-
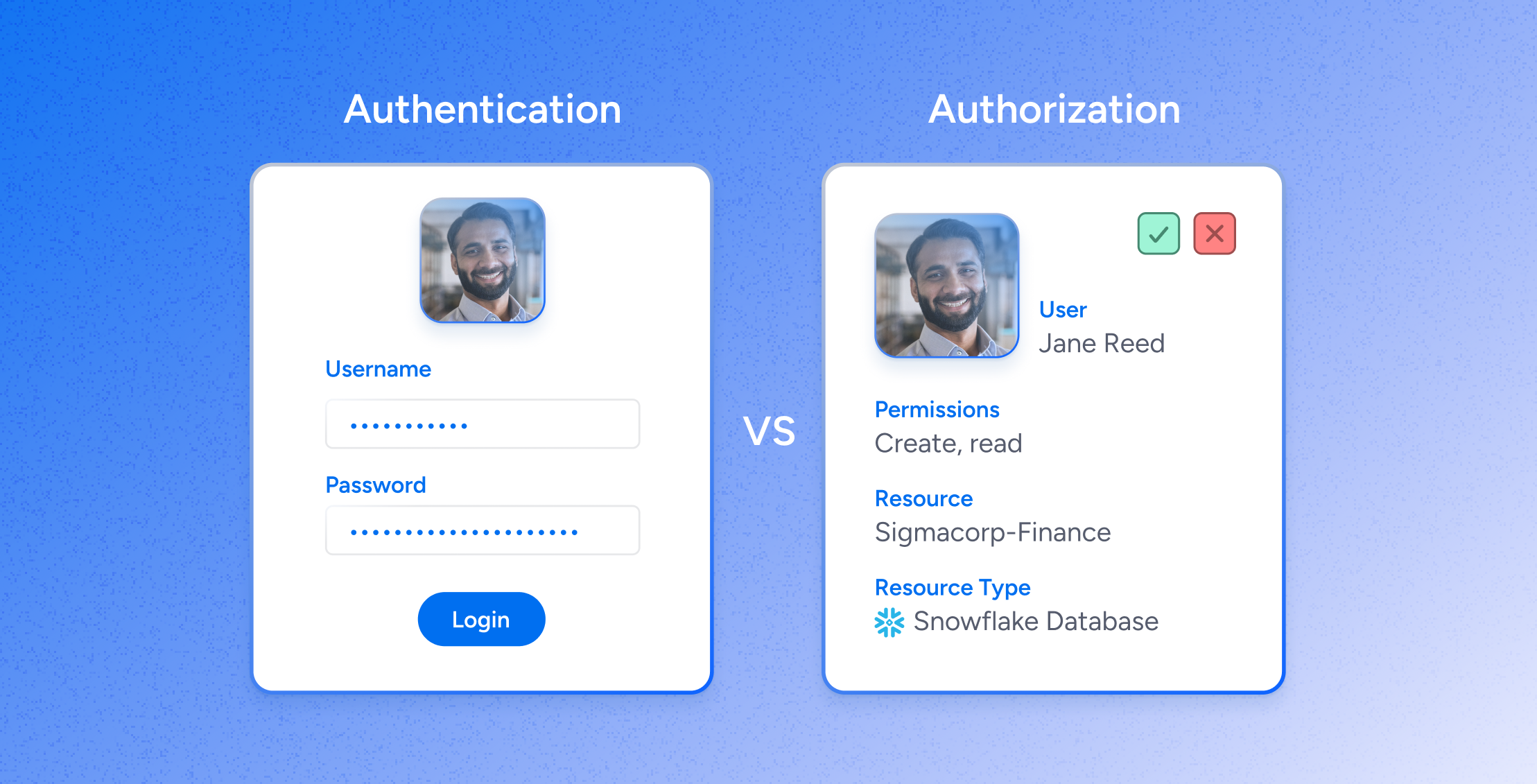
 Compliance
ComplianceEffortless Access Governance for Custom Applications with Veza: Boost Access Reviews with Automation
Learn more -
 AI
AIModel Context Protocol (MCP): Implications on identity security and access risks for modern AI-powered apps
Learn more -
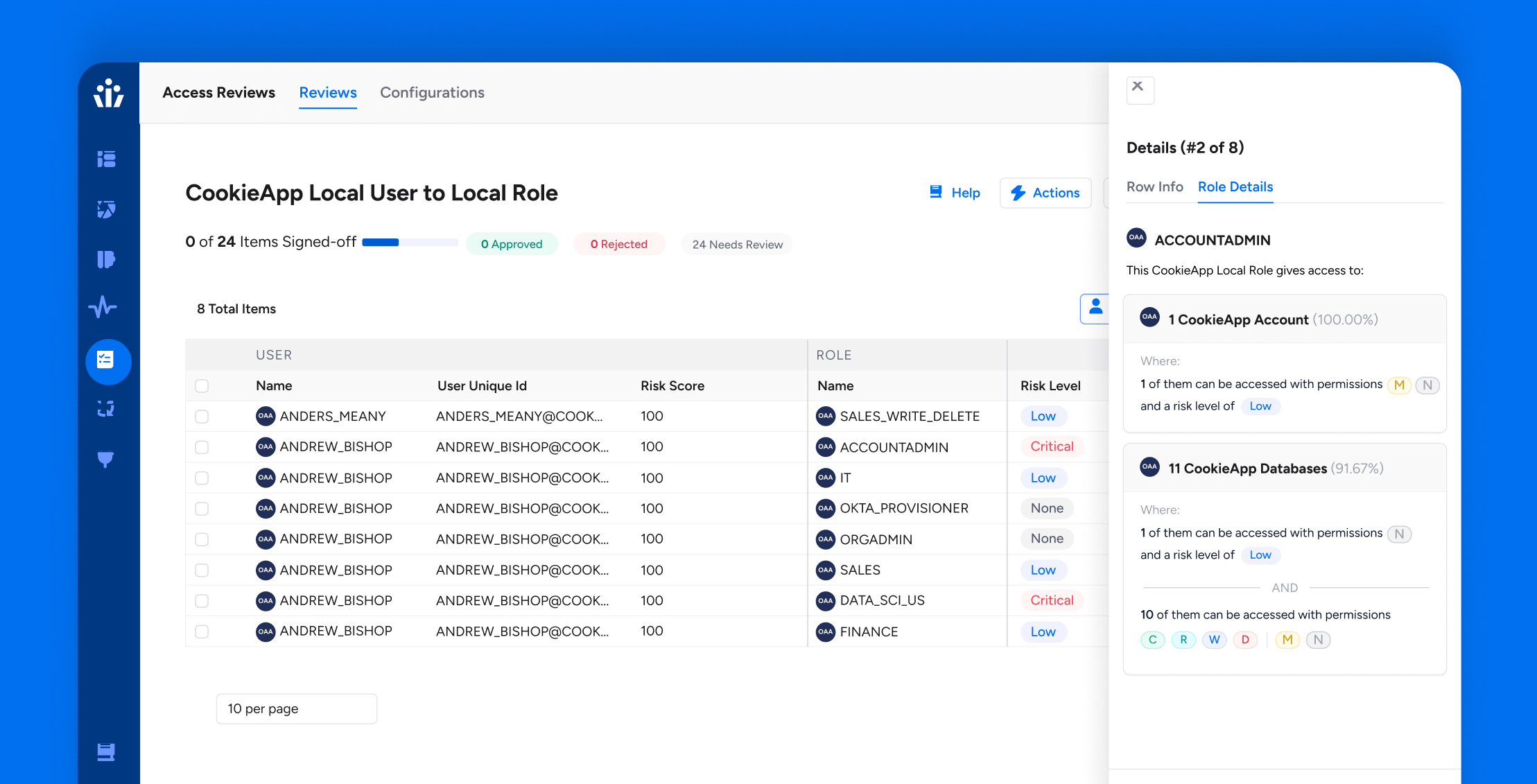
 Data Security
Data SecurityGitHub OAuth Attack Alert: A Developer’s Worst Nightmare and How to Prevent It
Learn more -
 Compliance
ComplianceAchieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -
 Identity Security
Identity SecurityFrom Access Oversights to Audit Excellence: How Veza and Legacy IGA Secure SharePoint Environments
Learn more -
 Technical Thought Leadership
Technical Thought LeadershipIntelligent Access for custom apps: getting started with Veza’s Open Authorization API
Learn more -
 IAM
IAMSnowflake Roles Best Practices: Steps to Least Privilege
Learn more -
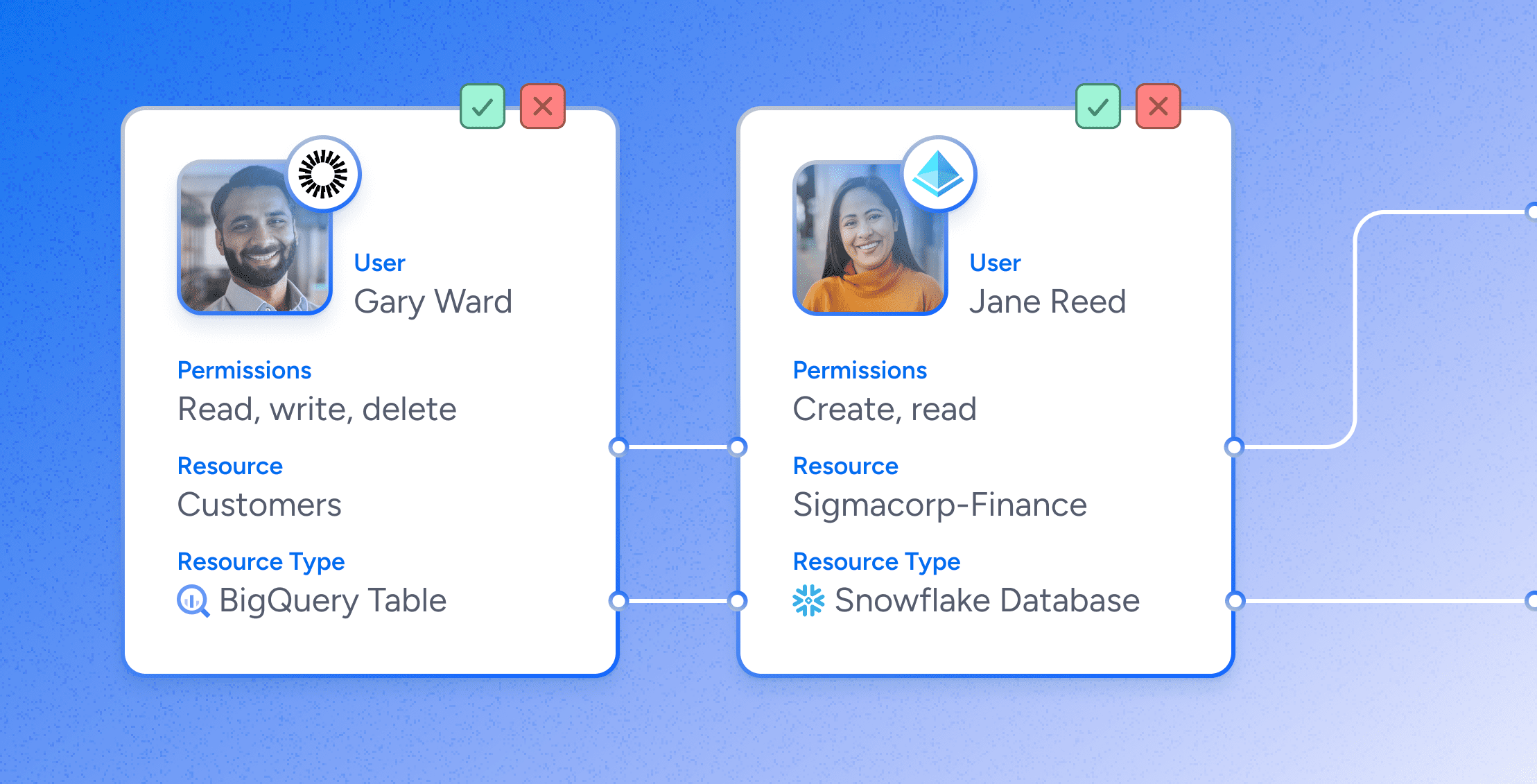 Compliance
ComplianceUser Access Reviews: How They Work & Best Practices
Learn more -
 Industry News
Industry NewsThe hard thing about Zero Trust
Learn more