-
 IAM
IAMWhen Identities Turn Against You: Building an Insider Threat Program for the Cloud Era
Learn more -
 IAM
IAMNHI 2×2 Framework: From Blind Spots to Closed Loops
Learn more -
 IAM
IAMAll the Keys, Visualized: Governing 90+ Non-Human Identities
Learn more -
 AI
AINHI Ownership: Solving the “Who Owns This Bot?” Problem
Learn more -
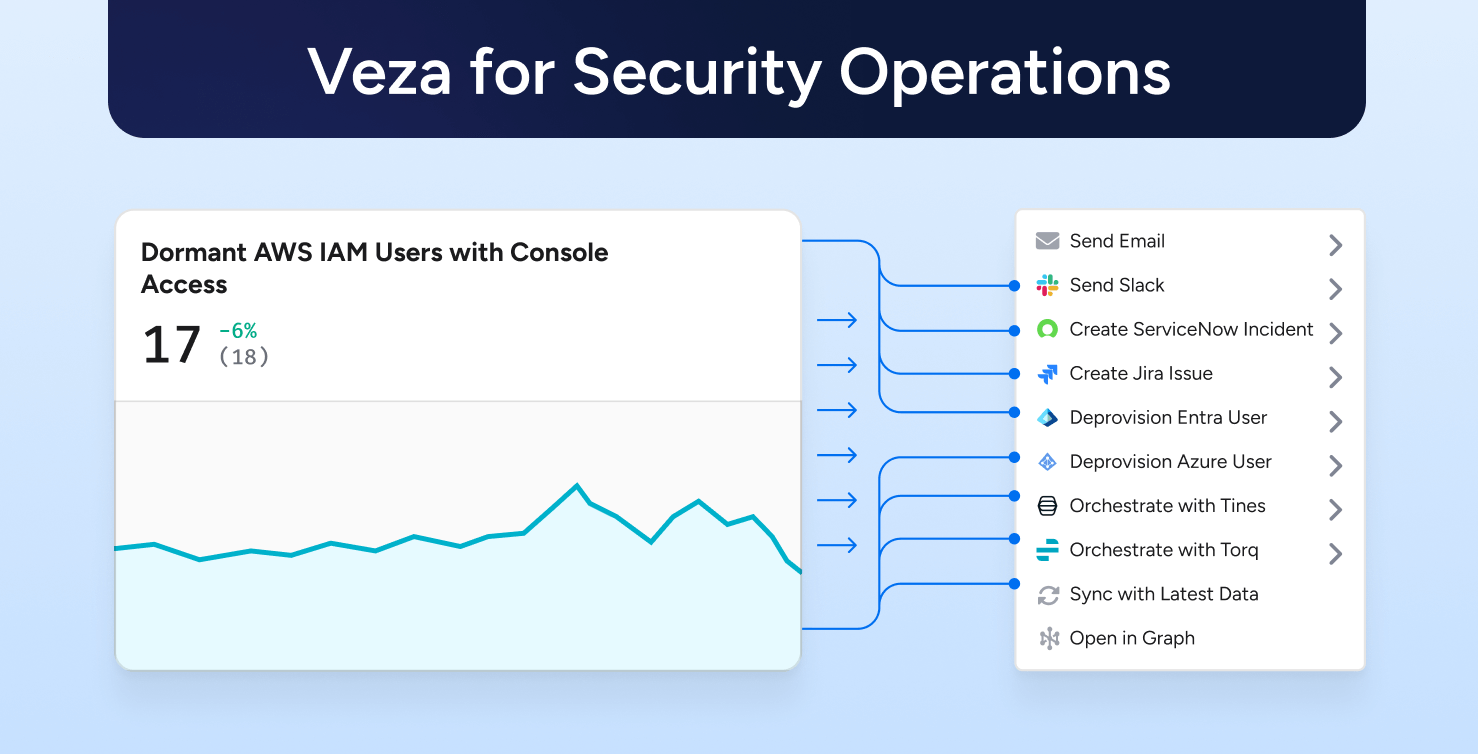 Identity Security
Identity SecurityVeza for Security Operations: Make Identity Operational
Learn more -
 Compliance
ComplianceAzure access control and compliance: a practical guide for intelligent access
Learn more -
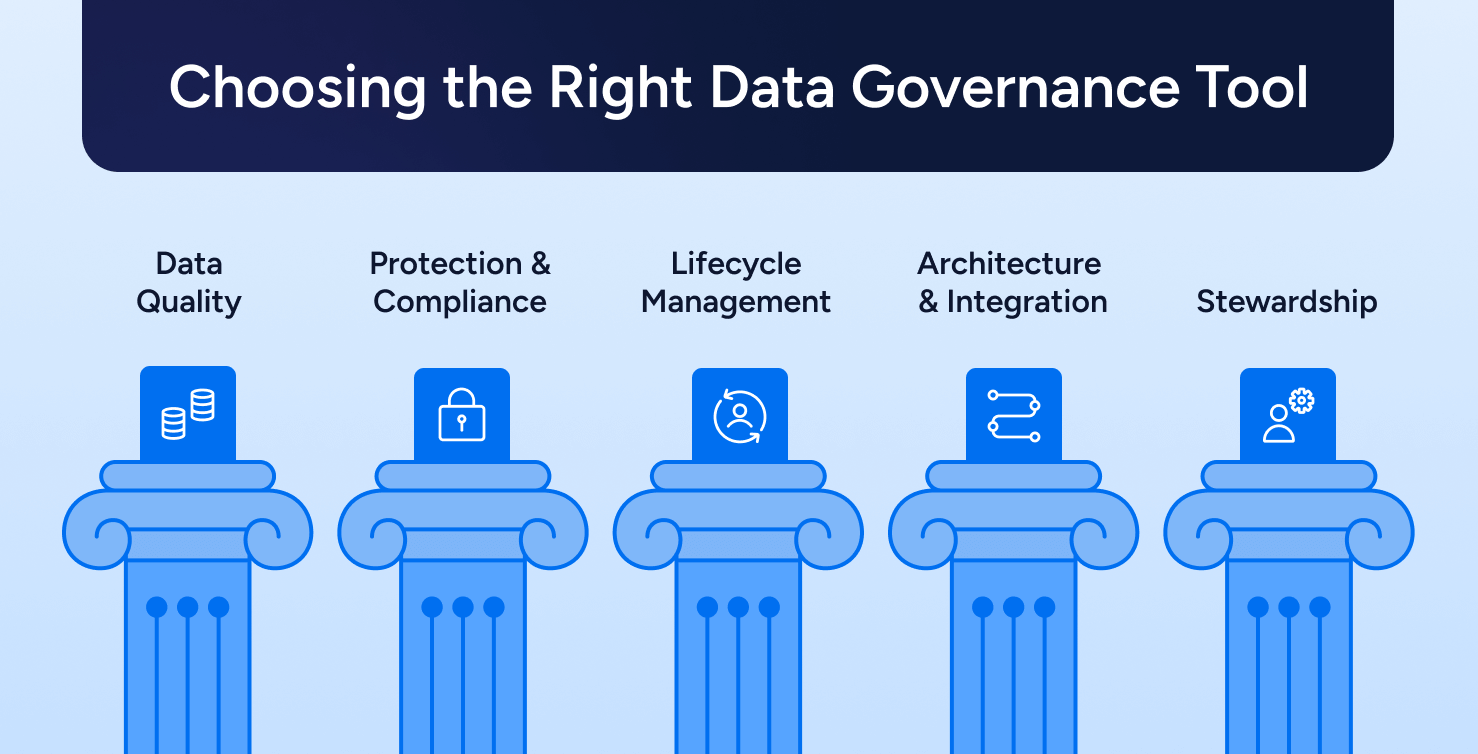 Compliance
ComplianceHow To Choose the Right Data Governance Tools [2025]
Learn more -
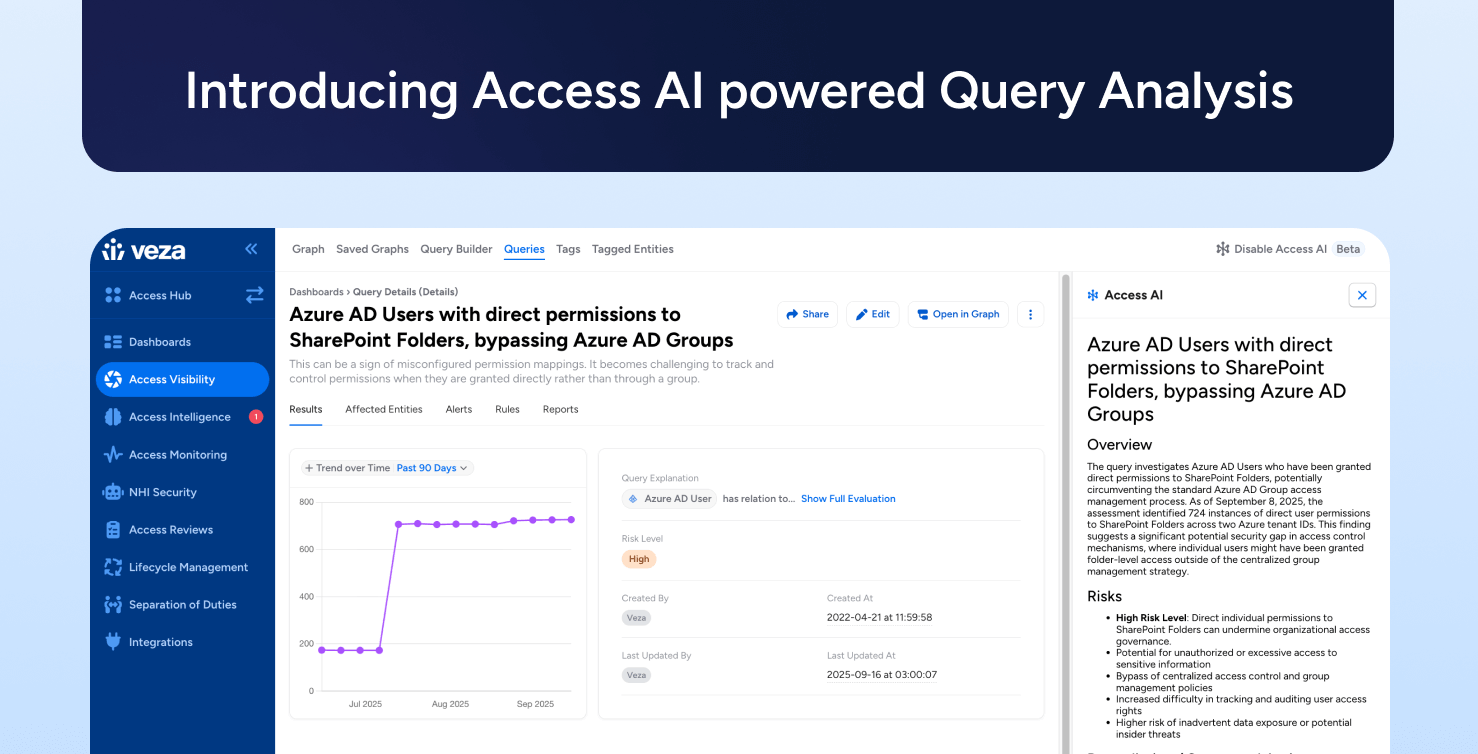 AI
AIIntroducing Access AI powered Access Risk Analysis
Learn more





