If you work in identity or security, you already know that IGA stands for identity governance and administration. And you know that these tools have been around for a long time. But the world has changed, and the identity attack surface has ballooned. Traditional IGA tools have blind spots because they rely on a data model of directories, users and groups, built for an era of on-premises architectures and fully-trusted networks. They assume that employees are listed in a single source of truth and that role and group definitions accurately reflect the permissions associated with those roles. But now, with the complexities of modern, cloud-centric environments and identity-based attacks a near daily occurrence, it’s clear that something is broken, and it’s time for a fresh approach to securing access in the enterprise.
It’s Hard to See Access
The world has changed. Access has decentralized to a point where security teams cannot possibly understand, let alone enforce, common-sense policies for the business. Years ago you might have been a Microsoft shop—using Active Directory as your enterprise directory, with Windows file shares and SharePoint to store files, some Microsoft SQL Server, and it was all in your data center. Now, the landscape is vastly different. The average enterprise has 364 SaaS apps and uses 1,295 cloud services, creating a fragmented ecosystem. Organizations rely on many different vendors providing identity attributes, data stores, cloud platforms, and apps. Today, the average organization uses 1.75 identity platforms, while 34% of identities are created outside of these platforms as local accounts in SaaS and cloud platforms. To complicate matters further, there’s a 17-to-1 ratio of non-human to human identities across these apps and systems.
With app sprawl comes access sprawl. Each of these apps has its own unique access control system, e.g., RBAC or ABAC. Some are complex, with hundreds of arcane permissions and nested roles and groups. As a result, it’s hard to determine who can access what. Making matters worse, lots of these new apps use service accounts to talk to each other, so that creates a new, fast-growing group of privileged identities. In short, it’s no longer practical to monitor enterprise permissions.
This wouldn’t be a problem if security teams could take months to evaluate access. Of course, that’s not the case. Business moves faster than ever, and if IT teams want to help their partners in the business, it’s essential to evaluate and grant access quickly while enforcing policies and regulatory compliance.
Adding to this complexity, the rise of AI systems has introduced entirely new challenges for identity governance. Organizations must now manage access to training data, model artifacts, and AI outputs. Traditional IGA approaches cannot adequately address the granular permissions needed for AI governance, including:
- Access controls for training data lineage
- Permission boundaries for model development
- Authorization controls for AI system outputs
- Governance of machine-to-machine access patterns
These AI-specific challenges compound the already difficult task of managing traditional access patterns and make the need for next-generation solutions even more urgent.
The Stakes are High
Identity is the new perimeter. Gartner has found that 80% of organizations have had some sort of incident related to identity in the last 12 months. 75% of breaches occur through the theft or mis-use of identities. CIOs and CISOs recognize that they have blind spots when it comes to who can do what with their data, and stakes are high for both the business and the team. A single incident of ransomware can cost $4.5m when factoring in the disruption and downtime. The average disruption lasts 25 days. Amid these rapidly growing threats, businesses are increasingly relying on data, digital, and technology to drive innovation, improve operational efficiency, and gain a competitive edge.
Users routinely accumulate risky permissions as access is granted during daily operations – a pattern that, over time, significantly increases organizational risk. Sometimes permissions are granted by accident, when someone misunderstands role entitlements. Sometimes permissions are not revoked when employees leave, change jobs, or finish a temporary project. All of these accumulated permissions live on as open doors for attackers. Identity and Security teams cannot see the permissions, so they cannot manage them.
Even on the good days, when these permissions don’t lead to a breach, they still jeopardize compliance (SOX, SOC 2, GDPR) and lead to onerous investigations and fines. As one CISO remarked to his Veza team, “I need you to get me out of SOX jail.”
Security and identity teams need a better way.
The Rise of Next-Gen IGA
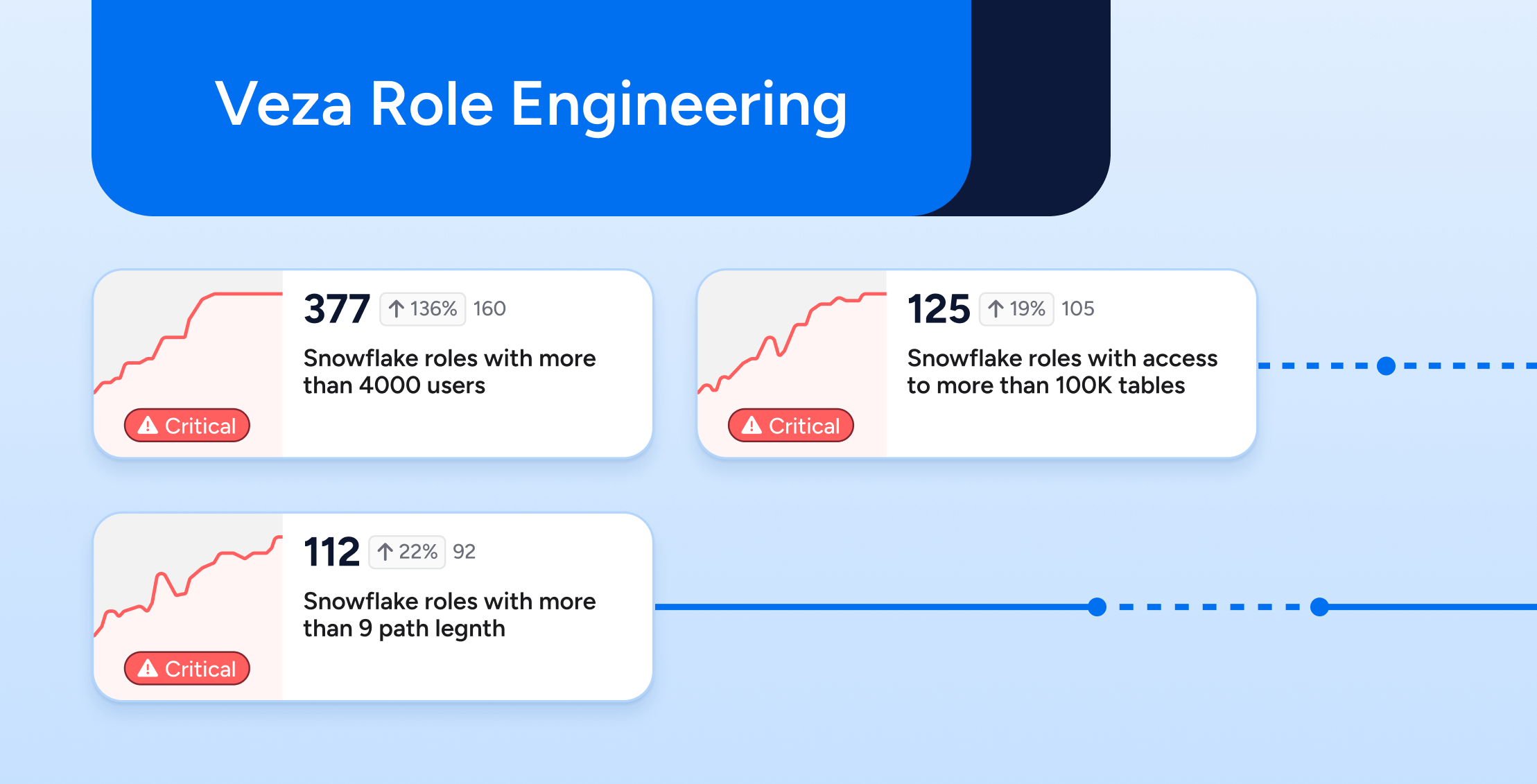
Identity governance is difficult at scale because there are so many different ways that someone (or something) can get access. Identities are duplicated across many systems, like Active Directory, Okta, Ping, and then locally in apps. Meanwhile, the volume of apps is easily in the hundreds, from on-prem to SaaS, from commercial to home-built. Each of those apps assigns access permissions in its own unique way, so nobody can be expected to master hundreds of access systems. Moreover, some of the most modern arrivals in the cloud have access control systems that are very complex. The IAM services of the cloud providers (AWS, GCP, Azure) offer hundreds of esoteric permissions, with nesting and inheritance. Snowflake and Salesforce are also powerful but complex. As a result, it’s simply not practical anymore to answer the question of who can access what.
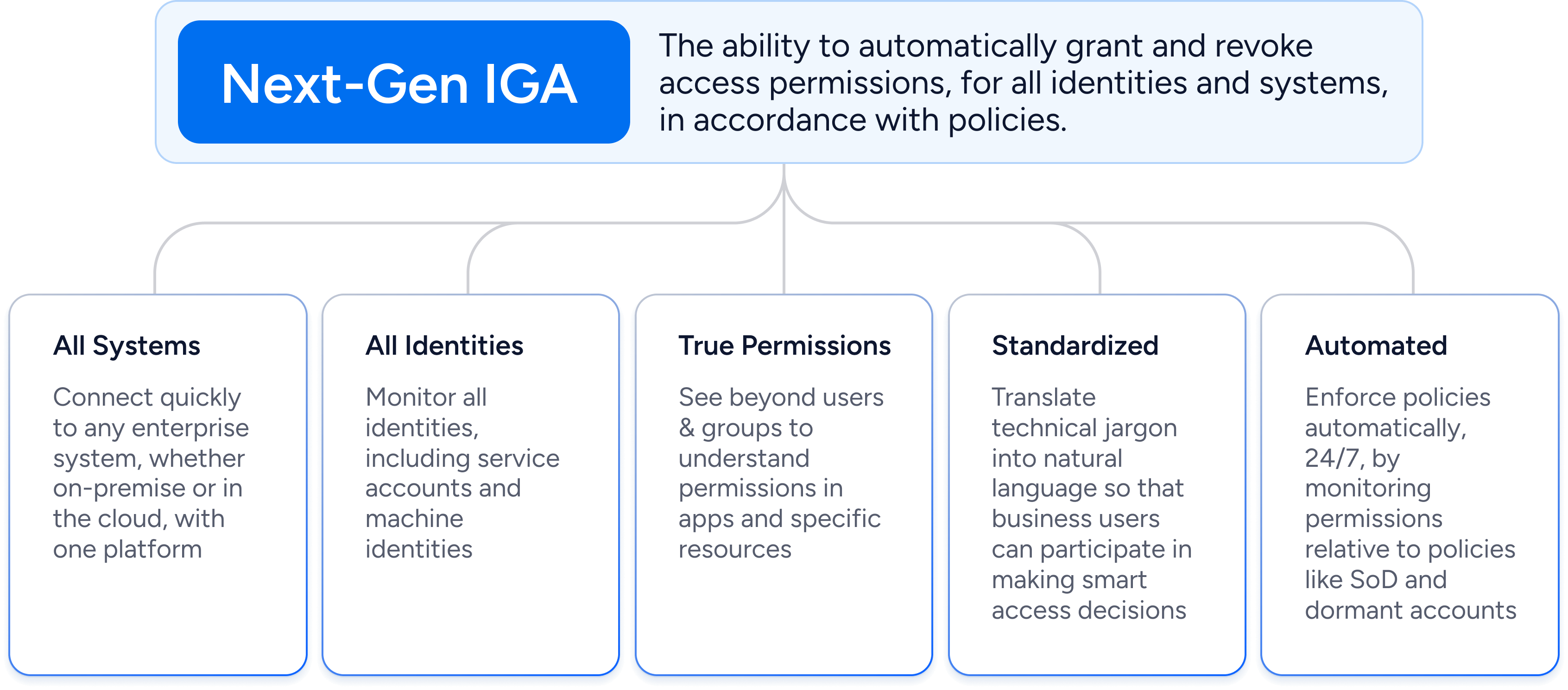
The IGA tools of the past risk obsolescence if they don’t adapt to the new world. At Veza, we believe that the next generation of IGA must enable organizations to govern access at scale. In short, organizations must be able to grant and revoke access permissions automatically, in accordance with policies, for all identities and systems. In order to do this, Next-Gen IGA will need to satisfy five essential tests:
- Works for all systems
- Works for all identities
- Sees true permissions
- Is standardized
- Is automated
Together, these five tenets enable organizations to implement risk-based and intelligence-driven governance, ensuring that access decisions and reviews are prioritized according to potential impact and exposure. Moreover, they must enforce a rigorous identity lifecycle – from initial provisioning with least-privilege entitlements, through ongoing access adjustments based on changing business needs, to timely deprovisioning when access is no longer required.
1) All systems
The #1 tenet for Next-Gen IGA is that it must protect all enterprise systems where access is a concern. In other words, it must connect to cloud services, on-prem, SaaS apps, legacy applications, custom applications, and more. The logic is simple: one cannot prevent policy violations if only watching a subset of systems. From provisioning to access reviews, all systems must be covered, delivering a single pane of glass for governance.
Moreover, the connection to systems must be practical. It’s well-known that in software, anything is possible given time and money. But the reality is that traditional IGA implementations often run out of budget after connecting to just a few systems. With sensitive data spread across an expanding landscape of apps and services, next-gen IGA will have to approach integrations in a fundamentally different way. Modern IGA platforms must simplify application integration through no-code/low-code frameworks, eliminating the need for complex deployments and costly integration teams.
This comprehensive visibility becomes especially critical for enforcing policies like separation of duties, where violations can only be detected by monitoring access patterns across multiple systems – for instance, when sensitive functions span across ERP, CRM, and financial applications.
2) All identities
The word “identity” is often associated with human identities (employees, contingent workers, and partners). But for many organizations, there are now more non-human identities like service accounts, machine identities, and IOT devices. However, for a traditional IGA tool, these non-human identities live in the shadows. Since service accounts usually have elevated privilege, it is essential that any governance program include them.
Another class of identity missed by traditional IGA is local users. When employees in an organization adopt a SaaS app, they may not always control access through an SSO platform like Okta. It’s common for employees to create user accounts directly in those SaaS apps. An IGA tool looking at the groups and roles assigned to employees will miss these local user accounts. Sometimes, the local accounts are even admin accounts, with elevated privileges. These are especially dangerous, as they may not get terminated properly when the employee leaves the company.
To govern the identity attack surface, organizations must monitor all types of identities, wherever they originate.
3) True permissions
Traditional IGA was limited to governing via groups and roles. Unfortunately, it’s often misleading to look at the defined permissions of a role as they might be mis-labeled or out of date. A group labeled “sales read-only” may very well have permissions to delete data. These labels can create a false sense of security. Even if you do realize there may be inconsistencies between your groups, roles, and permissions, traditional identity tools can’t investigate how these discrepancies occurred.
Companies will never secure their full attack surface until they can see, faithfully, who has access to what data, and how they got it. Any Next-Gen IGA solution will have to go beyond users & groups to implement comprehensive access intelligence that includes:
- Automated discovery of effective permissions across all platforms
- Real-time mapping of permission inheritance chains
- Detection of toxic permission combinations
- Analysis of access patterns and usage
- Risk-based evaluation of permissions
- Continuous monitoring of permission changes
- Cross-platform visibility into indirect access paths
Access intelligence now includes identity risk scoring that considers:
- Accumulated permissions across platforms
- Usage patterns and anomalies
- Historical access behavior
- Role combinations and toxic access
- Data sensitivity levels
These risk scores provide an objective measure for prioritizing reviews and automating access decisions. With this level of intelligence, organizations can:
- Make informed decisions about role design and assignments
- Identify and remediate excessive permissions
- Detect potential privilege escalation paths
- Monitor for unauthorized permission changes
- Maintain continuous compliance
- Drive towards true least privilege
4) Standardized
The next tenet of next-gen IGA is that it be democratized in the way it presents information. All systems require some level of system-specific expertise, but no organization should have to hire system experts just to handle access. Did you know that there are over 21,000 unique permissions available in AWS, Azure and GCP? The AWS IAM manual spans over a thousand pages. For S3 storage buckets, there are over a hundred potential permissions. Nobody is going to understand all these permissions without looking them up in the documentation, which just doesn’t scale for enterprise-wide governance.
Visualizing permissions isn’t helpful if identity professionals can’t understand them. To make smart decisions, identity teams just need to know the bottom-line: can somebody read, update, or delete this data? Next-gen IGA must translate arcane technical permissions into simple business terms.
Traditional annual access reviews are also giving way to more efficient and modern approaches. The concept of micro-certifications is a perfect example, enabling:
- Targeted, context-aware reviews
- Event-triggered certifications
- Risk-based review scheduling
- Focused scope based on changes
- Quick response workflows
This approach reduces reviewer fatigue while improving security by ensuring high-risk access is reviewed more frequently and with better context.
5) Automated
Next-gen IGA must go beyond basic monitoring to embrace proactive risk management through intelligent automation. Modern security teams need systems that can detect and respond to risks in real-time, analyzing permission combinations and access patterns to spot potential violations before they become incidents. This predictive capability allows organizations to stay ahead of threats, rather than merely responding to them.
Modern IGA platforms can now incorporate sophisticated risk analytics that continuously evaluate access patterns, providing early warnings when unusual combinations of permissions emerge or when access patterns deviate from established baselines. These systems can automatically recommend remediation steps, helping security teams prioritize their efforts where they matter most. This continuous risk monitoring and automated response operates independently of periodic access reviews, enabling organizations to identify and address potential threats as they emerge rather than waiting for the next scheduled review cycle.
But proactive monitoring is only half the equation. True next-generation IGA must also automate routine access management tasks intelligently. By leveraging risk scores and historical patterns, these systems can automatically approve low-risk birthright access when users join or move within the organization, access requests, provision appropriate permissions, and even grant just-in-time access when needed. Birthright access provisioning and self-service access requests become practical when bounded by intelligent guardrails that enforce policy while maintaining business agility.
This intelligent automation transforms what was once a manual, periodic process into a continuous, dynamic system that adapts to changing business needs. Security teams can focus on strategic decisions while routine access management happens automatically, guided by policy and risk analysis. The result is stronger security with less operational overhead – continuous compliance that doesn’t bog down the business.
In short, automation is the only practical strategy to driving least privilege and enforcing an ever-growing list of access policies.
Closing the Doors
The primary benefit of Next-Gen IGA is that you systematically remove and prevent identity-based risks. By automating governance across all systems, Next-Gen IGA enforces your access policies in a way that scales. With continuous policy enforcement, you reduce the risk of identity threats, both those coming from external bad actors and those coming from insiders (whether malicious or accidental). Without this, it is virtually impossible to adhere to the principle of least privilege. With this, you can reduce privilege, minimize blast radius, root out risky misconfigurations (like absence of MFA), and disable dormant accounts.
Next-gen IGA will also lower operational costs. Historically it costs a lot to govern access with the manual methods and spreadsheets. Whether you’re motivated by internal policies or external regulations (SOX, SOC 2, GDPR), next-gen IGA reduces the labor required to monitor, review, and enforce policies. Moreover, this will reduce the cost and aggravation of access reviews.