-
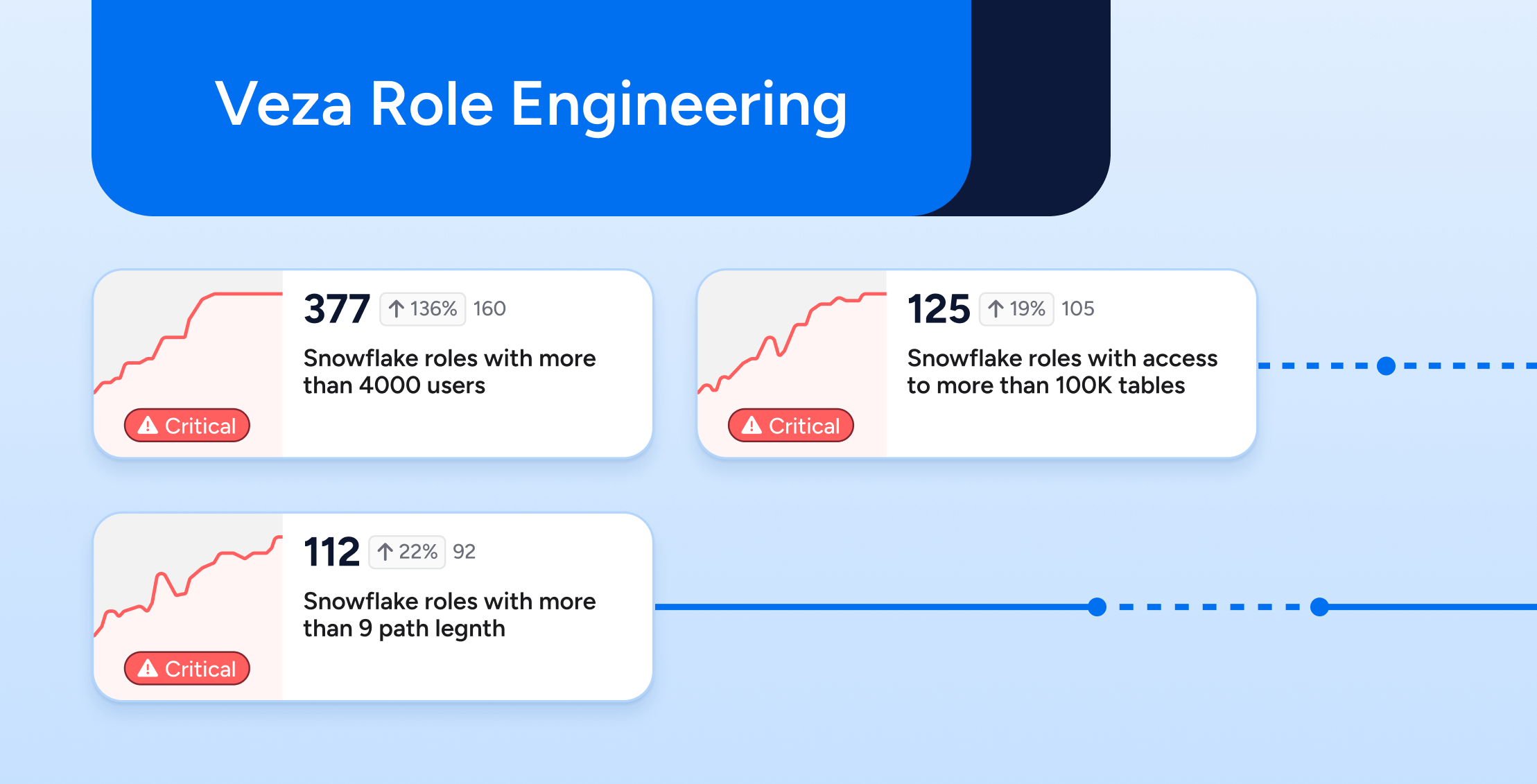 Identity Security
Identity SecurityVeza Access Intelligence: Role Engineering for Modern Access Control
Learn more -
 Identity Radicals
Identity RadicalsIdentity Crisis: The Rise of Machines
Learn more -
 Identity Security
Identity SecurityI Attended the Verizon Data Breach Session at RSA So You Don’t Have To:
Learn more -
 Identity Security
Identity SecurityReflections from Gartner IAM London: Visibility Leads to Observability
Learn more -
 Data Security
Data SecurityGitHub OAuth Attack Alert: A Developer’s Worst Nightmare and How to Prevent It
Learn more -
 Compliance
ComplianceAchieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -
 AI
AIVeza Access AI – Applications of Gen AI for Identity Security Use Cases
Learn more -
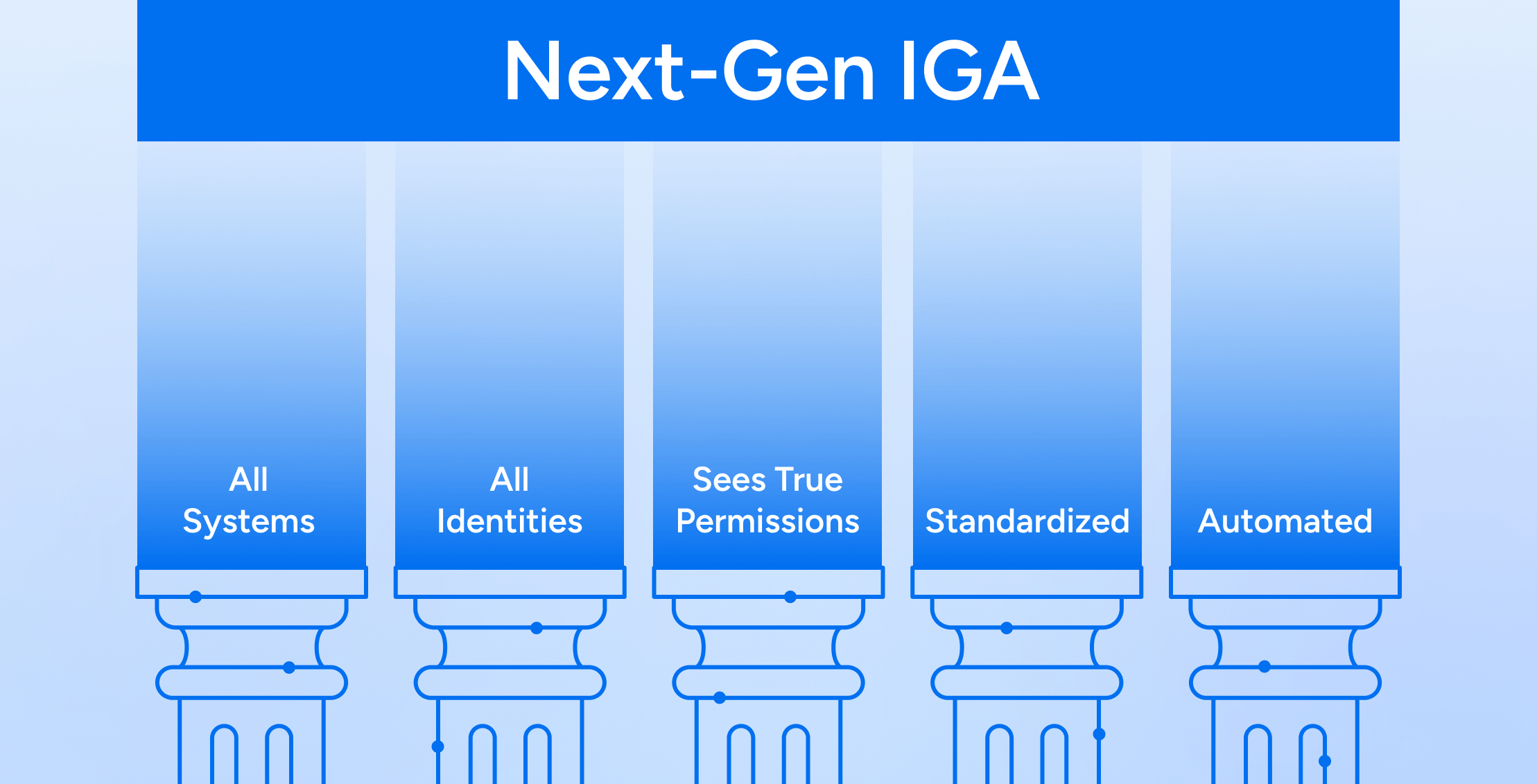 Identity Radicals
Identity RadicalsThe Five Tenets of Next-Gen IGA
Learn more -
 Data Security
Data SecuritySimplifying Security: The Power of Effective Access Control in Cybersecurity
Learn more







