-
 Identity Radicals
Identity RadicalsThe SharePoint Blind Spot: How Legacy IGA Failed to Stop Volt Typhoon
Learn more -
 Identity Radicals
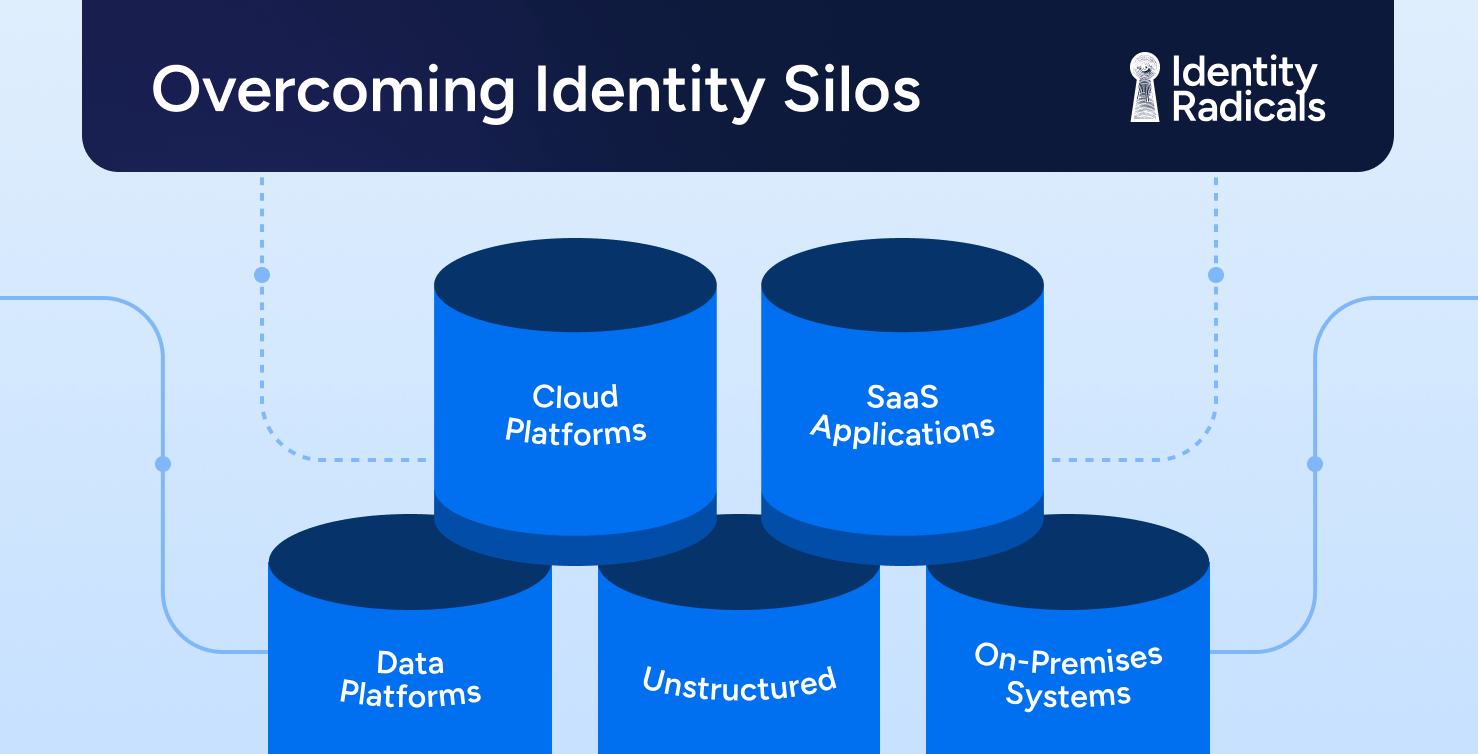
Identity RadicalsOvercoming Identity Silos: Toward Unified Identity Security
Learn more -
 Identity Radicals
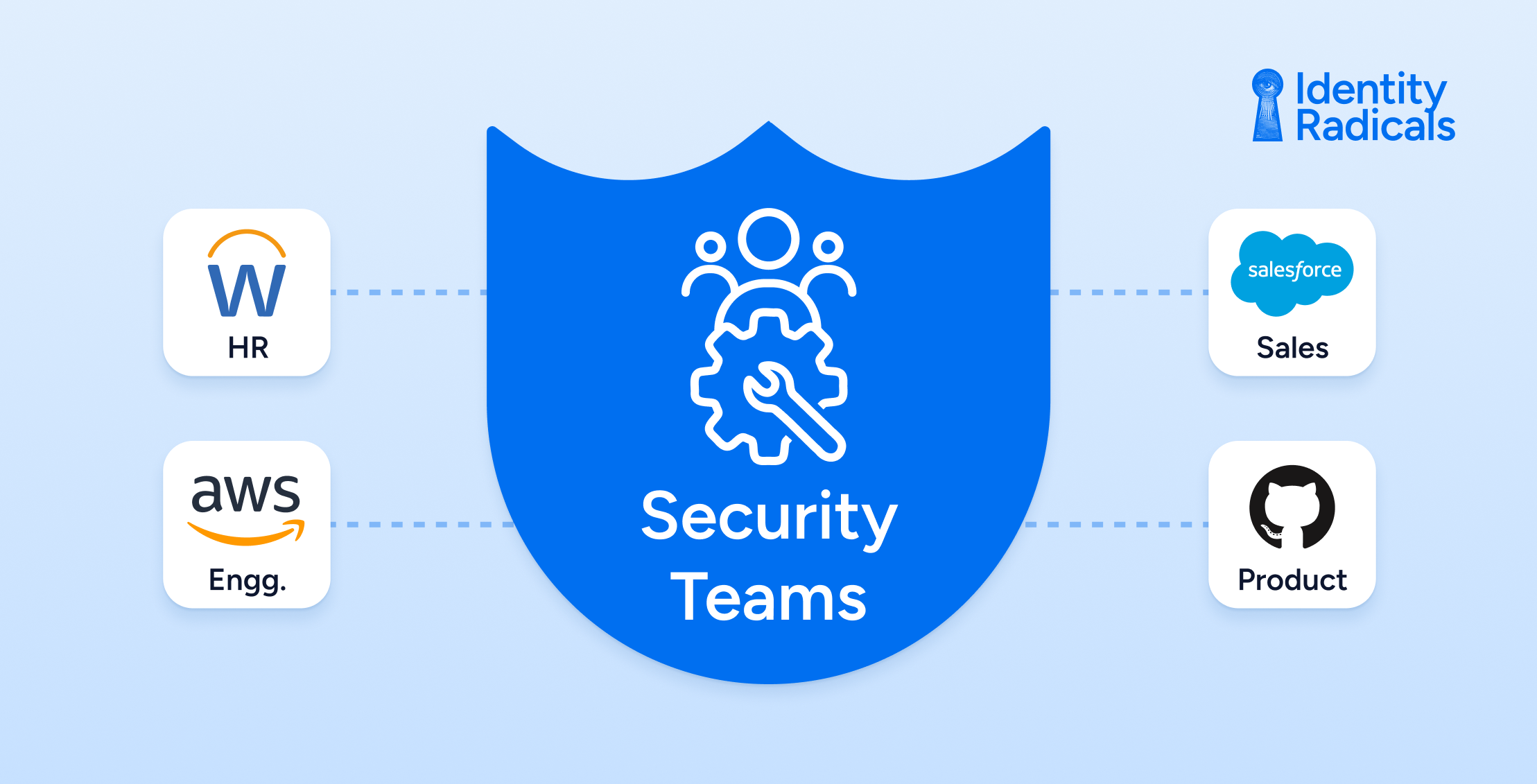
Identity RadicalsThe Security Paradox of Data and Digital Transformation
Learn more -
 AI
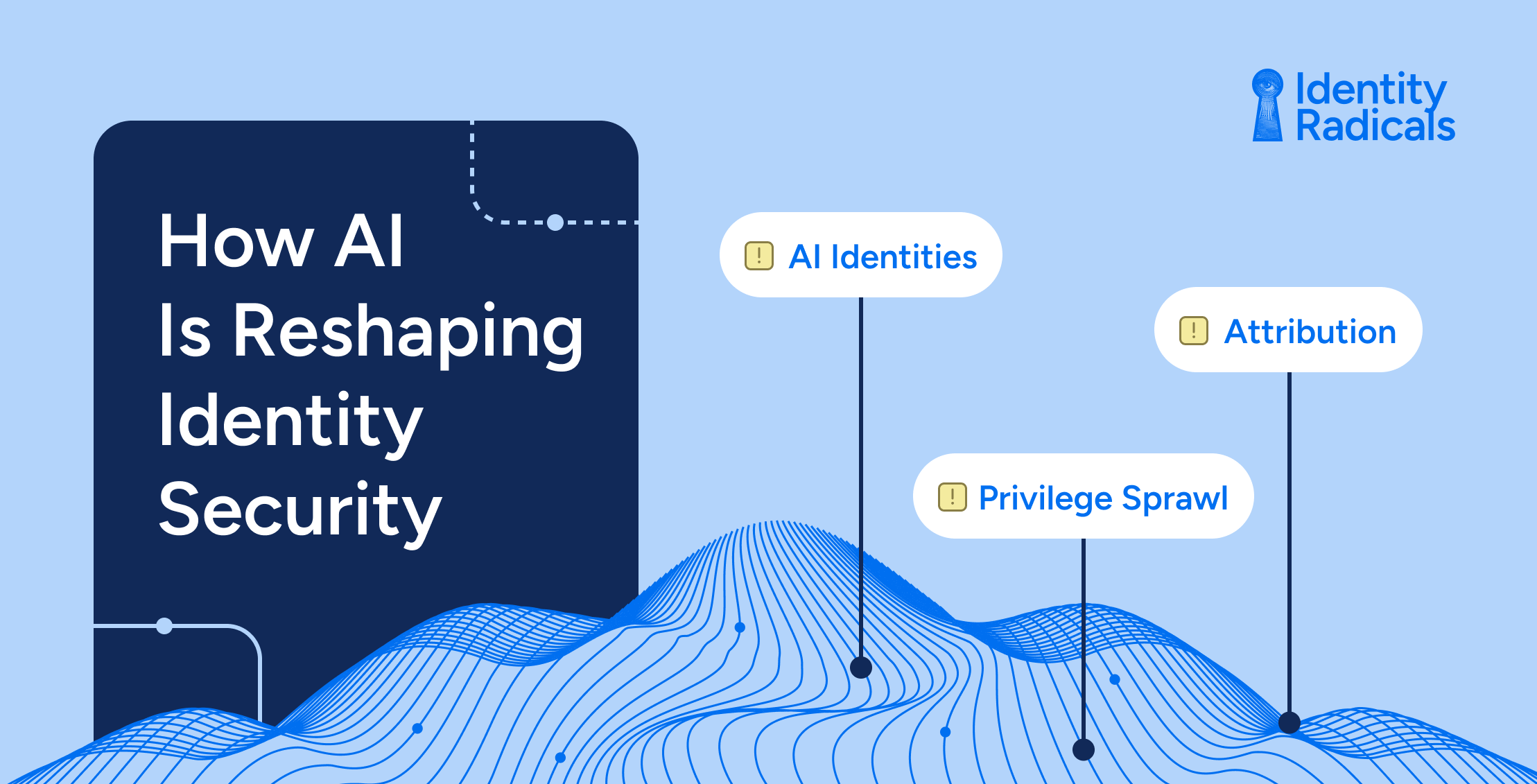
AIHow AI Is Reshaping Identity Security: Opportunities and New Threats
Learn more -
 Identity Radicals
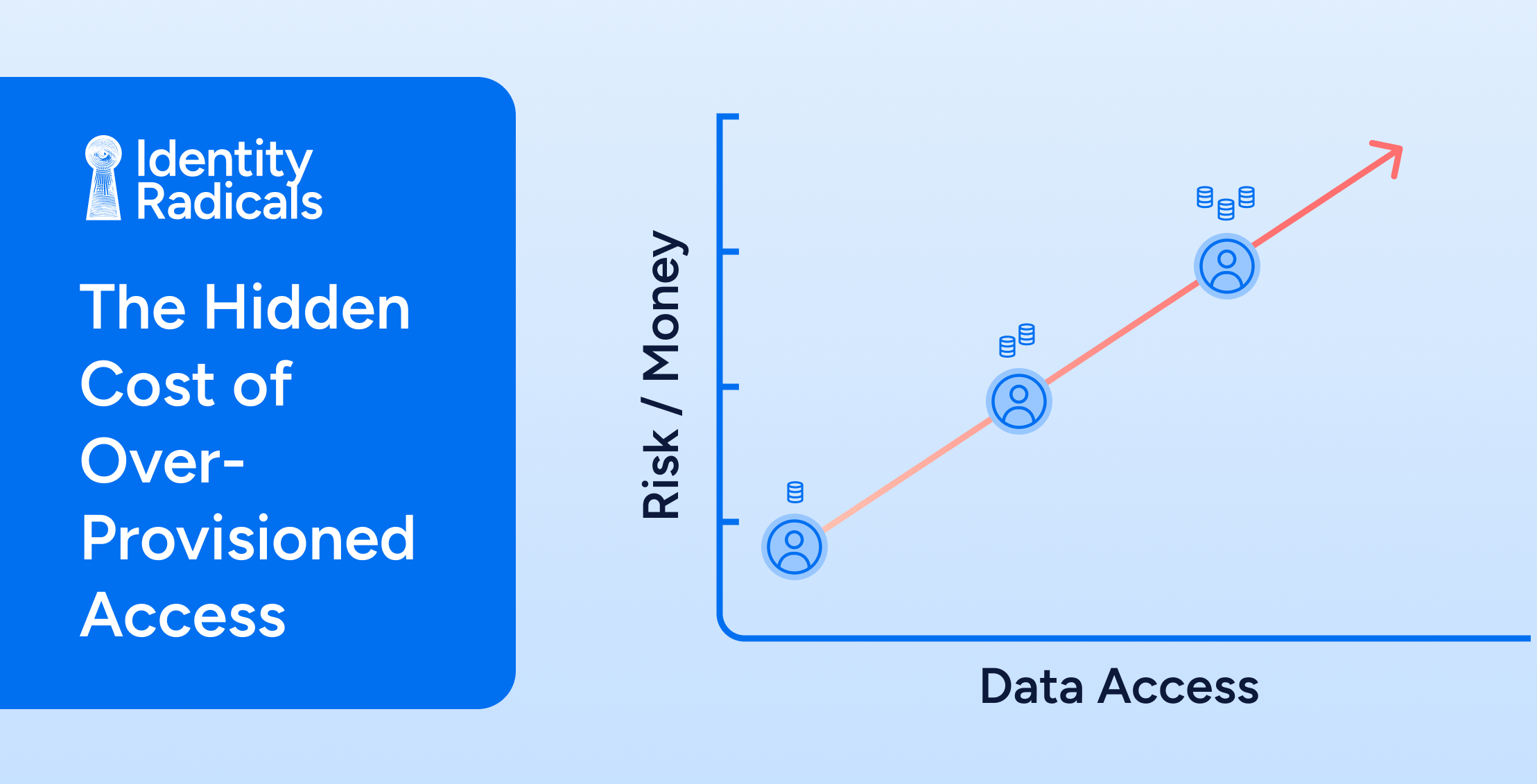
Identity RadicalsThe Hidden Cost of Over-Provisioned Access: Identity’s Role in Cloud Optimization
Learn more -
 Identity Radicals
Identity RadicalsIdentity is the New Security Perimeter
Learn more -
 Identity Radicals
Identity RadicalsThe Trust Dividend: How Security Leaders Build Enterprise Value
Learn more -
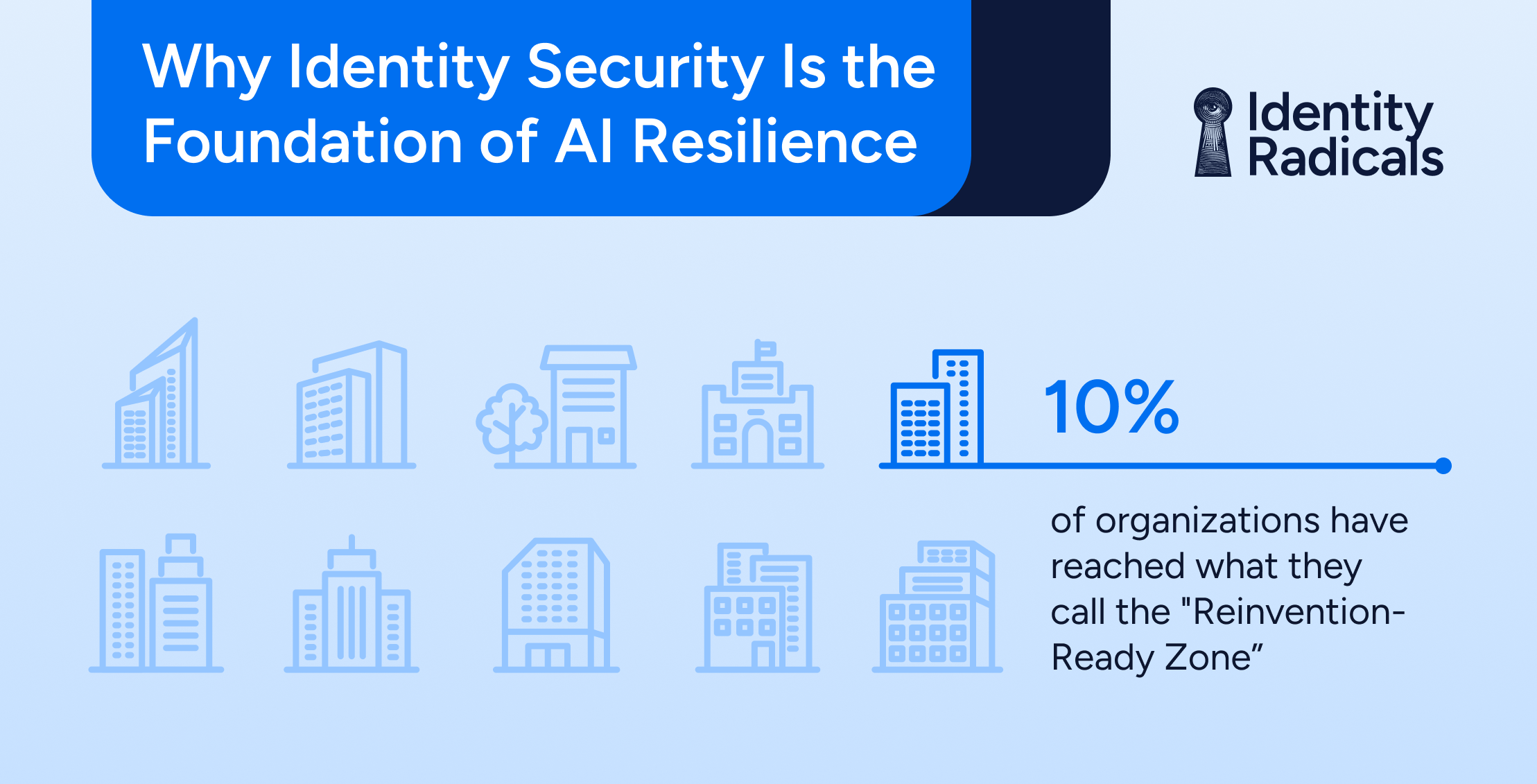 AI
AIFrom Exposed to Reinvention-Ready: Why Identity Security Is the Foundation of AI Resilience
Learn more -
 Identity Radicals
Identity RadicalsIdentity Crisis: The Rise of Machines
Learn more



