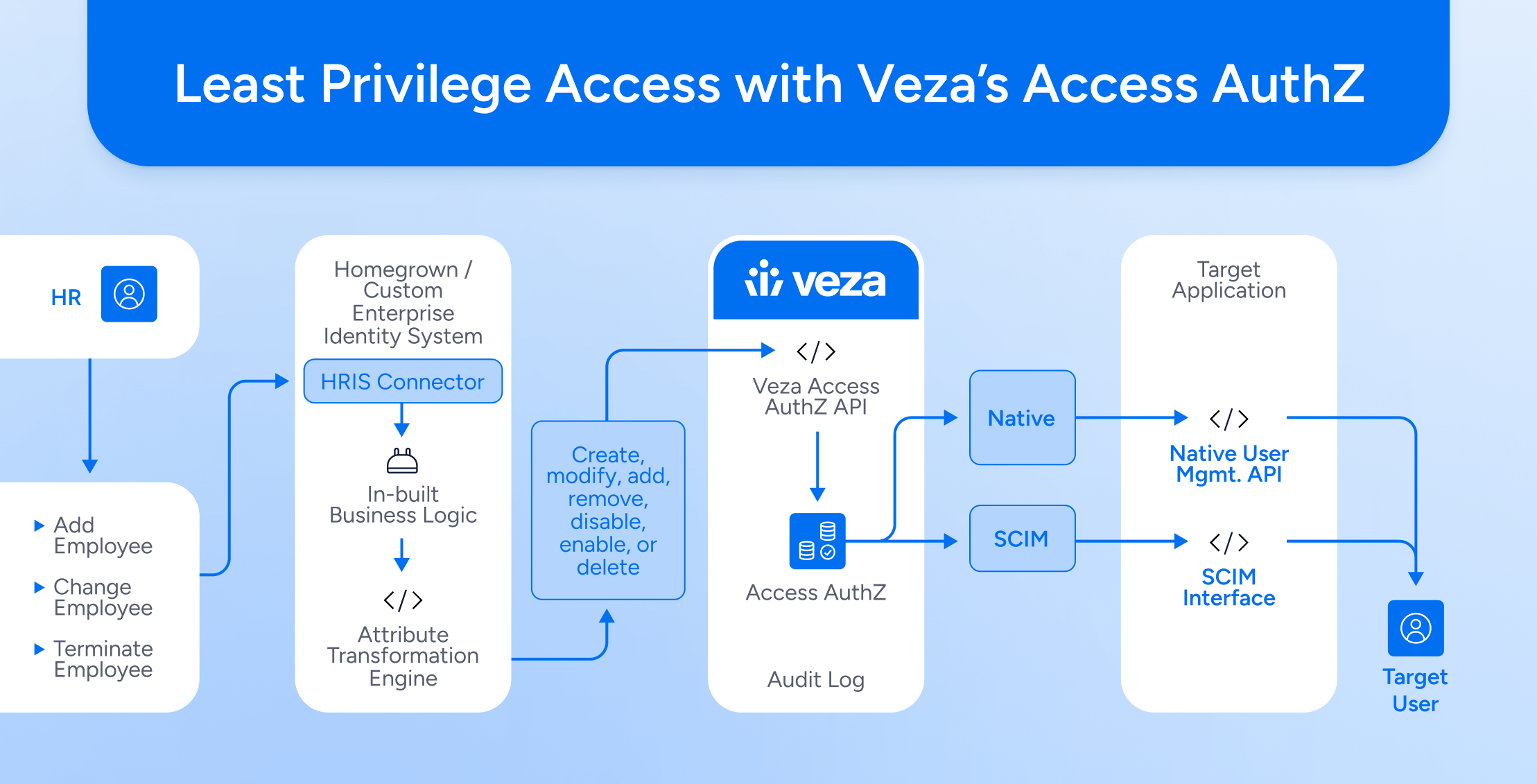
-
 IAM
IAM11 Best Zero Trust Providers for 2026
Learn more -
 Company
CompanyWhy Analysts Keep Pointing To Veza as the Leader In The New Identity Security Landscape
Learn more -
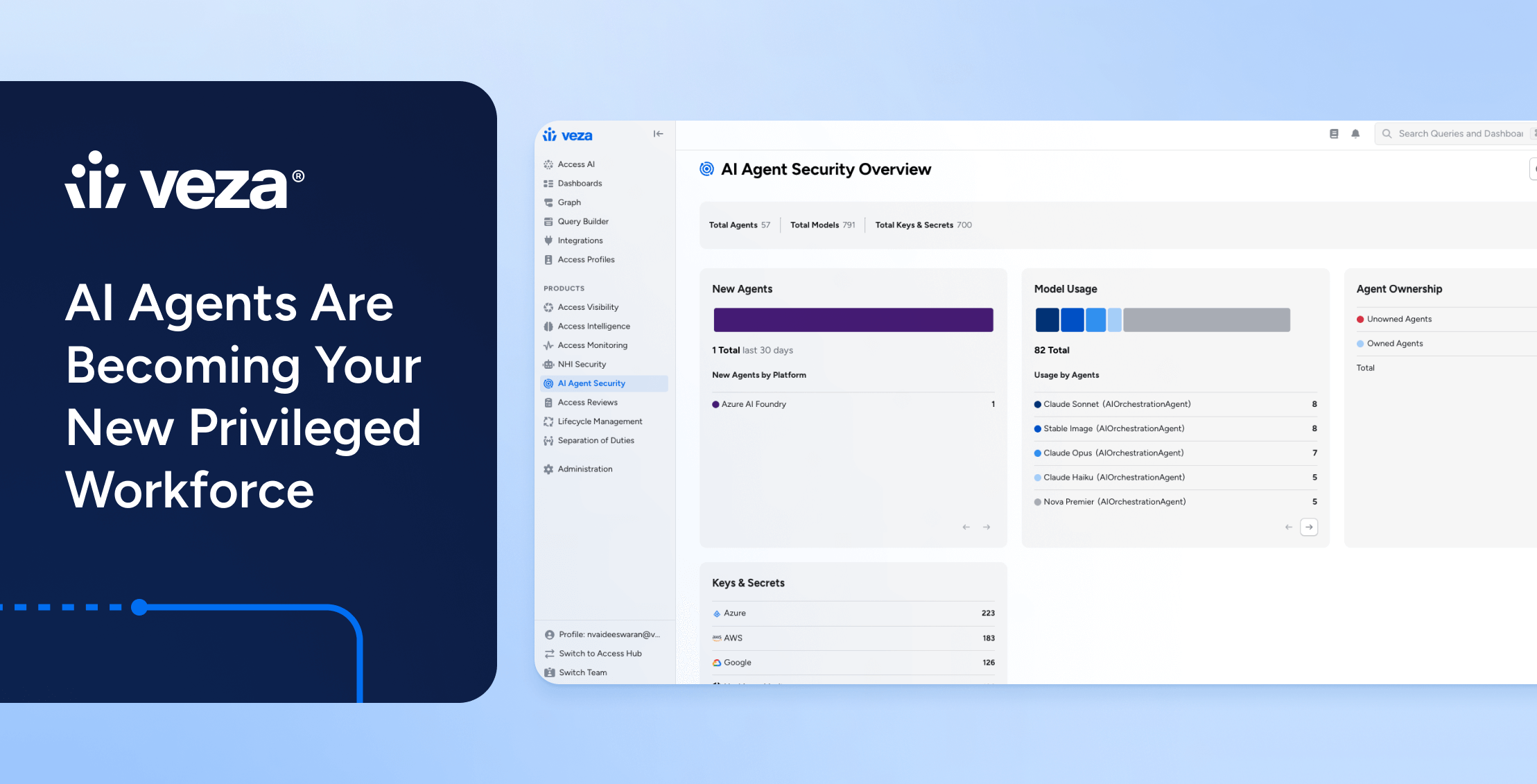 AI
AIAI Agents Are Becoming Your New Privileged Workforce
Learn more -
 Identity Security
Identity SecurityHow Revocation, Remediation, and Reconciliation Work in Veza Access Reviews
Learn more