Accountability for Protection Without the Responsibility for Control
In 2025, digital transformation has reached escape velocity. Multi-cloud adoption, SaaS sprawl, AI-driven automation, and decentralized business models aren’t just trends—they’re table stakes. Yet after two decades in security leadership, I’m witnessing a profound paradox: security leaders are held accountable for protecting data everywhere, while the actual levers of access and control have become more distributed—and opaque—than ever before.
This isn’t just an operational challenge. It’s a fundamental shift in how we must think about security leadership and trust architecture in the digital age.
The New Reality: From Castle Walls to Digital Ecosystems
The transformation is stark. Not long ago, security teams could rely on centralized control—a single directory, a handful of on-premise applications, and a defendable perimeter. That world didn’t just evolve; it evaporated.
Today’s reality:
- While the average enterprise manages 275 SaaS applications, large enterprises can use over 400, up from previous years as SaaS adoption accelerates (references: Zylo | Cloudwards).
- Non-human identities (NHIs)—including service accounts, bots, and AI agents—now outnumber humans by 40:1 in large organizations (reference: TechRepublic.com – Gartner VP analyst Felix Gaehtgens, speaking at Gartner’s Security & Risk Management Summit in Sydney, 2025).
- AI agents and automation are driving new business value but also creating new “superuser” identities that operate at machine speed and scale.
- API-to-API connections create invisible permission chains that traditional tools can’t track
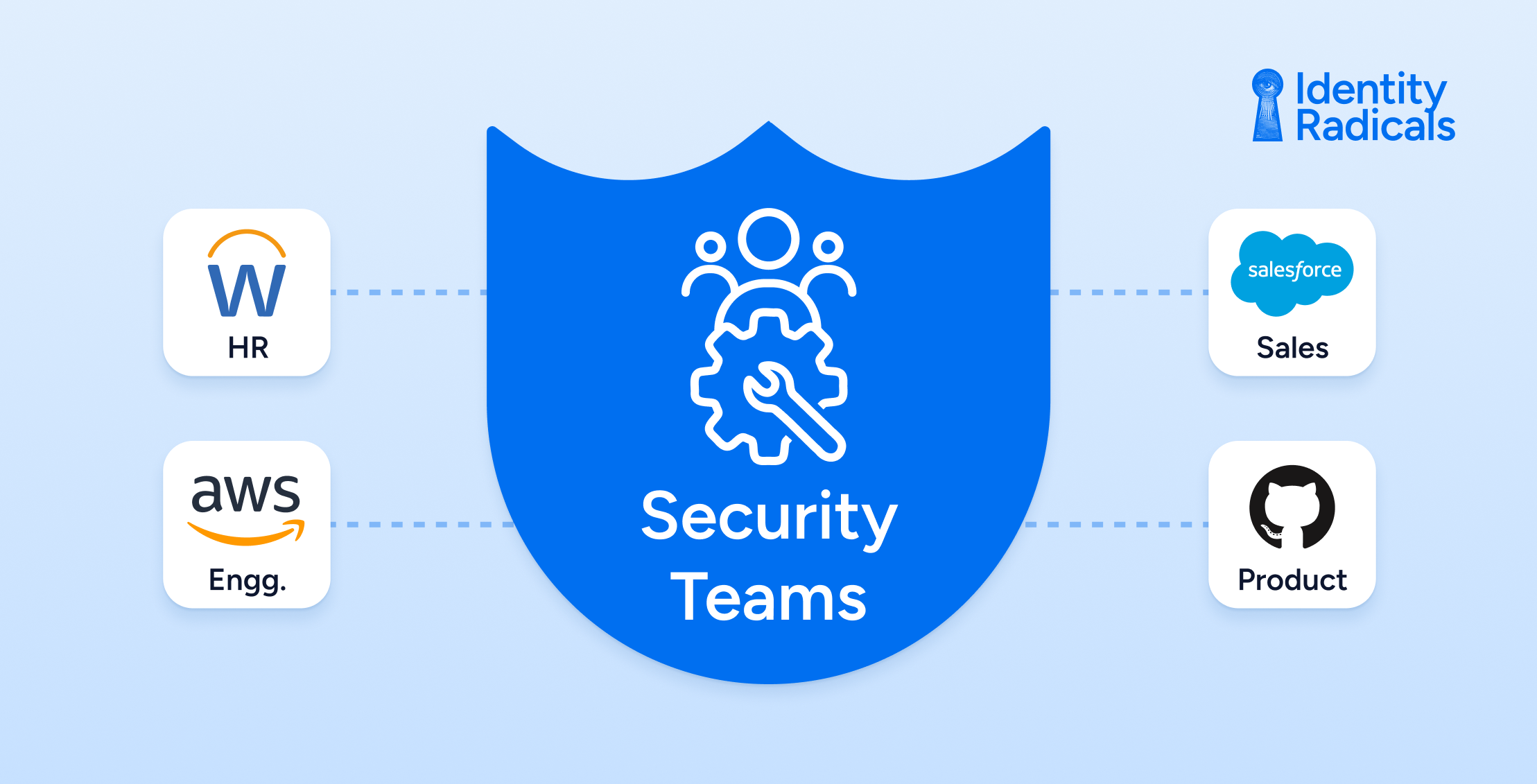
But here’s the real kicker: Business units now own and control these platforms. Commercial runs Salesforce. HR controls Workday. Engineering manages AWS. The Product team owns GitHub. Each creates their own identity ecosystems, permission structures, and access patterns.
Security teams? We’re held accountable for protecting it all, without operational control over any of it.
The Modern Paradox: Accountability Without Authority
This paradox creates real consequences:
Identity has become the primary attack vector. Recent incidents—Change Healthcare, Microsoft Exchange, MGM Resorts—prove attackers don’t break in anymore. They log in with valid credentials, often exploiting misconfigured NHIs or dormant service accounts that nobody remembered existed (reference: Fortify Data)
Shadow Access eclipses Shadow IT. It’s no longer about unsanctioned apps. It’s about invisible permission pathways—service accounts with inherited privileges, AI agents with composite identities, API keys that traverse multiple systems. I call this the “permission fabric,” and most organizations can’t even see it, let alone control it.
Regulatory pressure is intensifying. DORA, SEC cyber rules, and emerging AI governance frameworks demand that boards and CISOs demonstrate real-time visibility into “who can access what, where, and when.” Not in theory. In practice. Demonstrably.
The trust equation has shifted. Every digital interaction is now an act of trust. When a bot accesses customer data at 3 AM or when a contractor’s API key touches production systems, trust architecture determines whether that’s business as usual or indicators of compromise.
Why Traditional Approaches Fail in the Trust Economy
Legacy IAM and IGA solutions were architected for a different era—static roles, predictable access patterns, centralized IT control. These tools are simply outmatched by the new reality.
In 2025, these tools can’t handle:
- Dynamic permissions that change hourly across platforms
- Effective permissions—the actual capabilities buried under layers of groups, roles, and delegations
- AI agent identities that combine human and machine permissions in novel ways
- Cross-platform blast radius, where one compromised identity can cascade across dozens of systems
- Machine-speed attacks, where traditional detection and response cycles are meaningless
Most critically, they can’t build trust. They manage compliance, not confidence.
The Path Forward: From Control to Trust Architecture
Leading security organizations are transcending the paradox by shifting from control-based to trust-based security. Here’s how:
1. Map the Real Permission Fabric
Stop managing theoretical access. Focus on effective permissions—understanding precisely what identities can do across the entire digital estate, down to the individual resource level (e.g., database, S3 bucket, folder). This means understanding toxic combinations, privilege escalation paths, and the true blast radius of every identity, human or machine.
2. Embrace Distributed Trust Architecture
Accept that centralized control is dead. Instead, build a trusted architecture that works across distributed ownership:
- Partner with business units as trust architects, not compliance enforcers
- Embed security intelligence into their platforms, not impose controls from outside
- Make trust visible and valuable to stakeholders who own the systems
3. Operationalize Data-Driven and AI-Powered Governance
Manual processes can’t match machine-speed threats. To effectively govern at scale, we first need comprehensive, consistent data on permissions and access paths to every resource. With this foundation, we can then leverage AI to:
- Continuously baseline normal access patterns across thousands of identities
- Detect and respond to anomalies in real-time (that AI agent accessing 50,000 files? Shut it down in seconds, not hours)
- Automate access reviews and right-sizing at scale
- Predict and prevent toxic permission combinations before they’re exploited
4. Treat Every Identity as Critical Infrastructure
The operational difference between human and non-human identities is diminishing, necessitating consistent intelligence and controls. Implement comprehensive lifecycle management for ALL identities:
- Service accounts need the same governance as privileged users
- AI agents require composite identity models linking them to human accountability
- API keys and tokens demand ownership, rotation, and monitoring
- Every identity needs a birth certificate, a purpose, and an expiration date
5. Build Trust Through Radical Transparency
Transform security from a mysterious black box to a trust-building capability:
- Show business units their actual permission landscape in business language
- Make the value exchange clear—what they gain from security participation
- Publish trust metrics that matter to stakeholders, not just auditors
- Acknowledge the shared challenge and shared accountability
6. Prepare for the Agentic Future
AI agents aren’t coming—they’re here, likely operating in many environments today. Establish:
- Clear policies for AI agent provisioning and permissions
- Attribution models that track every action back to accountable humans
- Monitoring that distinguishes between human and agent activities
- Trust boundaries that enable innovation while preventing catastrophic failure
Beyond the Paradox: Security as Trust Catalyst
The security paradox of digital transformation—accountability without control—isn’t a problem to solve. It’s a reality to transcend. The most successful security leaders are those who stop fighting for control and start building for trust.
This means accepting that:
- We’ll never again have centralized control over all identities and access
- Business velocity will always outpace security’s ability to govern traditionally
- AI and automation will create new identity challenges faster than we can address old ones
- Trust, not control, is the currency of digital transformation
But here’s the opportunity: Organizations that master distributed trust architecture don’t just survive the paradox—they thrive because of it. They move faster because trust enables speed. They innovate boldly because trust provides guardrails, not roadblocks. They recover from incidents faster because trust creates resilience.
The Call to Action: From Paradox to Possibility
As security leaders, we stand at an inflection point. We can cling to the illusion of control and watch our influence diminish. Or we can embrace our role as trust architects and watch our impact multiply.
The choice isn’t just about security strategy. It’s about recognizing that in a world where every company is a technology company, and every interaction is a trust transaction, security leaders who build trust architecture become business leaders who enable transformation.
The paradox is real. The accountability without control is permanent. But for those willing to evolve from security guardians to trust architects, the opportunity has never been greater.
The future belongs to those who build trust at the speed of digital — and that starts with clear, continuous visibility into every identity, every permission, and every connection across your ecosystem.
- Ready to rethink identity visibility? Start with the Identity Radicals podcast episode “Identity Crisis: The Rise of Machines,” where Roland Cloutier unpacks the explosion of machine identities and the visibility gap that threatens trust.
- Dive deeper into the strategy with our ISPM Solution Brief, detailing how Identity Security Posture Management (ISPM) enables real-time posture scoring, continuous reduction of identity risk, and support for Zero Trust and emerging regulatory mandates.
- Ready to operationalize trust? Schedule a demo with Veza to see how real-time permission fabric mapping, anomaly detection, and identity lifecycle governance bring trust architecture into practice.






