Glossary
-
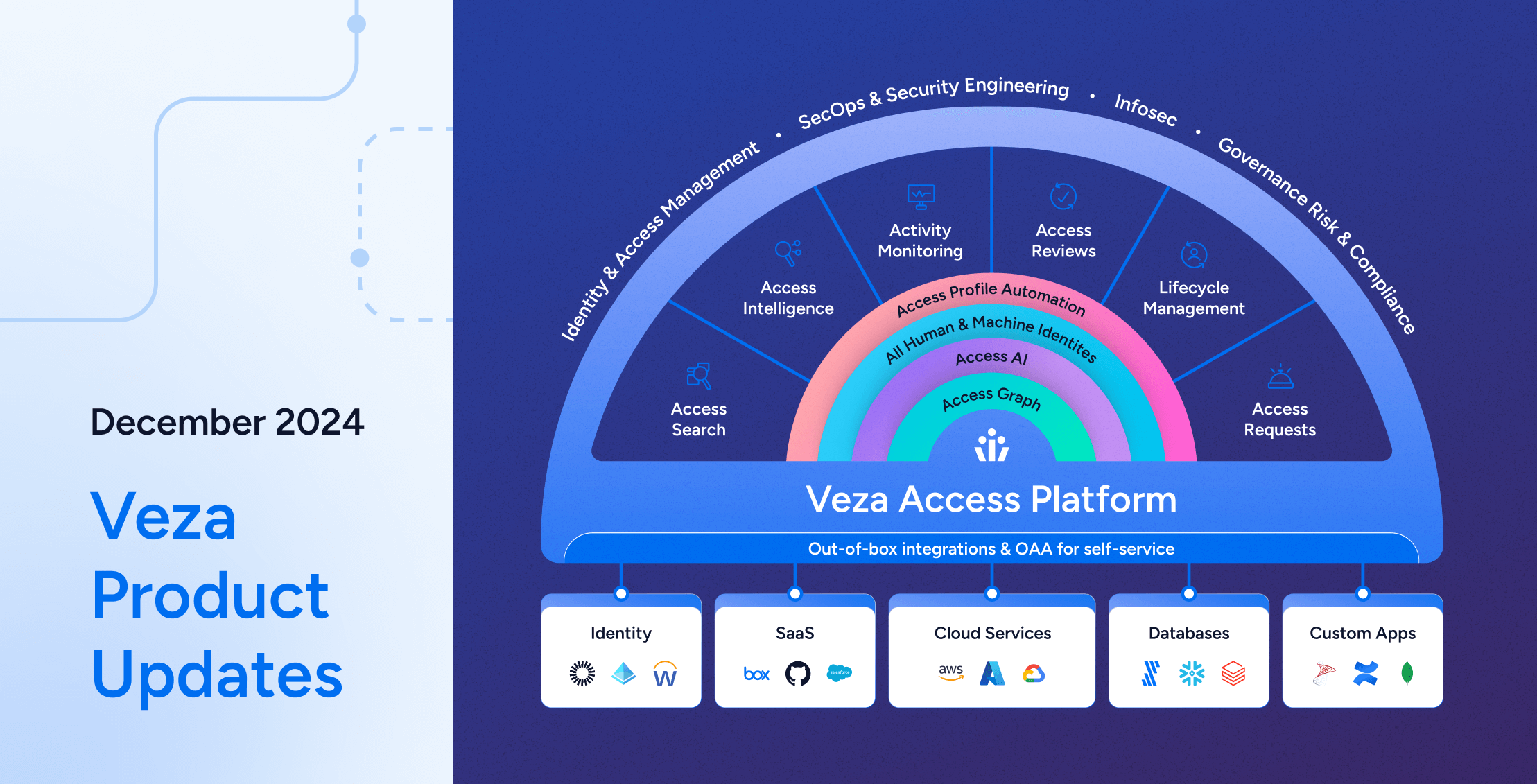
Veza Product Updates – December 2024
Learn more -

Demonstrating PCI DSS 4.0 Compliance with Veza’s Identity Security Platform
Learn more -

Complete SailPoint Review & Top Alternatives [2024]
Learn more -

Posture of Access, 3 Pillars of Least Privilege
Learn more -

Groundhog day in identity security
Learn more