-
 Authorization
AuthorizationHow to secure access to your source code in GitHub
Learn more Rich Dandliker
Rich Dandliker -
 Authorization
AuthorizationSnowflake security: how to manage entitlement creep
Learn more Kale Bogdanovs
Kale Bogdanovs -
 Authorization
AuthorizationUnderstanding and protecting against the rising threat of Whale Phishing
Learn more Ellen James
Ellen James -
 Authorization
AuthorizationSnowflake security: how to manage and secure data access at scale
Learn more Kale Bogdanovs
Kale Bogdanovs -
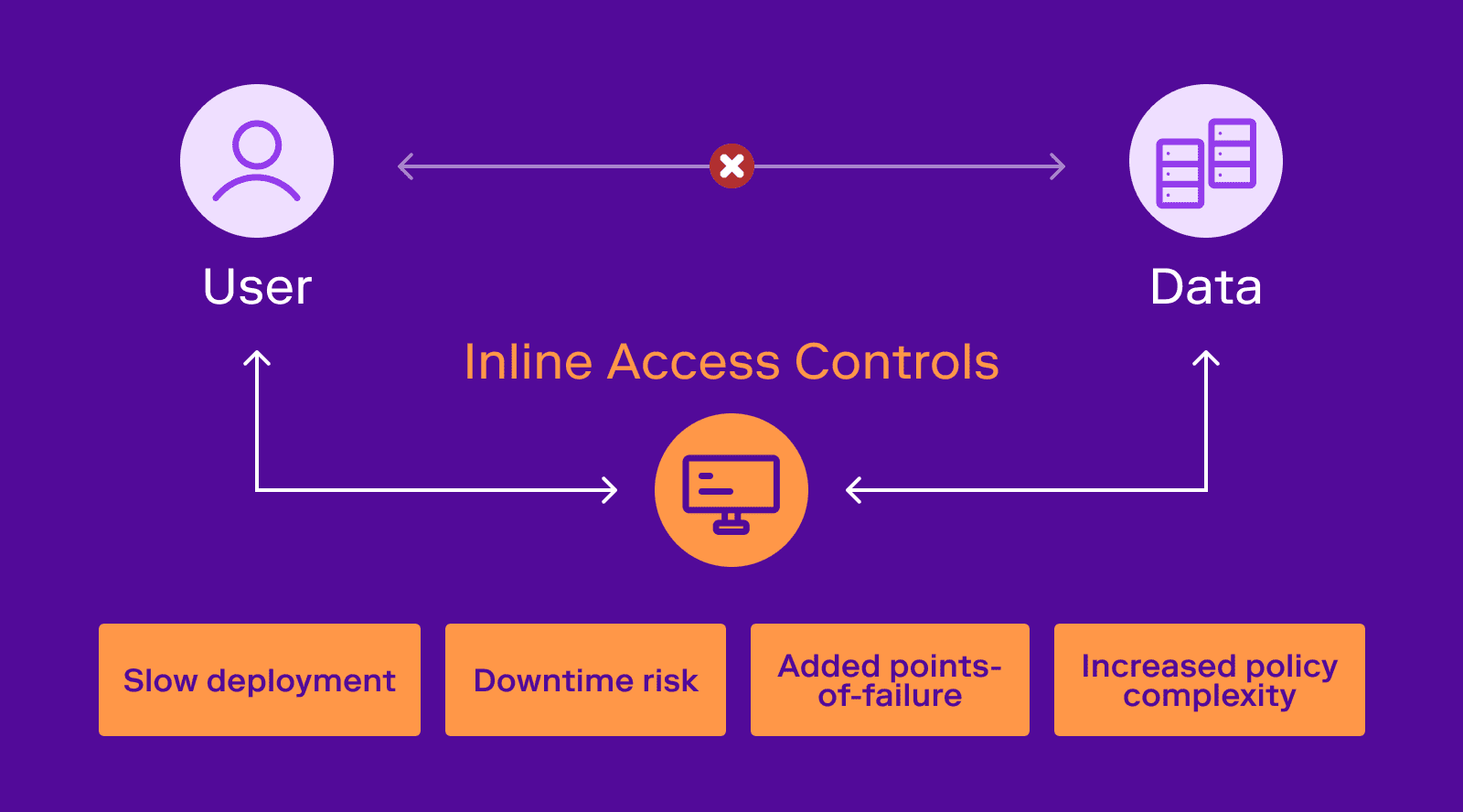 Authorization
AuthorizationThe Limits of “Man-in-the-Middle” Architecture for Authorization
Learn more Rich Dandliker
Rich Dandliker -
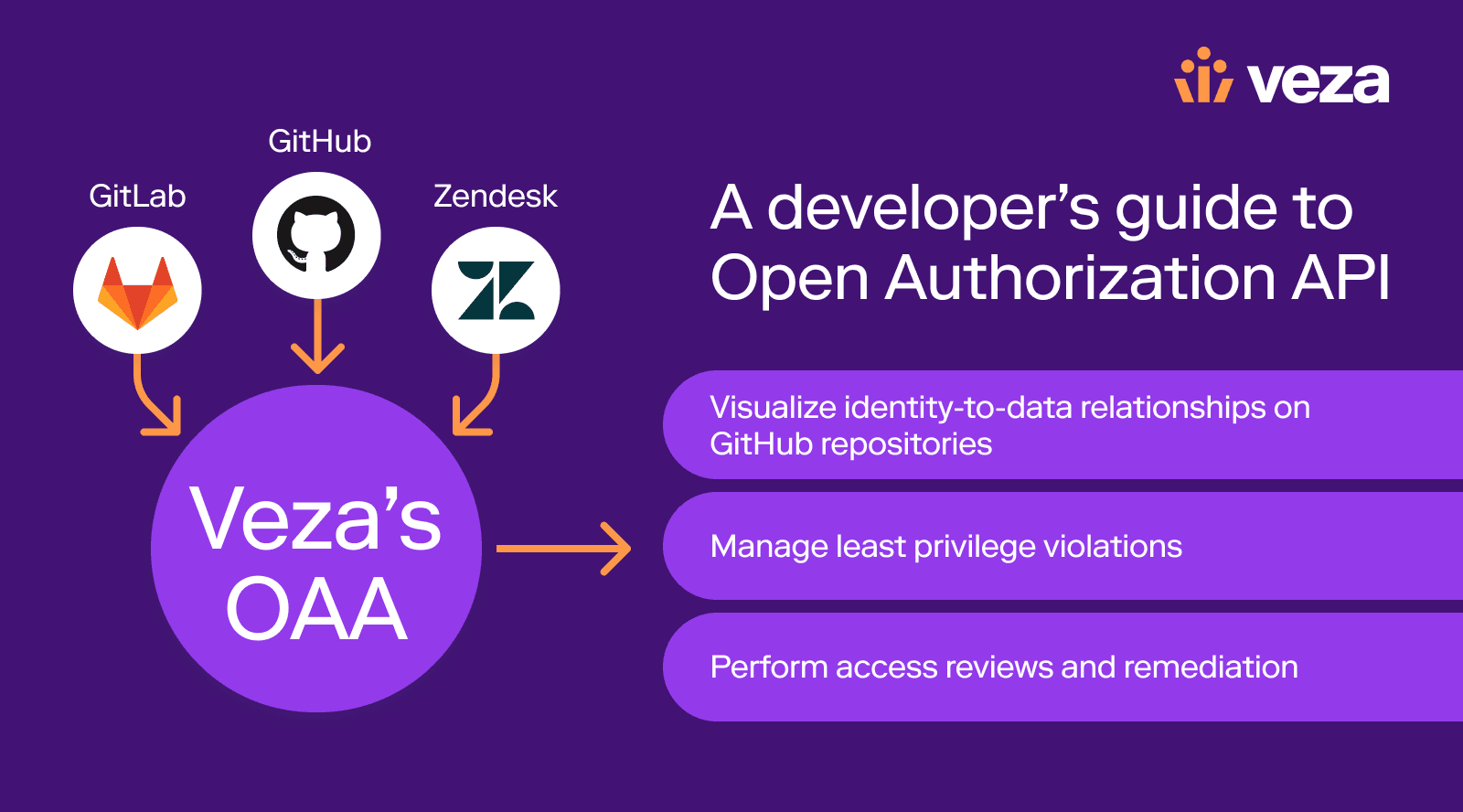 Authorization
AuthorizationIntegrate custom applications into a single control plane for authorization, with Open Authorization API
Learn more Jim Lester
Jim Lester -
Authorization
The Fundamentals of a Data-Centric Approach to Cloud Security
Learn more Teju Shyamsundar
Teju Shyamsundar -
Authorization
What is data security?
Learn more Teju Shyamsundar
Teju Shyamsundar -
 Authorization
AuthorizationRethinking Data Security with Veza
Learn more Craig Rosen
Craig Rosen -
 Authorization
AuthorizationSolving the Long-Tail Integration Problem with an Open Platform Strategy: Meet the Open Authorization API (OAA)
Learn more Rich Dandliker
Rich Dandliker