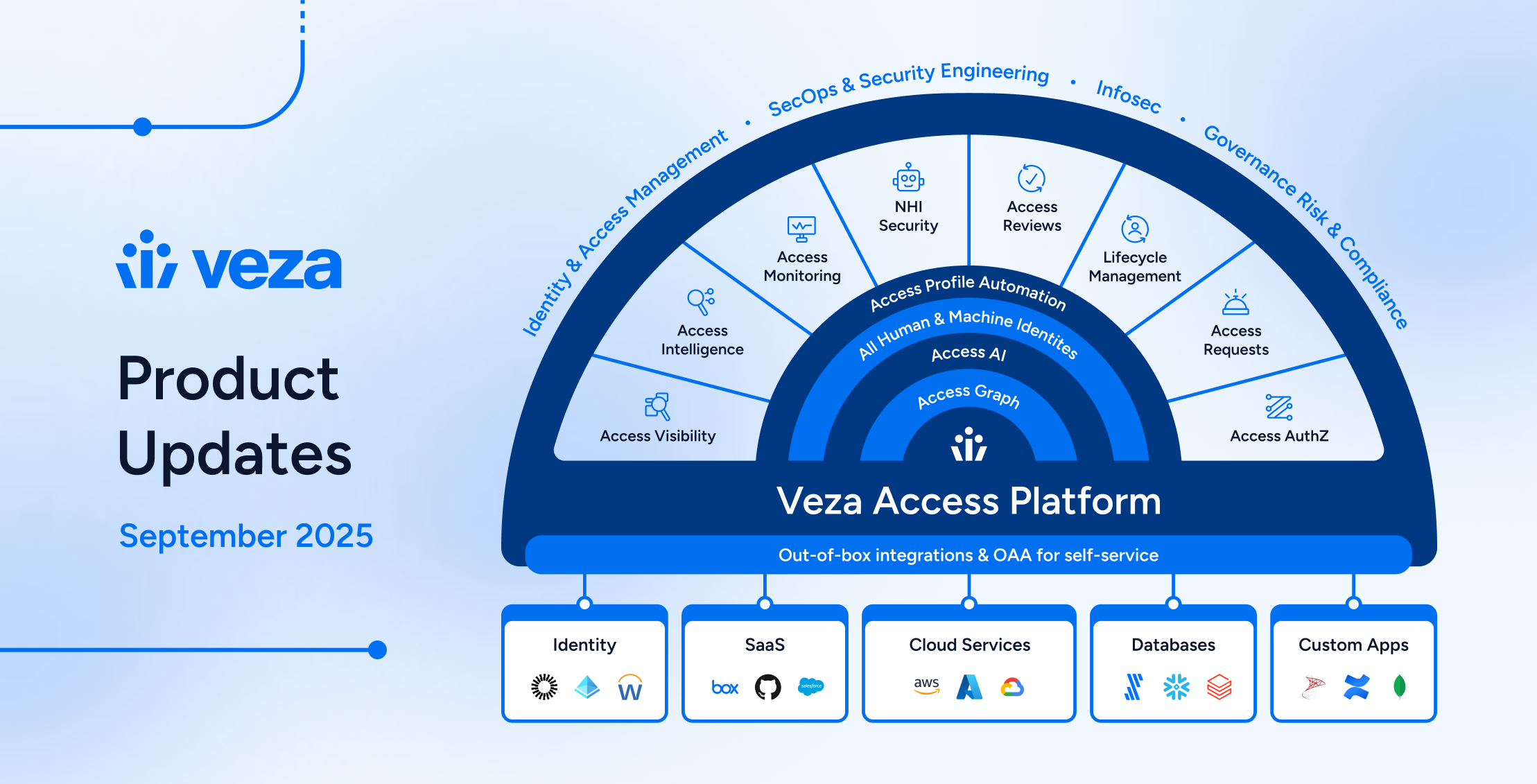
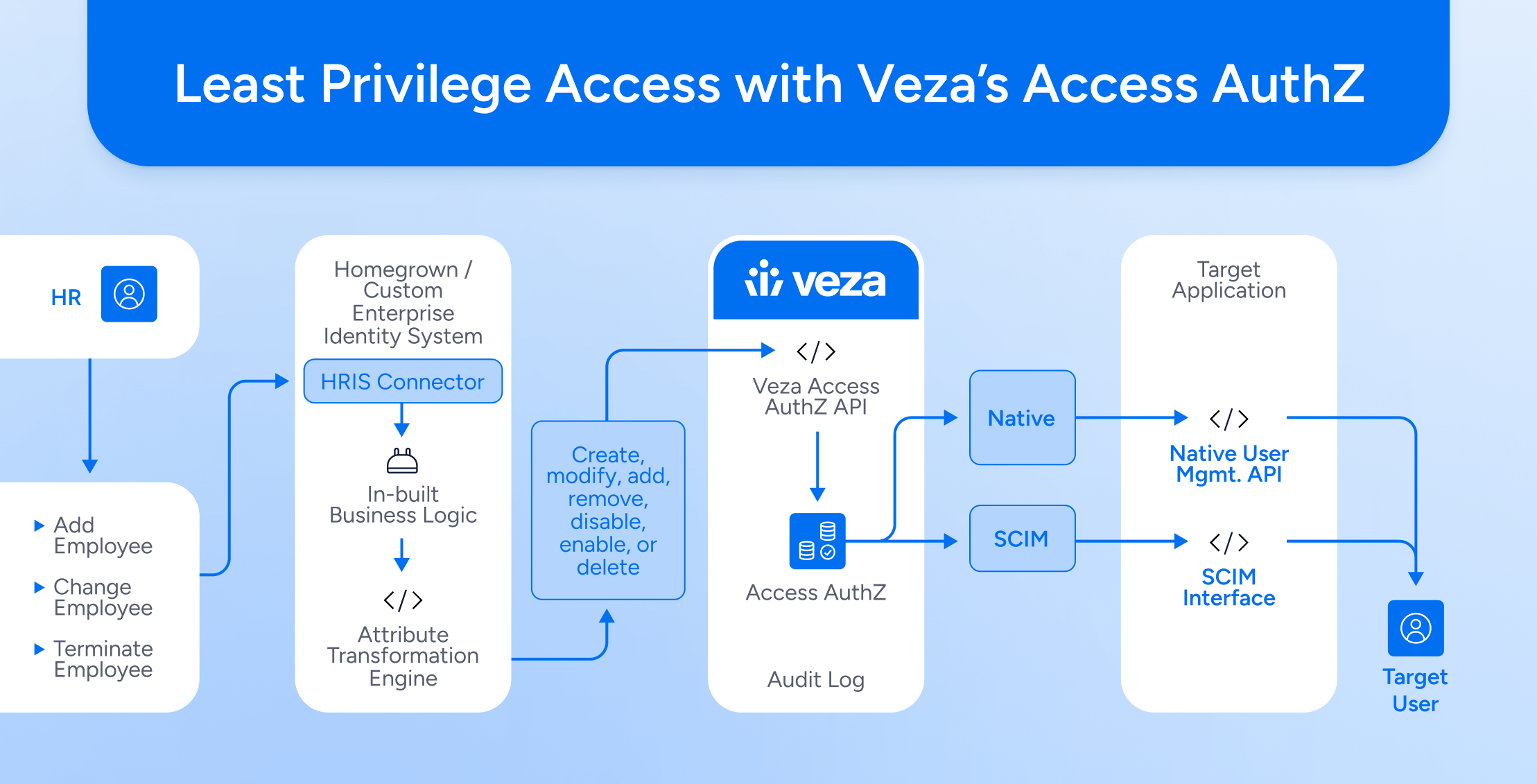
-
 Company
CompanyWhy Analysts Keep Pointing To Veza as the Leader In The New Identity Security Landscape
Learn more -
 Company
CompanyServiceNow + Veza: A new chapter in identity security
Learn moreToday marks a pivotal moment—not just for Veza, but for the entire identity security industry. I’m deeply proud to share that ServiceNow has signed a definitive agreement to acquire Veza. Together, we will accelerate the mission to secure identity across the modern enterprise as organizations transition into the era of agentic identities. When Maohua, Rob, […] -
 Identity Security
Identity SecurityHow Revocation, Remediation, and Reconciliation Work in Veza Access Reviews
Learn more -
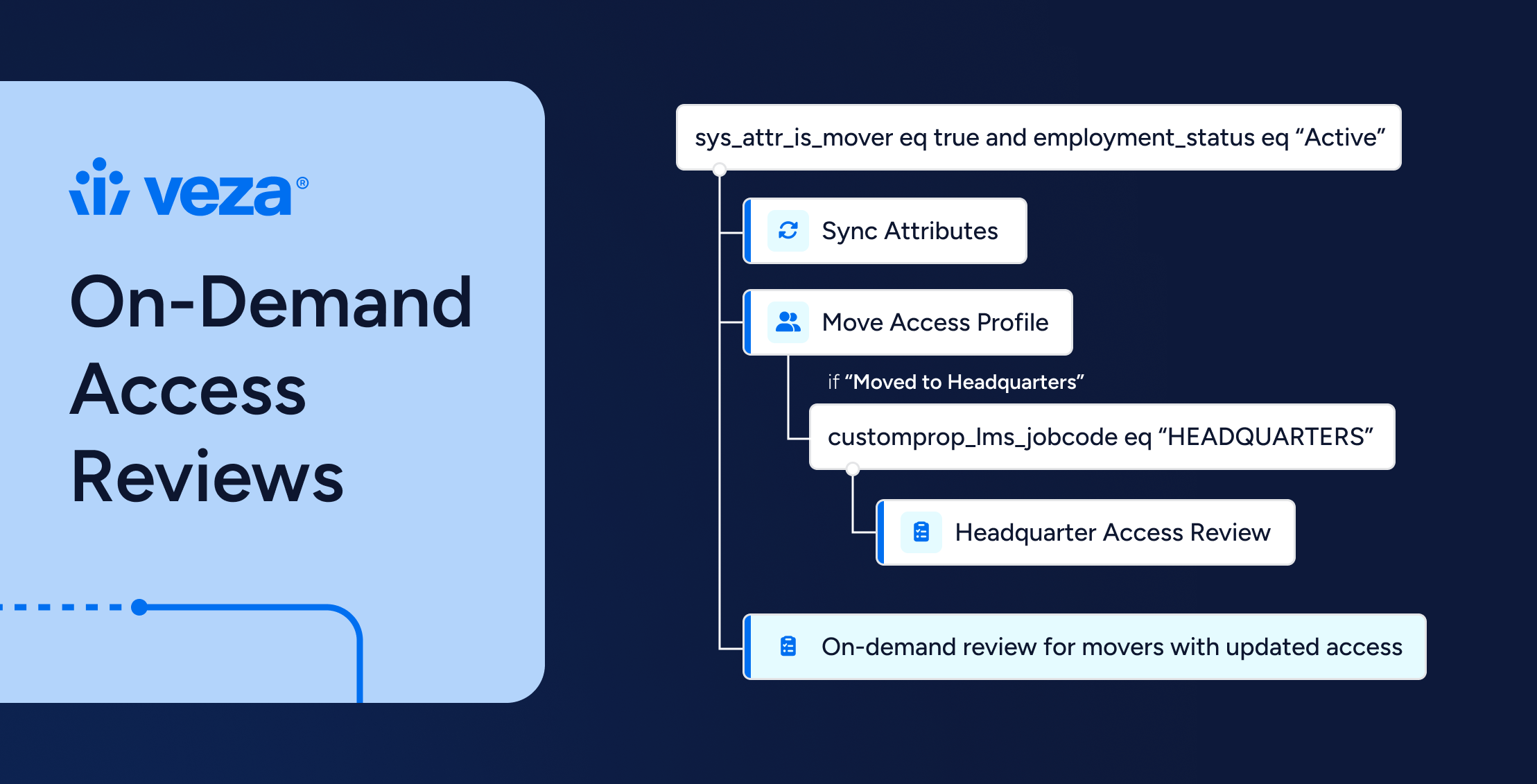 Compliance
ComplianceOn-demand Access Reviews
Learn more -
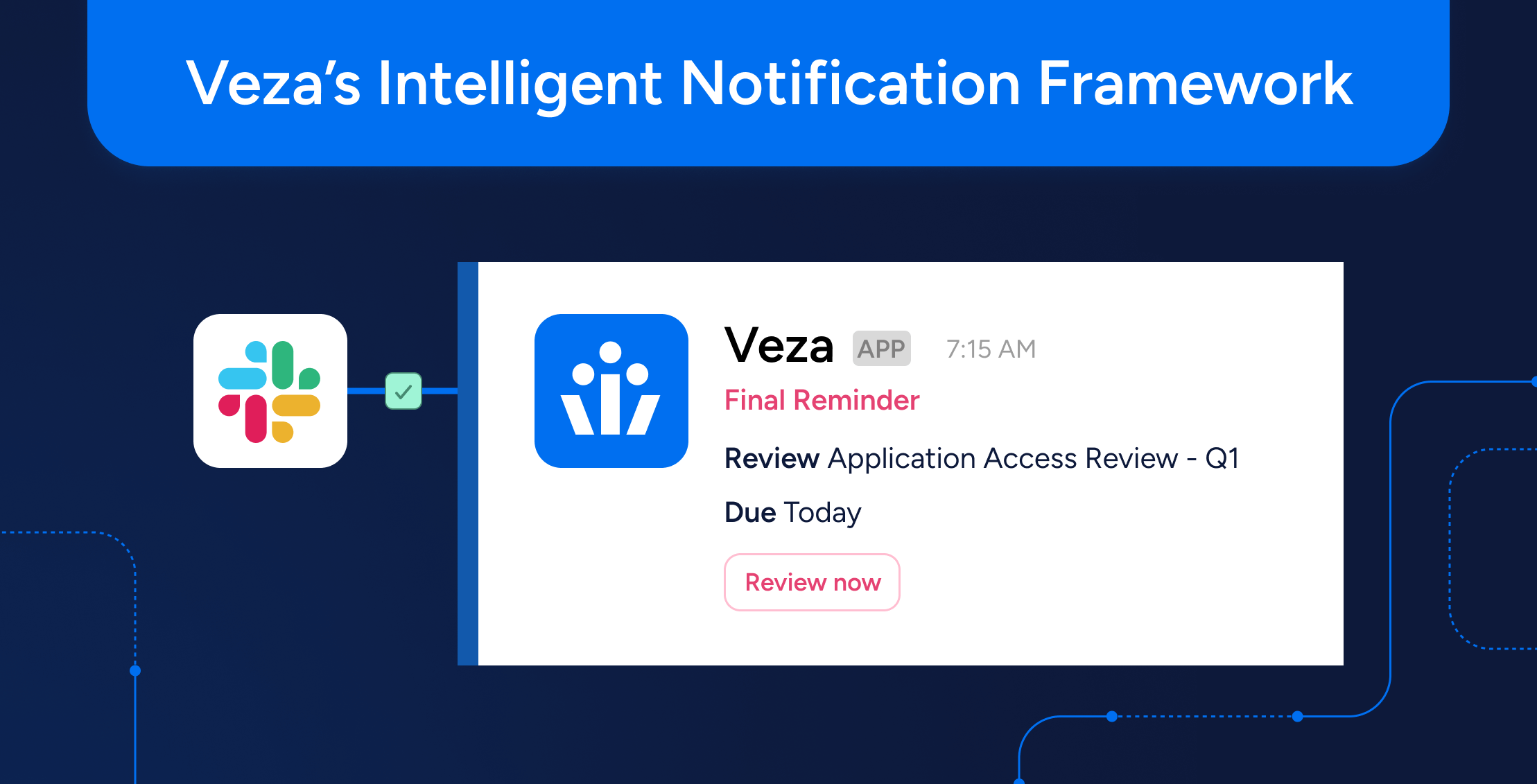 Identity Security
Identity SecuritySimplify Access Reviews with Veza’s Intelligent Notification Framework
Learn more -
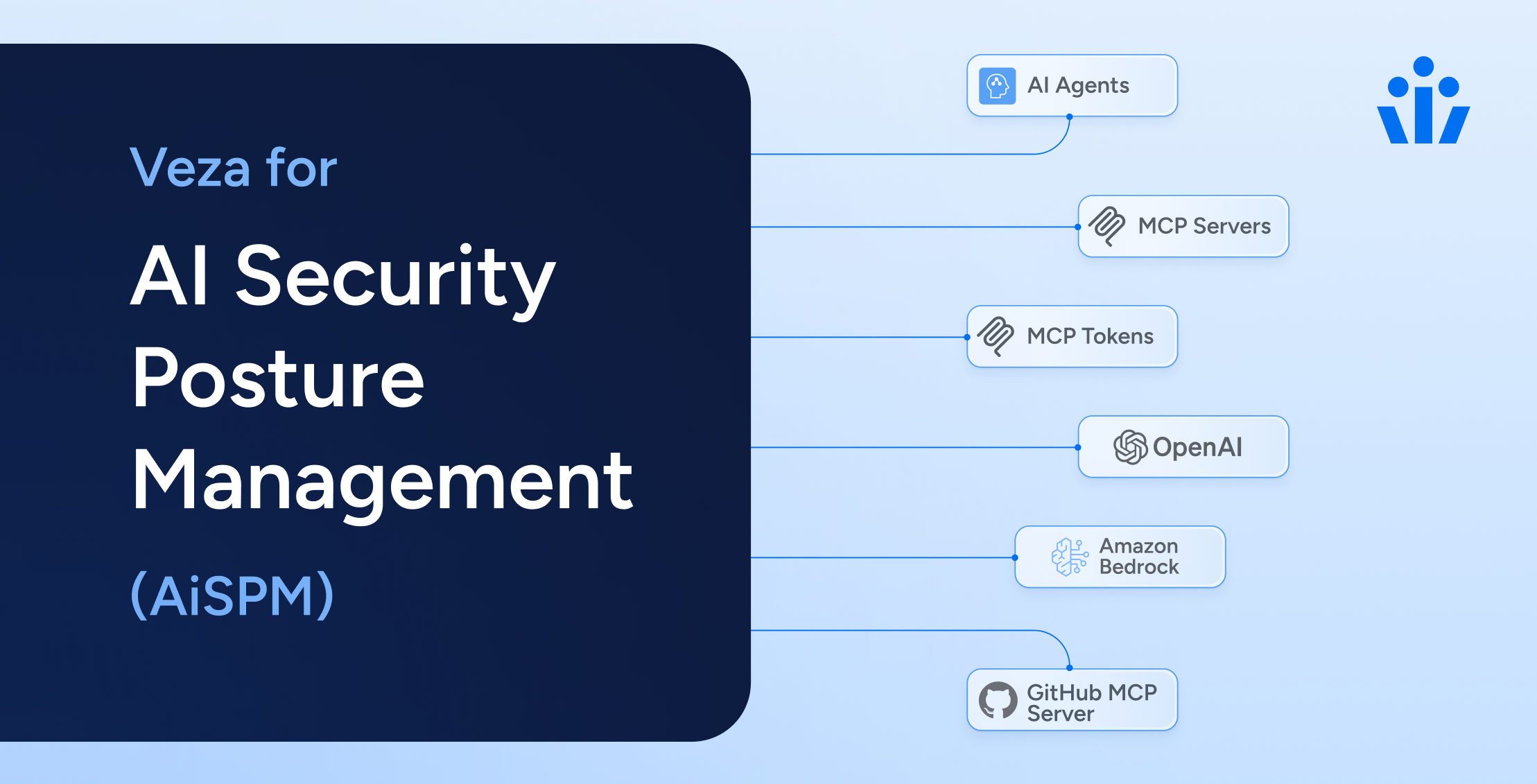 AI
AIDecoding Identity Security for AI Security Posture Management (AISPM)
Learn more -
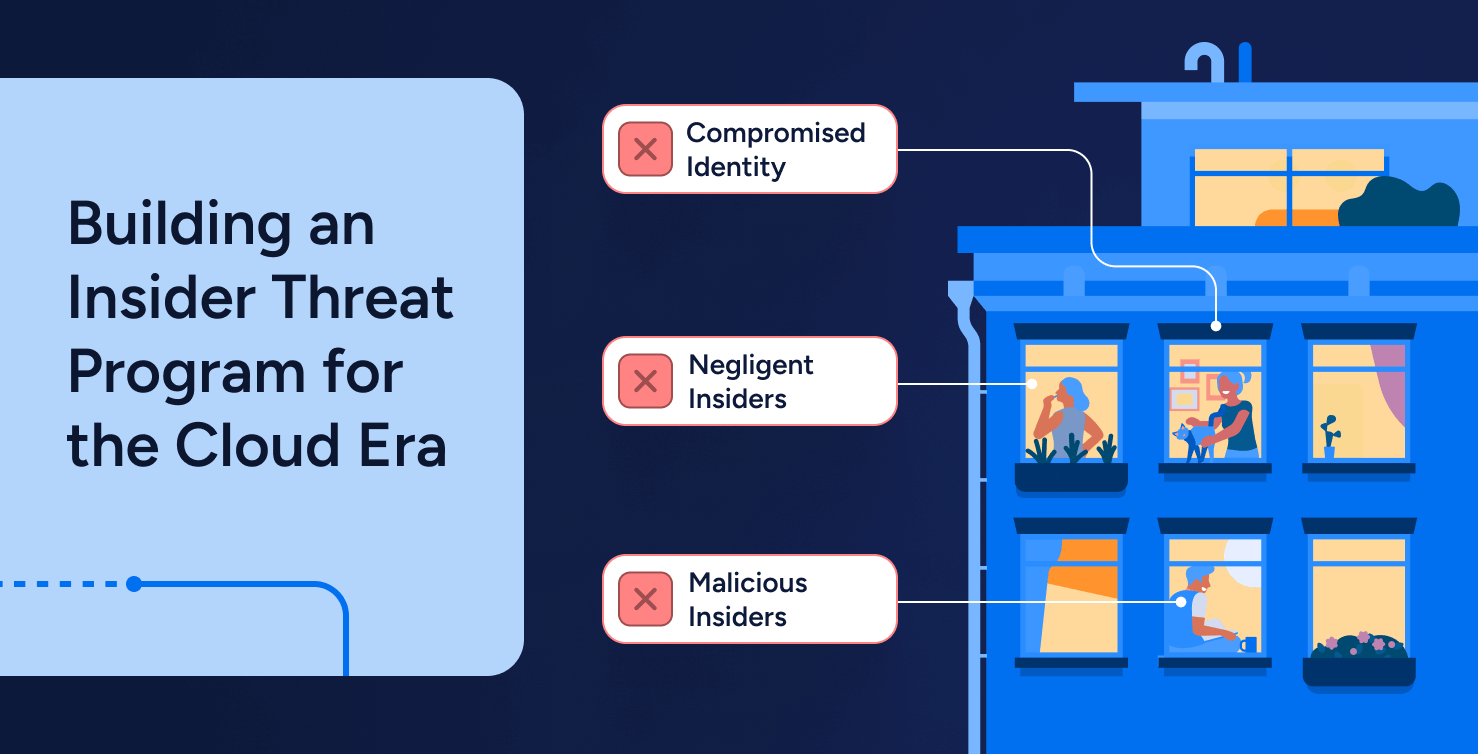 IAM
IAMWhen Identities Turn Against You: Building an Insider Threat Program for the Cloud Era
Learn more