Why identity classification isn’t optional anymore – and how Veza helps you automate it.
In the world of identity security, visibility without context is a half-measure. Knowing who can access what is foundational, but unless you can also understand what kind of identity it is and how risky that access is, you’re left guessing in the dark. This is where Enrichment Rules in Veza become a game-changer.
Enrichment Rules allow organizations to automatically classify identities and resources with metadata that reflects their real-world purpose, privilege level, and risk posture. Whether you’re labeling service accounts as non-human identities (NHIs), tagging roles as privileged, or flagging access to sensitive data stores, Enrichment Rules enable identity context at scale, without waiting for manual tagging or post-hoc analysis.
And for those already using Veza: if you haven’t explored the Enrichment tab in your integrations setup yet, you’re missing a core feature that transforms visibility into intelligence.
The Problem: Identity Sprawl and Context Blindness
Today’s enterprise identity landscape isn’t just sprawling—it’s chaotic. You’ve got:
- Thousands of human and non-human identities (service accounts, tokens, automations)
- Dozens of identity providers and cloud systems (Okta, Entra ID, AWS, Snowflake, GitHub)
- No standard way to tell which identities are privileged, sensitive, stale, or misclassified
Without consistent tagging, identity data is just raw telemetry. And traditional identity governance tools weren’t built to understand this complexity. You end up with dashboards full of raw access details, but no way to slice the data in a way that drives action.
That leads to critical failures:
- NHI accounts with broad entitlements but no visibility
- Overprivileged identities that evade reviews because they’re not labeled
- Incomplete enforcement of least privilege due to inconsistent tagging
Enter Enrichment Rules: Veza’s built-in mechanism to solve these challenges automatically.
What Are Enrichment Rules?
At their core, Enrichment Rules are user-defined logic statements that automatically assign metadata to identities or resources during the ingestion and parsing process. These rules act as filters, tagging entities based on naming conventions, access patterns, or any other attribute you define.
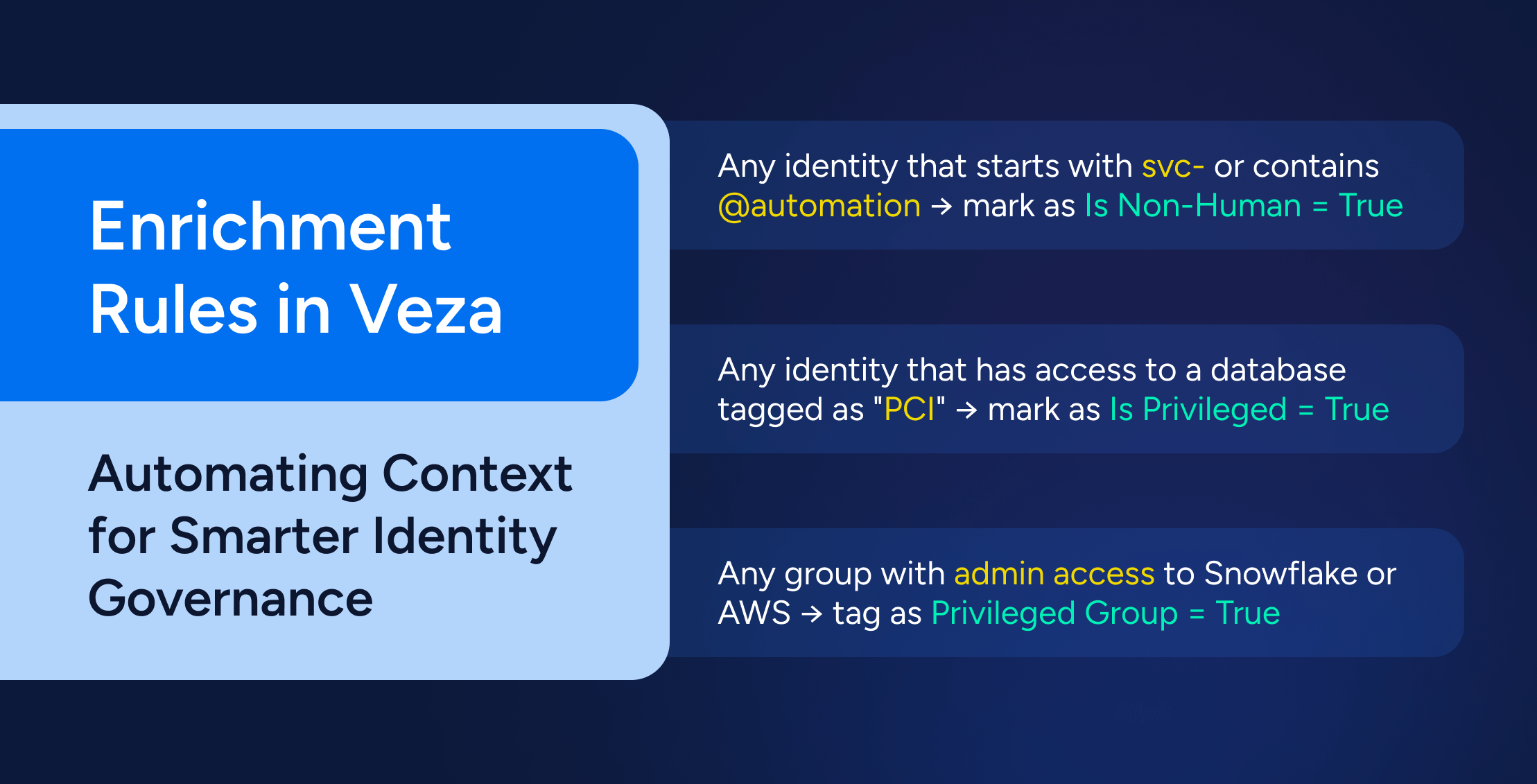
Examples:
- Any identity that starts with svc- or contains @automation → mark as Is Non-Human = True
- Any identity that has access to a database tagged as “PCI” → mark as Is Privileged = True
- Any group with admin access to Snowflake or AWS → tag as Privileged Group = True
These tags are then used throughout the Veza platform:
- In Access Graphs, to filter entities by type or risk
- In Access Review Automation to scope certification campaigns to just NHIs or privileged users
- In Policy Enforcement, to trigger action when identities match risky patterns
- In Dashboards like “Non-Human Identity Access” or “Privileged Access Surface Area” to drive SOC and compliance workflows
The rules are built and managed in the Integrations → Enrichment section of the Veza UI, allowing platform admins to define logic without code. You can preview matching entities, edit rule logic on the fly, or disable them entirely; changes are reflected in real-time.
Real-World Use Cases
1. NHI Classification at Scale
If your org uses service accounts that follow naming conventions like svc- or bot-, you can create a rule to mark them as Is Non-Human = True. That enables them to:
- Show up in NHI-focused dashboards
- Be included in NHI-only certification campaigns
- Trigger alerts or reviews if they drift outside defined access boundaries
2. Privileged Access Detection
You can define a rule such that any identity with s3:PutObject or iam:CreateUser permissions in AWS is tagged as Is Privileged = True. This metadata can drive:
- Real-time policy enforcement (auto-review, restrict, revoke)
- Scoped reviews for only high-risk roles
- Contextualized alerts when privileged accounts perform sensitive actions
3. Critical Resource Labeling
Tag specific data stores (e.g., Snowflake schemas, SharePoint sites) as Is Crown Jewel = True, and use this metadata to flag any identity that touches those assets as high priority. Pair with Veza Actions to automate response workflows.
How It Works Under the Hood
When an integration ingests data into Veza, the system parses identity and resource metadata. During this parse process, Enrichment Rules are evaluated.
- Matching entities are tagged with rule-defined metadata
- These tags are stored in Veza’s internal access model
- Downstream features (like dashboards, automation, and access reviews) consume this metadata
- You can view the metadata inline when inspecting users, roles, or resources
The entire process is transparent, editable, and auditable. Any changes to Enrichment Rules are versioned and visible within the rule editor interface.
What Makes Veza’s Approach Different?
Most legacy IGA and identity platforms rely on:
- Manual metadata mapping, which breaks at scale
- After-the-fact analysis, which delays response
- Static schemas, which can’t adapt to new naming conventions or cloud-native patterns
Veza’s Enrichment Rules solve for all three:
- Fully automated, rule-based classification
- Inline and real-time tagging at ingest
- Seamless integration with access governance, enforcement, and reporting features
- Works across both human and non-human identities
It’s part of what makes Veza a true execution layer for modern identity security—one that aligns with Gartner’s emerging IVIP framework, where visibility, intelligence, and action are unified.
How to Get Started
If you’re a current Veza customer:
- Go to Integrations → Enrichment
- Click Create Rule
- Define your matching logic
- Assign one or more metadata tags
- Save and watch the Access Graph, Dashboards, and Review scopes update automatically
You can also check out the official Enrichment Rules documentation for a detailed walkthrough.
Final Thoughts
Enrichment Rules may not look flashy at first glance, but they’re one of the most powerful enablers in the Veza platform. By automating identity and resource classification, they give you the context needed to secure access intelligently and act at speed.
For prospective customers: this is a core differentiator you won’t find in traditional IGA tooling.
For existing users: if you’re not actively using Enrichment Rules, you’re only seeing half the picture.
Now’s the time to close that visibility gap and turn raw access into intelligent control.
What’s Next? Take Action Based on Where You Are
Just exploring identity security platforms?
If you’re still evaluating what modern identity governance looks like, check out how Veza’s Access Graph transforms raw permissions into understandable, actionable context across your cloud and SaaS environments.
Already tackling NHI or privileged access challenges?
Learn how Veza’s Nonhuman Identity Governance and Access Review Automation combine with Enrichment Rules to reduce review fatigue, enforce least privilege, and stay audit-ready.
Ready to see it in action?
Schedule a demo with our team to see how Enrichment Rules can automatically classify identities, surface risk, and make your access reviews smarter, without manual tagging or complex policy engines.





