-
 IAM
IAMIdentity is Eating Security: Why Access Is the New Perimeter
Learn more -
 Identity Radicals
Identity RadicalsWhen Logging In Is the New Hacking: Nicole Perlroth on the Evolving Cyber Threat Landscape
Learn more -
 Compliance
ComplianceSimplifying CMMC 2.0 Compliance: Modern Access Control Strategies for Government Contractors
Learn more -
 Compliance
ComplianceAchieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -
 Identity Radicals
Identity RadicalsThe Evolution of Identity and Security at Workday: Insights from CISO Josh DeFigueiredo
Learn more -
 Identity Radicals
Identity RadicalsBeyond the Buzzwords: Identity, Zero Trust, and Digital Transformation
Learn more -
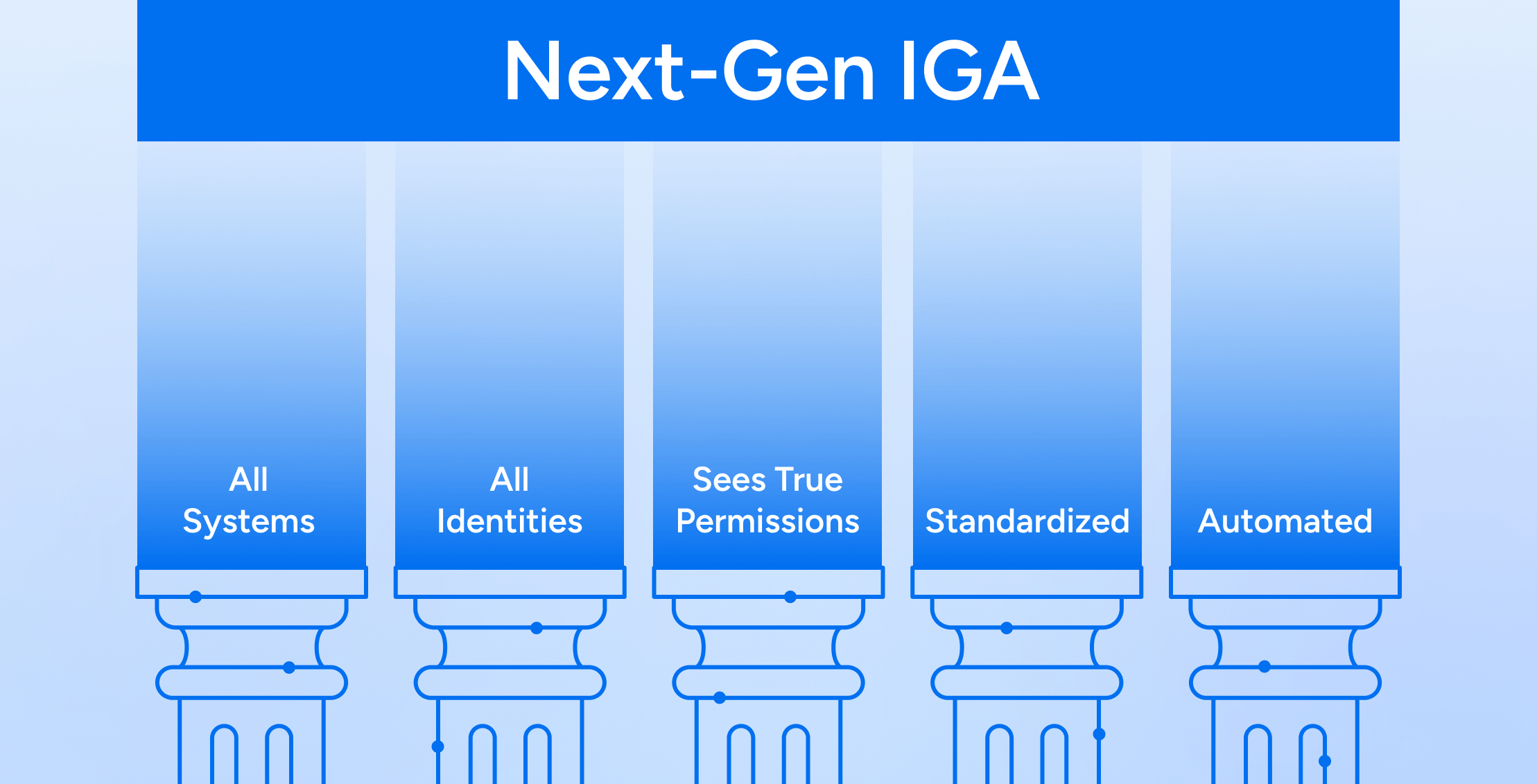 Identity Radicals
Identity RadicalsThe Five Tenets of Next-Gen IGA
Learn more