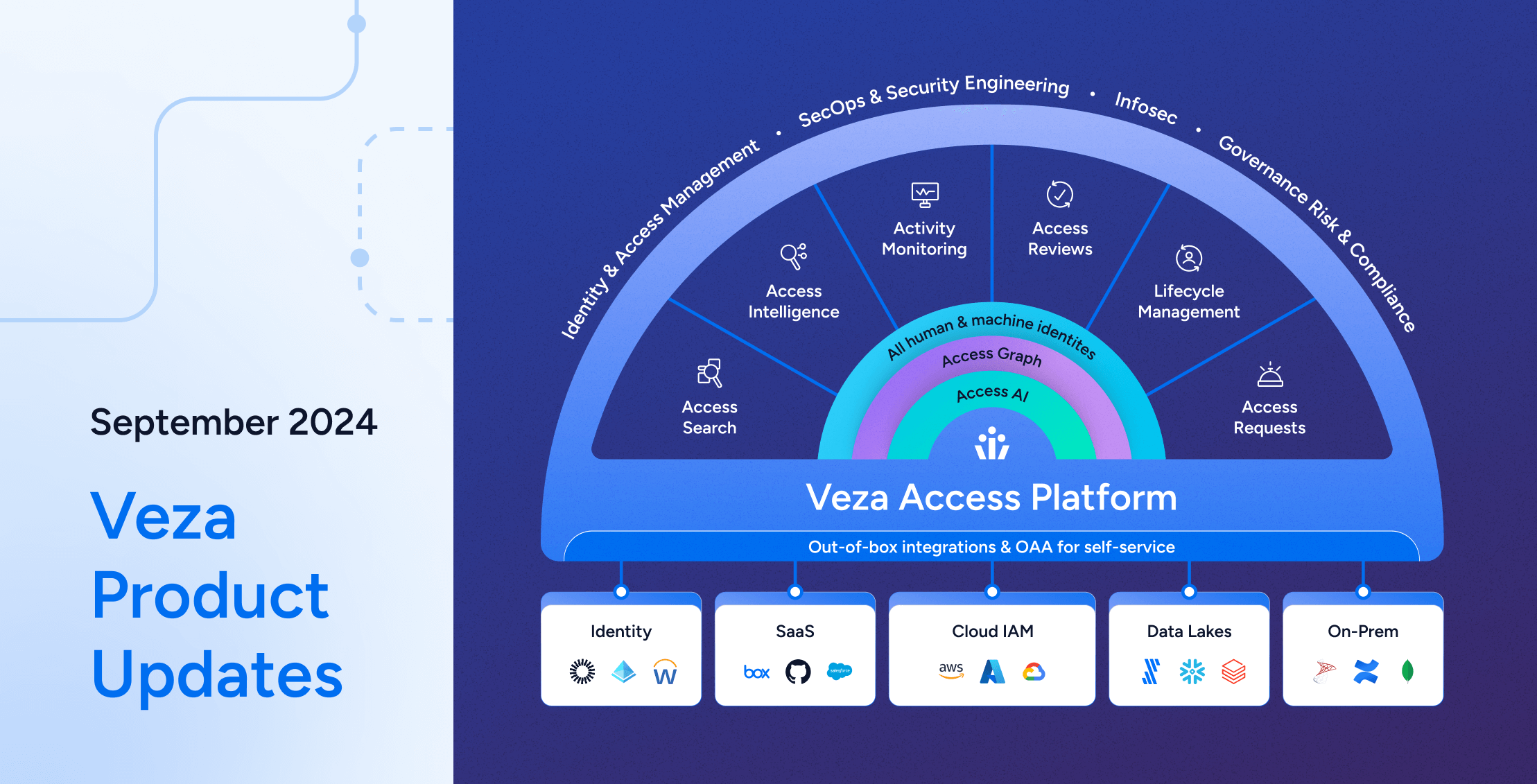
Veza Product Updates – September 2024
Learn more